“`html
KrebsOnSecurity recently received information from a reader whose supervisor’s email account was compromised through phishing, leading to an attempt to deceive one of the company’s clients into making a substantial payment to fraudsters. An examination of the assailant’s infrastructure suggests a longstanding Nigerian cybercrime syndicate that is targeting well-established businesses in the transportation and aviation sectors.

Image: Shutterstock, Mr. Teerapon Tiuekhom.
A reader involved in the transportation sector alerted us to a recent effective phishing campaign that deceived a corporate executive into entering their credentials on a fraudulent Microsoft 365 login page. Following that, the perpetrators swiftly probed the executive’s email for previous communications regarding invoices, altering and duplicating some messages with new payment requests that were dispatched to various clients and partners of the company.
The reader also noted that the email addresses linked to the registration records for the counterfeit domain — [email protected] — are associated with numerous similar phishing domains. Indeed, a search of this email address on DomainTools.com reveals it is linked to over 240 domains registered in 2024 or 2025. Nearly all of these mimic legitimate domains of companies engaged in the aerospace and transportation sectors globally.
An online search for this email address uncovers a humorous blog post from 2020 on the Russian platform hackware[.]ru, which identified [email protected] as associated with a phishing scheme that utilized the pretense of fake invoices to mislead recipients into logging onto a fraudulent Microsoft login page. We will revisit this research shortly.
JUSTY JOHN
DomainTools indicates that some of the initial domains registered to [email protected] in 2016 reveal additional useful details. For instance, the WHOIS records for alhhomaidhicentre[.]biz mention the technical contact as “Justy John” alongside the email address [email protected].
A review at DomainTools shows [email protected] has been registering individual phishing domains since at least 2012. At this point, I was certain that some cybersecurity firm must have previously published an analysis of this specific threat group, but I lacked sufficient data to form any definite conclusions.
DomainTools states that the Justy John email address is linked to over two dozen domains registered since 2012, but we can discover hundreds more phishing domains and relevant email addresses just by exploring details in the registration records for these Justy John domains. For instance, the street address associated with the Justy John domain axisupdate[.]net — 7902 Pelleaux Road in Knoxville, TN — appears in the registration records for accountauthenticate[.]com, acctlogin[.]biz, and loginaccount[.]biz, all of which at one point included the email address [email protected].
This Rsmith Gmail address is linked to the 2012 phishing domain alibala[.]biz (which is just one character off from the Chinese e-commerce giant alibaba.com, using a different top-level domain of .biz). A search in DomainTools for the phone number in those domain records — 1.7736491613 — unveils even more phishing domains, along with the Nigerian phone number “2348062918302” and the email address [email protected].
DomainTools indicates [email protected] is present in the registration records for the domain seltrock[.]com, which was utilized in the phishing scheme documented in the aforementioned 2020 Russian blog post. At this juncture, we are just two steps removed from pinpointing the threat actor group.
The same Nigerian phone number appears in numerous domain registrations referencing the email address [email protected], including 26i3[.]net, costamere[.]com, danagruop[.]us, and dividrilling[.]com. A web search for any of those domains indicates that they were included in an “indicator of compromise” list on GitHub curated by the Palo Alto Networks‘ Unit 42 research team.
SILVERTERRIER
According to Unit 42, these domains are the result of a vast cybercriminal organization based in Nigeria, termed “SilverTerrier” since 2014. In an October 2021 analysis, Palo Alto stated that SilverTerrier excels in so-called “business email compromise” or BEC scams, which aim at authentic business email accounts through social manipulation or system infiltration. BEC criminals leverage that access to initiate or reroute business fund transfers for personal profit.
Palo Alto claims SilverTerrier includes hundreds of BEC fraudsters, with some having been apprehended in various international law enforcement operations conducted by Interpol. In 2022, Interpol and the Nigeria Police Force arrested 11 purported SilverTerrier members, including a notable SilverTerrier figure who had been showcasing his wealth on social platforms for years. Regrettably, the allure of easy money, widespread poverty and corruption, along with minimal entry barriers for cybercrime in Nigeria continuously replenish the ranks of new recruits.
BEC scams were the 7th most frequently reported crime tracked by the FBI’s Internet Crime Complaint Center (IC3) in 2024, resulting in over 21,000 reports. However, BEC scams represented the second most financially devastating type of cybercrime reported to federal authorities last year, with almost $2.8 billion in estimated losses. In its 2025 Fraud and Control Survey Report, the Association for Financial Professionals found that 63 percent of organizations experienced at least one BEC last year.
Investigating some of the email addresses emerging from this inquiry reveals several Facebook profiles belonging to individuals residing in Nigeria or the United Arab Emirates, many of whom do not appear to have attempted to conceal their real-world identities. Palo Alto’s Unit 42 researchers came to a similar conclusion, acknowledging that while a small subset of these criminals…
“““html
took extensive measures to hide their identities, it was typically easy to uncover their identities on social media profiles and the primary messaging platforms.
Palo Alto stated that BEC perpetrators have become significantly more structured over time, and although it still remains straightforward to identify individuals operating collectively, the method of utilizing a single phone number, email address, or alias to establish harmful infrastructure for various actors has rendered it considerably more labor-intensive (though not unfeasible) for cybersecurity and law enforcement agencies to differentiate which individuals executed particular offenses.
“We consistently observe that SilverTerrier participants, irrespective of their geographical placement, are frequently linked by only a few degrees of separation on social media networks,” the analysts remarked.
FINANCIAL FRAUD KILL CHAIN
Palo Alto has released a valuable set of suggestions that organizations can implement to reduce the occurrence and effects of BEC schemes. Many of these recommendations are preventative, such as performing routine employee security training and assessing network security protocols.
However, one suggestion — becoming acquainted with a method known as the “financial fraud kill chain” or FFKC — deserves particular attention because it provides the best chance for BEC victims looking to retrieve payments made to fraudsters, and yet far too many victims remain unaware of its existence until it is too late.
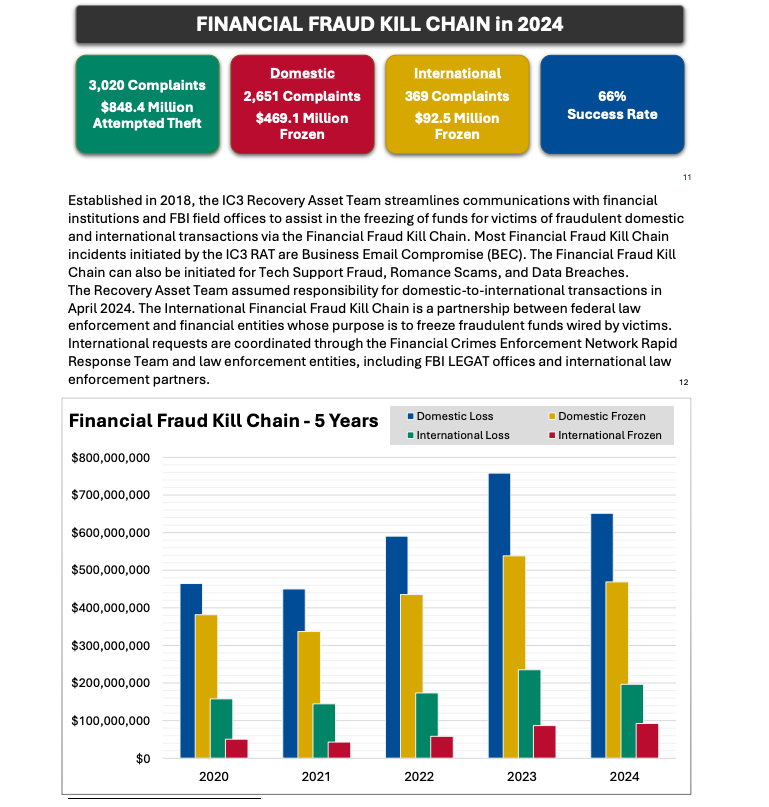
Image: ic3.gov.
As detailed in this FBI overview, the International Financial Fraud Kill Chain is a collaboration among federal law enforcement and financial organizations aimed at freezing fraudulent funds transferred by victims. According to the FBI, timely victim reports submitted to ic3.gov immediately following a fraudulent transaction (generally within 72 hours) will be automatically prioritized by the Financial Crimes Enforcement Network (FinCEN).
The FBI mentioned in its IC3 annual report (PDF) that the FFKC achieved a 66 percent success rate in 2024. Valid ic3.gov reports involve losses of no less than $50,000, and include all documentation from the victim or victim’s bank, along with a completed FFKC form (supplied by FinCEN) containing victim details, recipient data, bank names, account numbers, locations, SWIFT codes, and any supplementary information.
“`

