-
Ultimate Guide to Top Agile Certifications for 2025

Mastering Agile frameworks is more than just a fad; it’s essential for individuals aiming to progress in their careers. Agile certifications can unlock new professional avenues, improve project management abilities, and enable you to quickly adapt to evolving project needs. Regardless of whether you are a project manager, a software engineer, or a product manager,…
-
Essential Java Architect Interview Questions to Help You Succeed

Given that Java is a prominent, essential, and highly sought-after programming language, the career opportunities are encouraging. The position of Java Architect is among the most pivotal in software engineering due to its role in designing, developing, and upkeeping application frameworks. Recruitment for these positions necessitates the careful selection of candidates with exceptional …Read More.
-
Revolutionizing Google Ad Campaigns: The Influence of Performance Max

Earlier this year, we examined how Google’s Performance Max campaigns would significantly influence PPC advertising. To summarize, they would serve as the “ultimate intelligent campaign,” enhancing automation and machine learning for advertisements across all channels and inventories — all from a single campaign. And although advertisers have been able to transition to the new…Read More.
-
Maximizing Your Advertising Budget in 2025: Smart Strategies for Success

Recent indicators suggest a slower-than-expected increase in worldwide advertising expenditure for 2025. This is per two new projections indicating that a significant portion of this deceleration is driven by economic instability: Source It’s crucial to recognize that not every region or sector will react similarly — for instance, entertainment, travel, and gambling… Read More.
-
Key Functions and Duties of an Azure Administrator

Microsoft Azure, a premier cloud computing platform, enables organizations to utilize scalable and economical solutions. At the core of this ecosystem is the Azure Administrator, an essential position tasked with overseeing, protecting, and enhancing Azure resources. This article investigates the realm of Azure Administrators, examining their k…Discover More.
-
Unlock Your Future: Top Graduate Programs in Data Science

In this article, we will explore several graduate programs in data science that could provide you with an advantage in the employment market. We will review various program features, including courses, qualifications, and credentials, that may aid you in selecting the most suitable program for you. Additionally, we will briefly outline some further actions you…
-
SonicWall Web Scanning for CVE-2021-20016: Latest Insights (Wed, May 14th)
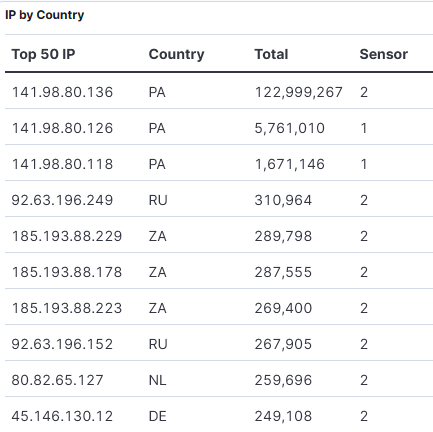
I released a diary [1] on April 29, 2025, concerning scanning activities targeting SonicWall, and since that publication, this activity has escalated tenfold. In the last two weeks, numerous BACS students have noted activities associated with SonicWall scans, all linked to the identical two URLs [4][5] previously referenced in my earlier diary. During this time…
-
Innovative Student Ventures Shape the Future of Los Angeles and Beyond

The 2025 Das Family Innovate x LA Student Contest encourages students to create significant urban solutions and vie for a $20,000 award.
-
Florida State University Enhances Unconquered by Debt Initiative to Boost Student Financial Literacy
Florida State University’s Gus A. Stavros Center for the Advancement of Free Enterprise and Economic Education is broadening Unconquered by Debt, a financial wellness initiative designed to enhance financial literacy and reshape decision-making, empowering students to become wealth generators, due to fresh backing from the Office of the Provost. Unconquered by Debt, or UBD, advocates…
-
USC Superfund Center Secures $8 Million from NIH to Combat ‘Forever Chemicals’

Authorities in public health, engineering, and medicine will investigate and tackle the adverse effects associated with the synthetic contaminants referred to as PFAS.
-
USC Trojan Marching Band Set to Embark on Exciting Tour in Japan

“`html The ensemble and USC Song Leaders showcased their talent at Aichi Prefecture’s Expo 2005 during the USA National Day of the event. (Photo/Courtesy of the USC Trojan Marching Band) Share University USC Trojan Marching Band Set to Perform in Japan The Spirit of Troy will be represented next week at the USA Pavilion during…
-
Pioneering Progress: The Inspiring Journey of Tiffany Toh ’25

In a Q&A, Toh shares what attracted her to Yale, her efforts in creating an innovative heart medical device, and her advice for incoming freshmen.
-
From Flames to Futures: A Firefighter’s Path to Healthcare Leadership in the YSN Class of 2025
Christopher Hardman is among the 19 individuals who have completed Yale School of Nursing’s Systems Leadership D.N.P. program and will honor their achievements at this year’s commencement ceremony.
-
Yale Library Honors Its Student Employees on Graduation Day

Since 2022, Yale Library has expressed gratitude to its graduating student workers for their numerous contributions via its distinctive bookplate initiative.
-
“Building Bonds: Luke Neal’s Journey to Community at Yale”

In addition to excelling on Yale’s tennis squad, Luke Neal persisted in exploring diverse communities throughout the campus, discovering transformative experiences that have altered his life.
-
Examining Accessibility: A Berkeley MFA Exhibition on the Exclusion of Disabled Bodies in Museums

Priyanka D’Souza’s Master of Fine Arts thesis presentation, “b. Call in absent,” resonates with UC Berkeley’s extensive legacy of free expression and disability advocacy. The article This Berkeley MFA exhibition investigates how museums and institutions marginalize disabled individuals was originally published on Berkeley News.
-
Tackling the Space Junk Crisis: Innovative Solutions for a Clearer Orbit

“`html Currently, there are roughly 35,000 monitored human-made items in orbit around our planet. Among these, only about one-third comprise active payloads: scientific and communication satellites, research initiatives, and other useful technological implementations. The remainder is classified as debris — inactive satellites, discarded rocket stages, and the remnants from numerous collisions, explosions, planned launch vehicle…
-
“Empowering Minds: Students Honor Their Mental Health Journeys at Flourish Together Celebration”
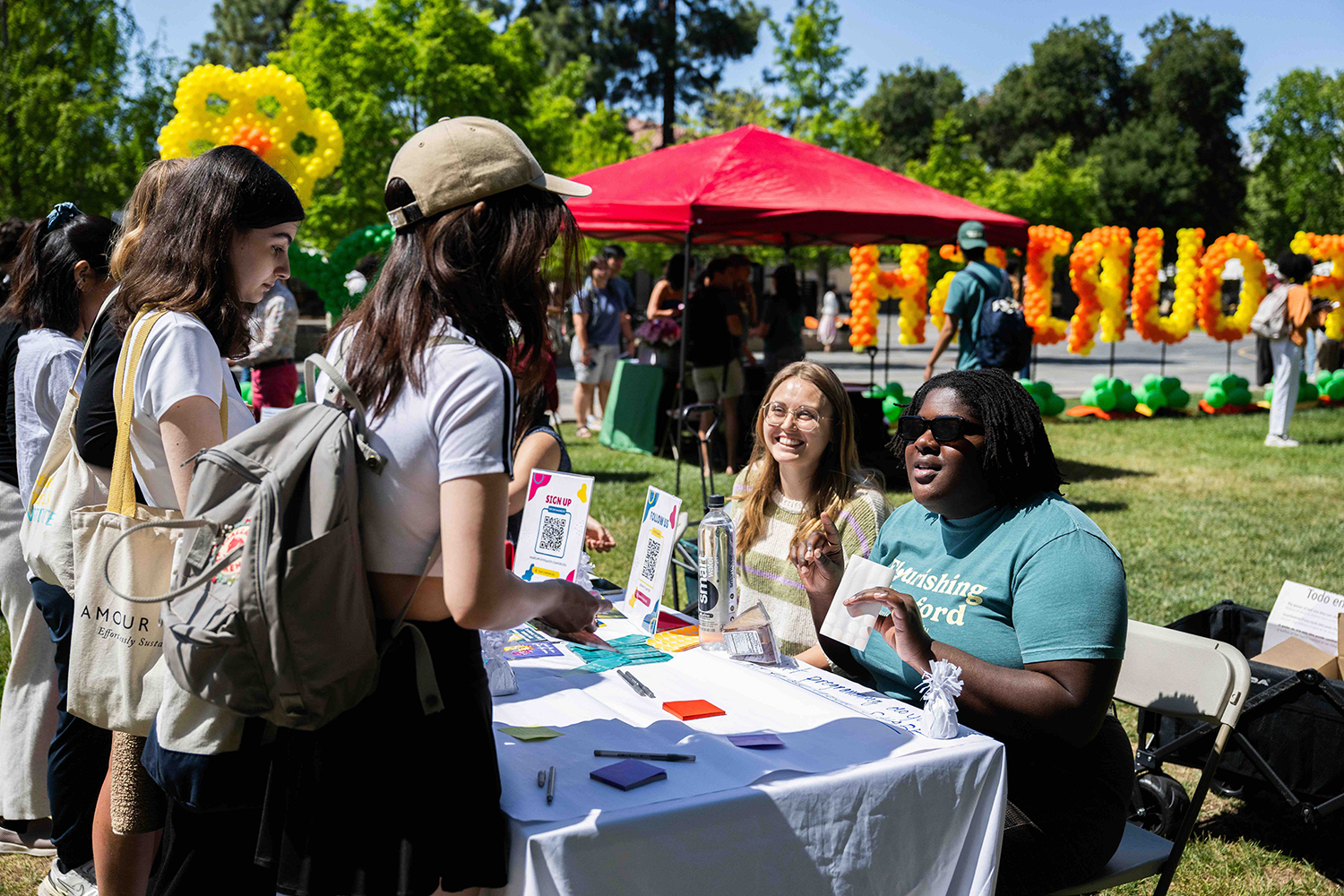
The second yearly wellness gathering included booths from various teams around campus and a student photography display.
-
The Ripple Effect: How Healthcare Provider Bankruptcy Impacts Patients

Recent studies reveal a rise in medical admissions, employee turnover, and an elevated application of physical restraints.
-
The Perilous Nature of the Achilles Region

“`html Health Why the Achilles is such a perilous area Boston Celtics star Jayson Tatum grips his foot in agony after sustaining an injury during Monday’s playoff matchup against the New York Knicks. Getty Images Christina Pazzanese Harvard Staff Writer May 14, 2025 5 min read With Jayson Tatum facing a lengthy journey to recovery,…
-
UT Celebrates 16 Outstanding Undergraduates for Their Academic Achievements

Each spring, The University of Texas at Austin honors undergraduate students who have displayed exceptional commitment and accomplishment in their respective fields with the UT Co-op George H. Mitchell Award. Nominations for the awards are made by faculty members. A selection committee is comprised of a variety of faculty individuals. This year, 70 undergraduate students…
-
Journeying Down the Path to Broadway

At Yale, Maxwell Brown discovered artistic motivation and gained fresh understanding of the significance of art.
-
Dimitris Bertsimas Honored with the Prestigious 2025-2026 Killian Award

Dimitris Bertsimas SM ’87, PhD ’88, a prominent personality in operations research, has been honored with the 2025-26 James R. Killian Jr. Faculty Achievement Award. This distinction is the highest accolade awarded by the MIT faculty to its own educators. Bertsimas holds the Boeing Professorship of Operations Research at the MIT Sloan School of Management,…
-
Survival Secrets: Decades of Wisdom for a Thriving Life

“`html Health Strategies for longevity, years in development JoAnn Manson has devoted her career to exploring – and emphasizing – how daily decisions impact well-being Alvin Powell Harvard Staff Writer May 14, 2025 5 min read JoAnn Manson. Veasey Conway/Harvard Staff Photographer Part of the Profiles of Progress series Regarding the notion that prevention constitutes…
-
Introducing the Oracle Database 23ai and GoldenGate Implementation Associate Certification Pathway
“`html Oracle GoldenGate 23ai Blog Welcome to the Oracle GoldenGate 23ai blog, where we delve into the latest advancements and features of this powerful data integration tool. Introduction to GoldenGate Oracle GoldenGate is a robust solution for real-time data integration and replication. It allows organizations to ensure data consistency across various environments. Key Features Real-time…
-
The Journey of Miriam Alrahil: A Story of Resilience and Inspiration

“`html Miriam Alrahil, a recipient of the Florida State University IDEA Grant and a student of the Middle Eastern Studies Center, came to FSU to contribute to her community through the Service Scholars Program. Alrahil works as an English tutor for middle and high school learners who speak other languages. She is also a youth…
-
FSU Honors Its Esteemed Distinguished University Scholar Award Recipients
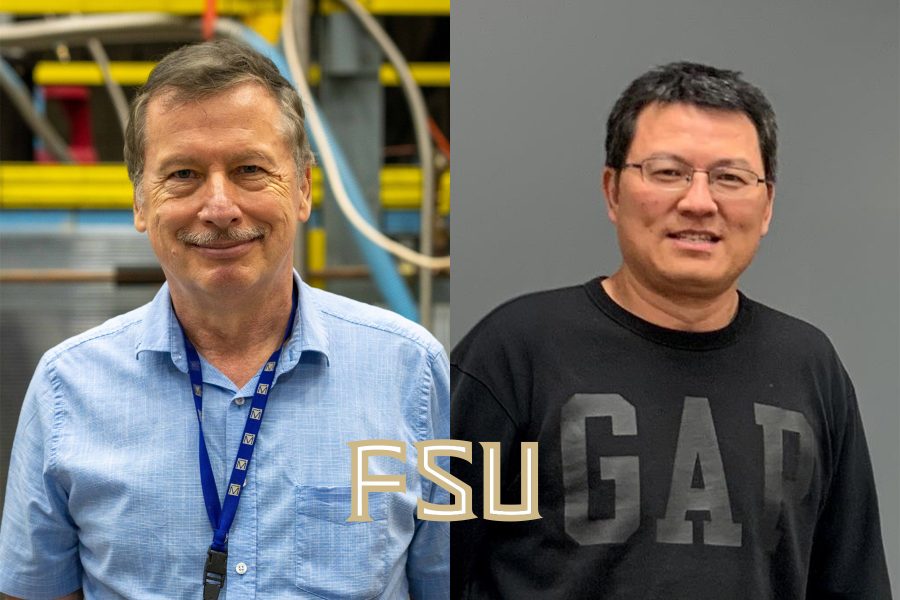
“`html The Florida State University has honored two exceptional researchers with the Distinguished University Scholar Award in acknowledgment of their extensive history of scholarly work. “Our esteemed faculty spearhead significant initiatives, mentor the upcoming generation of academics, and provide expertise that is often rare,” stated Vice President for Research Stacey S. Patterson. “Their dedication and…
-
Students Encouraged to Adopt a Policymaker’s Mindset to Tackle Homelessness

In the midst of a countrywide housing emergency, a course at Yale Law School led by former Hartford mayor Luke Bronin ’06 J.D. is encouraging students to develop practical solutions to one of the most intricate and urgent challenges of our time.
-
Gerber Steps in as Interim Dean of Social Sciences; Scheve Heads to Notre Dame
Ken Scheve will resign from his position as FAS Dean of Social Science at the conclusion of this academic year to take on the role of Dean of the College of Arts & Letters at the University of Notre Dame. Alan Gerber will assume the responsibilities of Acting FAS Dean of Social Science for the…
-
Unveiling Surprises: The Hidden Treasures of Yale

Keeley Brooks, a senior graduating from Morse College, persisted in her development as a musician at Yale — and discovered new abilities as well.
-
Innovative Tech Solutions from UC Berkeley Students Transforming Democracy During Uncertain Times

The Building Bridges program motivates learners to approach problems as entrepreneurs and “recognize that technology can serve a positive purpose.” The article In uncertain times, these UC Berkeley students are using tech to innovate democratic processes was first published on Berkeley News.
-
Stanford Honors Donor with SEQ Naming Ceremony

The Robert Rosenkranz Science and Engineering Quad commemorates the substantial donations that promote research on aging and establish professorships within the STEM disciplines.
-
Samsung Addresses CVE-2025-4632 Vulnerability Targeted by Mirai Botnet Using MagicINFO 9 Exploit

Samsung has issued software updates to rectify a significant security vulnerability in MagicINFO 9 Server that has been actively taken advantage of in real-world scenarios. The weakness, identified as CVE-2025-4632 (CVSS rating: 9.8), has been characterized as a path traversal issue. “Insufficient restriction of a pathname to a confined directory vulnerability in Samsung MagicINFO 9…
-
BianLian and RansomExx Target SAP NetWeaver Vulnerability for PipeMagic Trojan Deployment
At least two distinct cybercriminal organizations, BianLian and RansomExx, are reported to have taken advantage of a newly revealed security vulnerability in SAP NetWeaver, suggesting that several threat actors are capitalizing on the defect. Cybersecurity company ReliaQuest, in a recent update released today, stated it found indications pointing to the participation of the BianLian data…
-
UGA’s Michael Skibsted Honored as a 2025 Udall Scholar

Michael Skibsted’s passion for turtles and wildlife preservation has granted him a 2025 Udall Scholarship. The undergraduate from the University of Georgia is among 55 students nationwide being acknowledged for their leadership, community service, and dedication to environmental issues. A third-year Honors student hailing from Ladera Ranch, California, Skibsted is pursuing a major in ecology…
-
Study Reveals Men More Prone to ‘Broken Heart Syndrome’

“`html Males are at a greater risk of succumbing to ‘broken heart syndrome,’ according to research nprevenas Wed, 05/14/2025 – 09:22 Males are at a greater risk of succumbing to ‘broken heart syndrome,’ according to research Today Article Categories Health & Wellness Current Events By NBC News Type of News Article Third-party News “`
-
Chasing My Dreams: A Student’s Journey
Latino campus groups influenced my achievements, offering a feeling of direction.
-
USC Price Graduate Assumes Key Position at U.S. Department of Transportation

Shaz Umer holds the position of director of strategic initiatives within the office of the DOT secretary.
-
MACH 33 Festival Ignites Dialogue on AI, Morality, and Narrative Craft

A technology leader perishes in an autonomous vehicle operated by a self-driving company. A humanoid AI apparatus acts as the family caretaker for an elderly parent. These themes were examined in two original plays crafted and showcased at MACH 33: The Caltech Festival of New Science-Driven Works, which focused on artificial intelligence during its 2025…
-
The $8.4 Billion Crypto Underworld: Unraveling Xinbi Telegram’s Dark Ties to Fraud and Fraudulent Activities

A Chinese-language marketplace on Telegram known as Xinbi Guarantee has facilitated at least $8.4 billion in transactions since 2022, positioning it as the second noteworthy black market unveiled following HuiOne Guarantee. As per a report released by blockchain analytics company Elliptic, vendors on the marketplace have been discovered to trade in technology, personal information, and…
-
Navigating the Paradox of “Cruel Optimism” in Tech Industry Layoffs: Insights from a UW Researcher

“`html In 2023, researchers from the University of Washington engaged a cohort of 29 dismissed U.S. technology employees to investigate the repercussions of the layoffs on staff. Overall, the group exhibited mixed feelings towards tech employment. They expressed that it was frequently lacking in satisfaction, notwithstanding their intentions to remain in the field.iStock/mathisworks In 2022,…
-
One in Four Children Affected by Parental Substance Abuse, U-M Research Reveals

“`html Revised assessments highlight the necessity for enhanced treatment Study: U.S. Youth Residing With a Parent Dealing With Substance Use Disorder, JAMA Pediatrics. doi:10.1001/jamapediatrics.2025.0828 A significant portion of children in the United States is being raised in environments where at least one parent engages in problematic alcohol or drug use—heightening the likelihood that these children…
-
Dutcher Honored with Election to the National Academy of Sciences

Susan K. Dutcher, PhD, a professor of genetics as well as cell biology and physiology at Washington University School of Medicine in St. Louis, is among 120 newly elected members, including 30 international members, to the National Academy of Sciences, honoring her exceptional and ongoing contributions to innovative research. Being elected to the academy is regarded…
-
Innovative Strategies for Light Manipulation in Photonic Circuits
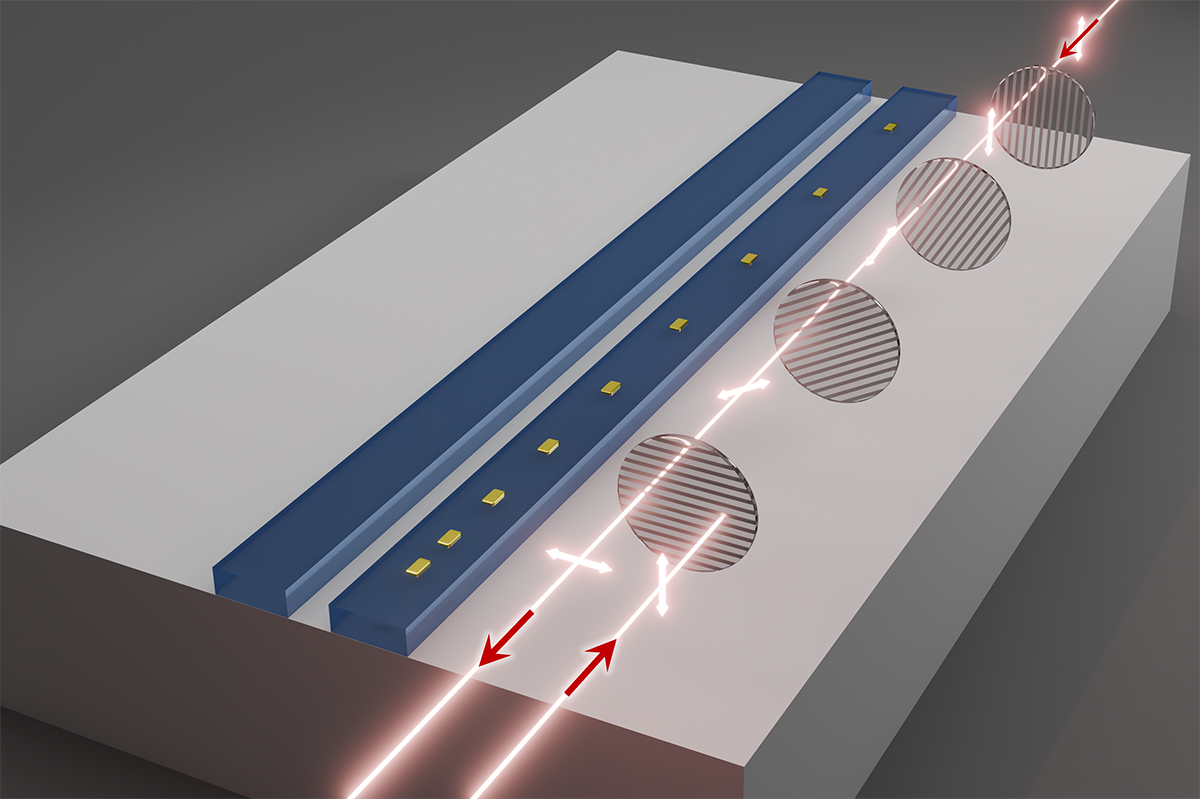
“`html A novel technique developed by WashU scientists can adjust the pathways of light in a manner that reduces costs and streamlines photonic circuits. (Image: Micro/Nano Photonics Lab) In an effort to enhance photonic and electronic circuitry utilized in semiconductor chips and fiber optic networks, researchers at the McKelvey School of Engineering at Washington University…
-
Graduation Day Chronicles: Simone, Joyful Moments, and Soaring Caps

Almost four years prior, Will Smith embarked on his inaugural journey to Francis Olympic Field for Bear Beginnings orientation. Encircled by close to 2,000 individuals of the WashU Class of 2025, he felt optimistic, thrilled, and somewhat anxious. On May 12, he returned — transformed, overwhelmed by familiar sentiments. “I couldn’t grasp it then, but…
-
Celebrating Excellence: Nine Students Honored with SUNY Chancellor’s Awards

The accolade is the foremost distinction granted to students by SUNY and acknowledges individuals who have showcased outstanding accomplishments in various fields, encompassing academics, leadership, and community involvement.
-
Gruber Foundation Honors 2025 Prize Recipients for Breakthroughs in Cosmology, Genetics, and Neuroscience

The Gruber Foundation today acknowledged four researchers who have made notable advancements in the domains of cosmology, genetics, and neuroscience.
-
Optimizing Pavement Performance with Limited Data: Three Key Questions to Consider

Pavements constitute the essential framework of our constructed surroundings. In the United States, nearly 2.8 million lane-miles, or roughly 4.6 million lane-kilometers, are surfaced. They connect us to our workplaces and educational institutions, transport goods to various locations, and serve many other purposes. To ensure a more sustainable tomorrow, we need to thoroughly examine the long-term…
-
Steven Truong ’20 Selected as a 2025 Knight-Hennessy Scholar

MIT graduate Steven Troung ’20 has been granted a 2025 Knight-Hennessy Scholarship and will become part of the eighth cohort of this esteemed fellowship. Knight-Hennessy Scholars receive up to three years of financial assistance for graduate education at Stanford University. Knight-Hennessy Scholars are chosen for their originality of thought, intentional leadership, and community-oriented perspective. Troung…
-
Future Speaking Engagements on the Horizon

This is an up-to-date compilation of my speaking engagements along with their locations and timings: I will be presenting (virtually) at the Sektor 3.0 Festival in Warsaw, Poland, on May 21-22, 2025. The compilation is updated on this webpage.
-
Navigating the Intersection of Chemistry and Strategy: Ishpinder Kailey’s Journey Through an iMBA to Amplify Her Influence in STEM
“`html When Ishpinder Kailey, a learner from Australia, contemplates her journey—from instructing physical chemistry in India, to managing global R&D teams in Canada, and now co-establishing her own advisory firm in Australia—her trajectory narrates a tale of steadfast tenacity, characterized by daring decisions, transformation, and a profound dedication to education and self-improvement. Having a scientific…
-
Trinity Pryor ’25 Receives Coveted Saint Andrew’s Scholarship

She will seek a master’s degree in education, public administration, and fairness in Glasgow.
-
Cultural Celebrations: Powwow and Lūʻau 2025

The Dartmouth community commemorated the 53rd yearly Powwow on Saturday and Lūʽau on Sunday.
-
Innovation in Drug Delivery: MIT’s $100K Competition Crowned a New Champion

“`html The victor of this year’s MIT $100K Entrepreneurship Contest is assisting advanced therapies in reaching more patients promptly with a novel type of drug-injection apparatus. CoFlo Medical claims its affordable device can administer biologic medications over 10 times quicker than current techniques, expediting the treatment of various ailments, including cancers, autoimmune disorders, and infectious…
-
CTM360 Discovers Rising Wave of Phishing Scams Aimed at Meta Business Users

A recent worldwide phishing menace known as “Meta Mirage” has been revealed, focusing on enterprises utilizing Meta’s Business Suite. This initiative particularly seeks to seize high-value accounts, such as those controlling advertising and official brand pages. Cybersecurity analysts at CTM360 disclosed that the perpetrators of Meta Mirage mimic official Meta communications, deceiving users into relinquishing
-
UGA Unites for a Memorable Staff Appreciation Gala

As the 2024-2025 school year approached its conclusion, personnel at the University of Georgia were honored at the Spring Staff Appreciation Celebration for their contributions to the institution. “The success of the University of Georgia relies on the commitment, skill, and effort of our exceptional staff,” remarked President Jere W. Morehead. “I am sincerely appreciative…
-
Welliver Awarded Coveted Guggenheim Fellowship

The article Welliver Receives Esteemed Guggenheim Fellowship was initially published on Florida State University News.
-
Exploring the World of JavaScript Objects: A Comprehensive Guide

In JavaScript, objects serve to hold data in key-value combinations. They facilitate the arrangement of information. This article will explore what JavaScript objects are, how to construct and utilize them, and some helpful functions that will assist you in managing objects. Table of Contents: What is an Object in JavaScript? Creating JavaScript Objects Accessing Object…
-
Key Considerations for Overriding equals and hashCode in Java

“`html When customizing equals() and hashCode() in Java, ensure that if both objects are deemed equal according to equals(), their hashCode() values should also be identical, maintaining the contract for hash-based collections. This article will explore the equals() and hashCode() methods in Java, along with the challenges one might encounter when overriding them. Contents Overview:…
-
Essential Arithmetic Operators in C Programming

“`html Arithmetic Operators in C are the symbols utilized to execute fundamental mathematical tasks. These operators are straightforward and accommodate a variety of data types. In this article, we will explore the concept of arithmetic operators in C, their classifications, precedence and associativity, examples of their use in C programming, benefits, and guidelines for effectively…
-
Understanding Scanner Behavior: Why Does nextLine Get Skipped?

“`html If you are obtaining user input utilizing Java’s Scanner class, you may notice that the next(), nextInt(), nextDouble(), etc., is followed by the subsequent nextLine() appearing to be overlooked. This is a frequent mistake for Java beginners and typically leads to incomplete or inaccurate input processing. So what is the origin of the issue?…
-
Effective User Input Handling in Java: Exploring Scanner, BufferedReader, and Console

“`html Obtaining user input forms a fundamental aspect of developing interactive Java applications. Whether you’re crafting a console-based utility, a form-driven platform, or even a game, the ability to read and manage user input is crucial. Java provides several techniques – Scanner, BufferedReader, and Console – to capture different types of input like strings, numbers,…
-
Understanding Memory Initialization: The Role of 0xCD, 0xDD, and Beyond in Memory Management

“`html Have you ever pondered why your C++ application unexpectedly crashes or behaves oddly at times? The reason could very likely be uninitialized memory, buffer overflows, or use-after-free faults—subtle issues that can be challenging to detect. Debugging tools such as MSVC, GCC, Valgrind, AddressSanitizer, and others utilize memory patterns (e.g., 0xCD, 0xDD, 0xFE, etc.) to indicate where…
-
Mastering Java Generics: Understanding PECS – Producer Extends, Consumer Super

“`html Java Generics offer adaptability and type security when working with collections and data structures. A fundamental concept related to generics is PECS, which stands for “Producer Extends, Consumer Super.” Advocated by Joshua Bloch, this guideline aids developers in determining the most appropriate wildcard while handling generic types. This article elaborates on PECS and its…
-
Understanding Data Models in Database Management Systems

“`html Data Modeling is a methodology in Database Management System (DBMS) that arranges, structures, and delineates the data within the database, assisting in preserving the integrity and operational efficiency of the data. Data modeling presents a schematic for the database employing components that stipulate relationships and constraints. By clarifying the model, the user can envision…
-
Understanding StackOverflowError in Java

“`html A StackOverflowError in Java arises when a thread’s stack, which holds data about the method invocations and variables, surpasses its size limit. This commonly occurs due to unrestrained recursion, where a method continually invokes itself without a stopping point. Consequently, the stack depletes its available space, leading the program to crash. In this article,…
-
Steer Clear of document.write() in JavaScript

“`html Initially, document.write() was the favored technique for inserting content into a web page. It was quick, straightforward, and beneficial for novice developers. However, as websites became more sophisticated, our approach to building them has evolved. Nowadays, employing document.write() is regarded as unwise due to several valid reasons. In this post, you will discover the…
-
Astronomers Revisit the Mysteries of Twin Star Systems
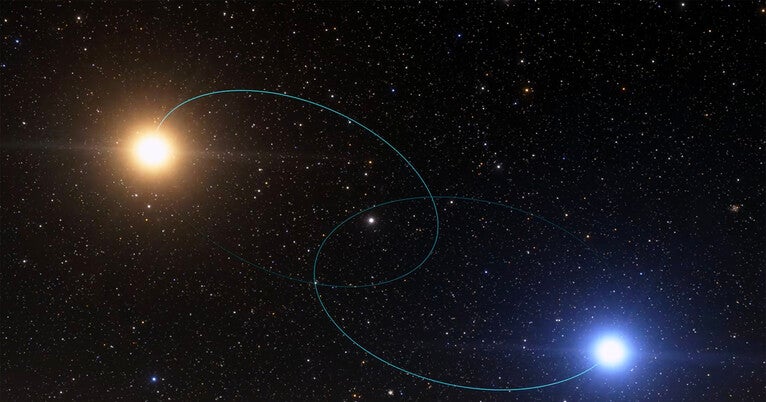
Binary star systems might provide a fresh perspective on planetary development throughout the cosmos, according to a Yale research group claims.
-
Ammit Exposes Vulnerabilities in Drone Supply Chains Through ERP Exploits in VENOM and TIDRONE Operations
A cyber intelligence collective identified as Earth Ammit has been associated with two connected yet separate initiatives from 2023 to 2024 aimed at numerous organizations in Taiwan and South Korea, encompassing military, satellite, heavy industry, media, technology, software services, and healthcare fields. Cybersecurity company Trend Micro reported that the initial phase, designated VENOM, primarily focused…
-
Unlocking the Power of Offensive Security Training: Transforming Your Entire Cybersecurity Team

“`html Various entities across sectors are witnessing considerable surges in cyber assaults, especially aimed at essential infrastructure suppliers and cloud-centric businesses. Verizon’s freshly published 2025 Data Breach Investigations Report identified an 18% year-over-year rise in verified breaches, while the utilization of vulnerabilities as a starting point for access increased by 34%. With the rise in…
-
Invoicing Trickery: Horabot Malware Strikes Six Latin American Countries

“`html Cybersecurity analysts have identified a fresh phishing initiative designed to disseminate malware known as Horabot, aimed at Windows users in Latin American nations such as Mexico, Guatemala, Colombia, Peru, Chile, and Argentina. This initiative is “utilizing meticulously crafted emails that mimic invoices or financial statements to deceive victims into accessing harmful attachments and has…
-
May 2025 Patch Tuesday: Essential Updates You Can’t Miss
Microsoft on Tuesday introduced software enhancements to address at least 70 vulnerabilities in Windows and associated products, including five zero-day weaknesses that are currently being actively exploited. Contributing to the urgency of this month’s patch release from Redmond are resolutions for two additional flaws that now have public proof-of-concept exploits accessible. Microsoft, along with several…
-
Phishing Alert: New Campaign Exploits Google Open Redirects (May 14)
A few weeks back, I encountered a phishing initiative that underscores a persistent problem with open redirect weaknesses in reputable and reliable platforms.
-
Google Launches Advanced Protection for Android Users

Google has expanded its Advanced Protection functionalities to Android gadgets. While it may not suit everyone, it is worth contemplating for users at elevated risk. Wired piece, accessible only via a subscription.
-
Microsoft Patches 78 Vulnerabilities, Five Actively Exploited Zero-Days; Critical CVSS 10 Issue Affects Azure DevOps Server
Microsoft on Tuesday released updates to tackle a total of 78 security vulnerabilities throughout its software portfolio, including a batch of five zero-days that have been actively exploited in the wild. Among the 78 vulnerabilities addressed by the tech giant, 11 are classified as Critical, 66 as Important, and one as Low in severity. A…
-
Decades Later: Alumnus Revisits USC Marshall to Achieve His Degree Dream

BEGINNING: Brad Dow is poised to obtain his bachelor’s degree this week. This achievement has been forty years in the making.
-
The Goto Statement in C++: A Deep Dive

The goto statement in C++ is a control flow element that facilitates unconditional transitions to a designated section of a program within the same function. Despite being a constituent of the C++ programming language, the use of the goto statement is typically discouraged in contemporary C++ development. In this piece, we shall explore what a…
-
Mastering the Switch Statement in C++: A Comprehensive Guide

“`html The switch statement in C++ serves as a robust control flow mechanism that streamlines decision-making in programming. It carries out various code segments depending on the value of a singular expression. This structure is a proficient substitute for if-else if sequences, whether for crafting a basic calculator or easily deciding based on user input.…
-
Understanding Pointers in C++: A Deep Dive into Memory Management

“`html C++ Pointers are variables that hold the address of other variables. They facilitate direct access to memory and enable dynamic memory management. Pointers are extensively utilized in numerous real-world scenarios, including game development. In this article, we will explore what a pointer is, how to create, declare, and initialize a pointer, how to dereference…
-
Mastering the Copy Constructor in C++: A Guide to Efficient Object Duplication

“`html The copy constructor in C++ is a type of constructor employed to generate a new object as a duplicate of an existing one. Managing resources with dynamic memory is crucial. There are two varieties: default and user-defined. This article will cover what a copy constructor in C++ is, when it is invoked, its categories,…
-
Understanding std::max in C++: A Comprehensive Guide to Finding Maximum Values

Assessing values and determining the greatest is a crucial endeavor in C++ programming. The std::max in C++ is a robust standard library function that facilitates the efficient identification of the largest among two or more values. It adeptly accommodates various types, whether dealing with primitive data types or user-defined objects. In this article, we will…
-
Harnessing the Power Function in C/C++: A Programmer’s Guide

The pow() function in C and C++ is a standard library feature utilized for computing the outcome of a base raised to an exponent. It operates effectively with integer, fractional, and negative exponents. In this article, we will explore what constitutes the power of a number, the definition of the power function, its syntax, return…
-
**Mastering String Reversal in C++: A Step-by-Step Guide**

“`html Reversing a string involves the creation of a new string where the characters are positioned in the opposite sequence. This task may appear simple and fundamental to you, yet it is a crucial function in C++ programming. Whether to validate a palindrome or to process data, you need to master the technique of reversing…
-
The Essential Guide to Data Scientist Roles: Key Duties and Skills

The data scientist is an emerging crucial figure within enterprises — a novel category of analytical data specialists. They embody both mathematicians and computer scientists, dominating the realm of big data. Companies today are grappling with immense amounts of unstructured data, which serves as a near-treasure trove that can enhance profits when properly analyzed….Read More.
-
Understanding Project Portfolio Management (PPM)

Every organization manages numerous initiatives, steering them towards objectives. The selection and planning of these initiatives, in addition to their execution, constitute some of the critical responsibilities that require skilled oversight. Aiming to optimize capital and effectively utilize the diverse array of resources, along with overseeing all projects and programs, Project Po…Read More.
-
Unlocking ITIL: Key Concepts, Essential Processes, and Transformative Benefits

Maintaining order and effectiveness in the dynamic realm of Information Technology is vital for any enterprise. This is where ITIL, which stands for Information Technology Infrastructure Library, becomes essential. What Is ITIL? ITIL, or Information Technology Infrastructure Library, represents a detailed framework designed to assist organizations in overseeing their IT services …Read More.
-
Understanding Critical Chain Project Management: A Comprehensive Guide

Critical Chain Project Management (CCPM) The concept of Critical Chain Project Management was introduced and promoted by Dr. Eliyahu M. Goldratt in 1997. Proponents of this project management approach suggest it serves as an alternative to the traditional methodologies defined by PMBOK® and other project management frameworks. In this piece…Read More.
-
Understanding the Iron Triangle in Project Management: A Key to Success

The Iron Triangle of project management illustrates the limitations that may impact the project. Scope, budget, and timeline are the three project limitations that project managers need to navigate. Any alterations to one of these elements will influence the others. To ensure a favorable project result, a project manager sustains the equilibrium and… Read More.
-
Top Project Management Alternatives to Asana for 2025

Teams, regardless of size, frequently need to manage numerous projects with tight deadlines. Coordination among team members and proficient project management are two essential components for consistently delivering successful projects. Tools for project management and collaboration, such as Asana, facilitate the achievement of these project objectives more swiftly by…Read More.
-
Mastering the PMP Exam: A Comprehensive Guide to Syllabus and Duration with Simplilearn

PMP® signifies Project Management Professional—it is the designation granted to anyone who clears the PMP certification examination. Therefore, upon successfully completing the PMP test, you earn the title of Project Management Professional (PMP). The PMP accreditation is the most esteemed individual certification in the field of Project Management and is v…Read More.
-
Project Analyst Salaries in India’s 2025 Job Market: A Comprehensive Overview

As the need for project management experts continues to grow, organizations worldwide will require around 88 million project management specialists by 2027. Significantly, China and India are projected to contribute to over 75 percent of this overall project management job market (Source: PMI talent gap analysis by AEG). Within this…Read More.
-
Fortinet Addresses Critical Zero-Day RCE Vulnerability in FortiVoice Systems

Fortinet has resolved a significant security issue that it reported has been leveraged as a zero-day in assaults against FortiVoice business phone systems. The flaw, identified as CVE-2025-32756, holds a CVSS rating of 9.6 out of 10. “A stack-based overflow vulnerability [CWE-121] in FortiVoice, FortiMail, FortiNDR, FortiRecorder, and FortiCamera could enable a distant unauthenticated attacker…
-
Ivanti Addresses EPMM Vulnerabilities Targeted for Remote Code Execution in Select Attacks

Ivanti has issued security patches to rectify two vulnerabilities in Endpoint Manager Mobile (EPMM) software that have been exploited in attacks to achieve remote code execution. The specific vulnerabilities are enumerated below – CVE-2025-4427 (CVSS score: 5.3) – A flaw in Ivanti Endpoint Manager Mobile that permits unauthorized access to secured resources, enabling attackers to…