-
Arizona Forms Committee to Develop AI Guidelines Under Governor Hobbs’ Leadership
“`html Gov. Hobbs designates 19 individuals to establish Arizona’s framework for utilizing AI nprevenas Wed, 05/21/2025 – 12:53 Gov. Hobbs designates 19 individuals to establish Arizona’s framework for utilizing AI Today Article Categories University News By KPNX News Article Category External News “`
-
The Impact of Adolescent BMI Fluctuations on Pollution-Related Insulin Resistance

The research directed by USC reveals how the detrimental impacts of air pollution could lead to enduring metabolic issues.
-
Dartmouth Unveils the Davidson Institute for Global Security

Donations amounting to $34 million are allocated for seed research and involvement in an evolving global landscape.
-
“Exploring the Healing Power of Social Bonds: A Documentary on Mental Wellness”

Yale School of Public Health’s Yusuf Ransome and his group of investigators have collaborated with Connecticut independent filmmaker Josh Bibbey to create a documentary focusing on the influence of social bonds in enhancing public health.
-
Yale Planetary Solutions Unveils Innovative New ‘Constellation’ of Funding Opportunities

For its fourth cycle of funding, Yale Planetary Solutions will support 23 initiatives — comprising a new “Constellation”-tier project aimed at eliminating hydrofluorocarbon refrigerant gases.
-
Desire for Gender-Equal Governance: New Global Research Reveals Public Support for Quotas

A recent global research initiative co-authored at UC Berkeley reveals that individuals perceive gender-equitable governance as more favorable for policy — and more advantageous for democracy. Although quotas remain contentious in the U.S., the populace still favors equilibrium over the sustained predominance of men. The post Global study finds most people want gender-balanced government, even…
-
“Navigating a Fly: Steering Insect Flight Like a Vehicle”

“`html Science & Tech ‘We possess a method for guiding a fly as you would a vehicle’ Kenichi Iwasaki collaborating with fruit flies. Photos by Niles Singer/Harvard Staff Photographer Clea Simon Harvard Correspondent May 21, 2025 4 min read Geneticists discover a technique to transform minuscule insects into living automatons Fruit flies, among the most…
-
Beyond the Edge: A Dive into the Fringe Experience

The article For the Fringe was initially published on UT Austin News – The University of Texas at Austin.
-
Yale Junior Honored with Prestigious Projects for Peace Award

Yale’s Zakira Bakhshi received a Projects for Peace grant for her efforts that emphasize the relationship between climate and conflict, especially in vulnerable communities.
-
Assessing Key Chemicals Behind Los Angeles Smog Issues

“`html The Los Angeles area has some of the most contaminated air in the United States, consistently failing to meet benchmarks established by the Environmental Protection Agency over the past decade. Recently, Caltech scientists have measured the concentrations of a smog component known as ammonium nitrate, a molecule that has been notoriously challenging to quantify,…
-
Do Groovy Brains Offer Enhanced Efficiency?

A recent investigation reveals that the extent of minor indentations on the brain’s exterior correlates with enhanced network interconnections and improved reasoning skills. The article Are groovy brains more efficient? was initially published on Berkeley News.
-
Empowering Change: PKG IDEAS Challenge Backs Innovative Student-Led Social Ventures

“`html On Wednesday, April 16, members of the MIT community assembled at the MIT Welcome Center to commemorate the annual IDEAS Social Innovation Challenge Showcase and Awards ceremony. Hosted by the Priscilla King Gray Public Service Center (PKG Center), the event acknowledged 19 student-led teams who dedicated the spring semester to devising and executing solutions…
-
The Impact of AI Art on the Market: A Win for Consumers, a Challenge for Artists
A recent investigation discloses that the implementation of AI enhances revenue while pushing out human creators.
-
The Linguistic Divide: How AI is Overlooking Non-English Speakers

Recent studies investigate the groups and societies that are being overlooked by AI technologies, resulting in lost chances and heightened dangers from prejudice and false information.
-
Russian Cybercriminals Target Email and VPN Flaws to Monitor Ukraine Aid Operations

Russian cyber adversaries have been linked to a government-backed initiative directed at Western logistics firms and technology corporations since 2022. The operations have been evaluated as being coordinated by APT28 (also known as BlueDelta, Fancy Bear, or Forest Blizzard), which is associated with the Russian General Staff Main Intelligence Directorate (GRU) 85th Main Special Service…
-
Propose a ‘Creative Daydreaming Zone’ to Your Boss
“`html Inquire with your supervisor: Could we set up a ‘daydreaming workspace’? nprevenas Wed, 05/21/2025 – 08:44 Inquire with your supervisor: Could we set up a ‘daydreaming workspace’? Tuesday Article Categories Health & Wellness Current Events Science & Technology By Big Think Type of News Article External News “`
-
Chasing the Cosmic Dawn: Astronomers’ Grand Adventure into the Universe’s Origins

“`html Astronomers’ grand expedition to observe the cosmic dawn nprevenas Wed, 05/21/2025 – 08:43 Astronomers’ grand expedition to observe the cosmic dawn Tuesday Categories of the Story In the Headlines Science & Innovation Cosmos By Scientific American Type of News Article Outside News “`
-
The Science Behind Why Exercise is Beneficial for Your Health
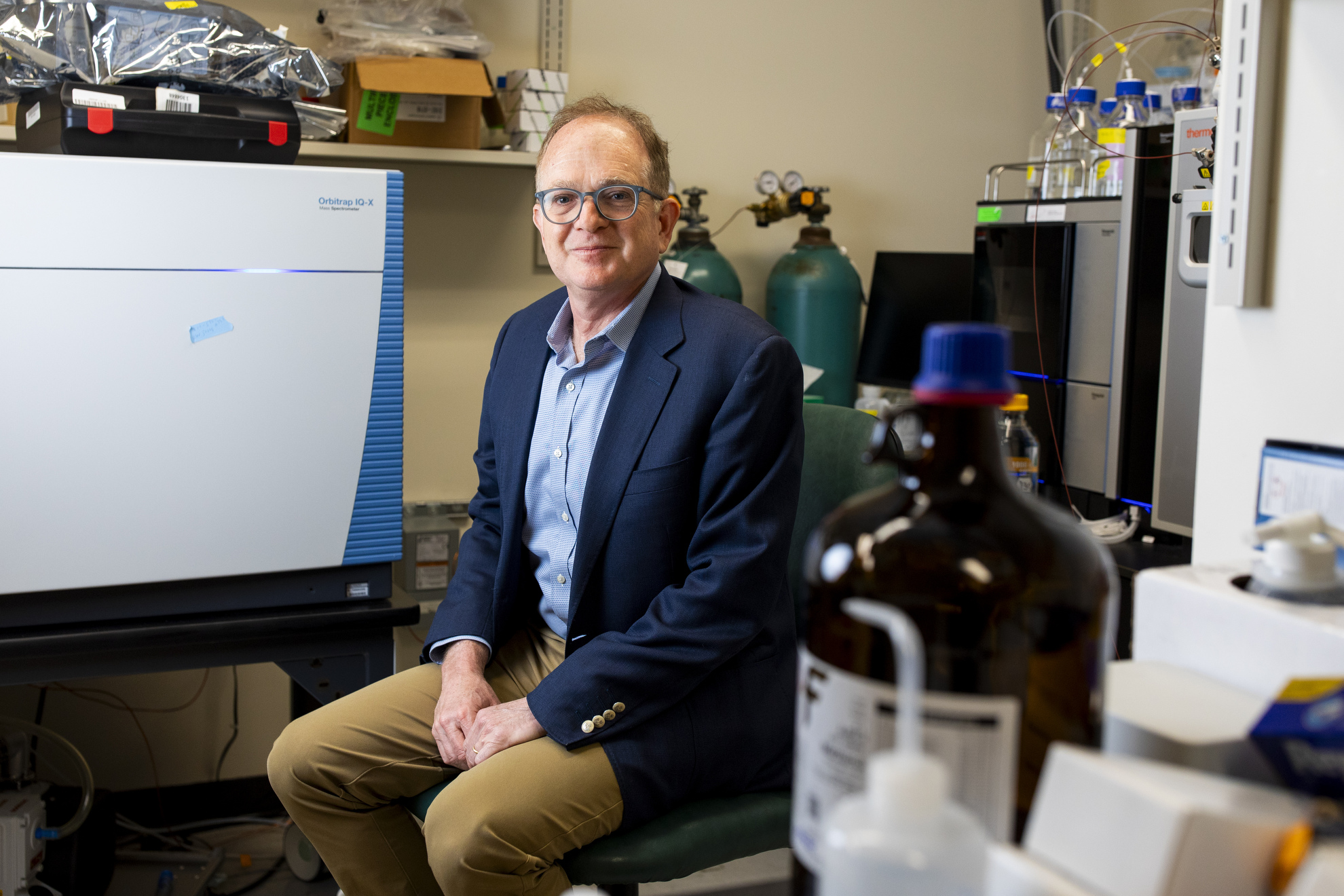
“`html Health We recognize exercise is beneficial for you. Why? He’s exploring it. Building on years of study, Robert Gerszten aims to identify movement’s molecular advantages Anna Lamb Harvard Staff Writer May 21, 2025 4 min read Robert Gerszten in his laboratory. Veasey Conway/Harvard Staff Photographer Part of the Profiles of Progress series We understand…
-
Crypto Confidence Scam Takes a New Turn: What You Need to Know
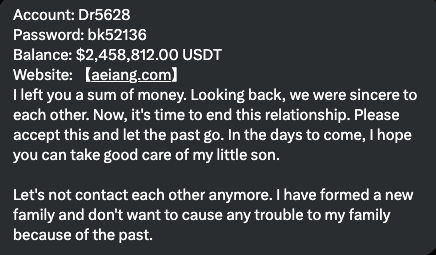
In February, we had several entries concerning scams related to crypto wallets. These scams utilized YouTube comments, but they also occurred on various other platforms and messaging apps, not solely on YouTube [1]. The fraudulent scheme was rather intricate: The perpetrator shared the secret key to their crypto wallet. Typically, this would jeopardize their crypto…
-
Mastering Group Discussions: Essential Strategies for Success

Group Discussions (GD) and personal interviews play a crucial role in academic admissions, campus recruitment, and job selection. Both activities evaluate not just knowledge of the subject matter but also verbal skills, analytical thinking, and collaboration abilities. By fostering clear thought, self-assurance, and showcasing effective participation, you can enhance your readiness to excel in these…
-
The Dynamic Role of a Scrum Master: Key Responsibilities Explained

“`html A Scrum Master serves as a servant-leader facilitating Agile teams to function effectively and maintain focus on their objectives. By 2025, the responsibilities of the Scrum Master will evolve from what was traditionally recognized in 2020. With the increasing prominence of Agile across multiple sectors, Scrum Masters are becoming pivotal in steering teams towards…
-
Exploring the Power of What-If Analysis in Excel

“`html In today’s data-centric landscape, making educated choices is vital in every facet of business and personal finance, along with numerous other areas, such as predictions. Microsoft Excel, a vital part of the analytical and efficiency toolbox, offers a robust feature known as What-If Analysis. This suite of tools and functionalities enables users to simulate…
-
Mastering the Calculation of Standard Deviation in Excel

“`html Standard deviation serves as a crucial statistical indicator that aids in comprehending the dispersion of values within a dataset. Simply put, it illustrates how much the figures vary from the average (mean). Whether you’re engaged in education, finance, or research, grasping standard deviation empowers you to evaluate trends and make well-informed choices. This article…
-
Collegiate Cup Champions Unite for Coral Reef Conservation

In the six weeks preceding Earth Day, over 200 Cornell student-athletes, coaches, and community participants engaged in physical activities not only to enhance their fitness but also to revive corals in the South Pacific.
-
Revolutionizing Freshness: A Breakthrough in Produce Preservation Technology

We’ve all experienced the prick of remorse when fruits and vegetables spoil before we have a chance to consume them. Recently, investigators from MIT and the Singapore-MIT Alliance for Research and Technology (SMART) have demonstrated that they can prolong the freshness of harvested produce by injecting melatonin using compostable microneedles. This is significant because the…
-
“Embracing the Unexpected: The Power of Miracles”

Stanley Cook commends student speaker Nathan Barry (foreground with yellow tassel) after the latter’s speech. (Photo: Joe Angeles/WashU) The visitors’ area at the Missouri Eastern Correctional Center (MECC) is characterized by harsh surfaces. Featuring tiled flooring, cinder block walls, glass partitions, and robust steel doors, the space is stark. However, on May 14, the room…
-
Unveiling the Potential of Potassium Ion Channel Mutations in Drug Innovation
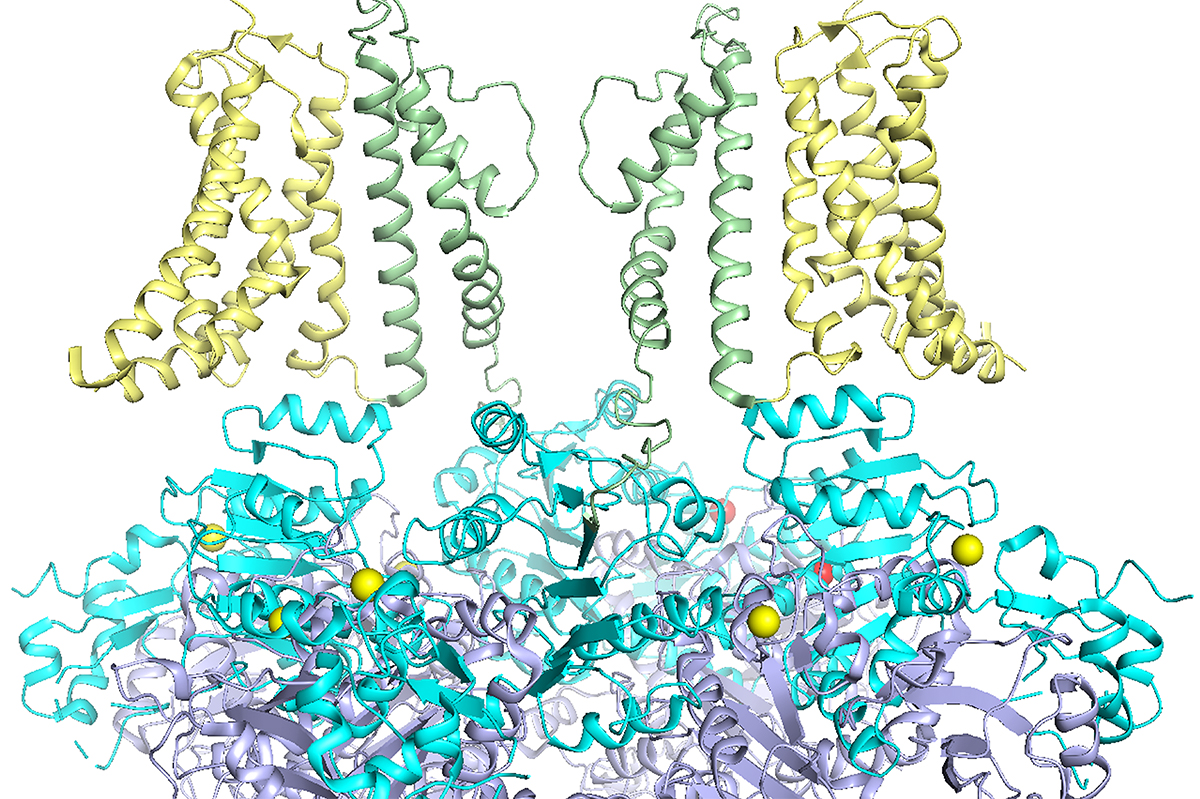
Ion channels play a crucial role in nearly all bodily functions, from maintaining regular heart rhythms to facilitating muscle movement and enabling internal communication. When any disruptions occur within these ion channels, it can lead to severe consequences for the organism. Jianmin Cui, a faculty member specializing in biomedical engineering at the McKelvey School of…
-
Navigating the Journey of an Honors Thesis

Collaborating intimately with instructors, undergraduates engage in bold research and innovative initiatives.
-
Yale’s Budget Lab Marks One Year of Trailblazing Policy Insights

In its inaugural year, The Budget Lab at Yale has developed into a prominent national authority in policy evaluation, addressing several of the most intricate and urgent economic challenges confronting the nation presently.
-
Revolutionary CRISPR Advances: Paving the Way for Neuron Repair

Researchers at Stanford have created a technology that transports RNA to injured neurons and encourages regeneration – opening up possibilities for new therapies for neurodegenerative conditions such as ALS and spinal muscular atrophy.
-
The Rise of Maiya Johnson: A Trailblazer’s Journey

“`html Maiya Johnson selected Florida State University for its outstanding research initiatives. At FSU, she has partaken in scholarly research and community engagement, underscored by her honors thesis and leadership roles. “I was aware that FSU was among the most prestigious research establishments in Florida, with students from the College of Arts and Sciences producing…
-
Innovative Ways Spartan Researchers Safeguard Your Family’s Health

MSU researchers are advancing towards identifying practical solutions that assist families in leading their healthiest lifestyles.
-
MSU Hosts Fifth Annual Juneteenth Celebration to Honor Freedom and Heritage
Sign up for the complimentary learning event at the Multicultural Center.
-
The Future of Debt Collection: Will AI Take the Lead?

Recent studies co-authored by James Choi from Yale SOM reveal that individuals are less inclined to honor a promise to repay a debt when it’s directed toward an AI agent.
-
Surge in PureRAT Malware: A 400% Increase in 2025 Targeting Russian Enterprises
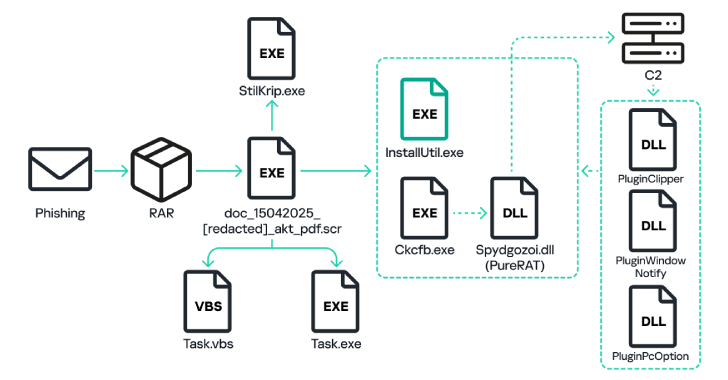
Russian entities have been targeted by a phishing initiative that spreads malware named PureRAT, as per recent insights from Kaspersky. “The operation directed at Russian companies commenced in March 2023, yet in the initial third of 2025, the frequency of assaults increased fourfold compared to the same timeframe in 2024,” the cybersecurity firm stated. The…
-
FSU Theatre Celebrates Senior Talents in the Heart of NYC

The article FSU Theatre Highlights their Graduating Students in NYC was initially published on Florida State University News.
-
Important Announcement: Upcoming Student Fee Adjustments

“`html Florida State University announces a public statement regarding intended rises in student fees effective Fall 2025. Information about the suggested fee hikes can be found at https://tuition.fsu.edu/proposed-tuition-and-fees. The FSU Board of Trustees will review the proposal during its meeting at 3:30 p.m. on June 12, 2025 (the schedule of meetings is subject to alteration).…
-
Building Bridges: How Positive Policies Foster Trust Between Residents and Police

An increasing number of Michigan communities are implementing strategies to enhance police-community interactions, with local authorities witnessing a rise in trust among residents for law enforcement where specific practices have been established. The recent Michigan Public Policy Survey, executed by the University of Michigan’s Center for Local, State, and Urban Policy, identifies two particular policies…
-
Deceptive Kling AI Facebook Ads Spread RAT Malware to More Than 22 Million Users
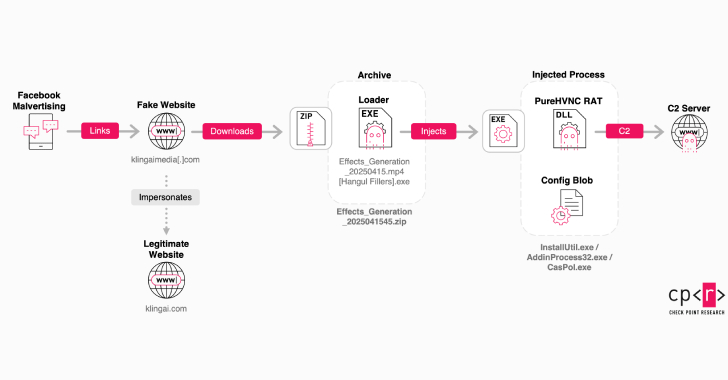
Counterfeit Facebook profiles and paid advertisements on the social networking site are being utilized to lead users to fraudulent websites posing as Kling AI, aiming to deceive individuals into downloading harmful software. Kling AI is a platform driven by artificial intelligence (AI) that generates images and videos from textual and visual cues. Introduced in June…
-
Fortifying Your CI/CD Pipelines with Wazuh

Continuous Integration and Continuous Delivery/Deployment (CI/CD) pertains to methodologies that automate the process of coding and distributing to various environments. CI/CD pipelines are essential in contemporary software development, guaranteeing that code is regularly tested, constructed, and deployed swiftly and effectively. Although CI/CD automation speeds up software distribution, it may also bring about security
-
Understanding the Dynamics of Human-Lion Conflict

Lions encounter numerous dangers. Humans rank among the most significant, according to recent findings from the University of Georgia. Between 1980 and 2018, humans claimed the lives of 698 lions in regions surrounding Etosha National Park in northern Namibia. This equates to an estimated 22 lions per year, though experts suggest this figure is likely…
-
Mastering Phishing Attack Detection: The Tycoon2FA Approach

“`html It requires merely one email to jeopardize a complete system. A solitary, skillfully designed message can evade filters, deceive staff, and provide intruders with the entry they require. If unnoticed, these dangers may result in credential theft, unauthorized entry, and even extensive breaches. As phishing strategies grow increasingly elusive, they can no longer be…
-
Unveiling a PWA JavaScript Vulnerability That Sends Users to Adult Scam Applications

“`html Cybersecurity analysts have unveiled a recent initiative that utilizes harmful JavaScript injections to divert mobile site visitors to a Chinese adult-content Progressive Web App (PWA) fraud. “Although the payload is not innovative (yet another adult gambling fraud), the means of delivery is noteworthy,” c/side investigator Himanshu Anand stated in a Tuesday evaluation. “The harmful…
-
The Rising Trend of AI in Polling and Surveys

I was already aware of the diminishing response rates for polls and surveys. The proportion of AI bots that engage with surveys is also rising. Solutions are challenging: 1. Enhance survey engagement. We ought to progress beyond tedious, grid-like surveys and start crafting experiences that individuals genuinely wish to finish. This includes mobile-first designs, shorter…
-
Trojan Earns Esteemed Fellowship at Mayo Clinic

Sure! How can I assist you with “Gianna Marino”? Would you like information, a summary, or something specific related to this name?
-
Unlocking Potential: How Summer Internships Propel Community College Students Toward Career Success
With assistance from Agilent Technologies, the USC-Cerritos College Summer Research Internship in Sustainability enables first-generation students to follow STEM career paths.
-
Google Chrome Introduces Automatic Password Updates for Enhanced Security
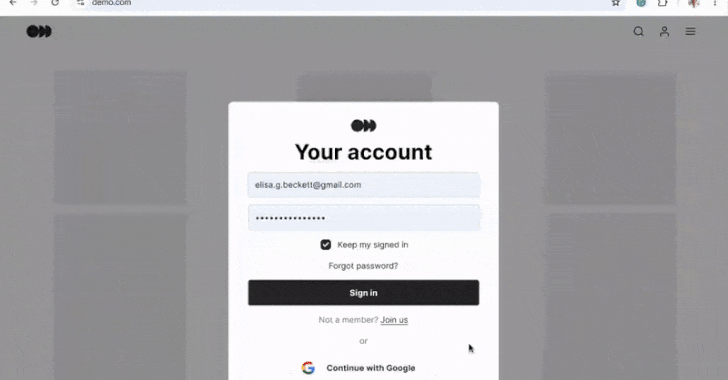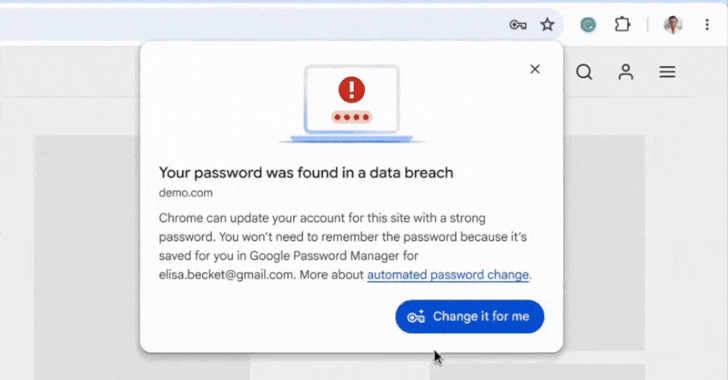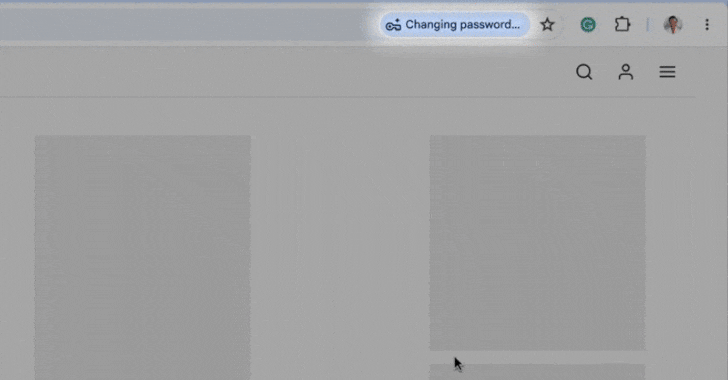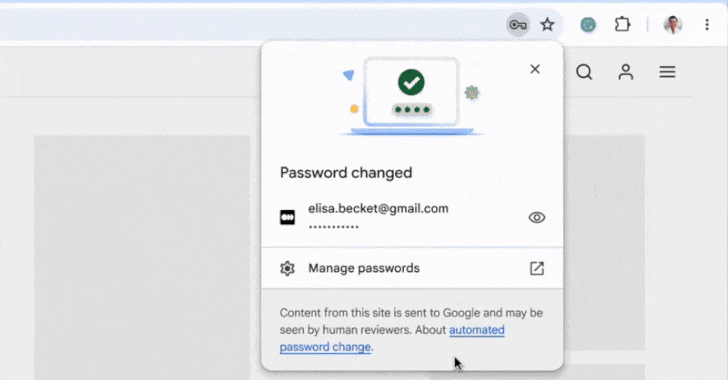
Google has revealed an innovative functionality in its Chrome browser that allows the integrated Password Manager to automatically update a user’s password upon identifying compromised credentials. “When Chrome notices a compromised password during the sign-in process, Google Password Manager provides the user with an option to rectify it automatically,” stated Google’s Ashima Arora, Chirag Desai,…
-
Mastering Asana: A Beginner’s Guide to Getting Started

In today’s environment of escalating customer expectations, heightened rivalry, and globally distributed teams, organizations cannot afford to lag behind. Projects must progress smoothly, and timelines must be adhered to. However, with remote staff located at great distances, it’s increasingly likely that productivity may suffer. When this occurs, performance…Read More.
-
Choosing Between Slack and Trello: Which Collaboration Tool Suits Your Needs?

Slack and Trello are two project management tools that are currently gaining immense popularity. Although both platforms are utilized for overseeing projects or workflows, they fulfill different purposes. Trello simplifies project organization for teams, whereas Slack primarily functions as an instant messaging tool, incorporating some task management capabilities. We will discuss t…Read More.
-
Understanding the Distinctions Between Performance Management and Performance Appraisal

The achievement of an organization, regardless of its scale, predominantly relies on the effectiveness of its workforce. Therefore, it is crucial to monitor employees’ performance. While performance management and performance appraisal are frequently used synonymously, they actually represent distinct concepts that serve different purposes in assessing and improving the…Read More.
-
Mastering Team Management: 50+ Innovative Tips and Strategies for 2025

Cultivating robust teams has consistently been a crucial aspect of a thriving workplace culture. However, as an increasing number of employees operate remotely, overseeing these teams has grown more intricate. Regardless of whether staff frequently work in the office or rarely interact in person, contemporary managers must prioritize communication, trust, and transparency to achieve their…
-
Understanding the Role of a Project Analyst: Key Skills for Success

A project manager holds a crucial position in project administration where tasks, objectives, timelines, and unforeseen events are interconnected. Nonetheless, overseeing a project efficiently is often more complex than it appears and necessitates the involvement of multiple individuals. You might find the expertise of a project analyst beneficial in such scenarios. A project analy…Read More.
-
The Role of a Program Director: A 2025 Perspective

A program director manages every element of the organizational initiative, including project budgeting, recruitment of staff, and promoting the program to potential participants. They are also accountable for establishing the program’s objectives, assigning responsibilities to team members, and setting distinct deadlines. This article will assist you in discovering more about the program director …Read More.
-
Must-Have Operations Management Tools for 2025!

The incorporation of AI and advancements in tools and technologies have greatly aided enterprises. With accessibility, automation, remote functionality, collaboration, and communication, the operations domain has surged in efficiency. Consequently, a variety of operations management tools are accessible to elevate productivity, improve decision-making,…Read More.
-
Mastering the Path to Risk Management Success!

Risk managers possess distinct abilities, expertise, and insight in recognizing and assessing risks that may influence organizational goals. This necessitates a comprehension of the financial landscape and regulatory frameworks, as well as policy and strategic management. The essential elements of becoming an accomplished risk manager involve acquiring knowledge and continuously updating oneself i…Read More.
-
Roles and Responsibilities in Effective Risk Management

Every organization necessitates a robust risk management strategy to thrive and excel over time. This strategy involves recognizing potential risks, assessing those identified, and subsequently overseeing the acknowledged risks. Risk management adheres to a structured approach that outlines the responsibilities and functions of the individuals involved to address all potential…Read More.
-
Navigating the Role of a Risk Manager: An In-Depth Overview!

In today’s dynamic business landscape, risk managers play a crucial role in safeguarding an organization’s integrity. This article delves into the role of a risk manager, outlining the key responsibilities, required skills, and the importance of the role in mitigating potential threats. Understanding your role in risk management is vital for organizations…Read More.
-
WashU Community Collaborates with Neighbors for Tornado Recovery Efforts

The Danforth Campus at Washington University in St. Louis experienced significant damage during the catastrophic tornado that struck parts of St. Louis on May 16, resulting in damaged roofs and concrete. Furthermore, the storm uprooted numerous large trees, obstructing roads and causing extensive power and technology failures. However, according to Chancellor Andrew D. Martin, this…
-
Innovative Startup Develops Century-Long Bridges Using Corrosion-Resistant Steel

“`html As per the American Road and Transportation Builders Association, one-third of all bridges require refurbishment or replacement, totaling over 200,000 structures nationwide. A significant factor contributing to the deteriorating state of America’s infrastructure is rebar that has gathered rust, causing cracks which ultimately fragment the surrounding concrete, increasing the likelihood of bridge failures. Currently,…
-
Inspiring Moments from USC’s 2025 Commencement Ceremony

GRADUATION: Why confine yourself to insights from merely one orator? View the video to witness selected moments from various motivating speeches that occurred during the ceremonies of the previous week.
-
KrebsOnSecurity Faces Massive 6.3 Tbps DDoS Attack
“`html KrebsOnSecurity encountered a nearly record-setting distributed denial-of-service (DDoS) assault last week, registering over 6.3 terabits of data per second (with a terabit equating to one trillion bits). This swift attack appears to have functioned as a test for an expansive new Internet of Things (IoT) botnet, capable of initiating debilitating digital strikes that few…
-
Celebrating a Century: Phi Kappa Phi Honor Society’s Legacy at FSU

The most ancient academic honor society at Florida State University commemorated the chapter’s centennial anniversary during its annual initiation event. The FSU chapter of the Phi Kappa Phi honor society celebrated the significant milestone during its annual initiation event on April 9 at the Grand Ballroom located in the FSU Alumni Center. “Phi Kappa Phi’s…
-
Sunny Strategies for a Vibrant Summer: Expert Advice from Florida State University

“`html As temperatures rise and summer vacations commence, it’s vital for individuals to focus on their health and wellness. Florida State University’s Amy Magnuson serves as the director of University Health Services (UHS) and is an experienced expert in nutrition, public health, and wellness. Under her guidance, UHS has recently been acknowledged as No. 14…
-
The Bold Gamble of Songbirds: A Path to Genetic Riches

Credit: Benjamin Winger, University of Michigan Songbirds that undertake the challenging migration from their breeding grounds in northern boreal forests to warmer southern regions during winter may gain a reward of increased genetic variation, as indicated by a study from the University of Michigan. Researchers at U-M discovered that songbird species migrating from the boreal…
-
Unraveling the Quantum Nature of Gravity
“`html One of the most significant open inquiries in contemporary physics is: “Is gravity quantum?” The other essential forces — electromagnetic, weak, and strong — have all been effectively articulated, but a complete and coherent quantum theory of gravity is still not available. “Theoretical physicists have suggested numerous potential scenarios, spanning from gravity being fundamentally…
-
The Priceless Pursuits: Why Some Treasures Are Beyond Wealth

“`html Robert Waldinger. Harvard file photo Nation & World Elements that money cannot procure — such as joy and improved wellness This is the conclusion of the Harvard Study of Adult Development, which has produced findings beneficial to various issues over its 87-year history Liz Mineo Harvard Staff Writer May 20, 2025 4 min read…
-
“Unveiling Hidden Mysteries”

“`html Cristina Morilla, associate paintings conservator, engaged in restoring a portrait of King Philip of Spain at Harvard Art Museums in 2020. “In specific instances, conservators themselves are artisans,” describes Brenda Bernier, the director of Preservation Services at Harvard Library. To comprehend how and why an artifact is deteriorating, understanding its assembly is crucial. “Each…
-
Imprint Secures $15 Million in Funding from Cornell Tech’s Runway Initiative

Imprint, an institution established at Cornell Tech focused on deciphering the body’s immune recollection and discovering the origins of persistent ailments, revealed that it has secured more than $15 million in financing.
-
Exploring the Intersection of AI and Theology: Insights from the Divinity School Conference
Inquiries regarding the significance of artificial intelligence and its consequences for human dignity and welfare were a focal point at a prominent conference held at Yale Divinity School last month.
-
Celebrating Student Innovation: The Simpson Prizes Highlight Research in Evolution and Fossils
Yale postgraduate scholars Chase Brownstein, Lisa Freisem, and Alexander Ruebenstahl were acknowledged for outstanding investigations.
-
Charting a Course Through Inflammatory Bowel Disease Treatment

Therapies for inflammatory bowel disorder, encompassing ulcerative colitis and Crohn’s disease, have progressed to emphasize managing inflammation even prior to the onset of symptoms.
-
Digitizing Knowledge: Matthew Blair ’26 Transforms a Student Magazine into a Digital Archive
Numerous editions of “The Yale Scientific Magazine,” the earliest collegiate scientific journal in the nation, are now accessible to scholars in digital format on EliScholar, the library’s digital platform for academic publishing.
-
Celebrating Innovation: The First Keggi Memorial Lectureship Pays Tribute to a Trailblazer

A fresh lecture series at Yale honors the remarkable life, pioneering accomplishments, and global prominence of orthopedic surgeon Kristaps J. Keggi.
-
Xavier Becerra Urges UC Berkeley Graduates: “Now is the Moment for Public Health Advocacy”

“We might not have the option to select the difficulties we encounter during our era, but we certainly have the power to decide how we confront them,” stated School of Public Health keynote speaker Xavier Becerra, who previously held the position of Secretary of Health and Human Services during the Biden administration. The post Xavier…
-
A Fresh Tangle: The Resurgence of the US-Mexico Tomato Trade War with July’s 21% Tariffs Set to Ignite Tensions
This conflict regarding tomatoes commenced in the 1990s when an increase in tomato imports from Mexico led U.S. farmers to question whether they were being offered at excessively low prices. The post The Conversation: Tomato Trade Dispute Between the US and Mexico Is Heating Up Again – with 21% Tariffs Expected in July first appeared…
-
Empowering Veterans: Colleges and Universities Championing the Transition to Civilian Life
“`html Colleges and institutions that assist veterans as they transition into civilian existence nprevenas Tue, 05/20/2025 – 11:55 Colleges and institutions that assist veterans as they transition into civilian existence Today Story Categories In the News University News By USA Today Article Type External News “`
-
The Vital Role of University Research in Shaping Our Future

“`html Illustrate, don’t narrate, the significance of university research nprevenas Tue, 05/20/2025 – 10:50 Illustrate, don’t narrate, the significance of university research Today Article Categories Current Events Research & Innovation By The Chronicle of Higher Education Type of News Article Outside News “`
-
Exploring Digital Humanities: A New Frontier in Knowledge

English, philosophy, and comparative literature are not commonly thought of when discussing large datasets. Nevertheless, the nexus of literature and data analysis is precisely where Anna Preus specializes. World According to Sound · Ways of Knowing 01: Digital Humanities Click to see the entire transcript of the episode Ways of Knowing The World According to…
-
UT Introduces Draft Principles for Ethical AI Integration in Education

The newly developed framework is available for public input prior to its official release this autumn. The article UT Unveils Proposed Guidelines for Responsible Use of AI in Teaching and Learning was initially featured on UT Austin News – The University of Texas at Austin.
-
WashU Medicine Fungal Experts Tackle Commonly Misidentified Infections

“`html When it pertains to inquiries regarding fungal infections, Andrej Spec, MD, has established himself as the primary authority for healthcare professionals globally. Weekly, he receives 10 to 15 inquiries from doctors grappling with intricate fungal diagnostics or treatment concerns. He has addressed questions from all over the U.S. and as far away as China,…
-
Triumphant SOM Graduates Honored with Dean’s Mission & Impact Award

The learners were acknowledged for their efforts toward the Yale SOM and New Haven communities.
-
Cherishing Graduation Moments at Sterling Memorial Library

Graduates, relatives, acquaintances—and library personnel—assembled, marched, and stood for photos in front of Sterling Library to honor the Class of 2025 during Yale’s 324th Commencement.
-
Integrity and Responsibility: The Hallmarks of Yale Law School’s Class of 2025

The Yale Law School Class of 2025 was honored on May 19 at a Commencement event in New Haven, accompanied by relatives, friends, and constituents of the YLS community.
-
Yale Celebrates Future Leaders at ROTC Ceremony

On Monday, Yale celebrated its graduating Air Force, Naval, and Army ROTC alumni during the customary joint commissioning event at Battell Chapel.