“`html
On July 22, 2025, the European law enforcement agency Europol announced that a lengthy inquiry spearheaded by the French authorities led to the detainment of a 38-year-old operator of XSS, a cybercrime forum in Russian with over 50,000 members. This operation has sparked a wave of conjecture and anxiety among XSS users regarding the identity of the undisclosed individual, but the prevailing belief is that he is a crucial player in the cybercrime forum arena, known by the hacker moniker “Toha.” Below is a comprehensive exploration of what is known about Toha, alongside a brief look at who was apprehended.

An unidentified 38-year-old male was detained in Kiev last month under suspicion of managing the cybercrime forum XSS. Image: ssu.gov.ua.
Europol did not disclose the suspect’s name but released blurred photographs taken during the raid at his residence in Kiev. The police agency indicated that the suspect acted as a reliable intermediary — settling disputes among criminals — and ensuring the safety of transactions on XSS. A declaration from Ukraine’s SBU security service noted that XSS included among its membership numerous cybercriminals from various ransomware factions, including REvil, LockBit, Conti, and Qiliin.
Following the Europol statement, the XSS forum reappeared at a new location on the deep web (accessible solely via the anonymity network Tor). However, upon reviewing the recent entries, there seems to be little agreement among veteran members regarding the identity of the detained XSS operator.
The most common remark concerning the arrest was an expression of solidarity and encouragement for Toha, the alias adopted by the long-standing administrator of XSS and multiple other prominent Russian forums. Toha’s profiles on other forums have remained inactive since the raid.
Europol stated that the suspect had a nearly 20-year history in cybercrime, which aligns closely with Toha’s timeline. In 2005, Toha became a founding member of the Russian-speaking forum Hack-All. That is, until it was severely compromised a few months after its launch. In 2006, Toha rebranded the forum to exploit[.]in, which would go on to attract tens of thousands of users, including a veritable Who’s Who of sought-after cybercriminals.
Toha declared in 2018 that he was selling the Exploit forum, inciting rampant speculation on various forums that the buyer was covertly a Russian or Ukrainian governmental entity or a front figure. Nonetheless, these suspicions lacked corroborative evidence, and Toha fervently denied the forum’s transfer to any authorities.
One of the earliest Russian-language cybercrime forums was DaMaGeLaB, which functioned from 2004 until 2017, when its administrator “Ar3s” was detained. In 2018, a partial backup of the DaMaGeLaB forum was revived as xss[.]is, with Toha listed as its administrator.
CROSS-SITE GRIFTING
Information regarding Toha’s early online presence — from approximately 2004 to 2010 — is accessible in the archives of Intel 471, a cyber intelligence organization monitoring forum activity. Intel 471 indicates that Toha utilized the same email address across various forum accounts, including at Exploit, Antichat, Carder[.]su, and inattack[.]ru.
DomainTools.com reveals that Toha’s email address — [email protected] — was employed to register at least a dozen domain names — the majority from the mid- to late 2000s. Aside from exploit[.]in and a domain named ixyq[.]com, the remaining domains pinned to that email address conclude with .ua, the top-level domain for Ukraine (e.g. deleted.org[.]ua, lj.com[.]ua, and blogspot.org[.]ua).
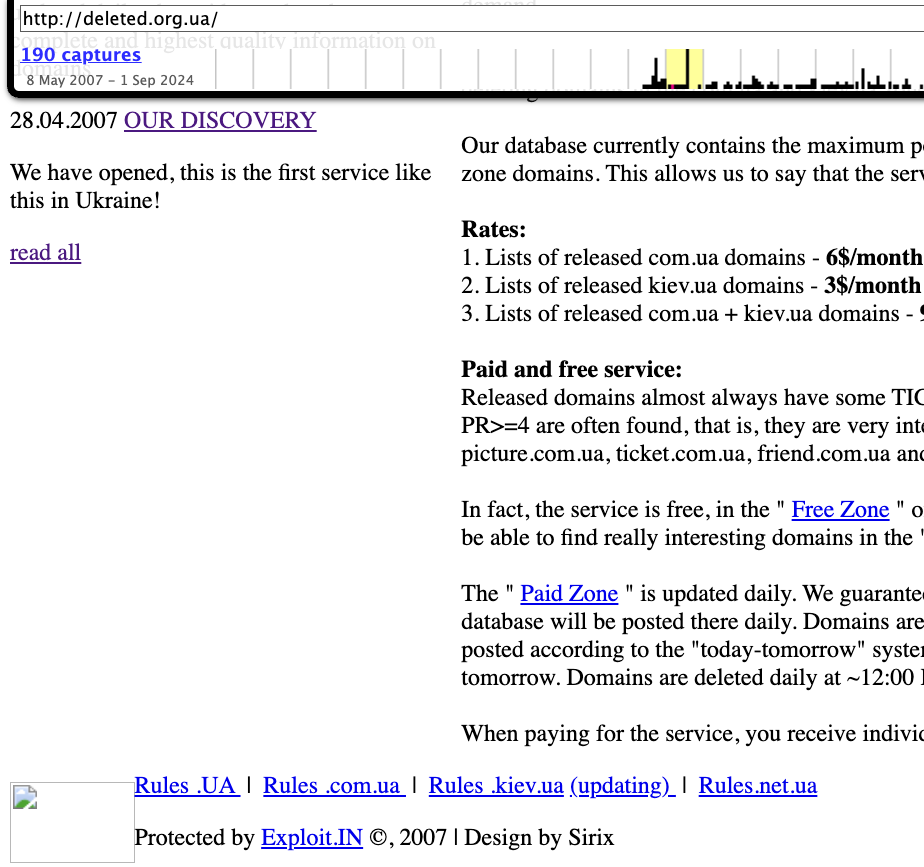
A 2008 snapshot of a domain registered to [email protected] and to Anton Medvedovsky in Kiev. Note the message at the bottom left, “Protected by Exploit,in.” Image: archive.org.
Almost all of the domains registered to [email protected] list the name Anton Medvedovskiy in the registration records, except for the previously mentioned ixyq[.]com, which is registered to Yuriy Avdeev in Moscow.
This Avdeev surname was mentioned in an extensive discussion with Lockbitsupp, the leader of the greedy and damaging ransomware affiliate group Lockbit. The dialogue occurred in February 2024, when Lockbitsupp sought assistance in identifying Toha’s true identity.
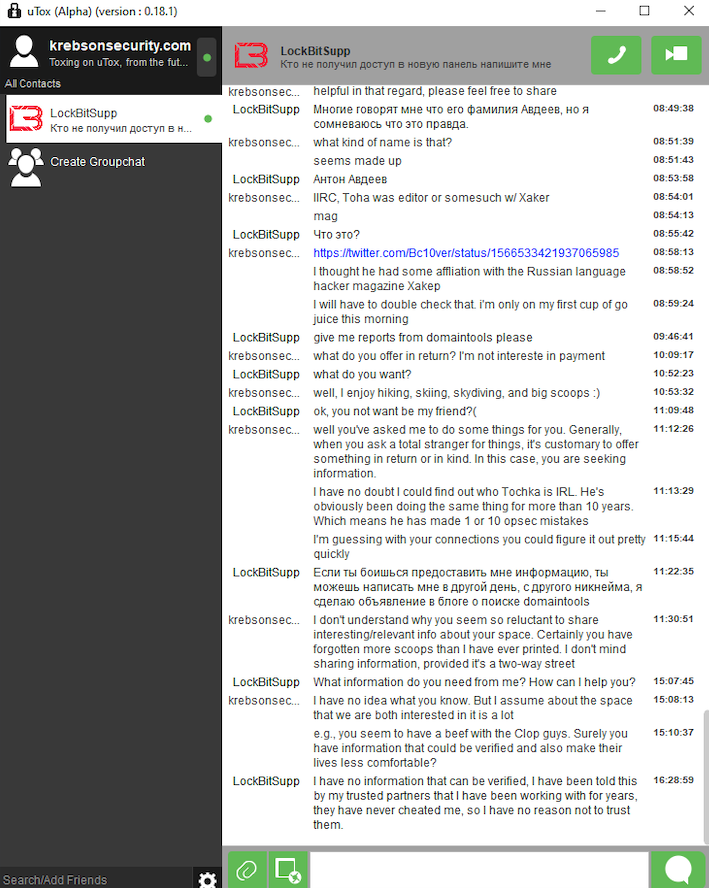
In early 2024, the head of the Lockbit ransomware group — Lockbitsupp — sought assistance in uncovering the identity of the XSS administrator Toha, whom he believed to be a Russian individual named Anton Avdeev.
Lockbitsupp did not disclose his reasons for wanting Toha’s information, but he insisted that Toha’s actual name was Anton Avdeev. I declined to assist Lockbitsupp in any potential retribution he may have been contemplating against Toha, but his inquiry piqued my interest to delve deeper.
This inquiry appeared to stem from a now-removed Twitter post from 2022, when a user named “3xp0rt” claimed that Toha was a Russian individual named Anton Viktorovich Avdeev, born on October 27, 1983.
Searching online for Toha’s email address [email protected] leads to a 2010 sales thread on the forum bmwclub.ru where a user identified as Honeypo was offering a 2007 BMW X5 for sale. The listing identified the contact person as Anton Avdeev and provided the contact phone number 9588693.
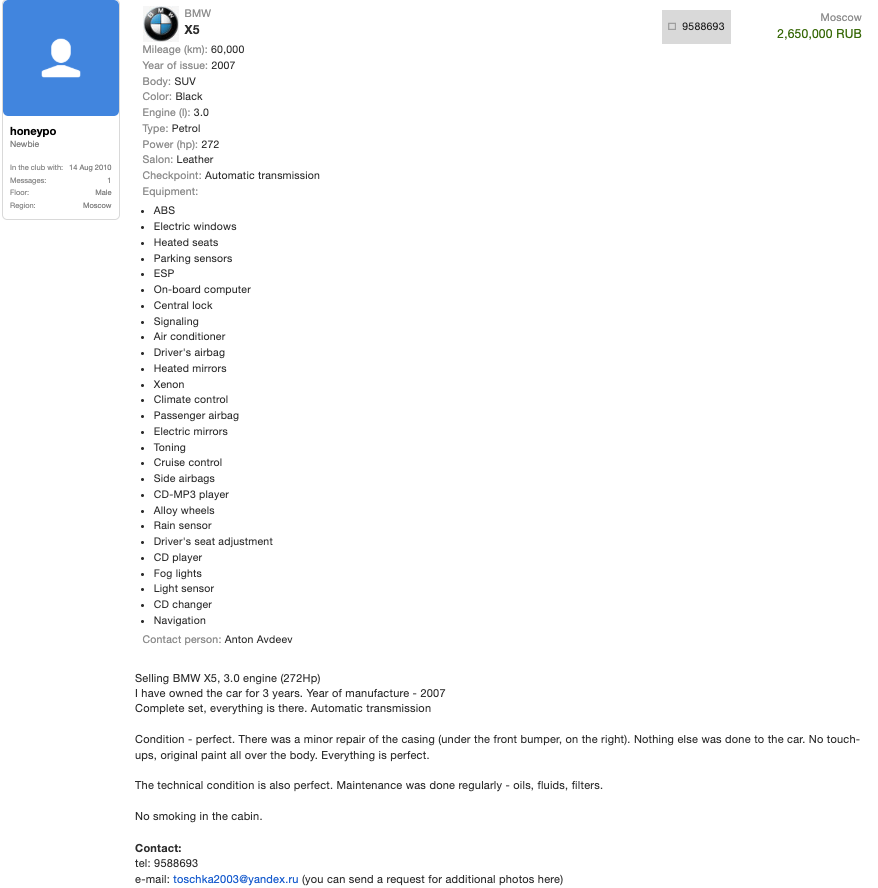
A search for the phone number 9588693 in the breach tracking service Constella
“`**Intelligence** finds numerous official Russian governmental records associated with this identifier, date of birth, and the name Anton Viktorovich Avdeev. For instance, breached Russian government documents reveal that this individual possesses a Russian tax ID and SIN (Social Security number), and has been noted for traffic infractions on multiple occasions by Moscow authorities—in 2004, 2006, 2009, and 2014.
Observant readers may have recognized that the ages of Mr. Avdeev (45) and the XSS administrator apprehended this month (38) differ significantly. This discrepancy implies that the individual detained may not be Mr. Avdeev, who did not respond to inquiries for a statement.
A FLY ON THE WALL
To gain additional perspective on this matter, KrebsOnSecurity reached out to Sergeii Vovnenko, a former cybercriminal from Ukraine who is now heading the security startup paranoidlab.com. I contacted Vovnenko because, for several years beginning around 2010, he was the proprietor and operator of thesecure[.]biz, an encrypted “Jabber” instant messaging server that Europol stated was run by the suspect detained in Kiev. Thesecure[.]biz gained popularity among many prominent Russian-speaking cybercriminals due to its meticulous minimal record-keeping of user activities, and its administrator was always a trusted figure within the community.
The reason I recall this historical detail is that in 2013, Vovnenko—using the hacker aliases “Fly” and “Flycracker”—devised a scheme to arrange for a gram of heroin to be purchased from the Silk Road darknet marketplace and sent to our residence in Northern Virginia. The plan was to imitate a call from one of our neighbors to local law enforcement, suggesting that a person named Krebs down the street was a drug user having narcotics delivered to his home.
I happened to be monitoring Flycracker’s private cybercrime forum when his heroin-framing scheme was enacted, and I called the authorities myself before the package eventually entered the U.S. Postal Service. Vovnenko was later captured for unrelated cybercriminal activities, extradited to the United States, convicted, and subsequently deported after spending 16 months in the U.S. prison system [on multiple occasions, he has expressed sincere apologies for the incident, and we have since reconciled].
Vovnenko mentioned that he acquired a device for cloning credit cards from Toha in 2009, which Toha shipped from Russia. Vovnenko clarified that he (Flycracker) operated thesecure[.]biz from 2010 until his arrest in 2014.
Vovnenko suspects that thesecure[.]biz was commandeered while he was incarcerated, potentially by Toha and/or an XSS administrator known by the nicknames N0klos and Sonic.
“While I was imprisoned, [the] admin of xss.is took that domain, or possibly N0klos acquired XSS from Toha or the other way around,” Vovnenko stated regarding the Jabber domain. “No one from [the forums] communicated with me post-incarceration, so I can only speculate about what indeed transpired.”
N0klos was the owner and administrator of an early Russian-language cybercrime forum called Darklife[.]ws. Nonetheless, N0klos also appears to have been a lifelong resident of Russia, and has seemingly disappeared from Russian cybercrime forums several years prior.
When asked if he believes Toha was the XSS administrator arrested this month in Ukraine, Vovnenko asserted that Toha is Russian and that “the French authorities apprehended the wrong individual.”
WHO IS TOHA?
So, whom did the Ukrainian enforcement agencies detain in relation to the investigation led by the French authorities? It seems reasonable that the BMW advertisement referencing Toha’s email address along with the name and phone number of a Russian citizen was merely a diversion on Toha’s part—aimed at misleading and confounding investigators. Perhaps this also elucidates the emergence of the Avdeev surname in the registration documents linked to one of Toha’s domains.
Nevertheless, sometimes the most straightforward explanation is indeed the accurate one. “Toha” is a prevalent Slavic nickname for individuals named “Anton,” which aligns with the name in the registration records for over a dozen domains associated with Toha’s [email protected] email address: Anton Medvedovskiy.
Constella Intelligence identifies an Anton Gannadievich Medvedovskiy residing in Kiev, who will turn 38 years old in December. This person owns the email address [email protected], as well as an Airbnb account featuring a profile image of a man with a similar hairline to the suspect in the blurred photos released by the Ukrainian authorities. Mr. Medvedovskiy did not reply to a request for commentary.
My assessment of the apprehension is that the Ukrainian officials likely detained Medvedovskiy. Toha disclosed on DaMaGeLab in 2005 that he had recently completed the 11th grade and was attending a university—at a time when Medvedovskiy would have been approximately 18 years old. On December 11, 2006, fellow Exploit members extended birthday wishes to Toha. Documents revealed in a 2022 breach at the Ukrainian public services portal diia.gov.ua indicate that Mr. Medvedovskiy’s birthday is December 11, 1987.
The law enforcement operation and the ensuing confusion regarding the identity of the apprehended have thrown the Russian cybercrime forum landscape into upheaval in recent weeks, provoking extensive and fervent debates about the future of XSS across the forums.
XSS relaunched on a new Tor address shortly after the authorities displayed their seizure notice on the forum’s homepage, yet all of the trusted moderators from the previous forum were dismissed without any explanation. Existing members observed their forum account balances plummet to zero and were requested to pay a deposit to register at the new forum. The new XSS “admin” asserted they were in contact with the prior owners and that the modifications were aimed at restoring security and trust within the community.
However, the new admin’s reassurances seem to have done little to alleviate the deepest concerns of the forum’s former members, most of whom appear to be maintaining a distance from the relaunched site for now.
Indeed, if there is one shared understanding amidst all of these discussions regarding the seizure of XSS, it is that Ukrainian and French authorities now possess several years’ worth of private communications between XSS forum members, as well as contact lists and other user data linked to the seized Jabber server.
“The myth of the ‘trusted individual’ is shattered,” the user “GordonBellford” warned on August 3 in an Exploit forum thread encompassing dozens of pages. “The forum is now managed by strangers. They acquired everything. Two years of Jabber server logs. Complete backup and forum database.”
GordonBellford continued:
And the most alarming aspect is: this data set is not merely an archive. It has been analyzed ALREADY. Utilizing modern tools, they can observe everything:
Graphs of your connections and activities.
Relations between nicknames, emails, password hashes, and Jabber IDs.
Timestamps, IP addresses, and digital fingerprints.
Your distinct writing style, phrasing, punctuation, consistency in grammatical errors, and even typical typos that will link your accounts across various platforms.They are not searching for a needle in a haystack. They have sifted the haystack through the AI filter and compiled ready-made dossiers.

