“`html
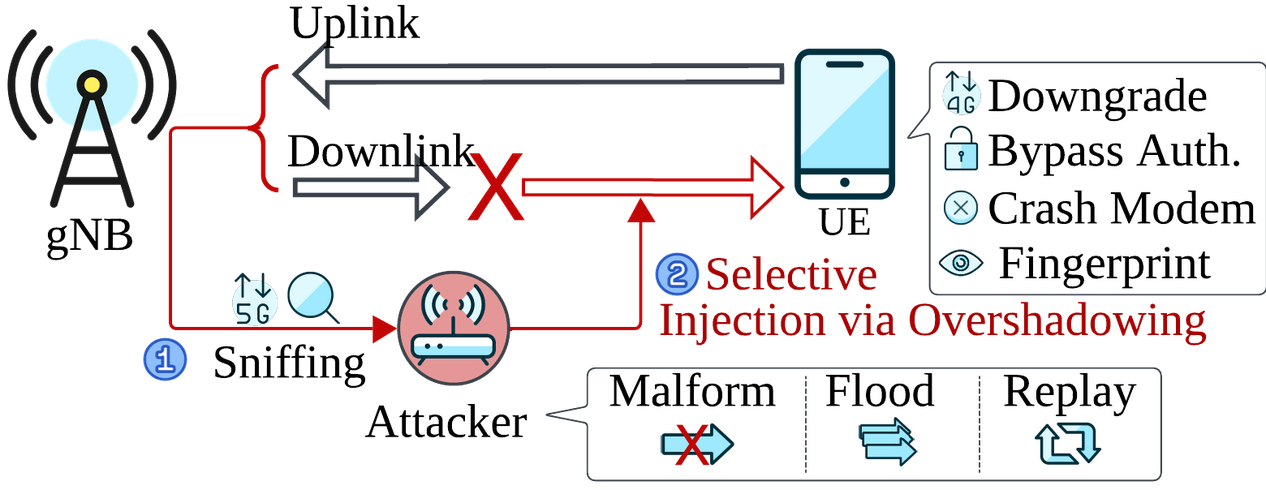
As the globe slowly embraces and shifts towards utilizing 5G for mobile, operational technology (OT), automation, and Internet-of-Things (IoT) gadgets, a secure 5G network framework is essential. Recently, the Automated Systems SEcuriTy (ASSET) Research Group has introduced a novel structure called SNI5GECT [articulated as Sni-f-Gect (sniff + 5G + inject)] that permits users of this framework to i) intercept messages from pre-authentication 5G interactions in real time and ii) introduce specific attack payloads in downlink communications directed at User Equipments (UE). I had previously elaborated on how 5G connections are initiated over here; therefore, I will proceed directly into the SNI5GECT framework. In this entry, I will succinctly outline the SNI5GECT framework and explore a new multi-stage downgrade attack utilizing the SNI5GECT framework.
“`