-
MFA Nonfiction Mentor Awarded 2025 American Mosaic Journalism Prize

The article MFA Narrative Nonfiction mentor awarded the 2025 American Mosaic Journalism Prize was initially published on UGA Today.
-
March 2025 Insights: Faculty and Staff Highlights

The faculty and personnel at Florida State University are integral to its vision and the foundation of its numerous successes. Throughout the calendar year, honors and accolades are presented to individual faculty and staff throughout the campus. Faculty and Staff Briefs are created monthly to acknowledge achievements and offer a platform where recognitions, awards, publications,…
-
U of A Launches Initiative to Accelerate Fusion Energy Commercialization

U of A establishes position focused on advancing fusion energy to market nprevenas Fri, 03/28/2025 – 09:34 U of A establishes position focused on advancing fusion energy to market Thursday News Categories Business & Economics Government, Public Policy & Law Science & Technology University News By Arizona Daily Star Type of News Article External News
-
The Emergence of Conversational Companions: The Chatbot Friendship Revolution

The emergence of chatbot ‘companions’ nprevenas Fri, 03/28/2025 – 09:34 The emergence of chatbot ‘companions’ Wednesday Article Categories Current Events Sociology By Vox Type of News Article Third-party News
-
Webb Telescope Discovers Galaxy at a Crucial Juncture in the Dawn of the Universe

Webb telescope detects galaxy during crucial phase in the nascent universe nprevenas Fri, 03/28/2025 – 09:32 Webb telescope detects galaxy during crucial phase in the nascent universe Wednesday Story Categories Current Events Science & Innovation Astronomy By Reuters Type of News Article Outside News
-
“Depleting Water Reserves: The Growing Crisis for Agriculture”

The planet’s reservoir of water within soil, lakes, and rivers is diminishing. This is particularly detrimental for agriculture. nprevenas Fri, 03/28/2025 – 09:31 The planet’s reservoir of water within soil, lakes, and rivers is diminishing. This is particularly detrimental for agriculture. Thursday Categories of the Story Government, Public Policy & Law Current Events Scientific &…
-
The Evolving Landscape of Wildfires: A Historical Perspective
In recent years, wildfires have increased in scale – yet they still seem insignificant when compared to those from centuries ago nprevenas Fri, 03/28/2025 – 09:22 In recent years, wildfires have increased in scale – yet they still seem insignificant when compared to those from centuries ago Thursday Categories of the Story Current Affairs Science…
-
How MSU research strengthens Michigan’s $6B grape industry
-
Jason Sudeikis Delves into Life Lessons with Pete Carroll’s ‘Game is Life’ Course

The Ted Lasso and SNL celebrity attended the renowned football mentor’s college class to motivate learners with teachings on self-assurance and determination.
-
Seven USC Professors Inducted as AAAS Fellows, Honoring Their Remarkable Achievements
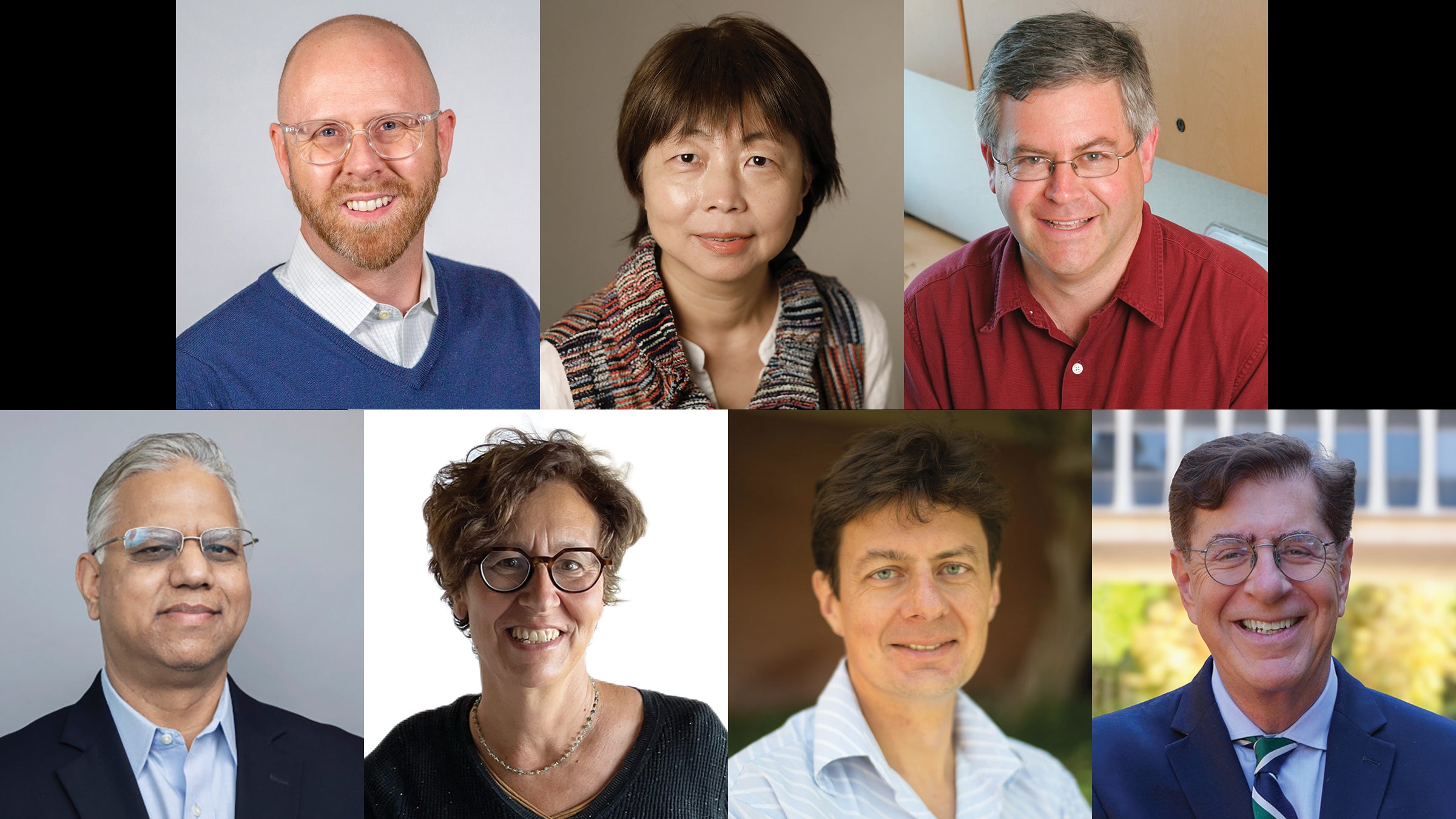
“`html The latest USC American Association for the Advancement of Science fellows are: (top row, left to right) Richard Brutchey, Yali Dou, and Steven Finkel; (bottom row, left to right) Satyandra K. Gupta, Emily Liman, Oleg Prezhdo, and Costas Synolakis . (Photos/top row, from left: Mike Glier, Steen Cohn, Phil Channing; bottom row, from left: Noé…
-
“Harnessing Sunshine: The Innovative Approach of Solar Canals in California”

“`html An artist’s depiction illustrates Project Nexus in California’s Central Valley, marking the state’s inaugural solar canal pilot. (Photo Illustration/Solar AquaGrid) Share Science/Technology ‘Solar canals’: A luminous answer for California’s water and energy requirements? The USC-led California Solar Canal Initiative has the potential to convert significant sections of the state’s 4,000 miles of canals into…
-
Shaping Perspectives: How Twitter Metaphors Influence Immigration Narratives

Research: When individuals are floods: Examining dehumanizing metaphors in immigration conversation with extensive language models Individuals holding strong political opinions on immigration can exert considerable impact by composing tweets rich with metaphors, influencing how others comprehend this intensely debated topic. In a recent investigation, scholars from the University of Michigan and the University of Chicago…
-
Economic Policy Uncertainty Dims Consumer Confidence Yet Again

Consumer confidence plummeted by 12% in March, marking the third consecutive month of decline. Although the prevailing economic conditions showed minimal alteration, the anticipatory expectations index sank sharply by 18%, having now declined over 30% since November 2024, noted economist Joanne Hsu, director of the University of Michigan’s Surveys of Consumers. This month’s downturn illustrates…
-
Laura and William Jens Appointed as Professors of Environmental Engineering

Jason He (left) is photographed alongside Dean Aaron Bobick during He’s ceremony of installation as the Laura and William Jens Professor of Environmental Engineering. (Photo: JJ Lane/WashU) Jason He, a specialist in wastewater management and environmental biotechnology, has been appointed as the Laura and William Jens Professor of Environmental Engineering. Since 2020, he has been…
-
Saltzman Appointed as New Head of Jonathan Edwards College

W. Mark Saltzman, a constructor and instructor who has been associated with the Yale academic staff since 2002, reverts to a position he occupied at Jonathan Edwards from 2016 to 2022.
-
How Survivors Spread Across the Globe After Earth’s Greatest Mass Extinction

Studying aquatic survivor species following a mass extinction may assist researchers and decision-makers in comprehending the ongoing biodiversity emergency.
-
FSU Historian Receives Esteemed Fellowship to Enhance Middle Eastern Studies at Durham University
The article FSU historian receives esteemed fellowship to promote Middle Eastern studies at Durham University was initially published on Florida State University News.
-
FSU Historian Receives Esteemed Fellowship to Propel Middle Eastern Studies at Durham University
A faculty member from Florida State University has been recognized as the 2025 Mohamed Ali Foundation Fellow by Durham University to delve deeper into the institution’s archives, antiquarian manuscripts, and unique documents related to Middle Eastern and Islamic studies. Associate Professor of History Will Hanley’s research investigates Egypt’s involvement in global frameworks, accentuating contributions from…
-
Four MSU researchers named AAAS Fellows
-
WashU Transitions Training Programs to Workday Learning Platform

WashU is currently in the process of transferring training and courses from Learn@Work to Workday. The subsequent group to shift their educational content to Workday Learning, starting April 14, comprises LinkedIn Learning, University Advancement, WashU Information Technology, the Brown School, the Department of Anesthesiology at WashU Medicine, and additional entities. The initiative aims to transfer…
-
University Approves Comprehensive Policy for Expressive Activities

Cornell has established its policy regulating demonstrations and other forms of expressive actions, concluding a lengthy examination that involved participants from all its campuses.
-
Critical Vulnerabilities Found in Solar Inverters from Sungrow, Growatt, and SMA: 46 Flaws Identified
Cybersecurity analysts have revealed 46 fresh security weaknesses in offerings from three solar inverter manufacturers, Sungrow, Growatt, and SMA, which could be manipulated by malicious entities to gain command of devices or carry out code execution from a distance, presenting significant dangers to power grids. The flaws have been jointly designated as SUN:DOWN by Forescout…
-
Naming Regions: How Place Names Are Shaping Political Narratives Across America
Altering a location’s designation can profoundly transform how individuals perceive, connect to, or sense their belonging within that locale. The article The Conversation: From Greenland to Fort Bragg, America Is Caught in a Name Game Where Place Names Become Political Tools was first published on News.
-
UK’s Phi Beta Kappa chapter inducts 55 new members

-
KCH patient’s strength runs on love, Legos and lifesaving blood

-
Celebrate like a champion: NCAA Tournament safety reminders
-
Temporary road closure planned for Huguelet Drive
-
The Joint Commission names UK HealthCare a Level IV maternal care verified facility

-
Breathitt Lecture to explore relationship between social issues, architecture
-
UK receives NASPA Gold Award for student retention efforts
-
Celebrating Local Collaborations: The Impact of the Sahm Awards on UGA Partnerships

The University of Georgia is enhancing its dedication to collaborating with Athens-Clarke County organizations via an endowment initiated by Athens native and UGA alumna Bobbi Meeler Sahm and her family. Four joint local initiatives between UGA and Athens-Clarke County organizations have been chosen to receive a combined total of $35,000 as part of the Bobbi…
-
CoffeeLoader Employs GPU-Powered Armor to Outsmart EDR and Antivirus Systems

Cybersecurity analysts are highlighting a new advanced malware named CoffeeLoader that is crafted to retrieve and run tertiary payloads. According to Zscaler ThreatLabz, this malware exhibits behavioral resemblances to another recognized malware loader referred to as SmokeLoader. “The objective of the malware is to obtain and execute subsequent payloads while avoiding
-
The Dual Chronicles of Deceptive Domains
In phishing and malspam, similar to any other domain, one can observe specific trends emerging over time. For clear reasons, the majority of threat actors prefer to utilize strategies and methods that are innovative and, therefore, more efficient. This typically results in the simultaneous adoption of identical strategies and technologies by various threat actors, which…
-
Unleashing Resilience: A Comprehensive Guide to Datto BCDR and Unmatched Business Continuity

Far behind us are the times when a basic backup in a data center sufficed to ensure a company’s safety. Although backups retain data, they do not assure operational continuity during emergencies. Given that IT calamities are excessively frequent and downtime consumes financial resources, contemporary IT landscapes necessitate alternatives that transcend mere storage and facilitate…
-
AIs: The New Trusted Mediators in Our Digital World

This is an exceptionally engaging document: “Reliable Machine Learning Models Enable Private Inference for Issues Currently Unmanageable with Cryptography.” The core concept is that AIs can serve as trusted intermediaries: Abstract: We frequently engage with unreliable entities. Emphasis on privacy can hinder the productivity of these interactions, as achieving certain objectives requires the exchange of…
-
Deceptive Chat Apps: The PJobRAT Malware Scheme Aimed at Taiwanese Users

An Android malware group previously noted for focusing on Indian military staff has been associated with a fresh initiative presumably directed at users in Taiwan masquerading as chat applications. “PJobRAT has the capability to extract SMS texts, contact lists, device and application details, documents, and multimedia files from compromised Android devices,” stated Sophos security expert…
-
Nine-Year-Old npm Packages Compromised to Steal API Keys with Concealed Scripts

Cybersecurity analysts have identified multiple cryptocurrency packages on the npm registry that have been compromised to extract sensitive data like environment variables from affected systems. “Several of these packages have existed on npmjs.com for more than 9 years and offer authentic features to blockchain developers,” noted Sonatype investigator Ax Sharma. “Nevertheless, […] the most recent
-
Mozilla Addresses Severe Firefox Flaw Echoing Recent Chrome Zero-Day Issue

Mozilla has launched updates to tackle a significant security weakness affecting its Firefox browser for Windows, just days after Google remedied a comparable issue in Chrome that had been actively exploited as a zero-day vulnerability. The security vulnerability, identified as CVE-2025-2857, has been characterized as an instance of an improper handle that could result in…
-
Essential Salesforce Interview Questions and Answers: The Ultimate Guide

The greater our experience, the more we learn to appreciate that the inquiries we make or the responses we provide during an interview reveal a significant amount about our passion and level of engagement with a product, enterprise, or organization. This is certainly true for Salesforce, the most powerful Customer Relationship Management (CRM) solution globally.…
-
Mastering Cloud Inventory Management: A Comprehensive Guide

Harness the capabilities of effective inventory oversight with our all-encompassing guide to cloud-hosted solutions. Delve into the advantages, attributes, and execution tactics of cloud-hosted inventory management systems to enhance operations, refine inventory quantities, and elevate your enterprise’s efficiency and profitability. What is Cloud Inventory …Read More.
-
Finding the Perfect AWS Professional for Your Company

Within the realm of cloud technology, Amazon Web Services (AWS) leads the way with a 47.1 percent share of the cloud services market. This indicates that the AWS cloud infrastructure supports hundreds of thousands of enterprises across 190 nations. Such a robust position in the industry has resulted in a similarly high demand for personnel,…
-
DigitalOcean vs Linode: An In-Depth Look at Cloud Hosting Solutions

In today’s online environment, those seeking expandable and dependable infrastructure for their websites and applications depend on cloud hosting. Two major contenders in the cloud hosting market are DigitalOcean and Linode. They provide not only a variety of cloud solutions but also serve as suppliers of Virtual Private Servers (VPS). This is a comp…Read More.
-
Top Animation Software to Bring Your Concepts to Life

Animation has revolutionized the way we express, amuse, and instruct. Animation software has become crucial in unlocking creativity and originality, from producing blockbuster films to creating captivating marketing strategies. These applications empower designers, artists, and even enthusiasts to manifest their concepts, making them attainable in various sectors. Wh…Discover More.
-
CISSP Exam Takes a Digital Leap: Simplilearn Offers New Online Format

Exciting announcement for individuals aiming for the CISSP examination. The CISSP exam timetable is now accessible on the internet. This opens up an opportunity for individuals to undergo digital assessments through Computer-Based Testing (CBT) at local examination venues around the globe. Candidates can now enroll and complete the test on the same day (depending on…
-
Essential Skills and Responsibilities of a Cloud Computing Engineer

Notable Insights Cloud computing engineers play a crucial role in transforming the way businesses manage information, leveraging cloud technologies for advancement and creativity. Their duties encompass developing and administering cloud-based services, supervising data storage, offering assistance, and resolving technical issues. A background in computer science is…Read More.
-
Soaring into Your Future: Launching a Career in the Aerospace Industry

You’re an aerospace designer racing against the clock to create a component for a rocket engine. No problem, you muse — you know the principles inside out, and the model appears suitable in CAD. However, upon examining the 3D-printed item you’ve contracted for production, you notice a flaw. The angle of the impeller blades is…
-
ISC Stormcast For Friday, March 28th, 2025 https://isc.sans.edu/podcastdetail/9384, (Fri, Mar 28th)

-
Hormone Therapy Linked to Reduced HIV Risk in Transgender Individuals, University of Michigan Research Reveals

Research: HIV seropositivity and viral non-suppression in transgender, non-binary, and gender-diverse individuals in primary healthcare receiving gender-affirming hormone therapy in the USAduring 2013 to 2019 (LEGACY): An observational, longitudinal cohort study (DOI: 10.1016/S2352-3018(25)00004-9) Perspective article: The Situated Vulnerabilities and Resiliencies Framework: A plea for integrated approaches to tackle global HIV disparities for transgender, non-binary, and…
-
Dartmouth Welcomes 1,702 New Undergraduates into Its Academic Community

Over 1 in 4 members of the Class of 2029 are eligible for complimentary tuition.
-
Tuition and Housing Costs for 2025-26 Unveiled: Details on Meal Plans and Associated Fees

Undergraduate fees for the academic year 2025-26 for scholars not receiving financial assistance at Washington University in St. Louis will be $68,240, reflecting an increase of $3,740 from the current rate of $64,500, as stated by Beverly Wendland, provost and executive vice chancellor for academic affairs. Rates for a shared accommodation for these students will…
-
Esteemed Tropical Plant Biodiversity Scholars Join Forces with WashU and Missouri Botanical Garden

Drawing from a rich legacy of effective partnership, Washington University in St. Louis and the Missouri Botanical Garden are welcoming two globally acknowledged botanists who will serve in dual roles at both research entities. Lúcia Lohmann, a botanist and advocate for conservation recognized for her in-depth research in the Amazon rainforest, assumed the role of…
-
Class of 2029: Where Passions Ignite Knowledge

Through community service, investigation, and promoting awareness, the 5,824 individuals accepted into the Class of 2029 embody Cornell’s dedication to transforming lives via civic involvement.
-
Yale Welcomes 2,308 New Faces to the Class of 2029

The candidates come from every one of the 50 states, 65 nations, and 1,586 secondary educational institutions.
-
The Southern Ocean Cools: The Impact of Melting Ice and Increased Rainfall

Researchers from Stanford discovered that heightened meltwater and precipitation account for 60% of a prolonged discrepancy between forecasted and actual temperatures in the waters surrounding Antarctica.
-
Glucose Unveiled: The Remarkable Influence on Tissue Development

The finding, rooted in comprehensive research from Stanford Medicine, holds significance for the management of diabetes and cancers.
-
Yale Representatives Collaborate with Connecticut Leaders During Exciting India Expedition

Yale’s vice provost for research, Michael Crair, accompanied Connecticut Governor Ned Lamont on a recent trip to India to interact with prominent researchers in quantum computing and to investigate potential partnerships.
-
Unlocking Imagination: A Journey Through Creative Exploration

The newly introduced Yale Engineering class “Discovering Yourself in the Future of Creativity” was crafted for budding entrepreneurs, upcoming leaders, and visionaries who aim to comprehend and enhance their imaginative capabilities to create a significant influence.
-
Empowering Young Minds: Introducing Business Education to New Haven Youth

Edward Chiu ’25 M.B.A. participated with SOM volunteers in a yearly service event aimed at instructing local elementary students on financial literacy skills.
-
Revolutionary Techniques for Tracking Subtle Transformations in Plant Cells

A multidisciplinary group spearheaded by Yale has created an innovative laser-focused technique for monitoring how vegetation modifies the pressure inside their cells in reaction to environmental conditions. This advancement may assist in devising strategies for agriculturists dealing with heightened drought challenges.
-
“Revolutionary Advances in Prostate Cancer Treatment Through Image-Guided Techniques”
A more affordable, readily available, and convenient option is available for individuals undergoing a prostate cancer biopsy, as indicated by results from a recent clinical investigation.
-
“Porcelain Perspectives: A Contemporary Twist on Orthodox Iconography at Yale ISM”

“Noah’s Garden: The Porcelain Realms of Svetlozar Parmakov,” a fresh art showcase at the Yale Institute of Sacred Music, highlights the stunning porcelain icons, artworks, and ornamental vessels by the illustrious Bulgarian artist.
-
Harnessing AI and iPhones, UC Berkeley Student’s Groundbreaking Startup Seeks to Recognize Stroke Symptoms and Save Lives

Through the use of smartphones, computers, and various advanced devices, Ashmita Kumar’s venture intends to revolutionize stroke healthcare, with bold aspirations for expansion. The article With AI and an iPhone, UC Berkeley student’s startup aims to detect stroke signs and save lives was first published on Berkeley News.
-
Charting the Path Ahead for Metamaterials
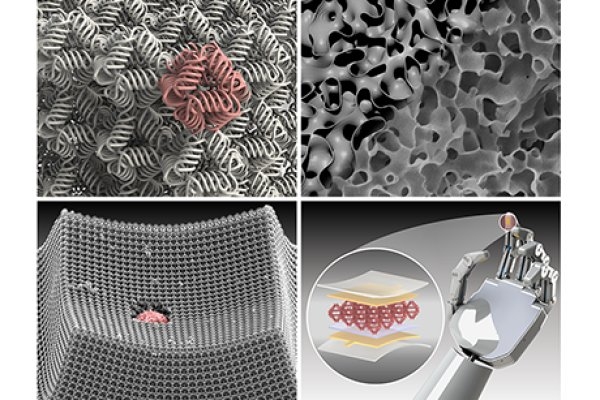
Metamaterials are synthetically-engineered substances with remarkable attributes that are not commonly available in nature. With designed three-dimensional (3D) shapes at the micro and nanoscale, these structured materials possess distinct mechanical and physical characteristics that surpass those of traditional materials — and have emerged over the last decade as a promising solution to engineering problems where…
-
Celebrating Achievement: MIT’s Inspiring Commencement Ceremony on May 27, 2022

The OneMIT Graduation Ceremony is scheduled for Friday, May 27 at 10:00 a.m. on Killian Court, situated off Memorial Drive. This year’s keynote speaker is MIT graduate Ngozi Okonjo-Iweala MCP ’78, PhD ’81, the director-general of the World Trade Organization (WTO) and former finance minister of Nigeria. A specialist in global finance, economics, and international development, Okonjo-Iweala…
-
The Enigmatic Quest of the Architect-Detective in Medieval Times
Arts & Culture A detective/architect’s medieval enigma Photos by Justin Knight Sy Boles Harvard Staff Writer March 27, 2025 6 min read Exhibit details scholar’s pursuit to reconstruct abbey ruined after French Revolution Cluny III, once the most expansive structure in Europe, was reduced to mere debris by the time Harvard architectural historian Kenneth Conant…
-
The Remarkable Journey of Kaitlyn Thomas: A Rising Star

Kaitlyn Thomas, a junior at Florida State University majoring in food and nutrition science, applies the insights acquired from her studies to contribute to the local community. She collaborates with Remote Area Medical (RAM) clinics, a community dental practice, and FSU University Health Services to facilitate accessible dental care for diverse demographics. Thomas also instructs…
-
University of Michigan Unveils Significant Revisions to DEI Initiatives

Following numerous months of intense dialogue and introspection involving various stakeholders within and outside the university, the University of Michigan is proceeding with significant modifications to its programs related to diversity, equity, and inclusion. The alterations, detailed in a March 27 email from university leaders to the Ann Arbor and Michigan Medicine communities, encompass the…
-
Decoding the Role of Immune Cells in Renal Health and Disease

In a Q&A, Irene Chernova from the Yale School of Medicine explores the effects of lupus on the renal system and the significance of B cells in lupus nephritis.
-
Caltech Researchers Unveil Groundbreaking Superconducting Phase
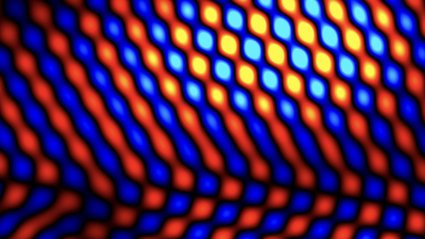
Superconductivity represents a quantum physical condition wherein a metal can conduct electricity flawlessly without any resistance. Its most recognized application is in enabling potent magnets in MRI machines to generate the magnetic fields necessary for medical professionals to visualize the interior of our bodies. Up to now, substances have only been able to attain superconductivity…
-
MIT Members Recognized as 2024 AAAS Fellows

Six present MIT members and 27 former MIT graduates have been selected as fellows of the American Association for the Advancement of Science (AAAS). The 2024 cohort of AAAS Fellows consists of 471 researchers, engineers, and innovators across all 24 AAAS disciplinary sections, who are being acknowledged for their significant scientific and societal accomplishments. Noubar…
-
MIT Unveils New Initiative for Health and Life Sciences Collaboration

To tackle some of society’s most urgent health issues, MIT President Sally Kornbluth is initiating the MIT Health and Life Sciences Collaborative, a fresh endeavor intended to leverage the unified strength of researchers from disciplines like engineering, science, AI, economics, business, policy, design, and the humanities to create transformative health solutions. By stimulating partnerships in…
-
MIT Economists Daron Acemoglu and Simon Johnson Awarded Nobel Prize in Economics

The Massachusetts Institute of Technology will conduct a virtual press briefing featuring Prof. Daron Acemoglu, Prof. Simon Johnson, and President Sally Kornbluth later this morning at 10:00 AM ET in light of the announcement that Acemoglu and Johnson have been awarded the Nobel Prize in Economics for their research on “how institutions are created and…
-
Exploring the Horizon of Generative AI Innovations

What might the future resemble in a realm enriched by generative AI technologies? Spanning health and commerce to art and education, the swift evolution of generative AI technologies introduces distinct obstacles concerning how to adeptly navigate the effects of AI systems and guarantee that emerging AI technologies are accountable and dependable. From November 28-30, journalists…
-
Moungi G. Bawendi of MIT Triumphs with Nobel Prize in Chemistry

The Massachusetts Institute of Technology will conduct a virtual press briefing with Professor Moungi G. Bawendi and President Sally Kornbluth later this morning at 10:30 AM ET, following the announcement made earlier today that Bawendi received one-third of the Nobel Prize in Chemistry for his contributions to “the discovery and synthesis of quantum dots.” Before…
-
A Celebration of Achievement: MIT’s Commencement Ceremony on June 1, 2023

The OneMIT Graduation Ceremony is scheduled for Thursday, June 1 at 3:00 P.M. on Killian Court, which is situated off Memorial Drive. This year’s keynote speaker is Mark Rober. Rober, an engineer from NASA who has transitioned to internet stardom, runs a YouTube channel that champions creativity, persistence, and the thrill of education. His videos…
-
Enhancing Accessibility to Higher Education for Students in Pakistan
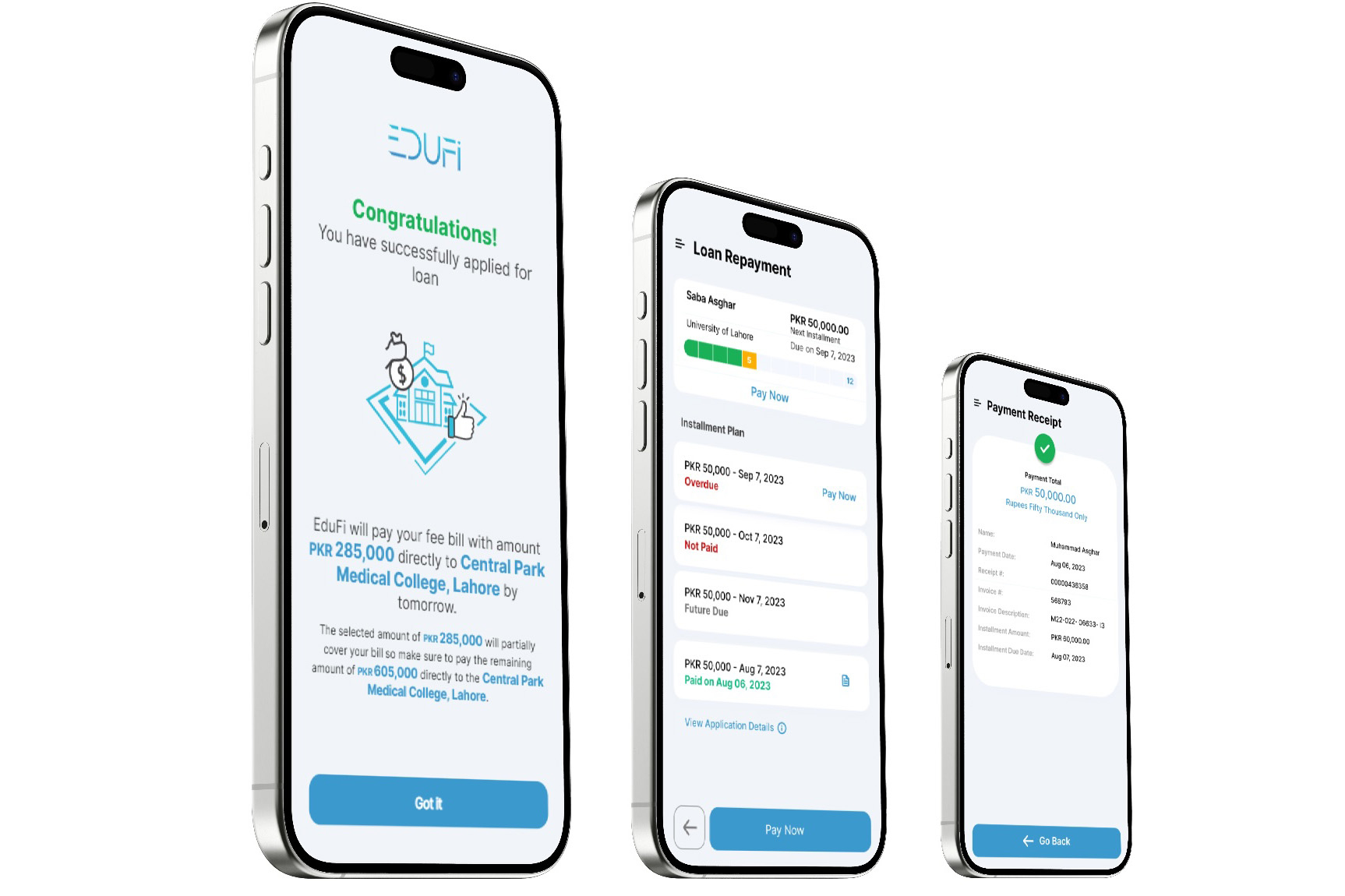
Securing a loan to pursue higher education is a valuable investment in your future. However, unlike in the United States, students in Pakistan face challenges in accessing educational loans. Most families end up dealing with elevated interest rates for personal loans that may necessitate collateral like property or real estate. Consequently, many students find college…
-
Rakesh Khurana’s Journey: Insights Gained from Leadership and Digital Influence
Photographs by Grace DuVal Campus & Community Rakesh Khurana reflects on experiences gained while leading — both as a mentor and an influencer, online and offline Melih Cevik ’27 Harvard Correspondent March 27, 2025 long read Danoff Dean of Harvard College to resign at conclusion of academic year after 11 years of progress, innovation, and…
-
Animating Ancestry: Transforming the Family Tree into a Cinematic Experience
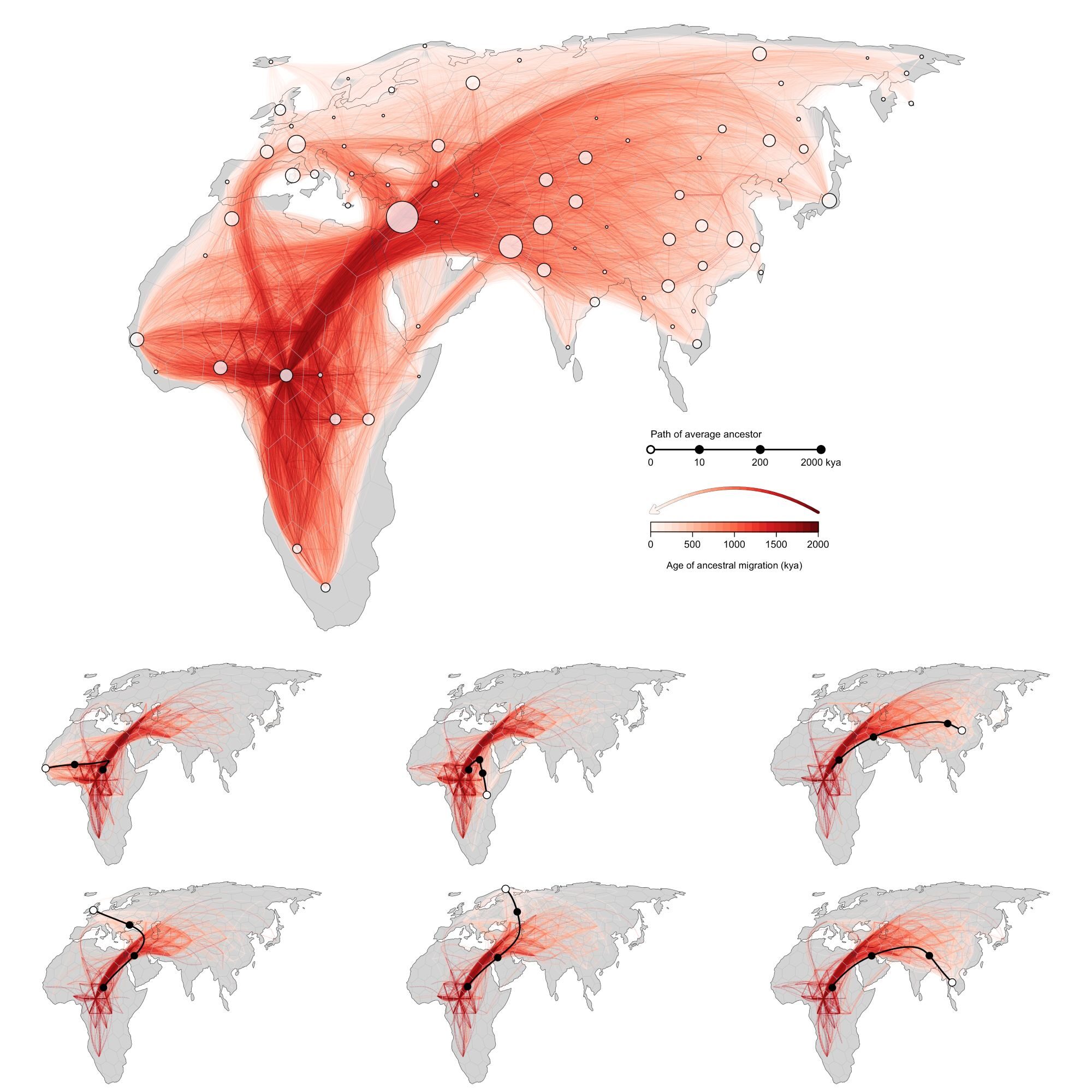
A georeferenced genealogical recombination graph. Red lines illustrate the suggested historical migrations of genetic forebears of the sample (white points), with darker shading applied to indicate movements that occurred in more distant eras. Image credit: Gideon Bradburd, Michael Grundler, and Jonathan Terhorst, University of Michigan Research: A geographical record of human genetic heritage (DOI: 10.1126/science.adp4642)…
-
Three Faculty Members from UT Inducted into the American Association for the Advancement of Science

AUSTIN, Texas — Three educators from The University of Texas at Austin have been chosen for the 2024 American Association for the Advancement of Science (AAAS) Fellows cohort. AAAS fellowships are a prestigious lifelong accolade awarded for significant and ongoing accomplishments in support of the advancement of science or its practical applications. Molecular biosciences […] The…
-
Latino Entrepreneurs: A Decade of Growth and Innovation

The 10th yearly State of Latino Entrepreneurship report reveals sustained expansion – with the quantity of Latino-operated enterprises rising by 44% – alongside an emerging emphasis on AI and sustainability.
-
Innovative Phishing Scam: Morphing Meerkat Tool Imitates 114 Brands by Exploiting Victims’ DNS Email Data

Cybersecurity analysts have illuminated a fresh phishing-as-a-service (PhaaS) platform that utilizes the Domain Name System (DNS) mail exchange (MX) records to deliver counterfeit login pages that mimic approximately 114 brands. DNS intelligence company Infoblox is monitoring the entity responsible for the PhaaS, the phishing toolkit, and the associated activities under the alias Morphing Meerkat. “The…
-
“Unpacking the Threat: Sitecore’s ‘thumbnailsaccesstoken’ Vulnerability and CVE-2025-27218”

On March 6th, Searchlight Cyber released a blog disclosing particulars concerning a recent deserialization vulnerability in Sitecore [1]. Sitecore refers to itself as a “Digital Experience Platform (CXP),” essentially an advanced content management system (CMS). The framework of Sitecore is built in .Net and is frequently marketed as a component of a solution provided by…
-
Andrea Bocelli’s Lexington debut to benefit UK Markey Cancer Center
-
Advancing Kentucky Together: UK alum driven by passion, purpose

-
Fueling sleep: UK researchers show key metabolic link to restful nights

-
UK Symphony Orchestra presents a world premiere and Mahler’s Fifth Symphony

-
DanceBlue celebrating 20 years of spreading joy, supporting pediatric cancer clinic

-
‘UK at the Half’: New downtown studio provides collaboration, hands-on learning opportunities
-
UK encourages on-farm conservation through conversations at One Good Idea Shop Talks

-
Supplemental Instruction sees record-breaking year of utilization

-
Chasing Clues: An FSU Professor Explores Agatha Christie’s Hawaiian Adventures
Michelle Kazmer serves as the dean of Florida State University’s College of Communication and Information. Additionally, she holds a professorship in the School of Information and is a prominent authority on crime fiction writer Agatha Christie, particularly from the Golden Age. Kazmer is a foremost specialist in how Christie incorporates information theories into her narratives;…
-
Revolutionary Microparticles Developed by FAMU-FSU College of Engineering Researchers Illuminate Protein Degradation and Immune Cell Dynamics
Researchers at FAMU-FSU College of Engineering have developed a novel technique for examining protein degradation within immune cells that employs engineered microparticles to monitor and evaluate degradation processes more efficiently than conventional approaches. This research, published in ACS Applied Materials & Interfaces, holds significant ramifications for the treatment of conditions such as cancer, Alzheimer’s disease,…
-
MSU researchers identify why 911 calls are delayed, failed, or dropped
-
“Revving Up Innovation: Michigan’s Journey to Becoming the E-Motor Capital”

MEDIA NOTICE DATE: April 1 from 4-7:30 p.m. and April 2 from 8 a.m.-4 p.m., 2025 EVENT: Key technologies and pressing matters influencing the future of electric vehicles and transport will be examined at the University of Michigan Electric Vehicle Center Symposium 2025. This two-day gathering will convene stakeholders from industry, government, and academia. Presentations…
-
Celebrating Excellence: 13 U-M Faculty Inducted as 2024 AAAS Fellows

Thirteen faculty members from the University of Michigan have been elected to the American Association for the Advancement of Science for the year 2024. The AAAS, recognized as the largest general scientific organization globally, disclosed the selection of 471 individuals for the 2024 cohort, honored for their “commitment to the advancement of science, or its…
-
Yale Faculty Honored as AAAS Fellows: A Celebration of Scientific Excellence

The American Association for the Advancement of Science has chosen eight faculty members from Yale to join its newest cohort of fellows.
-
Imagining Tomorrow: The Role of Science Fiction in Shaping Our Future

In a discussion, Annalee Newitz, the pioneering “creator-in-residence” for a fresh Yale initiative named “Sci X Sci-Fi,” articulates how speculative fiction can illuminate the path toward a flourishing future.
-
Unveiling the Future of E-Commerce: An Insight with Ph.D. Student Nicholas Wu

An ongoing investigation that Wu collaborated on alongside Yale economics academic Dirk Bergemann examines the data-driven processes through which significant online platforms such as Google, Meta, and Amazon connect consumers with advertisers.
-
Harnessing Lupus Antibodies for Enhanced Cancer Therapies

A Yale investigation presents fresh discoveries that may enhance treatments for glioblastoma and other fierce malignancies that are challenging to manage.
-
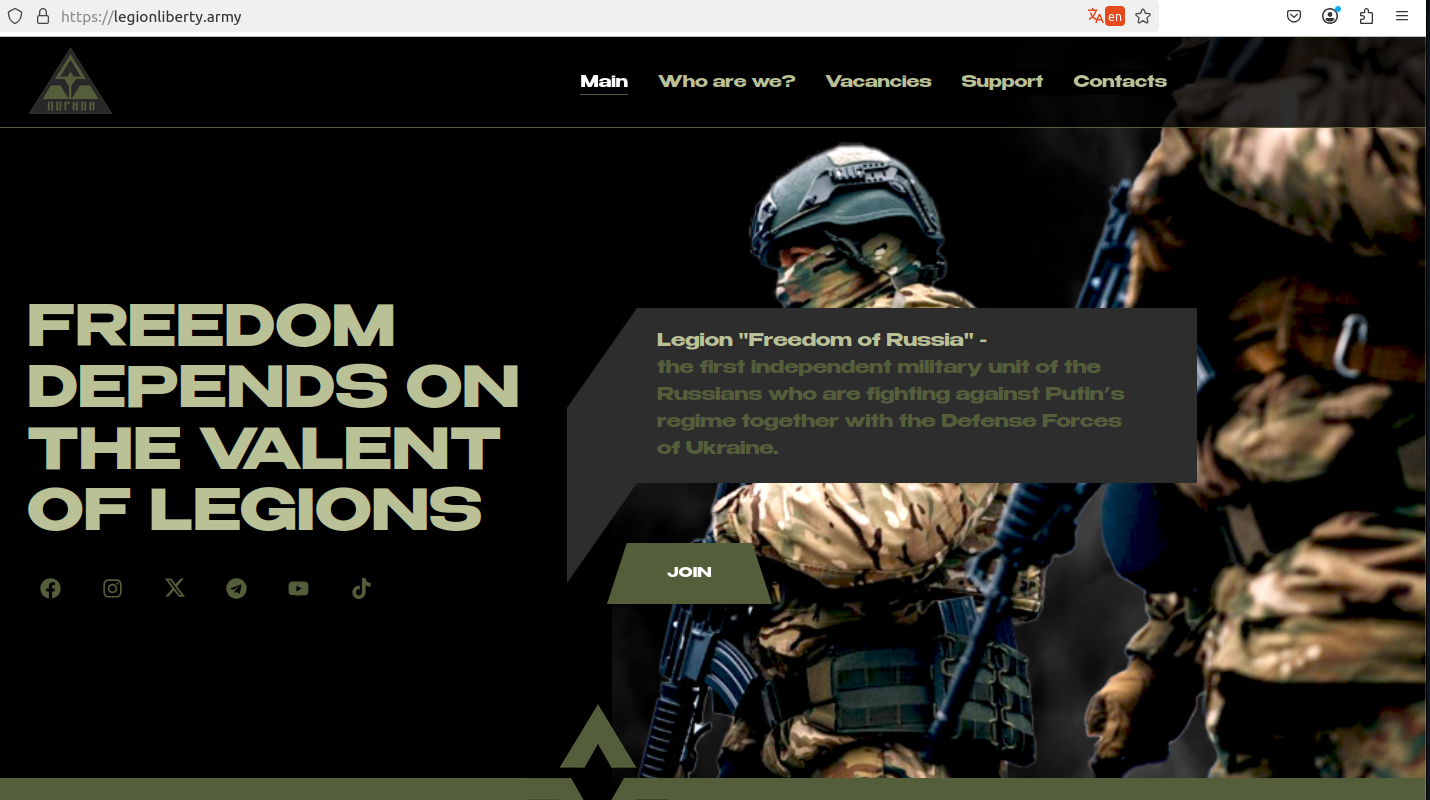
Phishing Threats: When Cyber Deception Takes a Deadly Turn
A multitude of effective phishing schemes lead to monetary losses or malware infiltration. However, falling victim to certain phishing cons, particularly those currently aimed at Russians seeking information about organizations opposing the Kremlin’s military actions, could endanger both your liberty and your life. The authentic website of the Ukrainian paramilitary group “Freedom of Russia” legion.…