-
Detecting Illness: How Humans Use Distant Senses to Identify Sickness

Research: I see ill individuals: Perceptions regarding sensory awareness of infectious diseases are mainly similar across cultures (DOI:10.1016/j.bbi.2025.04.020) If you’re in close proximity to someone during influenza season, how can you discern if they are unwell, particularly in scenarios where they may not be aware themselves? A recent international study conducted by a researcher from…
-
Innovative Medicaid Policy Lab Enhances Data-Driven Discussions
As Congress deliberates over $715 billion in reductions to Medicaid over the forthcoming decade, a new resource from Washington University in St. Louis is assisting in grounding the national conversation in empirical evidence. Initiated earlier this year, the Medicaid Policy Analysis Lab has started publishing a series of relevant policy briefs illustrating how legislative choices…
-
Santiago Schnell Appointed as Dartmouth’s New Provost
The renowned biologist and dean of the University of Notre Dame will commence the position on July 1.
-
Celebrating the Remarkable Recipients of Caltech’s 2025 Distinguished Alumni Award

“`html Annually, the Institute bestows its premier accolade for alumni—the Distinguished Alumni Award—upon individuals who, due to both personal dedication and professional impact, have made significant contributions to a field, the community, or society at large. The 2025 cohort of DAAs—initially revealed this year at Caltech’s 88th Annual Seminar Day on May 17—includes Deborah D.L.…
-
“Unbelievable Breakthroughs from Initial Experiments”

Stanford neuro-oncologist Michelle Monje is exploring a remedy for a lethal childhood brain tumor – and redefining our comprehension of how cancer and brain growth connect.
-
Hazy Hawk Uses DNS Manipulation to Seize CDC and Corporate Domains for Malware Distribution
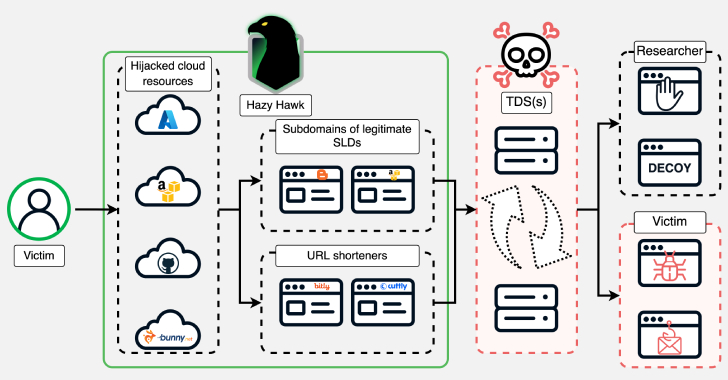
A malicious agent identified as Hazy Hawk has been detected commandeering neglected cloud assets of prominent enterprises, which includes Amazon S3 buckets and Microsoft Azure endpoints, by exploiting flaws in the Domain Name System (DNS) configurations. The seized domains are subsequently utilized to host links that lead users to fraudulent schemes and malicious software through…
-
UT Earns Recognition as a Top Employer for New Graduates by Forbes

Alongside its recognition as a leading employer for recent graduates, Forbes has also identified UT as a coveted workplace and among the finest colleges in the United States. The article UT Named One of Nation’s Best Employers for New Graduates by Forbes first appeared on News.
-
Honoring the Pillars of Education: A Tribute from Medical Students to Their Mentors

“`html Brian Dineen bestows the Humanism In Medicine accolade upon Amjad Musleh, MD (right), during the Distinguished Service Teaching Awards Ceremony on April 15. Throughout this occasion, medical students award faculty members with distinctions. (Photo: Carol Green/WashU) Recently, medical scholars at WashU Medicine acknowledged faculty and residents with Distinguished Service and Teaching Honors for the…
-
Jupiter: A Giant Once Twice Its Size With a Powerful Magnetic Embrace

“`html Grasping Jupiter’s initial evolution aids in clarifying the broader narrative of how our solar system acquired its unique configuration. Jupiter’s gravitational influence, often referred to as the “creator” of our solar system, was pivotal in forming the orbital trajectories of other planets and in shaping the disk of gas and dust from which they…
-
Over 100 Deceptive Chrome Add-ons Discovered: Session Hijacking, Credential Theft, and Ad Injection Unveiled

An unidentified threat entity has been linked to the development of multiple harmful Chrome Browser extensions since February 2024. These extensions appear to be harmless utilities but contain hidden features designed to extract data, accept commands, and run arbitrary code. “The entity constructs websites that pretend to be genuine services, productivity applications, and tools for…
-
Coping Strategies for Mental Well-Being After Recent Storms

A tornado devastated St. Louis on May 16, resulting in five fatalities, damaging over 5,000 structures, and leaving tens of thousands without electricity. Abdalla Salma Abdalla, an assistant professor at the School of Public Health at Washington University in St. Louis, has previously examined the effects of Hurricane Harvey on the psychological well-being of Houston…
-
Unveiling the Web: Insights from Researchers Scanning the Internet

We have utilized our information to pinpoint researchers exploring the web for several years. At present, we are monitoring 36 teams conducting such explorations, and our data stream of the IP addresses employed comprises approximately 33,000 addresses [1].
-
Unlocking the Mysteries of the Kuiper Belt: A Journey Through the Outer Solar System

“`html What is the Kuiper Belt? An overview of the outer Solar System nprevenas Tue, 05/20/2025 – 06:20 What is the Kuiper Belt? An overview of the outer Solar System Monday Article Categories Current Events Science & Tech Cosmos By BBC Type of News Article Outside News “`
-
Exploring Connection Through the Art of Pysanka

Students engage with classmates in Kyiv via a Ukrainian artistic custom.
-
Innovative Indian Startups Shaping the Global Landscape

“`html The Indian startup landscape has evolved beyond a mere national scene; it has now emerged as a worldwide innovation powerhouse. Indian startups are addressing challenges not just within India but on a global scale, utilizing advanced technology, innovative business strategies, and exceptional talent. By 2025, numerous Indian startups are anticipated to thrive internationally across…
-
Choosing Between PMP and MBA: Navigating Your Career Path for 2025
“`html Are you striving for professional advancement but uncertain whether to pursue an MBA degree or a PMP certification? Unsure about what an MBA or PMP involves? This article will assist you in finding answers to these inquiries. This comprehensive guide will address all aspects you need to know regarding both credentials. You will obtain…
-
Understanding IoT Devices: A Dive into the Connected World

“`html The technological advancements observed today are primarily a result of the expansion and evolution of the Internet of Things (IoT). Whether it’s a smartwatch monitoring your heartbeat or a smart fridge compiling your shopping list, IoT gadgets are increasingly becoming integral to our everyday existence. These gadgets prove to be highly beneficial, offering connectivity…
-
Breaking News: Major Developments on May 19, 2025

“`html Florida State University’s College of Medicine recognized the launch of 113 new physicians into practice at the commencement held on May 17. Additionally, it embraced eight new participants in the incoming medical class of 2029 with the graduation of the Bridge to Medical Sciences master’s program. Discover more … Check out the newsletter. The…
-
U-M Launches Innovative Tool to Revolutionize Financial Reporting for Local Governments

Complimentary webinar on June 4 will showcase the Excel to iXBRL Conversion tool A complimentary, open-source tool crafted by the University of Michigan’s Ford School of Public Policy is now accessible to assist local governments in enhancing the accessibility of financial data. Created by the Ford School’s Center for Local, State, and Urban Policy (CLOSUP),…
-
Overcoming Bottlenecks in CO2 Capture and Conversion Technology
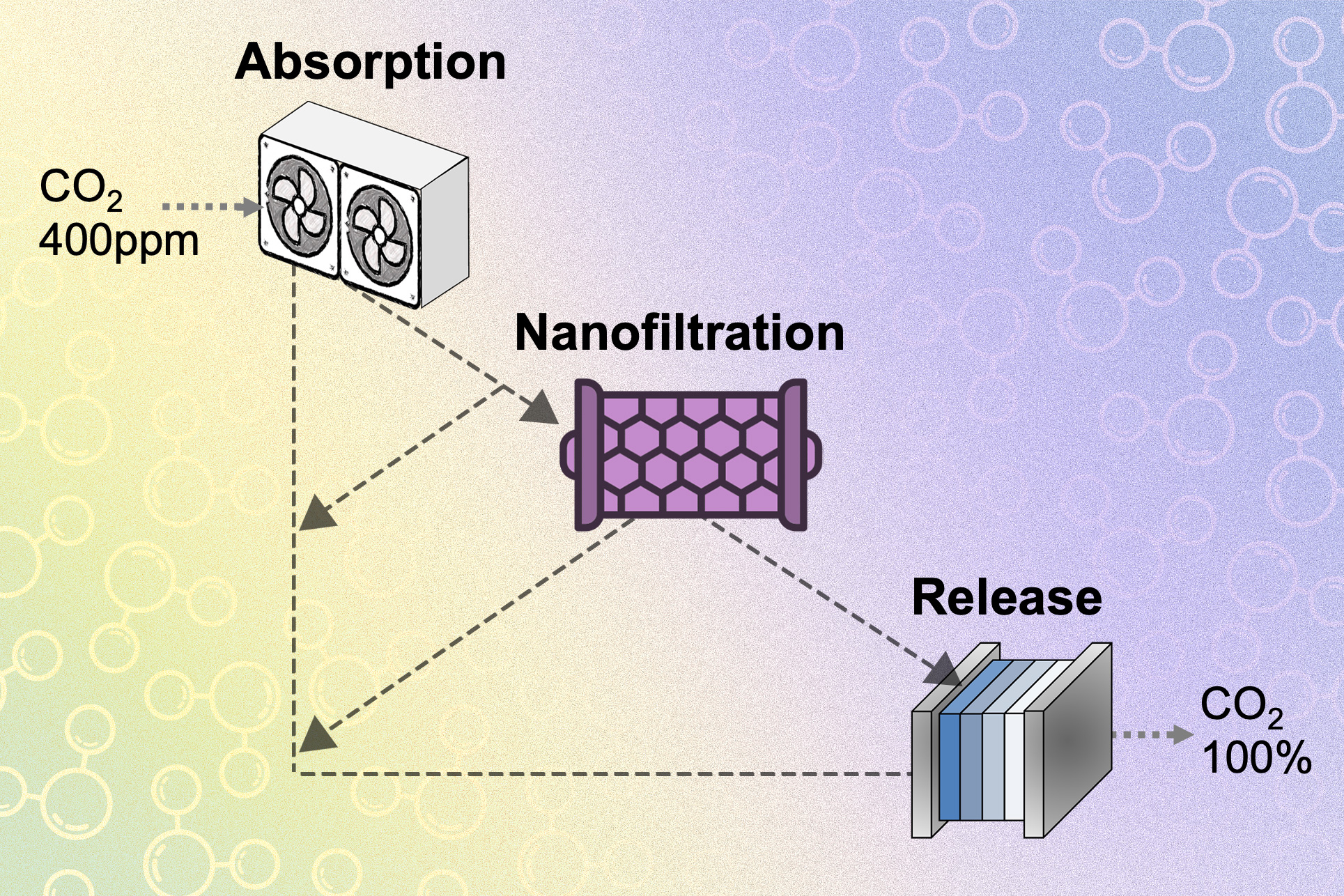
“`html Efficiently eliminating carbon dioxide from the atmosphere is frequently regarded as a vital necessity for addressing climate change, yet methods for extracting carbon dioxide face a compromise. Chemical substances that effectively capture CO₂ from the air do not readily release it once it has been trapped, while substances that release CO₂ efficiently are not…
-
South Asian Organizations Targeted by SideWinder APT Employing Legacy Vulnerabilities and Tailored Malware

High-ranking governmental entities in Sri Lanka, Bangladesh, and Pakistan have become the focus of a recent initiative led by a threat group identified as SideWinder. “The perpetrators utilized spear phishing emails combined with geofenced payloads to guarantee that only individuals in designated nations accessed the harmful material,” stated Acronis researchers Santiago Pontiroli, Jozsef Gegeny, and…
-
Exploitable AWS Default IAM Roles: A Pathway for Lateral Movement and Cross-Service Attacks

Cybersecurity experts have identified hazardous default identity and access management (IAM) roles affecting Amazon Web Services that may enable adversaries to elevate privileges, alter other AWS services, and, in certain instances, even completely take over AWS accounts. “These roles, frequently generated automatically or suggested during the configuration process, provide excessively wide permissions, such as complete…
-
Harnessing Technology for Innovative Solutions: The Power of AI Competitions

As artificial intelligence becomes more widely integrated, students at the University of Georgia are devising creative applications for this technology. For the second consecutive year, learners submitted their projects to the Generative AI Competition, which is sponsored by the Office of Instruction and the Franklin College of Arts and Sciences’ philosophy department, aimed at highlighting…
-
U-M Teams Up with Google to Offer Free Career Certificates and AI Learning for Students
The University of Michigan Center for Academic Innovation and Google are collaborating to offer access to Google Career Certificates and AI Essentials courses at no charge for students registered at all three Michigan campuses: UM-Ann Arbor, UM-Dearborn, and UM-Flint. Over 66,500 University of Michigan students currently have complimentary access to Google Career Certificates, which have…
-
Navigating the Chaos: Essential Takeaways from the 2025 Pentesting Report

In the recently published 2025 State of Pentesting Report, Pentera conducted a survey of 500 Chief Information Security Officers (CISOs) from worldwide organizations (200 from the USA) to gain insights into the approaches, methods, and instruments they employ to manage the multitude of security notifications, ongoing breaches, and escalating cyber threats they face. The results…
-
Chinese Cyber Operatives Utilize MarsSnake Backdoor in Prolonged Assault on Saudi Entity

Threat investigators have uncovered the methodologies of a China-affiliated threat entity known as UnsolicitedBooker that aimed at an undisclosed global organization in Saudi Arabia utilizing a previously unrecorded backdoor referred to as MarsSnake. ESET, which initially identified the cyber group’s breaches aimed at the organization in March 2023 and once more a year later, stated…
-
“Unlocking the Secrets of DoorDash: Tips and Tricks for Maximizing Your Experience”

A DoorDash driver embezzled more than $2.5 million over a span of several months: The driver, Sayee Chaitainya Reddy Devagiri, made high-value orders using a deceitful customer profile within the DoorDash application. Subsequently, by utilizing DoorDash employee credentials, he manually allocated the orders to driver accounts that he and his accomplices had established. Devagiri would…
-
Breakthrough Discoveries Unveil Promising Targets for Alzheimer’s Treatment

By merging insights from numerous extensive datasets, MIT scholars have uncovered various new possible targets for addressing or averting Alzheimer’s disease. The investigation uncovered genes and cellular pathways that had not previously been associated with Alzheimer’s, including one related to DNA repair. Discovering new drug targets is vital since many Alzheimer’s medications developed thus far…
-
Revolutionary Method Quickly Assesses Cell Density, Indicating Health and Growth Status
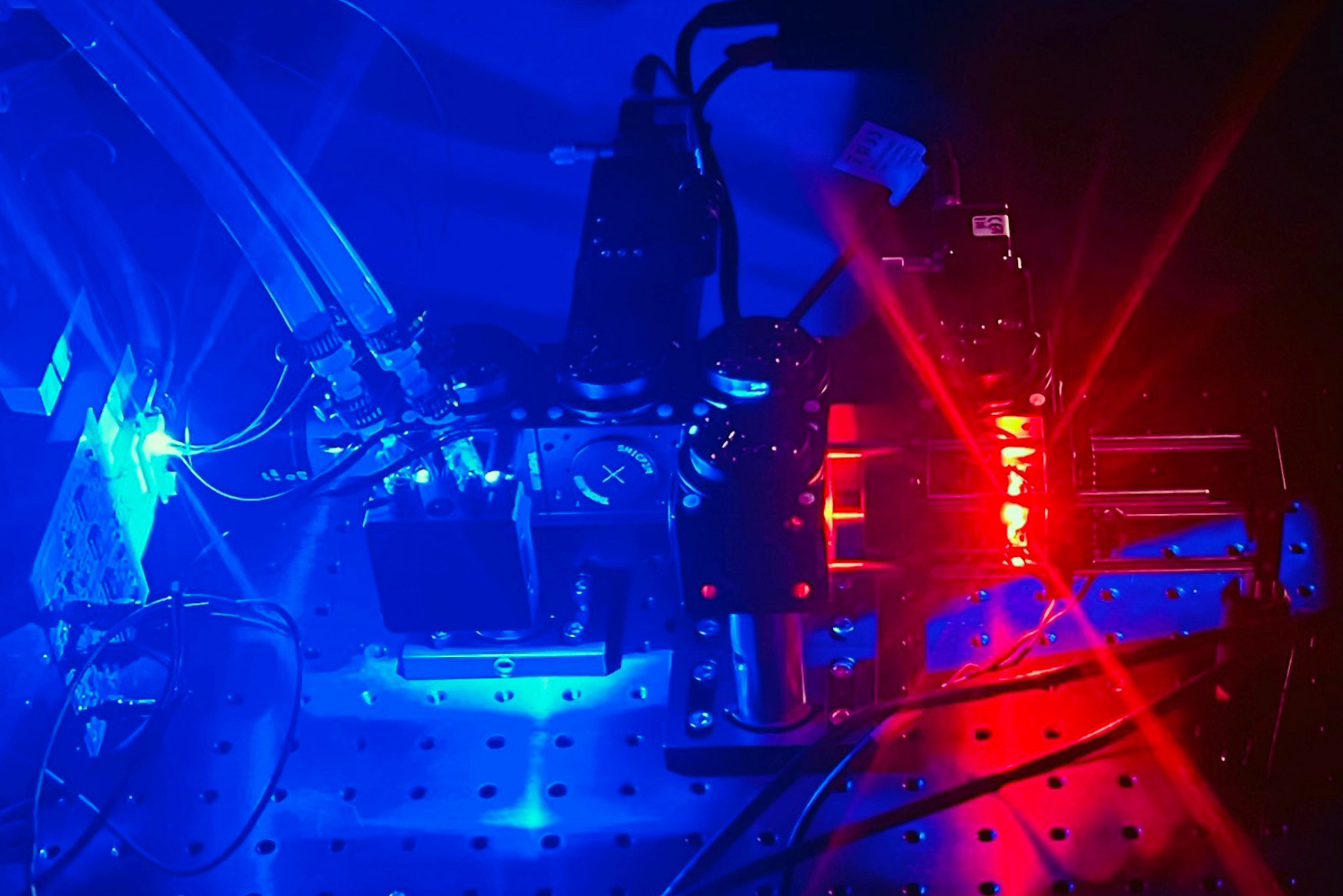
Assessing the density of a cell can disclose a considerable amount regarding the cell’s condition. As cells multiply, specialize, or experience apoptosis, they may absorb or lose water and other substances, which becomes evident through alterations in density. Monitoring these minute variations in the physical condition of cells on a large scale can be quite…
-
Redis Configuration Exploitation: The Rise of Go-Based Malware Deploying XMRig Miners on Linux Systems
Cybersecurity analysts are highlighting a novel Linux cryptojacking initiative that is focusing on publicly accessible Redis servers. This nefarious operation has been dubbed RedisRaider by Datadog Security Labs. “RedisRaider proactively probes random segments of the IPv4 space and employs valid Redis configuration commands to carry out harmful cron jobs on at-risk systems,”
-
Innovative Approaches to Project Management: Discovering Agile Alternatives

In the ever-evolving field of project management, Agile has surfaced as a leader, renowned for its adaptability, agility in responding to alterations, and emphasis on client contentment. Nevertheless, it is not a universal answer. Varied projects necessitate varied approaches, prompting many to investigate substitutes to Agile project management. This investigation…Read More.
-
15 Key Advantages of Total Quality Management (TQM) for 2025

Total Quality Management (TQM) denotes the oversight of processes to improve the quality of products or services to achieve customer satisfaction. This strategy entails ongoing enhancement across all levels of staff by recognizing and removing risks, streamlining the supply chain, and employing continual learning techniques. Studies show that Total Qual…Discover More.
-
Elevate Your Career: The Future of Team Leadership in 2025

Effective guidance is crucial for organizational achievement in the continuously changing contemporary workplace. As we progress into 2025, the position of a team leader has assumed new aspects, requiring a combination of conventional leadership abilities and creative methods for team supervision. In this article, we investigate the Team Leader job description, examining …Read More.
-
The Future of Manufacturing: An In-Depth Exploration

Advanced manufacturing is transforming the production landscape. From the creation of pharmaceuticals to software, robotics to electronic devices, innovation is driving the manufacturing journey forward. Advanced manufacturing technologies boost business competitiveness across various sectors, including machinery, materials, information technology, and electronic data. T…Read More.
-
Unlocking Project Health Metrics: The Essential Guide to Peak Performance

The well-being of a project is a crucial aspect of project management that evaluates the performance and advancement of an initiative. It entails assessing various elements to guarantee a project achieves its aims and outputs. Elements Contributing to Project Well-being Timeline Compliance: Is the project moving forward as per the established schedule? Setbacks can i…Read…
-
Unlocking the Secrets of Product Breakdown Structure: Your Comprehensive Guide
Based on findings from the Project Management Institute (PMI), initiatives with a clearly defined scope are 2.5 times more prone to success compared to those lacking clarity. A Product Breakdown Structure (PBS) serves as a communication instrument in project management, designed to systematically decompose complex projects or product developments into…Read More.
-
Understanding Hybrid Project Management: A Comprehensive Guide
Hybrid project management represents a strategy that merges principles and techniques from both conventional project management methodologies, like waterfall, and agile project management practices. This adaptable and flexible strategy seeks to utilize the advantages of various methodologies to meet the unique requirements of a project. In hybri…Read More.
-
Demystifying Software Project Management: A Comprehensive Guide

In the rapidly changing realm of technology and creativity, software development initiatives act as the cornerstone of contemporary business functions. Nevertheless, the intricacy and magnitude of these projects demand a systematic and organized methodology to guarantee their successful achievement. This is where software project management comes into play. Software project manage…Read More.
-
The Hidden Mental Health Struggles of Journalists in America

BEGINNING: Henrick Karoliszyn established The Freelance Frontier initiative within USC’s Doctor of Social Work program to tackle an escalating concern among reporters who report on distressing occurrences.
-
Malicious Packages on PyPI Target Instagram and TikTok APIs for User Account Validation

Cybersecurity investigators have revealed harmful packages submitted to the Python Package Index (PyPI) repository that function as validation tools for verifying compromised email addresses with TikTok and Instagram APIs. All three packages are presently unavailable on PyPI. Below are the names of the Python packages: checker-SaGaF (2,605 downloads) steinlurks (1,049 downloads) sinnercore (3,300 downloads)
-
Revolutionary Imaging Method Eliminates Water Distortion in Underwater Photography

“`html The sea is brimming with life. However, unless you venture nearby, a significant portion of the aquatic realm can easily stay concealed. This is due to water acting as an efficient veil: Light that penetrates the ocean can refract, scatter, and swiftly diminish as it travels through the dense medium of water and reflects…
-
Yale SOM Commemorates the Graduating Class of 2025

Enveloped by peers, educators, and cherished individuals, graduating scholars were awarded their diplomas during a day filled with ritual and festivity.
-
M.D. Class of 2025: Ready to Revolutionize Medicine and Impact Lives

Family and friends of the 87 graduates, together with YSM faculty, students, and staff, gathered at Amistad Park for the event.
-
Honoring the Class of 2025: A New Chapter for the Graduate School of Arts and Sciences

The Graduate School conferred a cumulative total of 776 degrees, comprising 120 Master of Arts, 258 Master of Science, 126 Master of Philosophy, and 272 Doctor of Philosophy degrees.
-
Yale Divinity School Honors the Graduating Class of 2025
Yale Divinity School Dean Greg Sterling encouraged the 106 graduates to embrace the duty of leadership as they follow their vocations and professions, and to guide with bravery and ethical principle.
-
Celebrating Success and Camaraderie: Commencement 2025 in a Splash of Confetti

Yale’s 324th Commencement event commemorated academic accomplishments and the forging of enduring friendships, recognizing over 4,600 scholars from Yale College, various graduate and professional schools, as well as eight other esteemed individuals.
-
Florida State University President Inducted into Florida Inventors Hall of Fame

“`html Richard McCullough, the President of Florida State University, will be inducted into the latest cohort of the Florida Inventors Hall of Fame. McCullough received accolades for his invention and progression of a specific type of polymer referred to as regioregular polythiophenes along with other innovative organic electronic materials, and for establishing companies that have…
-
Stanford Historian’s Immigration Tome Secures PEN America Nonfiction Prize

Ana Raquel Minian’s In the Shadow of Liberty received recognition for its “impactful message, especially at this moment.”
-
The Lasting Psychological Impact of Cancer in Young Adults

“`html Research: Mental Health Trends Among US Survivors of Adolescent and Young Adult Cancer Over Time Young adult and adolescent cancer survivors show consistently high levels of anxiety and depression throughout their lives, but only anxiety symptoms appear to stabilize as they age, according to researchers from the University of Michigan. The results are detailed…
-
Revitalizing Cultural Entrepreneurship
Yale School of Music graduate Frances Pollock talks about her collaboration with Yale SOM professor Sven Riethmueller to establish a new venture studio that revolutionizes the incubation of cultural assets.
-
Jackson School Class of 2025 Graduates Embrace Change in a World of Challenges

The Yale Jackson School of Global Affairs honored its graduates from the Class of 2025 on May 19, conferring 34 Master of Public Policy diplomas and six Master of Advanced Study diplomas.
-
Revolutionary Breakthroughs in Heart Surgery Enhance Recovery and Survival Rates

Yale’s head of cardiac surgery emphasizes minimally invasive procedures, robotics, artificial intelligence, and improved patient experiences.
-
Innovative Minds at MIT Transform Ideas into Impactful Solutions

“`html Life is somewhat more luminous in Kapiyo these days. For numerous residents in this rural Kenyan locality, the onset of night used to signify the conclusion of schoolwork and other family endeavors. Now, though, the darkness is penetrated by electric illumination from recently solar-powered residences. Inside, children in this off-grid region can study while…
-
The Delight of a Fresh Concept

“`html Behavioral economist Sendhil Mullainathan has never forgotten the joy he experienced the first time he savored a delectable crisp yet gooey Levain cookie. He likens that experience to his encounters with fresh ideas. “That hedonic gratification is very much akin to the pleasure I derive from hearing a new concept, discovering an innovative perspective…
-
The Roots of Extremism: A Natural Pathway to Radicalization

“`html Image by Stuart Simpson © Science & Tech How do radicals become that way? Likely quite naturally. In a new publication, neuroscientist Leor Zmigrod explores the links between brain biology and political ideologies May 19, 2025 long read Excerpted from “The Ideological Brain: The Radical Science of Flexible Thinking” by Leor Zmigrod, Visiting Research…
-
Stacy Jones Takes on Role of VP for Public Service and Outreach at UGA

“`html Stacy Jones, a talented public service, development and communications expert, has been appointed vice president for public service and outreach at the University of Georgia after a nationwide search. Jones is presently the associate vice president and director of the UGA Center for Continuing Education & Hotel. She will commence her new position on…
-
Pioneering the Future of Space Exploration with Dr. Vishnu Reddy

“`html Space preparedness: The frontier of tomorrow, today with Dr. Vishnu Reddy nprevenas Mon, 05/19/2025 – 12:37 Space preparedness: The frontier of tomorrow, today with Dr. Vishnu Reddy Today Categories of the Story Science & Technology Space By Homeland Security Today Type of News Article External News “`
-
USC Women Capture Big Ten Track & Field Championships; Men Finish Fourth

Sophomore Madison Whyte triumphed in the 200m and 400m events and anchored the decisive 4x400m relay.
-
Empowering Change: The Journey of Melanie Saenzpardo
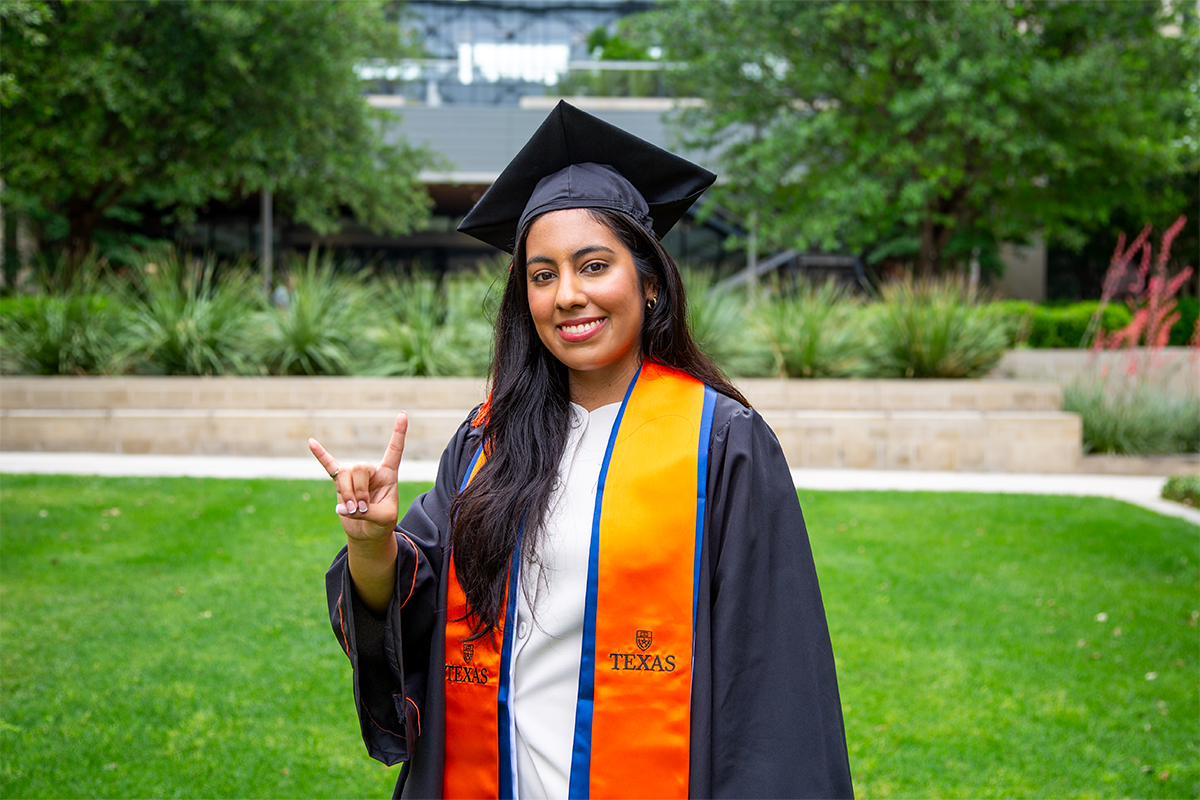
The article Prepared to Transform the Globe: Melanie Saenzpardo was initially published on UT Austin News – The University of Texas at Austin.
-
Silent Struggles: Uncovering the Hidden Epidemic of Eating Disorders in College Life

What does an individual with an eating disorder appear like? The image may not be as straightforward as many assume. Scholars at Washington University in St. Louis conducted an innovative study with a crucial takeaway: Eating disorders do not show bias. A recent survey demonstrated that the likelihood of eating disorders was fairly consistent among…
-
Berkeley Ph.D. Student Curates the Ultimate Word List for the World’s Premier Spelling Bee

Frank Cahill, a student of comparative literature, participated in the Scripps National Spelling Bee during his eighth-grade year. This year, on May 28 and 29, he will find himself on the opposite side of the stage. The post The world’s premier spelling bee is approaching. This Berkeley Ph.D. candidate created the word list. appeared first…
-
Mastering Active Listening in Six Simple Steps

Engaged listening is crucial for preventing misinterpretations and promoting efficient dialogue – particularly regarding contentious subjects.
-
Students Unite Through Community Service at the ‘Spring into Action’ Event

During the Haas Center for Public Service’s yearly gathering, more than 180 students engaged in pursuits such as putting together care packages for campus staff and crafting blankets for nearby shelters.
-
Mastering the Art of Active Listening: Insights from Law Professor Norm Spaulding
The Frosh 101 training facilitator asserts that significant dialogue begins with active listening to genuinely comprehend: “Everyone can observe instances in public affairs where discord and disagreement become counterproductive and fixed, where neither party is actually hearing what the other has to say.”
-
Stanford Rowing Secures Fourth Straight Conference Championship

With triumphs in all five championship finals and four ACC benchmarks, No. 1 Stanford showcased a remarkable display on Lake Hartwell.
-
U.S. Climate Leadership Faces Setback Amidst a Lack of Informed Dialogue

“`html Science & Tech Experts observe a ‘low information’ reversal of U.S. climate dominance The Conemaugh Generating Station in New Florence, Pennsylvania, was set to shut down in 2028. In April, President Trump enacted executive orders aimed at strengthening coal mining and coal-fired power plants. Gene J. Puskar/AP Photo Alvin Powell Harvard Staff Writer May…
-
Tuned In for an Engaging Experience

“`html William Makris, Ed.M. ’00. Photographs by Veasey Conway/Harvard Staff Photographer Campus & Community Eager to listen Newly appointed board president Will Makris anticipates alumni sharing their stories and learning from each other May 19, 2025 6 min read As a business school admissions officer, William Makris, Ed.M. ’00, was guided by a straightforward tenet…
-
Celebrating Achievement and Service: The Joy of Spring Graduation Ceremonies

This spring, over 6,200 diploma recipients stepped onto UT’s graduation platform. Through eight ceremonies, the institution recognized scholarly excellence and the dedication to servant leadership that characterizes the Volunteer ethos. The article Spring Commencement Ceremonies Honor Academic Achievement, Volunteer Spirit was initially published on News.
-
Florida State University Specialist Available to Discuss Recent CDC Findings on Opioid Recovery
“`html Florida State University’s Ellen Piekalkiewicz, an eminent authority in public policy, legislative and governmental affairs, as well as disability rights in the College of Social Work, is open for interviews regarding the recent Centers for Disease Control and Prevention report that revealed the lowest rates of drug overdose fatalities in five years. Piekalkiewicz serves…
-
NASA Selects Rocket Lab for 2026 Launch of Compact Aspera Space Telescope

“`html NASA selects Rocket Lab to deploy shoebox-sized Aspera space observatory in 2026 nprevenas Mon, 05/19/2025 – 10:42 NASA selects Rocket Lab to deploy shoebox-sized Aspera space observatory in 2026 May 16, 2025 Story Categories In the Headlines Science & Innovation Cosmos By Space.com News Article Classification External Coverage “`
-
UA Students Find Healing Through Art: A Pilot Program to Alleviate Anxiety, Depression, and Loneliness

“`html UA scholars can utilize Art Pharmacy to address anxiety, depression, and isolation in initial initiative nprevenas Mon, 05/19/2025 – 10:41 UA scholars can utilize Art Pharmacy to address anxiety, depression, and isolation in initial initiative Today Story Categories Arts & Humanities Health & Wellness In the News By KJZZ News Article Type External News…
-
5 Foods and Habits for a More Restful Night’s Sleep

“`html 5 dietary practices that can enhance your nighttime rest nprevenas Mon, 05/19/2025 – 10:38 5 dietary practices that can enhance your nighttime rest Today Categories of the Story Health & Wellness Science & Technology By NPR Type of News Article External News “`
-
$10 Million Donation Fuels Groundbreaking Longevity Research at USC’s Keck School of Medicine

The contribution from R. Rex Parris and his spouse, Carrol, will facilitate cooperation among specialists in engineering, gerontology, and stem cell exploration to identify remedies for aging-related ailments.
-
Breakthrough in Laser Technology: The U.S. Unveils Its Most Potent Laser yet

“`html Achieving 2 petawatts, the NSF-funded ZEUS facility at U-M facilitates investigations that could enhance healthcare, national defense, materials research, and beyond The ZEUS laser facility at the University of Michigan has approximately doubled the peak power of any other laser in the country with its inaugural experiment at 2 petawatts (2 quadrillion watts). Exceeding…
-
Future Frontiers: Navigating the Challenges of Space Exploration

A simulation platform – featuring actual, hovering spacecraft – would have enabled scientists, businesses, and governmental bodies to evaluate essential space technologies, but a work stoppage directive from the federal authorities has halted development.
-
Yale University Honors Eight Distinguished Individuals with Honorary Degrees

Notable figures awarded honorary degrees at Yale’s yearly commencement comprised leading experts in the fields of arts, sciences, history, engineering, and religion.
-
Mastering the Risk Register in Project Management

A risk register, often referred to as a risk log, is a crucial element of the comprehensive risk management framework. Established in the initial phases of a project, the risk register serves as a mechanism to monitor problems and resolve them as they occur. The risk register is also a significant subject of examination for…
-
Mastering Project Cost Management: Strategies, Advantages, Significance, and Effective Techniques

“This motion picture had a budget of $31 million. With that amount, I could have launched an invasion of some nation.” – Clint Eastwood Now, it’s clear how Clint Eastwood perceives the control of filmmaking expenses. For project leaders, cost regulation is a crucial responsibility, one that remains essential throughout each phase of a project’s…
-
Key Project Management Essentials: Understanding the Project Charter and Scope

Project Charter Why Should a Project Commence Without a Project Charter? Among the most vital and indispensable documents for any project is the Project Charter. Serving as the initial document for a project, it establishes the groundwork for the endeavor. A project charter is a document that provides an overview of the project at a…
-
Mastering Scope Management: Essential Q&A Guide

The Scope Management Knowledge area holds significant importance and is considered one of the simpler knowledge domains for those pursuing project management certification. You can anticipate between 10 to 12 direct inquiries specifically from the scope knowledge area. These questions may range from very simple to somewhat complex and verbose. Typically, the inquiries will revolve…
-
Understanding the Distinction Between Quality Assurance and Quality Control in Project Management

A frequent error that many exam participants commit is mixing up the two operations in Project Quality Management: Execute Quality Assurance and Execute Quality Control. Nevertheless, it’s quite understandable to err in this way, as the distinction between these two activities is nuanced. Unless an individual is actively engaged in this…Read More.
-
Understanding Project Scope Management: A Comprehensive Guide

Ascend to the Esteemed Circle of Project Management Experts with PMP Accreditation from Simplilearn! Every Project Manager’s ultimate goal is to see their projects unfold seamlessly from initiation to completion, without any delays or unexpected expenses. Unfortunately, this is seldom the case. Here, project scope management becomes crucial. It guarantees that a projec…Discover More.
-
Navigating the Landscape of Centralized and Decentralized Contracting in Project Management

Before understanding centralized and decentralized contracting, let us first explore what constitutes a contract. You may often encounter the term “contract.” We all enter into contracts; for instance, your employment agreement with your employer is also a form of contract, outlining the duration of your work and the remuneration you will receive for that labor…Read…
-
Mastering Project Management: The Art of Performance Reporting

What does performance reporting entail? It is a crucial task within project communication management. This process encompasses gathering and sharing project details, reporting on project advancement, resource allocation, and predicting future progress and conditions to different stakeholders, as outlined in the communication management strategy. Throughout the …Read More.
-
Revitalizing the Operating Room: Insights from Arash Motamed

“`html Arash Motamed is the inaugural medical director for sustainability at Keck Medicine of USC, having begun leading sustainability efforts well before taking on that role in 2022. (USC Photo/Gus Ruelas) Share Environment ‘Greening’ the operating room: Arash Motamed As the medical director for sustainability at Keck Medicine of USC, Associate Professor Arash Motamed is…
-
Caltech Unveils Eight Honorees for the 2025 National Brown Investigator Award

“`html Each researcher, acknowledged for inquiry-oriented studies in chemistry or physics, will obtain up to $2 million over a five-year period. The Brown Institute for Basic Sciences at Caltech today unveiled the 2025 cohort of Brown Investigators. This group, the second to be chosen through the Brown Institute for Basic Sciences, consists of eight esteemed…
-
Summer Enrollment for Continuing Education Programs

Summer enrollment is now available! Discover over 100 online and on-site classes across various disciplines. Courses are accessible to all, and STAP funds can be utilized for any class. The term begins the week of June 23. Find out more and register today.
-
RVTools Website Compromised to Spread Bumblebee Malware through Corrupted Installer
The official webpage for RVTools has been breached to distribute a tampered installer for the widely-used VMware environment reporting tool. “Robware.net and RVTools.com are presently unavailable. We are diligently striving to reinstate services and value your understanding,” the firm stated in a communiqué published on its site. “Robware.net and RVTools.com are the sole sanctioned and…
-
Celebrating Gratitude and Love: Highlights from FSU College of Medicine’s Commencement Ceremony

Families gathered prominently on Saturday, both inside and outside Ruby Diamond Concert Hall, as the Florida State University College of Medicine commemorated the achievement of 113 new physicians entering the profession. Additionally, eight new members joined the incoming medical school cohort for 2029 with the graduation of the Bridge to Medical Sciences master’s program. Following…
-
Cornell Gears Up for the 2025 Graduation Ceremony and Celebration

Cornell is set to conduct two Graduation ceremonies for the Class of 2025 and their attendees on Saturday, May 24, at Schoellkopf Field.
-
“Physicist Brad Ramshaw Secures $2 Million Funding as a Brown Investigator”

Brad Ramshaw, assistant professor of physics, has been selected for the 2025 cohort of Brown Investigators. Each investigator, acknowledged for inquiry-based research in chemistry or physics, will be awarded as much as $2 million over a period of five years.