“`html
Security analysts recently uncovered that the private details of millions of individuals who applied for positions at McDonald’s were compromised after they managed to guess the password (“123456”) for the fast food giant’s account at Paradox.ai, a firm that develops AI-driven hiring chatbots utilized by numerous Fortune 500 corporations. Paradox.ai stated that the security lapse was an isolated event that did not impact its other clients, however, recent security incidents involving its staff in Vietnam portray a more intricate scenario.
A screenshot of the paradox.ai homepage displaying its AI hiring chatbot “Olivia” engaging with potential candidates.
Earlier this month, security analysts Ian Carroll and Sam Curry reported on straightforward techniques they discovered to gain access to the backend of the AI chatbot system on McHire.com, the McDonald’s platform that many franchise operators employ to assess job applicants. As first noted by Wired, the analysts found that the weak password employed by Paradox led to the exposure of 64 million records, including applicants’ names, email addresses, and phone numbers.
Paradox.ai acknowledged the analysts’ discoveries but asserted that the organization’s other client instances remained unaffected, and that no sensitive data — like Social Security numbers — was compromised.
“We are confident, according to our logs, this test account was not accessed by any third-party aside from the security researchers,” the company expressed in a July 9 blog entry. “It had not been logged into since 2019 and frankly, should have been decommissioned. We wish to be very explicit that while the researchers may have temporarily accessed the system containing all chat interactions (NOT job applications), they only reviewed and retrieved five chats in total that contained candidate information. Again, at no stage was any data leaked online or made publicly accessible.”
Nevertheless, an examination of pilfered password data collected by various breach-monitoring services indicates that at the conclusion of June 2025, a Paradox.ai administrator in Vietnam experienced a malware breach on their device which captured usernames and passwords for numerous internal and third-party online platforms. The results were grim.
The password data from the Paradox.ai developer was taken by a malware variant known as “Nexus Stealer,” a type of grabber and password thief that is marketed on cybercrime forums. The information siphoned by stealers like Nexus is frequently recaptured and indexed by data leak aggregator services such as Intelligence X, which reports that the malware on the Paradox.ai developer’s device unveiled hundreds of predominantly weak and reused passwords (utilizing the same foundational password but with slight variations at the end).
Those stolen credentials reveal that the developer in question had, at one time, employed the same seven-character password to access Paradox.ai accounts for multiple Fortune 500 companies listed as clients on the firm’s website, including Aramark, Lockheed Martin, Lowes, and Pepsi.
Seven-character passwords, particularly those consisting entirely of digits, are extremely susceptible to “brute-force” attacks capable of testing a vast number of potential password combinations in quick succession. According to a widely-referenced password strength guide maintained by Hive Systems, contemporary password-cracking tools can deduce a seven-digit password practically instantly.
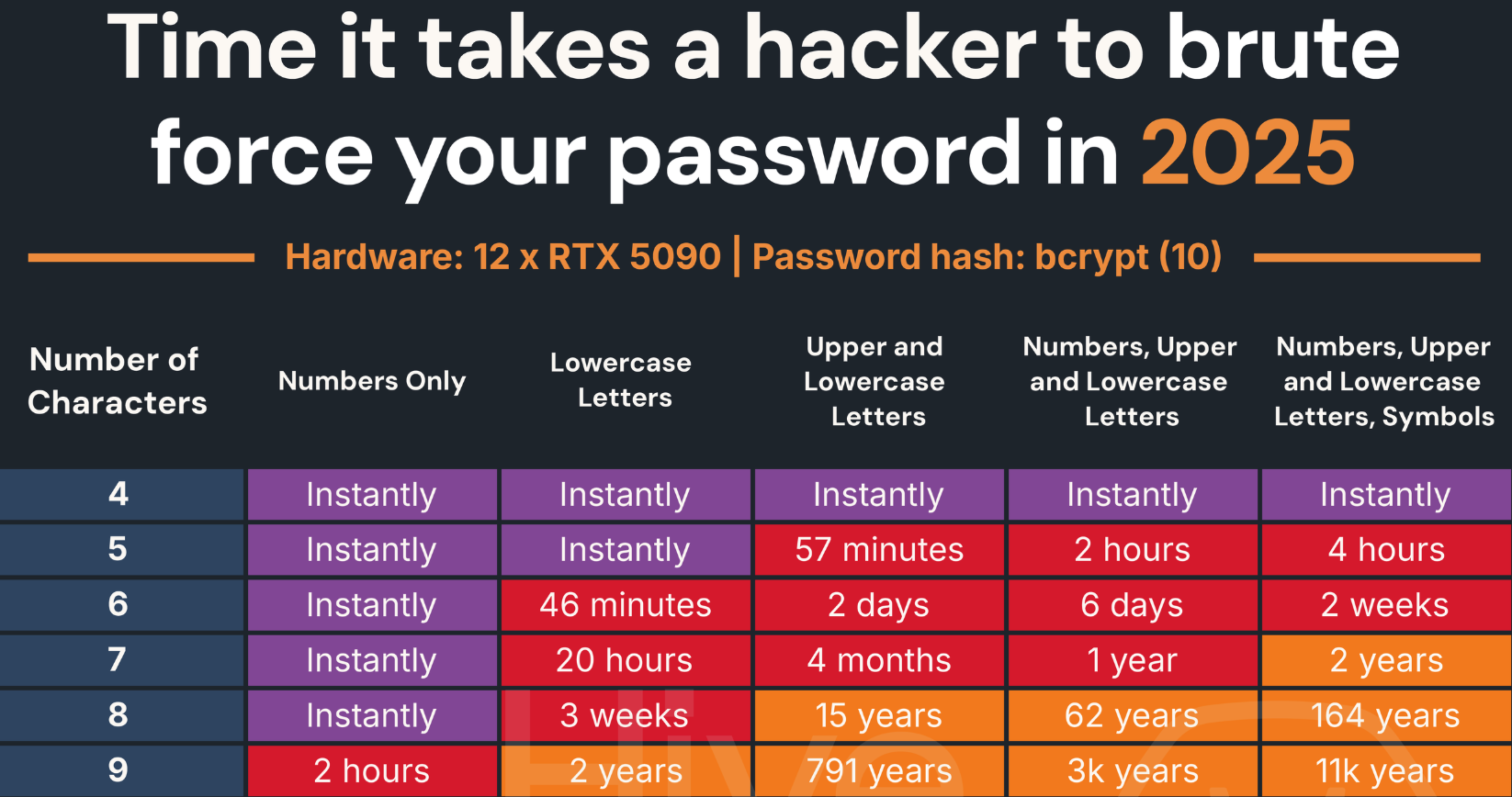
Image: hivesystems.com.
In response to inquiries from KrebsOnSecurity, Paradox.ai confirmed that the password data was recently pilfered due to a malware infection on the personal device of a long-time Paradox developer situated in Vietnam, and stated that the firm was alerted to the breach shortly after it occurred. Paradox contends that few of the exposed passwords were still in use, and that most were present on the employee’s personal device solely because he had transferred the contents of a password manager from an old computer.
Paradox also noted that it has mandated single sign-on (SSO) authentication since 2020 which enforces multi-factor authentication for its partners. Still, a review of the exposed passwords reveals they incorporated the Vietnamese administrator’s credentials to the company’s SSO platform — paradoxai.okta.com. The password for that account ended in 202506 — possibly referencing June 2025 — and the digital cookie left behind after a successful Okta login using those credentials indicates it was valid until December 2025.
Also compromised were the administrator’s credentials and authentication cookies for an account at Atlassian, a platform designed for software development and project management. The expiration date for that authentication token was similarly December 2025.
Infostealer infections are among the primary causes of data breaches and ransomware incidents today, leading to the theft of stored passwords and any credentials that the victim inputs into a browser. Most infostealer malware also siphons authentication cookies stored on the victim’s device, and depending on how those tokens are configured, attackers may be capable of using them to circumvent login prompts and/or multi-factor authentication.
Frequently, these infostealer infections will establish a backdoor on the victim’s machine, permitting attackers to remotely access the infected device. Indeed, it appears that remote access to the compromised device of the Paradox administrator was recently available for sale.
In February 2019, Paradox.ai announced the successful completion of audits for two quite comprehensive security standards (ISO 27001 and SOC 2 Type II). Meanwhile, the company’s security disclosure this month indicates that the test account with the dreadful 123456 username and password was last accessed in 2019, yet somehow overlooked in their yearly penetration tests. How did it manage to pass such rigorous security audits with these practices in place?
Paradox.ai informed KrebsOnSecurity that during the 2019 audit, the firm’s various contractors were not subjected to the same security standards that the company enforces internally. Paradox stressed that this has since changed, and that it has revised its security and password requirements multiple times since then.
It remains unclear how the Paradox developer in Vietnam infected their computer with malware, but a more detailed examination reveals a Windows device belonging to another Paradox.ai employee from Vietnam was compromised by similar data-stealing malware towards the end of 2024 (that breach included the victim’s GitHub credentials). In both cases of the employees, the pilfered credential data encompasses web browser history logs indicating that the victims repeatedly downloaded pirated movies and television shows, which are often bundled with malware disguised as a necessary video codec to view the pirated content.
“`