-
Whispers of Restless Souls
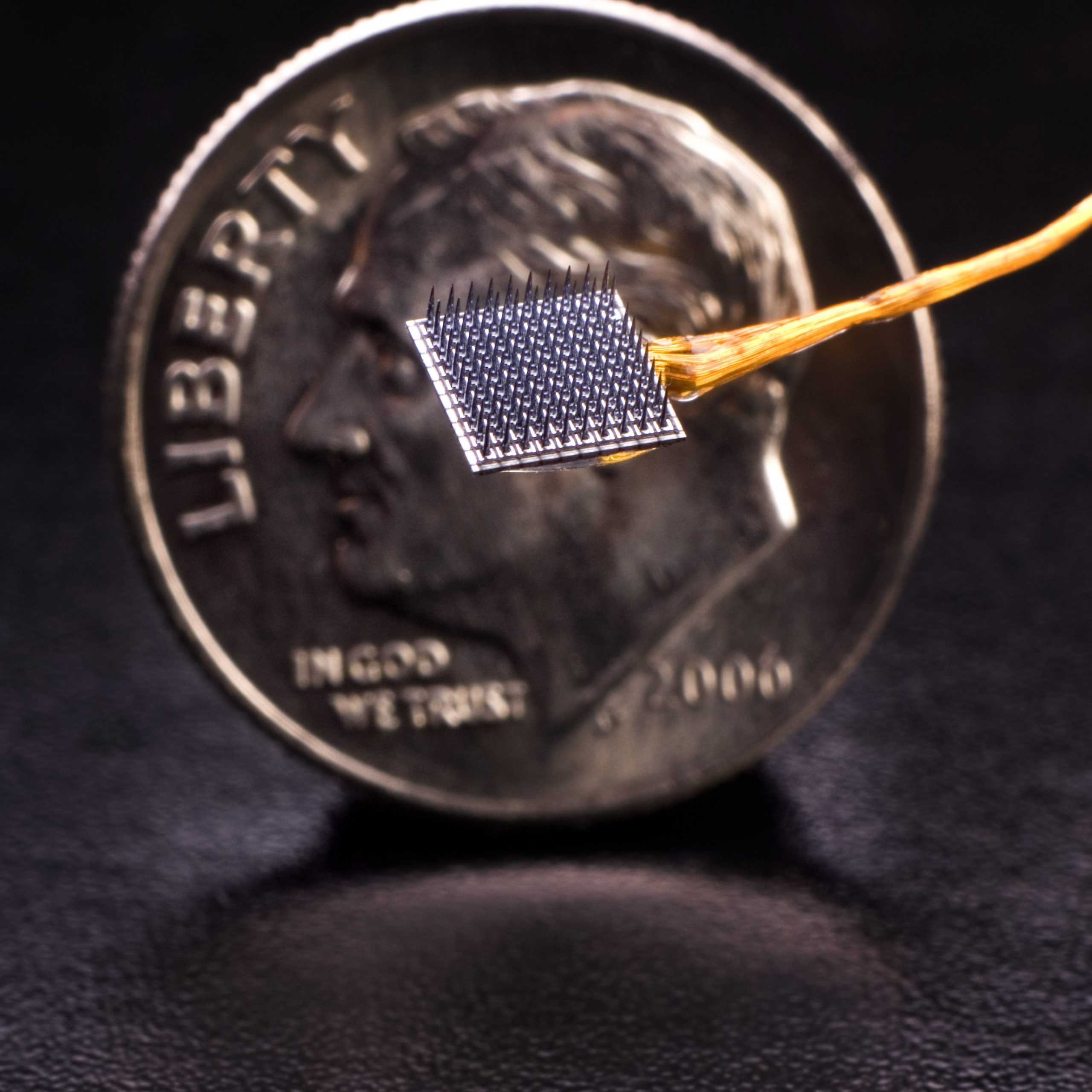
Sure! Here’s a revised version with synonyms and altered sentence structures while preserving the original HTML format: “`html Depiction of an electrode array similar to those inserted in the brains of study participants Image courtesy of Daniel Rubin Science & Tech Restless minds Researchers are making progress in deciphering internal dialogue Sy Boles Harvard Staff…
-
“UT Unveils Pioneering Center for Law and Democracy”

The University of Texas at Austin has initiated the Center for Law and Democracy, an endeavor focused on fostering research, instruction, and publication at the confluence of public law and political science. Located within the College of Liberal Arts’ Department of Government, the center possesses an interdisciplinary goal to unite scholarship from various fields. The…
-
Navigating Tariffs: The Need for Agile Supply Chains in Today’s Economy

Yale’s Sang Kim, a specialist in supply chains, describes how changes in international politics and commerce might disturb the intricate networks that deliver goods to your door.
-
Campus Kickoff: Eli Days Celebrates Students with Fun and Appreciation
Organized by the Yale Alumni Fund and the Yale Alumni Fund Student Representatives, the gathering honors alumni contributions and their impact on defining the Yale experience.
-
Exploring the Implications of Ending Affirmative Action

In his latest publication, Yale’s Justin Driver contends that the U.S. Supreme Court’s annulment of affirmative action in university admissions does not signify the conclusion of racial diversity in higher education, but rather the onset of a fresh chapter in the struggle for fairness.
-
Freeman Appointed as the Alan Boles, Class of 1929 History Professor

Joanne B. Freeman, who became a part of the Yale faculty in 1997, is among the foremost historians in the political dynamics and cultural landscape of the revolutionary and early national eras of American history.
-
Gilbert Appointed as the Esteemed Singer Professor of Molecular Biophysics and Biochemistry

Wendy V. Gilbert, who became a member of the Yale faculty in 2017, examines the regulatory components in mRNA that govern the cellular manifestation of the data embedded in genetic code.
-
Revolutionizing Gene Therapy: How AI-Driven CRISPR Is Accelerating Medical Breakthroughs

Stanford Medicine’s CRISPR-GPT utilizes artificial intelligence to aid researchers in the gene-modifying procedure, with the possibility of improving the creation of life-saving therapies.
-
Unpacking the Political Leanings of Small Business Entrepreneurs

A groundbreaking document discovers that small enterprise proprietors form a unique, Republican-aligned group, aiding in clarifying certain steady political patterns.
-
Revolutionizing Manufacturing: How Algorithms Enhance Robot Collaboration in Assembly Lines
Researchers at Stanford have created a groundbreaking algorithm that enhances the assembly manufacturing process by efficiently coordinating autonomous robots.
-
Navigating the Stars: The Astronaut’s Guide to Risk Assessment

“`html Image provided by Anil Menon Science & Technology How an astronaut assesses risk With launch date nearing, Anil Menon gears up for the ‘impossible’ Sy Boles Harvard Staff Writer September 17, 2025 5 min read A series delving into how risk influences our choices. When Anil Menon embarks on his journey into space aboard…
-
The Supreme Court’s Potential Reevaluation of a Pivotal Climate Decision

“`html Nation & World How the Supreme Court might have an opportunity to revisit a pivotal climate decision Alvin Powell Harvard Staff Writer September 17, 2025 7 min read Legal analysts assert that justices could nullify the ruling permitting the EPA to oversee greenhouse gas discharges on procedural bases amid changes in court composition The…
-
“Unmasking the Digital Threat: How AI-Powered Scripts Fuel Venom RAT Attacks in Brazilian Hotels”

“`html The malicious entity recognized as TA558 has been linked to a new wave of assaults introducing different remote access trojans (RATs) such as Venom RAT to infiltrate hotels in Brazil and Spanish-speaking regions. The Russian cybersecurity firm Kaspersky is monitoring the operations, noted in the summer of 2025, to a group it refers to…
-
The Coding Attorney: Kirk Sigmon’s Journey to Dartmouth Engineering

“`html Kirk Sigmon is not your average attorney. As a collaborator and intellectual property lawyer focused on AI legislation, he consistently strives to broaden his understanding in the swiftly advancing realm of technology. Unlike many peers in the sector, Kirk has adopted a practical approach to truly grasp the engineering behind the AI technologies he…
-
Transforming Perspectives: Chuck’s Evolution from Teacher to Online Student in the Pitt MDS Program

“`html For over twenty years, Charles “Chuck” Allias developed his profession in emergency medical services (EMS). Serving as an educator and program director, he guided the upcoming generation of paramedics and EMTs, crafting programs that aligned with national benchmarks, mentoring students through challenging examinations, and discovering novel methods to enhance their success rates. Data had…
-
FSU College of Law’s Class of 2028 Achieves Unprecedented Academic Brilliance

“`html By Raghad Hamad Florida State University College of Law has recently embraced its incoming Juris Doctor (J.D.) Class of 2028. This year’s group consists of 153 first-year law scholars who have achieved the highest academic standards in the history of the institution, boasting a median LSAT score of 166 and a median undergraduate GPA…
-
FSU Chemist Secures $2.1 Million NIH Grant to Explore Molecular Roots of Disease

“`html A scholar from Florida State University has obtained a multi-million-dollar funding opportunity to explore the impact enzymes — which affect almost every function in the human organism from digestion to the interaction among neural cells — have on human ailments. Wen Zhu, Assistant Professor of Chemistry and Biochemistry, has been awarded the Maximizing Investigators’…
-
Revolutionary U of A Technology to Assist Seniors Facing Vision Challenges

“`html University of A innovation strives to assist seniors dealing with vision challenges nprevenas Wed, 09/17/2025 – 09:26 University of A innovation strives to assist seniors dealing with vision challenges Tuesday Article Categories Health & Wellness Current Events Science & Technology By AZPM Type of News Article External News “`
-
Innovative Solar Tower from University of Arizona Takes Aim at Reducing Food Waste

“`html Researchers from the University of Arizona create solar tower to combat food waste nprevenas Wed, 09/17/2025 – 09:24 Researchers from the University of Arizona create solar tower to combat food waste Today Story Categories In the Headlines Science & Innovation By KGUN Type of News Article External Coverage “`
-
Calculating the Universe’s Total Mass: A Cosmic Challenge

“`html What methods are used to determine the overall mass of the universe? nprevenas Wed, 09/17/2025 – 09:23 What methods are used to determine the overall mass of the universe? Currently Article Categories In the Headlines Science & Engineering Cosmos By Astronomy Magazine Type of News Article Outside News “`
-
Sacred Sites: The Clash of Tribal Sovereignty and Modern Development

“`html Indigenous lawsuits regarding revered locations nprevenas Wed, 09/17/2025 – 09:21 Indigenous lawsuits regarding revered locations Monday Article Categories Commerce and Jurisprudence Current Affairs By Bloomberg Law Type of News Article Outside News “`
-
“University of Arizona Dedicates $257 Million to Strengthen Tribal Community Collaborations”

“`html University of Arizona allocates $257M towards tribal community collaborations nprevenas Wed, 09/17/2025 – 09:18 University of Arizona allocates $257M towards tribal community collaborations Today Article Categories In the Headlines Strategic Objectives University Updates By KOLD Type of News Article Outside News “`
-
“Transforming Healthcare: A Texas A&M Researcher’s 3D Printing Breakthroughs”

Dr. Mansoor Khan is utilizing 3D printing technology to produce accurate, tailored medication dosages, a significant advancement for pediatric healthcare.
-
Texas A&M Innovates Groundbreaking Cryopreservation Technique to Avoid Organ Cracking
The innovative method could open doors for effective, enduring organ transplants — bringing science fiction nearer to medical fact.
-
Melodies of Remembrance: A Tribute Concert Celebrating Clifton and Dolores Wharton

Michigan State University honored the contributions and memories of Dr. Clifton W. Wharton and Mrs. Dolores Wharton with a complimentary tribute concert at the Wharton Center, showcasing jazz, Broadway, dance, and orchestral acts.
-
Nurturing Futures: MSU’s Commitment to Student Parents from Cribs to Commencement

MSU commemorates Student Parent Awareness Month with a diaper collection, open house event, and narratives of graduate students managing family responsibilities alongside their education.
-
Diverse Impacts of Chronic Conditions on Mortality: A Study on Race and Ethnicity
A recent extensive investigation conducted by a team of researchers from Yale discovered that the persistent ailments that lead to death differ by race and ethnicity.
-
Innovative Insights from YSE Experts Set to Illuminate Progress During NYC Climate Week

From bridging political divides to the possibilities of AI enhancing solutions, faculty and research scholars at the Yale School of the Environment will provide perspectives on a diverse range of subjects.
-
Chimpanzees: Nature’s Hidden Boozers Enjoying Their Daily Fermented Treats

An examination of the alcoholic strength of fruits commonly consumed by African chimpanzees indicates that their nourishment could provide 14 grams of ethanol each day. Considering their physique, that’s almost the equivalent of two cocktails. The article In the wild, chimps likely ingest the equivalent of several alcoholic drinks every day was originally published on…
-
Moe Obeidat’s Journey to Earning a Master of Data Science at Pitt Online
“`html Moe Obeidat understands data. Residing in the Chicago region, he serves as a data analyst for a Fortune 500 firm, where tasks such as reporting, visualization, and SQL are integral to his daily activities. However, like numerous professionals in the domain, Moe was keen to advance: transitioning from analysis to elevated positions in data…
-
Keck Hospital of USC Recognized for Excellence in Patient Care for the Third Consecutive Year

The medical center is a recipient of Vizient’s Birnbaum Quality Leadership Performance accolade, which honors leading performers’ excellence in patient care.
-
Empowering Tomorrow’s Leaders: Tillerson’s Commitment to Civics, Engineering, and the Longhorn Band

AUSTIN, Texas — Rex Tillerson, the previous U.S. secretary of state, energy sector executive and Distinguished Alumnus of the University of Texas at Austin, has made significant contributions to UT’s School of Civic Leadership, the Cockrell School of Engineering, and the Longhorn Band. His most recent donations to the University, amounting to $16 million, will…
-
Americans Advocate for Choice in Mental Health Care as Federal Government Seeks Mandatory Treatment

“`html The demand for mental health services is increasing across the country, yet millions of individuals in the U.S. still lack access to necessary support. Recent statistics indicate that just approximately half of those with a mental health issue — and under one in four individuals dealing with a substance use disorder — receive treatment.…
-
Kickstarting the Fall Semester: Highlights and Moments

“`html First-year learners adjust as a fresh academic year commences. “`
-
Where Enthusiasm Embraces Conservation

Brian Meacham fuses his passion for cinema and heritage as Yale’s film curator, reviving forgotten reels and constructing narratives from filmic pieces.
-
The Intriguing Journey of a Vital Vitamin B Nutrient to Mitochondrial Riches

Researchers have discovered the reason that the vital nutrient CoA predominantly exists in mitochondria. This insight may aid us in comprehending several ailments.
-
Harnessing Expertise: Seasoned State Employees Drive Major Savings in Infrastructure Development
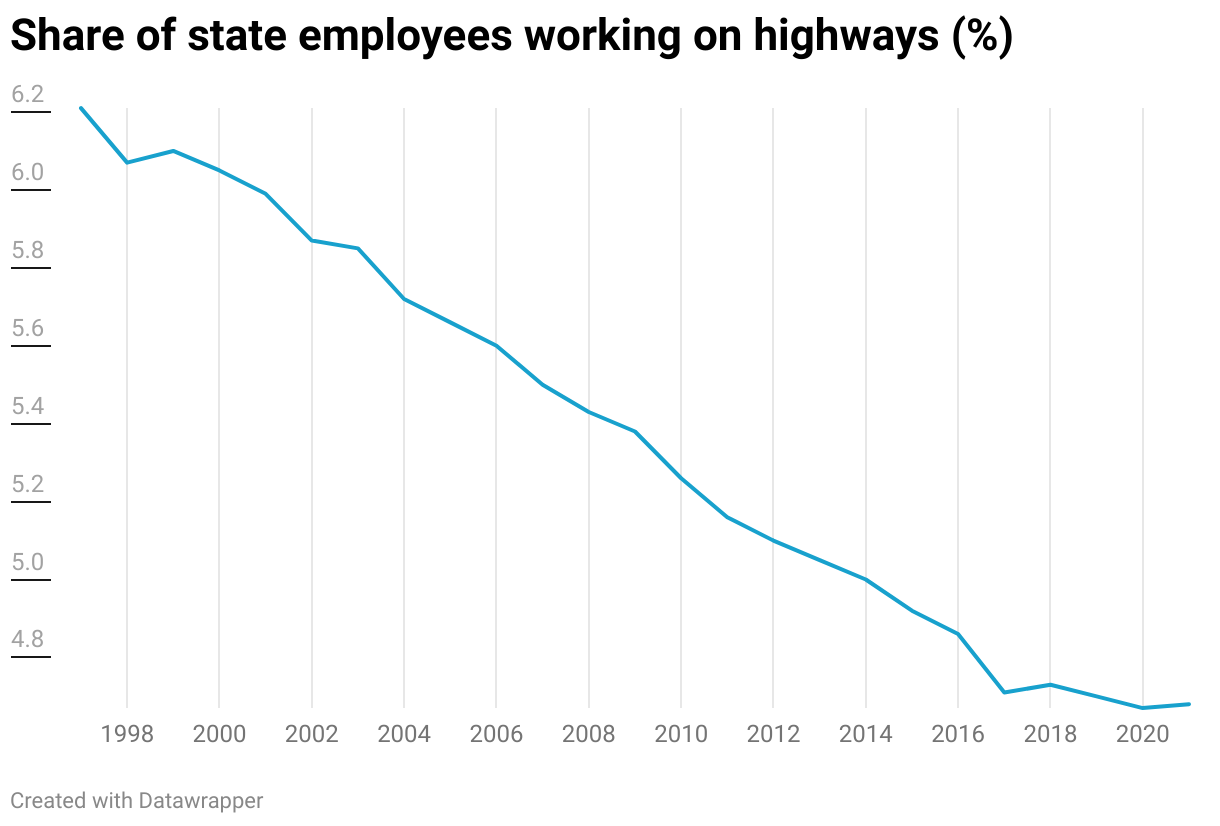
To construct swiftly and at a lower cost, governments ought to be prepared to invest significantly more to keep the top engineers, recent research co-authored by Yale’s Zachary Liscow discovers.
-
Revolutionary 3D Bioprinting Method Poised to Enhance Engineered Tissue Production
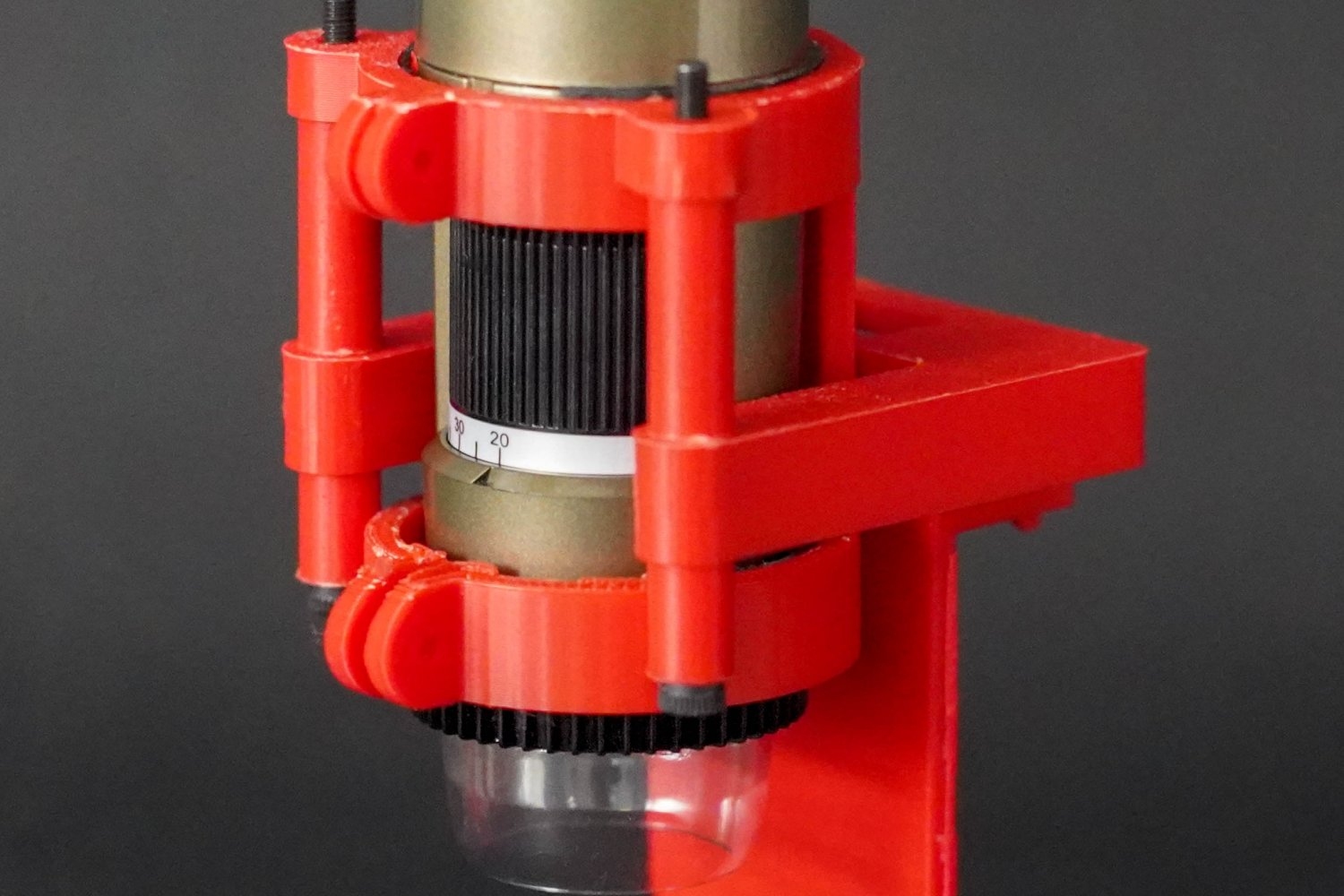
The realm of tissue engineering seeks to mimic the architecture and functionality of actual biological tissues. This manufactured tissue holds significant promise for applications in disease simulation, pharmaceutical exploration, and implantable grafts. 3D bioprinting, which employs living cells, biocompatible substances, and growth factors to construct three-dimensional tissue and organ frameworks, has surfaced as a pivotal…
-
Navigating the Arctic: David Whelihan’s Insights on Overcoming Operational Hurdles

“`html For many, the Arctic might seem like a conceptual location, challenging to envisage beyond snapshots of ice and polar bears. However, researcher David Whelihan from MIT Lincoln Laboratory’s Advanced Undersea Systems and Technology Group is well-acquainted with the Arctic. Through Operation Ice Camp, a biennial initiative sponsored by the U.S. Navy to evaluate operational…
-
Harnessing Fusion Energy: Pioneering a Sustainable Future

“`html George Tynan traversed an unconventional route to fusion. After earning his undergraduate degree in aerospace engineering, Tynan’s professional experience ignited his fascination with rocket propulsion technology. Since many propulsion techniques involve the manipulation of heated ionized substances, or plasmas, Tynan directed his focus toward plasma physics. It was during this period that he understood…
-
Revolutionizing Genome Editing: A New Precision Approach

“`html A genome-altering method referred to as prime editing shows promise for addressing numerous ailments by converting defective genes into operative ones. Nevertheless, this technique comes with a slight risk of introducing inaccuracies that could be detrimental. Researchers at MIT have recently discovered a method to significantly reduce the error rate of prime editing by…
-
Revolutionary Bioelectronic Fibers: Monitoring Hundreds of Biological Events at Once
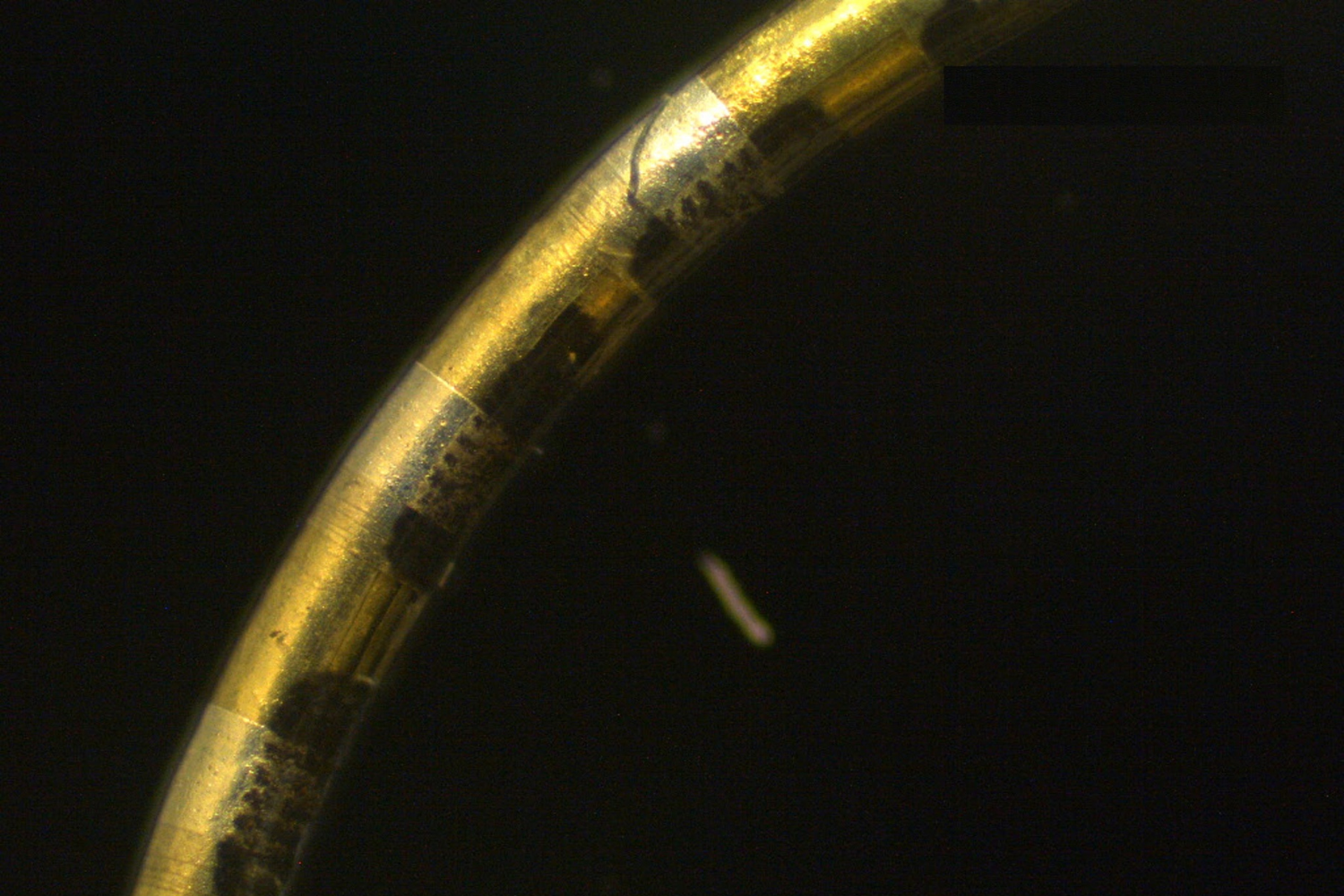
Created by researchers at Stanford, NeuroString is an ultra-fine multichannel biosensor and stimulator with encouraging potential uses in medication administration, nerve activation, intelligent textiles, and beyond.
-
“Unveiling Espionage: How Chinese TA415 Exploits VS Code Remote Tunnels to Target U.S. Economic Analysts”

“`html A China-aligned menace identified as TA415 has been connected to spear-phishing operations aimed at the U.S. government, research institutions, and educational entities leveraging U.S.-China economic-themed bait. “In this operation, the entity impersonated the present Chair of the Select Committee on Strategic Competition between the United States and the Chinese Communist Party (CCP), as well…
-
Celebrating Excellence: Rachel Ward Boatwright Named Employee of the Year at Florida State University

“`html Rachel Ward Boatwright has been honored as the 2025 Florida State University Max Carraway Employee of the Year Award recipient. President Richard McCullough selected Boatwright, who acts as a senior academic advisor in the College of Music, for this prestigious award, which has lauded exceptional employees since 2008 for their significant contributions and exceptional…
-
Revolutionary 3D-Printed Medicine for Kids Earns Prestigious Fast Company 2025 Innovation Award

A significant advancement in the management of a lethal illness has garnered a national accolade for Texas A&M University.
-
“MSU Public Health Celebrates a $220 Million Funding Achievement”

How community-engaged research enhances public health results in Flint and elsewhere
-
Unyielding Cyber Resilience: Mastering Quantum and AI Defenses

“`html Quantum computation and artificial intelligence collaborating will introduce remarkable prospects. United, these technologies will enable us to advance innovation more extensively and swiftly than at any previous time. However, consider the alternative: awakening to reports that cybercriminals have employed a quantum computer to breach your organization’s encryption during the night, compromising your most confidential…
-
Supporting Your Child Through Social Anxiety: Effective Strategies for Parents

“`html It’s typical for teenagers to experience unease or timidity around peers. However, the manner in which their guardians interact with them could potentially alleviate or exacerbate their social anxiety, as revealed by a recent research from the University of Georgia. Cullin Howard The investigators discovered that both mothers and fathers significantly affect their offspring’s…
-
UGA Students Make a Big Impact with 500 Volunteer Hours in Athens Community

“`html On September 13, the University of Georgia commemorated Dawg Day of Service, the most significant day of student community involvement in Athens. 488 students participated with 23 community partner organizations and campus locations, which included local gardens, food and clothing pantries, thrift shops, and animal shelters. Serve UGA, a student-led organization guided by the…
-
Theatre Department Unveils Exciting Lineup for 2025-26 Season

The article School of Theatre Unveils 2025-26 Season was published initially on Florida State University News.
-
Revamping AI Data Security: Your Essential Buyer’s Handbook

“`html Generative AI has evolved from a fascination to a fundamental element of organizational efficiency in merely a few brief years. From assistants integrated within office software to specialized large language model (LLM) systems, workers increasingly depend on these resources to program, evaluate, compose, and make choices. However, for CISOs and security designers, the rapid…
-
Mastering the Art of Electronic Safe Security

“`html Weaknesses in digital safes featuring Securam Prologic locks: Although both methods illustrate significant security flaws, Omo indicates that the one taking advantage of a function designed for legitimate access by locksmiths is the more prevalent and hazardous. “This breach is such that, if you possessed a safe with this type of lock, I could…
-
Scattered Spider Reemerges to Target Financial Sector Despite Alleged Retirement

“`html Cybersecurity analysts have linked a new wave of cyber assaults aimed at financial services to the infamous cybercriminal collective referred to as Scattered Spider, raising skepticism about their assertions of going “dark.” Threat intelligence agency ReliaQuest noted that it has detected signs indicating that the threat entity has redirected their attention to the financial…
-
Unraveling CTRL-Z DLL Hooking Techniques: A Comprehensive Guide

“`html When you’re analyzing a malware specimen, you likely execute it in a debugger and establish several breakpoints. The concept is to seize control of the program prior to it carrying out “noteworthy” actions. Typically, breakpoints are placed on memory allocation API calls (such as VirtualAlloc()) or process functions (like CreateProcess(), CreateRemoteThread(), …). “`
-
Transforming Strings into Arrays in PHP: A Guide to Various Techniques

“`html PHP is a freely available programming language that is employed for server-side programming and scripting. It is extensively recognized and utilized for server-side programming. It operates effectively with databases such as MySQL, Oracle, Microsoft SQL Server, PostgreSQL, and numerous other popular databases. Additionally, it accommodates file management and data encryption. It accommodates a diverse…
-
Mastering Vector Initialization in C++: 6 Creative Approaches

“`html Vectors are STL containers utilized for the dynamic storage of information. They are viewed as a dynamic version of arrays, equipped with the capability to adjust their size automatically based on the addition and removal of elements. Similar to its static equivalent, it can hold only a single entity at a single index. Both…
-
Unlocking the Power of Partial Classes in C#

“`html Each source document includes the definition and declaration of functions that are united when an application undergoes compilation. We can divide classes, structures, interfaces, and other functions utilizing different source files. Partial classes assist in separating the functions into two or more source (.cs) files. All the partial classes will merge when the entire…
-
Mastering the Implode Function in PHP: A Beginner’s Guide

“`html PHP denotes Hypertext Preprocessor. The PHP coding language is founded on the Object-Oriented Programming (OOP) paradigm. It is a freely available language utilized for scripting and general programming tasks, created by Rasmus Lerdorf, a Danish-Canadian programmer, in 1994. PHP ranks among the most favored programming languages and serves as a…Read More. “`
-
Unleashing the Power of Node.js: Your Ultimate Guide to Mastering JavaScript on the Server Side

Node Javascript serves as a JavaScript execution environment that is open-source and multi-platform. It is a favored instrument for nearly any endeavor. Operated by the V8 JavaScript engine, which powers Google Chrome, Node Javascript functions outside of the browser. Consequently, it is remarkably swift. By avoiding the creation of a new thread for each request…Read…
-
Join USC in Honoring Constitution Day 2025

“`html The U.S. Constitution was ratified on Sept. 17, 1787. (Photo/Mr.TinDC via Flickr) Share University Honor Constitution Day 2025 with USC Congress designates Sept. 17 to acknowledge the significance and heritage of the foundational document. September 17, 2025 By USC Team We the People of the United States, in Order to create a more perfect…
-
Restoring Democracy: A USC Initiative to Explore Solutions for a Strained System

USC Price’s Mindy Romero heads By the People, For the People, a countrywide nonpartisan effort aimed at restoring confidence in U.S. democracy.
-
BreachForums Creator Receives 3-Year Sentence for Cybercrime and CSAM Charges

“`html The U.S. Department of Justice (DoJ) on Tuesday reimposed a sentence on the previous administrator of BreachForums, confining him to three years of incarceration due to his involvement in operating the cybercrime forum and possessing child sexual exploitation materials (CSEM). Conor Brian Fitzpatrick (also known as Pompompurin), aged 22, from Peekskill, New York, admitted…
-
The Inspiring Journey of Betha Whitlow

“`html To finance her education at Northwestern University, Betha Whitlow, currently the curator of visual resources and a lecturer in art history within Arts & Sciences, held various jobs including bartender, babysitter, tutor, and front-desk assistant. Now serving as the director of the Digital Art History Lab (DAHL) at Washington University in St. Louis, Whitlow…
-
Microsoft and Cloudflare Unite to Take Down the RaccoonO365 Phishing Network, Targeting 338 Domains
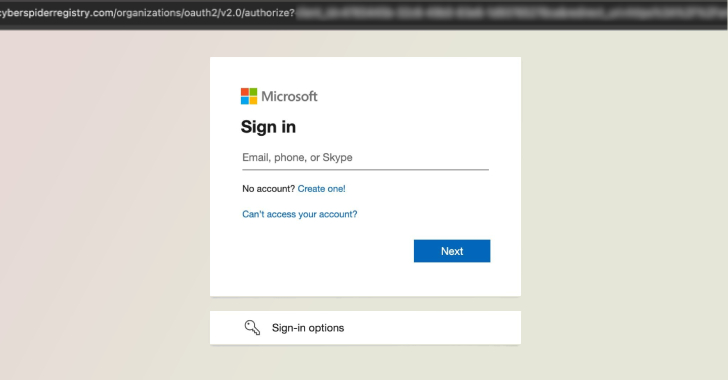
“`html Microsoft’s Digital Crimes Unit announced it collaborated with Cloudflare to orchestrate the confiscation of 338 domains utilized by RaccoonO365, a profit-driven threat organization that was responsible for a phishing-as-a-service (Phaas) toolkit employed to acquire over 5,000 Microsoft 365 credentials from 94 nations since July 2024. “Leveraging a judicial order issued by the Southern District…
-
Unforgettable Moments of Move-In Day
The enthusiasm was tangible on Move-In Day 2025. Observe moments from the significant day.
-
Vibrant Memories: A Glimpse into Stanford’s Move-In Day

The latest freshmen, transfer, graduate, and professional students at Stanford have come. Take a look at some unforgettable highlights from their inaugural day on campus.
-
Harnessing AI: Transforming Weather Forecasting for Indian Farmers

Collaboratively created by UC Berkeley’s William Boos, an AI-driven meteorological model provided a prompt forecast of a halted monsoon this season, assisting farmers in determining the optimal time for planting their crops. The article AI transforms weather forecasting to aid farmers in India was originally published on Berkeley News.
-
Daylight Saving Time: A Surprising Link to Stroke and Obesity Risks

Based on a recent evaluation by Stanford Medicine, the majority of Americans would experience better health if time adjustments were not made biannually.
-
The Urgent Need for Phishing-Resistant Authentication Today
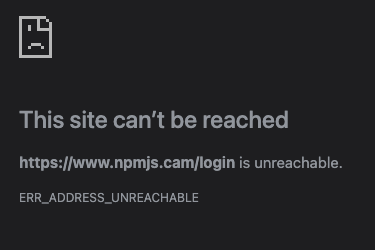
“`html The recent (and currently continuing) impersonation of NPM developer accounts demonstrated once more that even technically savvy and informed individuals are susceptible to phishing temptations. Anyone can be deceived by phishing if a precisely targeted email is employed. “`
-
FSU Celebrates Unprecedented Graduation and Retention Success

The article FSU Achieves Unprecedented Graduation and Retention Rates was originally published on Florida State University News.
-
FSU and Tallahassee Memorial HealthCare Team Up to Create a Cutting-Edge Academic Health Center

“`html Florida State University and Tallahassee Memorial HealthCare (TMH) have endorsed the framework for a momentous collaboration agreement aimed at establishing an academic health center in Tallahassee, a progress that will revolutionize health care in North Florida and enhance FSU’s objectives in education and inquiry. In a collective announcement, FSU President Richard McCullough and TMH…
-
Groundbreaking $4.87 Million Grant Fuels Creation of Innovative Sepsis Diagnostic Tool
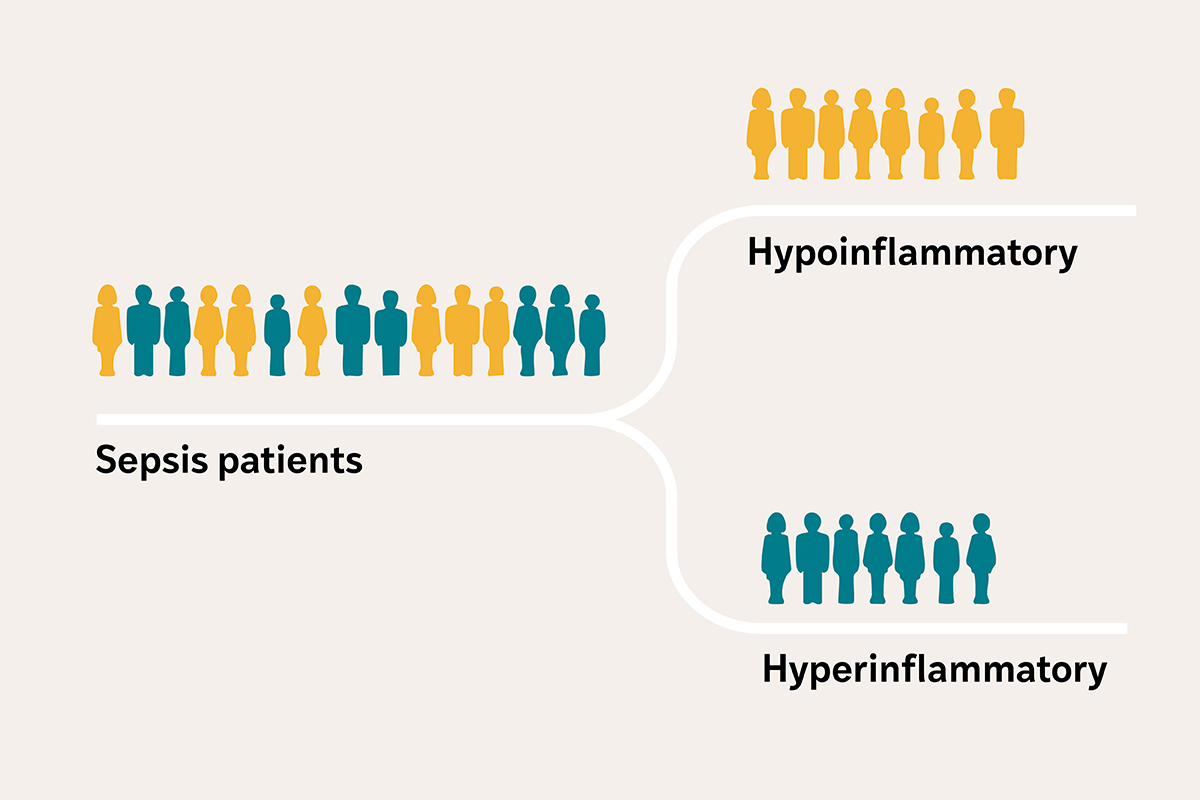
“`html Severely ill individuals afflicted with sepsis — a disorder where the body’s reaction to an infection escalates uncontrollably and may result in organ harm — frequently enter the intensive care unit (ICU) exhibiting analogous symptoms, including fever, reduced blood pressure, and kidney dysfunction, among others. However, investigators at Washington University School of Medicine in…
-
A Captivating Glimpse of Robert Redford’s Charismatic Smile

The cinematic icon and ecological advocate was celebrated by the Dartmouth Film Society in 1987.
-
“Two Ph.D. Scholars Honored with Prestigious HHMI Gilliam Fellowship”
Jordan Polster and Denethi Wijegunawardana from the Biological and Biomedical Sciences program have been recently chosen as Howard Hughes Medical Institute Gilliam Fellows. This fellowship aims to propel exceptional students into influential scientific research careers while promoting inclusive training settings.
-
Unveiling the Ancient Roots of Corporations: A History Beyond Our Imagination

The inception of the joint-stock corporation is typically linked to the establishment of the English East India Company and the Dutch East India Company circa 1600. Recent studies co-written by Prof. William Goetzmann suggest that this narrative might be inaccurate by centuries.
-
In Memoriam: Celebrating the Legacy of Jim Van Horne at Stanford GSB

The finance educator departs with a heritage of wisdom, guidance, and motivation.
-
Reimagining Careers: Can Retraining Save Jobs from AI’s Reach?

“`html Labor & Economy AI has taken your employment — can retraining be beneficial? Karen Ni. Niles Singer/Harvard Staff Photographer Anna Gibbs Harvard Correspondent September 16, 2025 7 min read Research indicates advantages for displaced workers even in jobs at risk of automation A multitude of individuals fret that AI will assume their roles. However,…
-
Critical GraphQL Vulnerabilities in Chaos Mesh Allow for Remote Code Execution and Complete Kubernetes Cluster Compromise

“`html Cybersecurity analysts have revealed several significant security flaws in Chaos Mesh that, if effectively leveraged, might result in cluster domination within Kubernetes settings. “Intruders require merely limited in-cluster network entry to manipulate these weaknesses, carry out the system’s fault injections (such as terminating pods or interfering with network communications), and execute “`
-
U-M Marching Band Takes on the Magic of ‘Wicked’
“`html The University of Michigan Marching Band, in partnership with the U-M School of Music, Theatre & Dance Department of Musical Theatre and Percussion Studio, showcased selections from the Broadway musical and film series “Wicked” during the halftime performance of the U-M versus Central Michigan University football game. In anticipation of the forthcoming release of…
-
WashU Selected as a Pivotal Player in Upcoming Artemis Lunar Missions
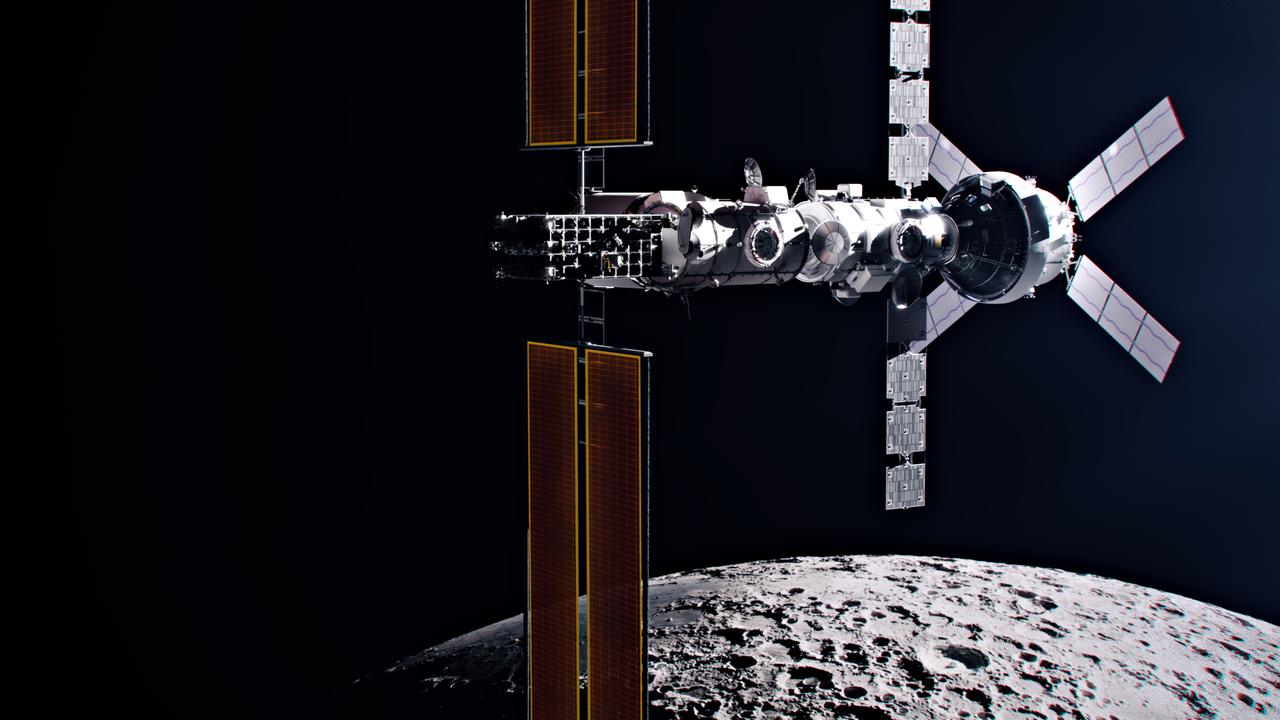
NASA’s forthcoming Artemis endeavors to the moon, where astronauts will return to the lunar terrain, will signify a substantial advancement in space exploration — with WashU playing an essential part in every mission. In July, the space organization officially appointed the Geosciences Node, a branch of NASA’s Planetary Data System (PDS) that has been established…
-
Matriculation Moments: A Celebration of New Beginnings

Members of the Cohort of 2029 celebrate their formal commencement at Dartmouth.
-
Revolutionary AI Method Decodes Quantum Vibrations in Materials
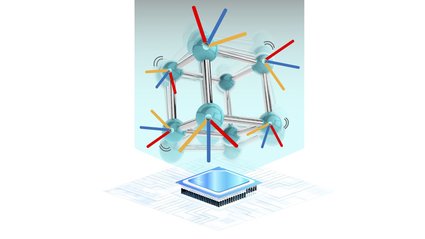
“`html Caltech researchers have devised an artificial intelligence (AI)–driven approach that significantly accelerates computations of the quantum interactions occurring within materials. In recent work, the team concentrates on interactions among atomic vibrations, known as phonons—interactions that influence a broad spectrum of material characteristics, encompassing heat transfer, thermal expansion, and phase changes. This innovative machine learning…
-
Defining the Essence of Asian American Literature

Long Le-Khac, an associate professor of ethnic studies at UC Berkeley, has recently released a 1,900-entry dataset that he anticipates will be utilized to explore which works are labeled as “Asian American” in academic discussions — and whom that excludes. The article What constitutes ‘Asian American literature,’ anyway? first appeared on Berkeley News.
-
The Surprising Trust in Fake Local News Over Authentic Sources
A recent investigation indicates that numerous individuals frequently favor algorithm-generated websites over those with reporters employed by an established news organization.
-
Arthur Sze: Yale’s Bollingen Prize Winner and New U.S. Poet Laureate

The recently proclaimed U.S. Poet Laureate Arthur Sze received Yale’s Bollingen Prize for American Poetry in February. His manuscripts are housed at the Beinecke Library.
-
Bridging Opportunities: Introducing Local Students to the World of Crew

Middle school students immerse themselves in rowing at Yale’s revitalized summer camp — from ergometer competitions to on-water excursions at Gilder Boathouse.