-
Master the PMP® Exam in Just 60 Days: Join Our Simplilearn Webinar on July 16, 2025, at 3:30 PM!
“`html Getting ready for the PMP® examination requires more than just familiarizing yourself with the study resources; it also entails grasping the correct approach. And believe me, that truly alters the outcome. Annually, individuals dedicate weeks, or even months, preparing for the PMP®, only to fall into exhaustion, disarray, or the unfortunate necessity of a…
-
Mastering Data Scrubbing: An Essential Guide for Beginners

It should not be surprising that data isn’t flawless. Similar to everything else in existence, digital information is prone to human mistakes, discrepancies, redundancies, typographical errors, and incomplete details. Given that a significant portion of our personal and professional lives now exists in databases, it’s increasingly crucial to ensure that data is as close to…
-
Transform Your Business Workflow in Just 30 Minutes: Join Our Live Demo!
Experiencing the urge to “accomplish more in a shorter duration”? It’s a fact that monotonous manual duties can sap your innovation and hinder your efficiency, regardless of your industry. However, what if you could reclaim hours in your working hours by automating those tedious tasks? In this live webinar, you’ll learn how Generative AI tools…
-
A Decade of Advances in Artificial Intelligence and Machine Learning

The speed of technological advancements has surged significantly over the past century. Additionally, in the last ten years, progress in the realm of information technology has escalated immensely, particularly within the spheres of Artificial Intelligence (AI) and machine learning (ML). These transformations are increasingly influencing our lives, impacting everything from…Read More.
-
The Dilemma of “We the People”: Unpacking American Democracy’s Challenges

A study conducted by the Democracy Policy Lab at UC Berkeley reveals that Americans are perplexed regarding the definition and execution of democracy and exhibit significant distrust towards public institutions — as well as one another. The authors suggest that robust “democracy policy” could assist in reestablishing national connections. The article ‘We the people’ is…
-
Global Explorations: Berkeley Scholars Dive into the World of International Art

In conjunction with the Department of History of Art’s Judith Stronach Travel Seminar, UC Berkeley students journeyed to Senegal last November for an enriching, nine-day excursion centered around a significant exhibition of contemporary African artistry. The post Innovative Berkeley scholars explore the world to engage with international art was originally featured on Berkeley News.
-
The Curious Case of the Squid “Egg Mop”: What to Do When You Encounter One

Guidelines on actions to take if you encounter a cluster of squid eggs. Similarly, this squid article provides an opportunity to discuss security topics in the news that I haven’t addressed. Blog managing rules.
-
Emergency Response Drill at WashU on July 9

“`html The Washington University Police Department (WashU PD) is scheduled to carry out its semiannual active shooter training drill on July 9 in the South 40 region of the Danforth Campus. This training exercise is not prompted by any specific threat; instead, it is a preventive approach to enhance WashU PD’s readiness and response abilities.…
-
Brown School Faculty Secures $1.4 Million Grant to Explore Economic Mobility and Wealth Disparities

“`html Two educators from Brown School have been granted a total of $1.4 million in funding from the Ewing Marion Kauffman Foundation to facilitate research aimed at enhancing economic mobility and mitigating wealth inequalities. Cameron (left) and Jabbari Heather Cameron, serving as the Michael B. Kaufman Professor of Practice in Social Entrepreneurship, has secured $920,000…
-
Fred Smith ’66: Pioneering FedEx Founder and Advocate for Yale’s Carbon Capture Innovation

Smith, who passed away on June 21, directed FedEx, an idea he envisioned as a Yale undergraduate, during its groundbreaking support of Yale’s Center for Carbon Capture. This center focuses on creating natural methods for diminishing atmospheric greenhouse gases.
-
Tropical Forests: Nearing a Critical Tipping Point?

Yale authorities provide insights on the deterioration of tropical forests, biodiversity, and avenues for rehabilitation.
-
The Intricate Craft of Eggshells: Unveiling a Hidden Artistry

80 million metric tons of eggshell refuse, the age-old craft of ceramics, and innovative technology unite to address an ecological issue — transforming eggshell refuse into eco-friendly ceramic glaze.
-
New Blood Test Enhances Early Detection of Heart Transplant Rejection
A recent investigation indicates that cellular messengers referred to as exosomes from donated hearts and T cells may serve as indicators for the prompt identification of organ rejection.
-
Cultural Heritage Leaders Unite: A Global Summit for Collaboration and Innovation

A meeting in Côte d’Ivoire earlier this month signified the conclusion of the first Yale Directors Forum, a fellowship initiative for senior leaders of museums, libraries, archives, and heritage organizations across the African continent.
-
Cultivating Joy: Finding Light Amidst Uncertainty

In this installment of the Greater Good Science Center podcast, Poet Tomás Morín explores a writing technique aimed at fostering a greater sense of hope and drive to pursue his aspirations. The article Science of Happiness: How to feel hope in a time of uncertainty was initially published on Berkeley News.
-
Echoes of Nature: Exploring the Cultural Landscapes of the Animal Kingdom

“`html From vibrations to ceremonies: Researchers chart the societies of the animal realm nprevenas Fri, 06/27/2025 – 11:29 From vibrations to ceremonies: Researchers chart the societies of the animal realm Thursday Article Categories Current Affairs Science & Innovation By Earth.com Type of News Article Outside News “`
-
Meet Ylana Lopez: A Shining Star of MIT

“`html Ylana Lopez manages programs and events at the Martin Trust Center for MIT Entrepreneurship. The Trust Center provides over 60 courses in entrepreneurship and innovation throughout the campus, a specific entrepreneurship and innovation pathway for students pursuing their MBA, online learning options for self-studiers at MIT and globally, and initiatives for individuals both within…
-
From Waste to Cosmos: The Transformation of Trash into a Universe

“`html Arts & Culture When refuse transforms into a cosmos Bottle caps discovered on the Australian shore. © TRES [ilana boltvinik + rodrigo viñas], image illustration by Liz Zonarich/Harvard staff Sy Boles Harvard Staff Writer June 27, 2025 5 min read Art collective unveils ‘intraterrestrial’ realms at Harvard Peabody Museum The bottle caps that washed…
-
Beat the Heat: Expert Tips for Safe Food Handling in Hot Weather

“`html With the Fourth of July on the horizon, there are critical summer food safety precautions that everyone should consider while gearing up for barbecuing and cooking. Every year, roughly 1 in 6 Americans fall ill, with 128,000 requiring hospitalization, and 3,000 succumbing to foodborne illnesses, as stated by the Department of Homeland Security. Illnesses…
-
USC to Host the Upcoming National Academy of Inventors Annual Gathering in Los Angeles

“`html The university alongside the National Academy of Inventors will commemorate visiting scholars with an event akin to the Hollywood Walk of Fame, complete with Oscar-sized Tommy Trojan statuettes. (Photo/Courtesy of the USC Stevens Center for Innovation) Share Science/Technology USC to host next year’s National Academy of Inventors annual convention in L.A. The esteemed academy…
-
Insights from U-M Experts on Supreme Court’s Decision Regarding Preventive Health Care Coverage

“`html Legal, medical, and public health scholars assess the ramifications of the Kennedy v. Braidwood verdict Today’s Supreme Court decision in the case of Kennedy v. Braidwood Management maintains the Affordable Care Act clause that enables specific preventive care to be accessible to patients without any expense, provided they satisfy requirements outlined in the guidelines…
-
Honoring Bill Moyers: A Beacon of Wisdom and Legacy

“I possess that newly awakened feeling of truly thriving here,” the reporter remarked about his university. The article Remembering Bill Moyers, a UT Icon and National Asset was initially published on UT Austin News – The University of Texas at Austin.
-
Chairperson Announced for Mechanical Engineering and Materials Science Department

“`html Friend James Friend, affiliated with the University of California, San Diego (UCSD), has been appointed as the head of the Department of Mechanical Engineering & Materials Science in the McKelvey School of Engineering at Washington University in St. Louis. His tenure will commence in 2026. Friend oversees the medically advanced devices laboratory within the…
-
Elevating Robotics: How Generative AI is Revolutionizing Jumping and Landing Mechanics
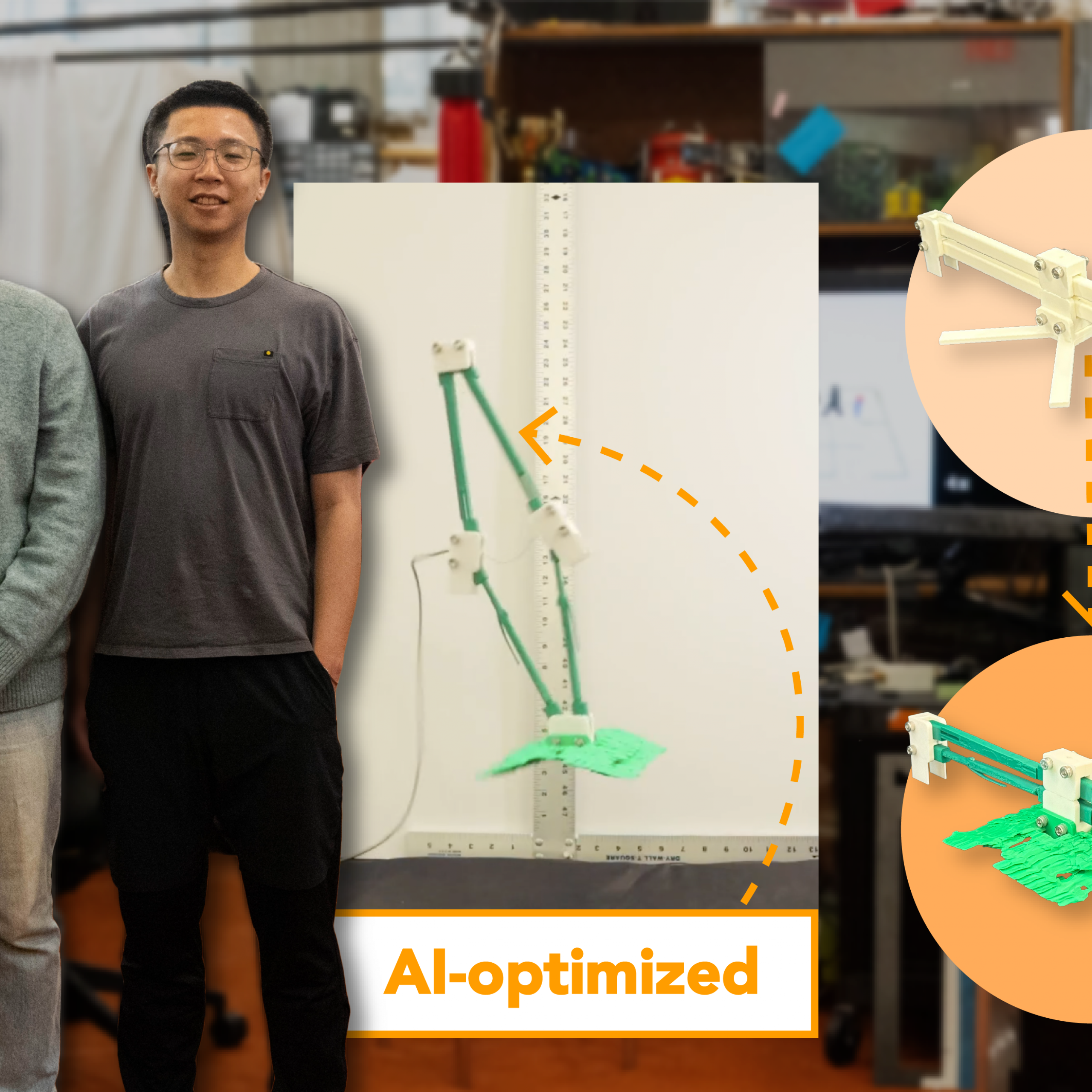
“`html Diffusion models, such as OpenAI’s DALL-E, are proving to be increasingly beneficial in assisting with the ideation of novel designs. Individuals can instruct these systems to produce an image, develop a video, or enhance a blueprint, returning with concepts they had not previously contemplated. However, were you aware that generative artificial intelligence (GenAI) models…
-
MIT and Mass General Brigham Unite to Propel Health Innovation Through New Seed Program

“`html Utilizing the capabilities of two premier research establishments, MIT and Mass General Brigham (MGB) recently commemorated the initiation of the MIT-MGB Seed Program. The innovative effort, which receives backing from Analog Devices Inc. (ADI), will finance collaborative research endeavors led by experts from MIT and Mass General Brigham. These joint initiatives aim to progress…
-
Transformative Housing: A Powerful Solution for Homelessness and Opioid Challenges

A recent research indicates that offering housing without the prerequisite of previous drug rehabilitation leads to significant improvements in public health and financial savings.
-
“China-Linked Cyber Espionage Campaign Compromises Over 1,000 SOHO Devices in LapDogs Operation”
Threat seekers have identified a system of over 1,000 infiltrated small office and home office (SOHO) apparatuses that have been exploited to support an extended cyber espionage infrastructure initiative linked to China-affiliated hacking factions. The Operational Relay Box (ORB) network has been designated as LapDogs by SecurityScorecard’s STRIKE team. “The LapDogs network exhibits a significant…
-
Pioneering Sickle Cell Gene Therapy Administered to First Patient in the Region

WashU Medicine and St. Louis Children’s Hospital are the first in the area — and among merely a handful of academic institutions in the U.S. — to start providing a newly sanctioned gene therapy to remedy sickle cell disease. Martin Mwita Jr. (right) journeyed with his mother from their residence in Nebraska to St. Louis…
-
Revolutionary “Smart Capsule” Ignites Innovation in Gastrointestinal Health Research

Researchers are increasingly discovering that the gastrointestinal (GI) system is essential for our overall well-being. Although its primary roles revolve around digestion, the GI system also plays a part in the creation of hormones, immune cells, and even neurotransmitters that can influence mood and cognitive function. Consequently, the GI tract harbors numerous biomarkers that can…
-
Consumer Confidence Sees First Upturn of the Year, Yet Caution Reigns

“`html The sentiment of consumers rose for the initial time in six months, increasing by 16% from the prior month but still hovering about 18% below the levels seen in December 2024, when consumer sentiment had demonstrated a post-election boost. These patterns were clearly evident across various demographics including age, income, wealth, political affiliation, and…
-
Dedicated Research Fellows Driven by Passion to Empower Tribal Communities

Harley Kell ’24 and Henry Eberhart ’24 discuss their encounters.
-
The Tobacco Industry’s Role in the Surge of Ultra-Processed Foods

In 1963, an American tobacco firm acquired Hawaiian Punch. This signaled the start of the tobacco sector’s foray into the food industry and resulted in a surge of overly enticing, chemically formulated edibles — along with a significant increase in obesity rates. The post Berkeley Talks: How the tobacco sector influenced the surge of ultra-processed…
-
Mustang Panda’s Targeted Tibet Assault: Exploring PUBLOAD and Pubshell Malware

A China-associated threat entity identified as Mustang Panda has been linked to a fresh cyber espionage initiative targeting the Tibetan community. The spear-phishing assaults utilized subjects pertaining to Tibet, including the 9th World Parliamentarians’ Convention on Tibet (WPCT), China’s educational strategy in the Tibet Autonomous Region (TAR), as well as a recently released book by…
-
A Compelling Case for Agentic AI in Security Operations Center Analysis

“`html Security operations centers (SOCs) face mounting pressure from multiple fronts: threats are becoming increasingly sophisticated and frequent, while security funding is not maintaining its trajectory. Modern security executives are anticipated to minimize risk and achieve outcomes without depending on expanded teams or heightened expenditures. Concurrently, SOC inefficiencies are depleting resources. Research indicates that nearly…
-
Silver Fox: The Deceptive Tactics of a Chinese Group Spreading Sainbox RAT and Covert Rootkits

A novel initiative has been detected utilizing counterfeit websites promoting well-known software like WPS Office, Sogou, and DeepSeek to distribute the Sainbox RAT and the publicly available Hidden rootkit. This activity has been linked with moderate assurance to a Chinese hacking collective known as Silver Fox (also referred to as Void Arachne), pointing to resemblances…
-
Integrity Unleashed: Embracing a New Era

“`html We must discuss the importance of data integrity. Specifically, the term signifies ensuring that data is not altered, whether during transmission or while stored. Altering account balances in banking databases, erasing entries from criminal records, and deleting mentions of allergies from medical documents are all attacks on integrity. More generally, integrity pertains to verifying…
-
Surge in Scanning Elevates Threats to MOVEit Transfer, Exploiting CVE Vulnerabilities

Threat analysis company GreyNoise has raised alarms about a “significant increase” in scanning activities aimed at Progress MOVEit Transfer systems beginning May 27, 2025—indicating that cybercriminals could be gearing up for another widespread exploitation effort or searching for vulnerable systems that have not been updated. MOVEit Transfer is a widely used managed file transfer application…
-
OneClik Malware: A New Threat to the Energy Sector Leveraging Microsoft ClickOnce and Golang Backdoors

Cybersecurity analysts have outlined a fresh initiative named OneClik that utilizes Microsoft’s ClickOnce software distribution technology alongside custom Golang backdoors to infiltrate entities in the energy, oil, and gas industries. “The initiative displays traits consistent with threat actors linked to China, although attribution is approached with caution,” stated Trellix researcher Nico Paulo.
-
Business Analyst Role Overview: Key Responsibilities and Skills

A business analyst employs data analysis to assess operations, pinpoint needs, and deliver reports and recommendations based on data to executives and stakeholders. This role is vital to connect IT with the business sector. A comprehensive grasp of the “business analyst job description” is vital for anyone aspiring to enter this fascinating…Read More.
-
Revitalizing U.S. Industry: Nth Cycle’s Groundbreaking Venture in Critical Metals Refining
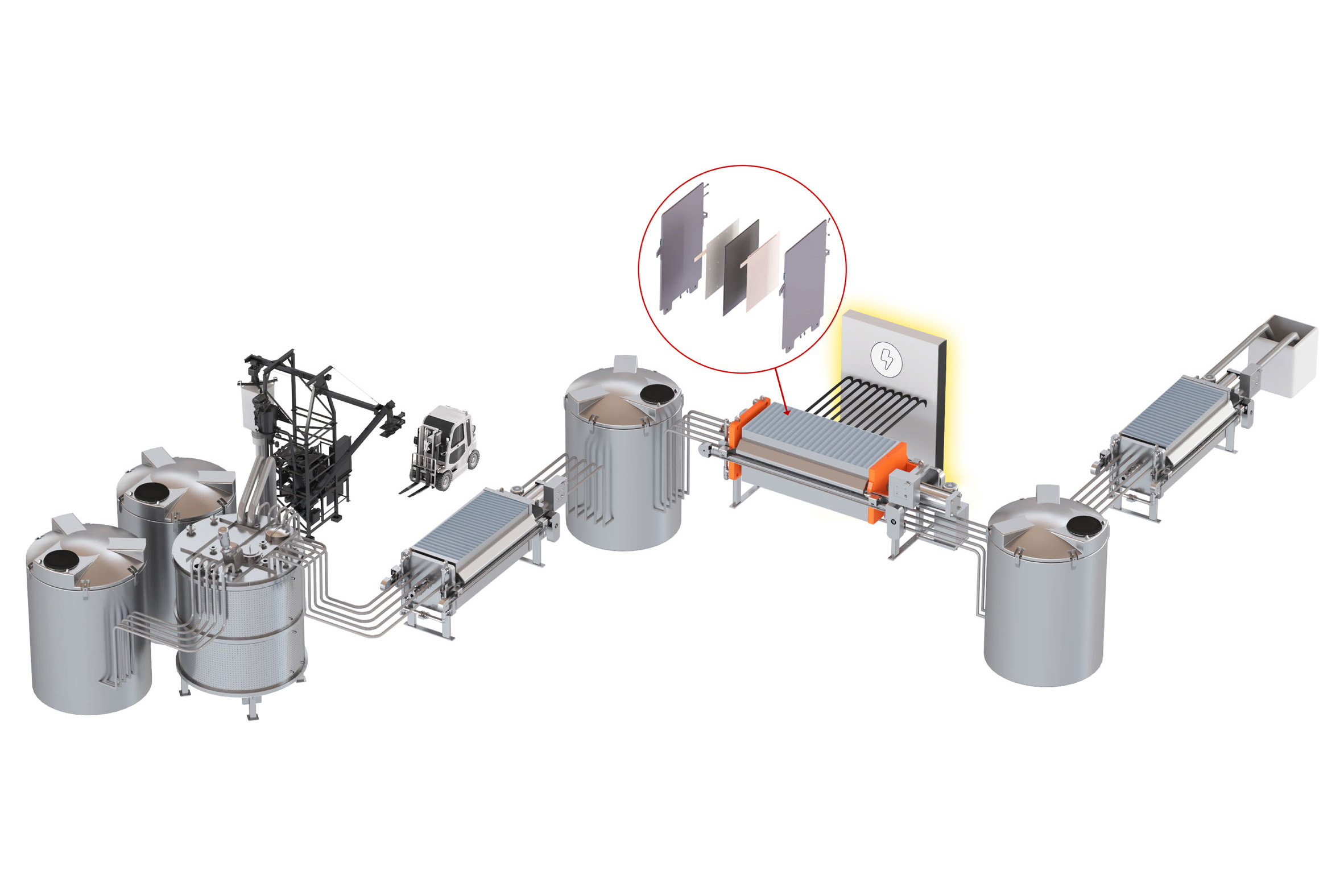
“`html Similar to Middle Eastern petroleum production during the 1970s, China presently leads the worldwide processing of essential metals that form the backbone of the United States economy. In the 1970s, America’s reliance on oil resulted in shortages that hindered growth and caused significant price increases. However, in recent years, U.S. fracking advancements have created…
-
Seven UW Scholars Awarded Prestigious Fulbright Grants for Global Study and Research Opportunities
“`html Seven UW scholars and recent graduates have been chosen for Fulbright exchange honors. Top row: Emily Bassett, Thomas Key, Vincent Da, Elana Skeers. Bottom row: Sabrina Prestes Oliveira, Jack Regala, and Annabella Lee.University of Washington Seven UW scholars and recent graduates were granted Fulbright U.S. Student Program scholarships for the 2025–2026 academic session, joining…
-
Building Bridges: A Gender Equity Advocate’s Role in Creating an Inclusive Community for LGBTQ+ Students

Joanna Villegas, the associate director of student initiatives and leadership at the Gender Equity Resource Hub, contemplates the efforts they undertake and presents resources accessible to students. The article How one Gender Equity staff member cultivates community for LGBTQ+ students on campus was originally published on Berkeley News.
-
The Feathered Giant: Rethinking the Image of Dinosaurs
UC Berkeley paleontologist Jack Tseng describes how recent findings contest our longstanding perceptions regarding the realm of paleontology. The article A T. rex with feathers? Researchers assert that dinosaurs were probably unlike what most of us envision was originally published on Berkeley News.
-
Impending Medicaid Cuts May Significantly Affect Older Workforce Segments

Individuals between the ages of 50 and 64 are progressively forced out of the job market due to declining health, age bias, and the responsibility of caring for elderly relatives. Reducing Medicaid funding would jeopardize their health and wellness, according to an analyst from UC Berkeley. The article Proposed Medicaid cuts could have a ‘far-reaching,…
-
Revolutionary AI Tool Transforms How Patients Decode Their Radiology Reports

“RadGPT” simplifies medical terminology to respond to typical patient inquiries.
-
Stanford Unveils ‘Last Mile’ Initiative to Enhance Mail Efficiency and Promote Sustainability

The student parcel handling and distribution system will commence this autumn and is a component of the recently introduced Mail and Package Services initiative announced earlier this year.
-
An Intimate Encounter with Es Devlin

Es Devlin, the honoree of the 2025 Eugene McDermott Award in the Arts at MIT, designs environments for individuals to unite — be it a small gathering in a room or throngs filling a massive stadium — spaces in which to blend one’s personal identity with the larger community. She embodies numerous influences; equally comfortable…
-
FAMU-FSU College of Engineering Faculty Honored with Prestigious International Young Investigator Award for Innovative Blood Clotting Research
“`html FAMU-FSU College of Engineering Assistant Professor Z. Leonardo Liu has been honored with the 2024 Eberhard F. Mammen Young Investigator Award for his innovative research into the mechanisms of blood coagulation. Liu stands out as the sole recipient from the United States among six international awardees, placing him among the most promising emerging researchers…
-
Empowering Futures: The Role of New Educators in Advancing Fair Science Education

“`html Research: Demonstrating Four Collaborative Methods to Equity Among Pre-Service Elementary Science Teachers: “If This is Our Approach to Science, Then The Future May Improve Significantly” Recent findings from the University of Michigan highlight that novice elementary instructors advocating for equity in science are notably successful in engaging students from diverse backgrounds. Researchers at U-M…
-
Raising the Bar: Customized Support Empowers Struggling Readers
“`html Research: The Effects of Grade Repetition Policy With Minimal Retention Regulations advocating for retaining children in elementary school to enhance their reading abilities are prevalent—if not well-received—throughout the United States. Nonetheless, the advantages for students seem to stem from the supplemental services established once they are identified for grade repetition—not the retention per se—according…
-
Shifting Focus: The Dance of Attention in Ever-Changing Environments

In a recent investigation, Yale scholars present a novel framework of human attention that clarifies how the brain assesses pertinent elements in a fluid environment — and allocates, in real time, cognitive resources appropriately.
-
Yale Introduces Innovative Courses to Shift the Dialogue on Ukraine

Olha Tytarenko, who launched a Ukrainian language course on campus for Yale students last year, is now incorporating additional courses and initiatives that she asserts will enhance students’ comprehension of the nation.
-
Crafting SPHEREx in a Caltech Lab Space

“`html Chi Nguyen recalls the instance when she connected her laptop to a sizable monitor in a conference hall, prompting the audience to applaud. She was showcasing a group of scientists, engineers, and administrators at NASA’s Jet Propulsion Laboratory (JPL), which is overseen by Caltech, with the initial “aliveness test” image captured by the agency’s…
-
Presidential Update: New Faculty Appointments in the Academic Council

The subsequent appointments, promotions, and reappointments of the Academic Council faculty were evaluated by the Advisory Board of the Academic Council and sanctioned by the president.
-
Jeannette Wang Honored as Newman Civic Fellow for Enhancing Civic Engagement
The Stanford third-year student was acknowledged for her initiatives to bring together students from different political backgrounds and promote civic participation.
-
Revolutionary Research Reveals 500 Million Years of Biomass Evolution

Although researchers have been aware for some time that biodiversity has grown throughout geological history, this is the initial research to assess enduring patterns in the overall quantity of life. The results reinforce the assertion that preserving biodiversity is essential for the well-being of both humanity and the Earth.
-
Vulnerabilities in Open VSX Registry Put Millions of Developers at Risk of Supply Chain Attacks

Cybersecurity analysts have revealed a significant flaw in the Open VSX Registry (“open-vsx[.]org”) that, if effectively leveraged, might have allowed malicious actors to seize control of the complete Visual Studio Code extensions marketplace, presenting a grave supply chain threat. “This flaw grants attackers complete dominion over the entire extensions marketplace, thus granting them total control
-
Unpacking the Bear Down Blueprint: Desireé Reed-Francois on Arizona Athletics’ Vision

“`html Desireé Reed-Francois analyzes Arizona Athletics’ Bear Down Blueprint nprevenas Thu, 06/26/2025 – 11:03 Desireé Reed-Francois analyzes Arizona Athletics’ Bear Down Blueprint Wednesday Story Categories Athletics In the News By KGUN News Article Type External News “`
-
Mystifying Astronomers: Black Holes ‘Burp’ Repeatedly After Stellar Feasts

“`html Researchers perplexed by black holes that continue to ‘belch’ after consuming stars nprevenas Thu, 06/26/2025 – 11:02 Researchers perplexed by black holes that continue to ‘belch’ after consuming stars Wednesday Categories of the Story Current Affairs Science & Technology By Newsweek Type of News Article News from External Sources “`
-
TikTok Could Be Fueling Political Polarization, New Research Reveals

“`html Engaging with TikTok may lead to increased political polarization, recent research indicates nprevenas Thu, 06/26/2025 – 11:01 Engaging with TikTok may lead to increased political polarization, recent research indicates Today Story Categories Government, Public Policy & Law In the News Science & Technology By The Conversation News Article Type External News “`
-
The Giant Magellan Telescope Moves Forward in its Ambitious Journey

“`html The Colossal Magellan Telescope makes significant progress nprevenas Thu, 06/26/2025 – 11:00 The Colossal Magellan Telescope makes significant progress Wednesday News Categories Current Events Science & Technology Astronomy By The Planetary Society Type of News Article Outside News “`
-
7 Delightful Ways to Boost Your Oxytocin Levels for a Happier You

“`html 7 methods to obtain a delightful boost of hormone oxytocin nprevenas Thu, 06/26/2025 – 10:56 7 methods to obtain a delightful boost of hormone oxytocin Today Categories of the Story Health & Wellness Current Updates By The Washington Post Type of News Article External News “`
-
Resilience Revolution: Preparing for the Domino Effect of Cascading Hazards
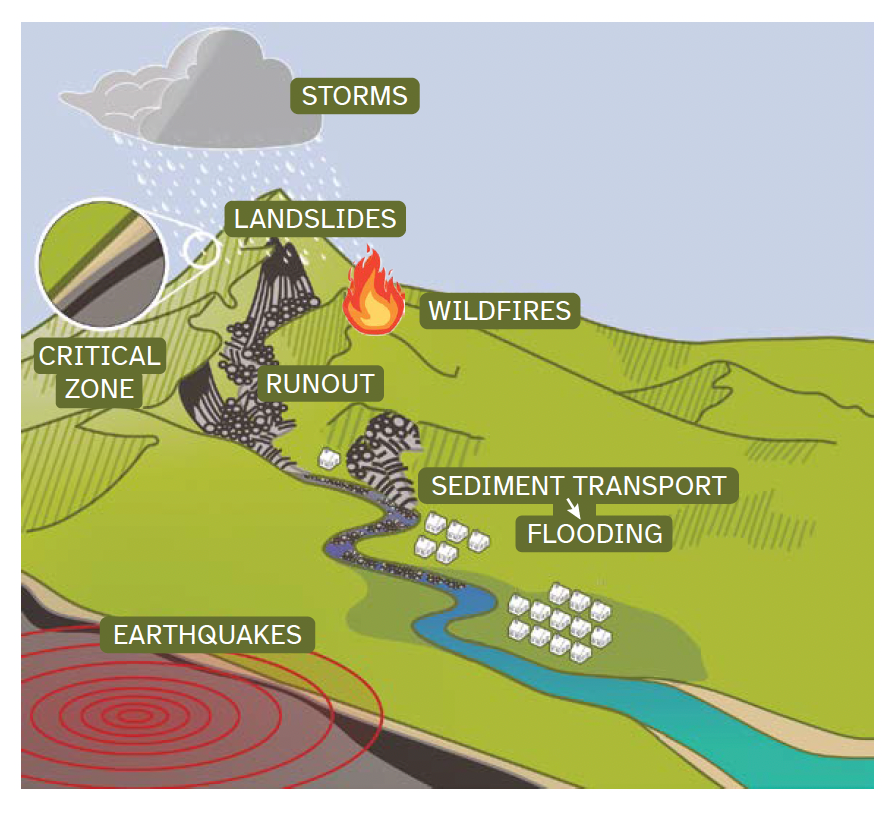
Researchers from the University of Michigan, along with collaborators from across the U.S., are striving to gain deeper insights into the interconnected hazards that arise from occurrences such as earthquakes and wildfires, aiming to enhance resilience against these downstream threats. Image credit: Courtesy of CLaSH Report: Cascading land surface hazards as a nexus in the…
-
MIT’s Summer 2025 Reading List: A Dive into Innovation and Imagination
Summer is an ideal season to settle in with an engaging book — and MIT authors have offered a wealth of material in the previous year. The following selections showcase some of the publications released in the last 12 months by MIT faculty and staff. Alongside links for each book from its publisher, the MIT…
-
Evelyn Wang: Pioneering Innovative Energy Solutions at MIT

“`html Evelyn Wang ’00 is well-versed in engineering solutions for challenging issues. After all, she developed a method to extract water from air. Currently, Wang is channeling her problem-solving skills — along with a persistent sense of hope — into the pressing matter of climate change, aiming to bolster the American energy sector and guarantee…
-
Outlook on the 2025-26 Fiscal Plan

The president and provost of Stanford offer an overview of the institution’s financial planning for the 2025-26 academic year.
-
The Quest for a Revolutionary Exercise Pill

“`html Health A workout medication? Christiane Wrann in her laboratory. Niles Singer/Harvard Staff Photographer Anna Lamb Harvard Staff Writer June 26, 2025 4 min read Scientists aim to leverage the cognitive advantages of physical activity for Alzheimer’s patients facing mobility challenges For numerous years, scholars have identified a correlation between physical activity and the development…
-
Voices of Solitude: Understanding America’s Perspective on Loneliness
“`html Health Insights from Americans on Isolation Artwork by Liz Zonarich/Harvard Staff Sy Boles Harvard Staff Writer June 26, 2025 1 min read Survey explores insights on a critical public health issue Studies have associated feelings of loneliness with an increased likelihood of illness and early mortality, prompting the U.S. Surgeon General to declare it…
-
Reimagining Civil Rights Advocacy for Modern Challenges

“`html Research: Frame Backfire: The Complications of Civil Rights Appeals in Modern-day America (DOI: 10.1177/00031224251333087journals.sagepub.com/home/asr) Civil rights appeals have traditionally played a critical role in advancing social transformation and protecting human rights in the United States. However, according to recent findings from the University of Michigan, leveraging civil rights for rallying public backing on contemporary…
-
Ornitz Secures NIH Funding for Lung Development Research
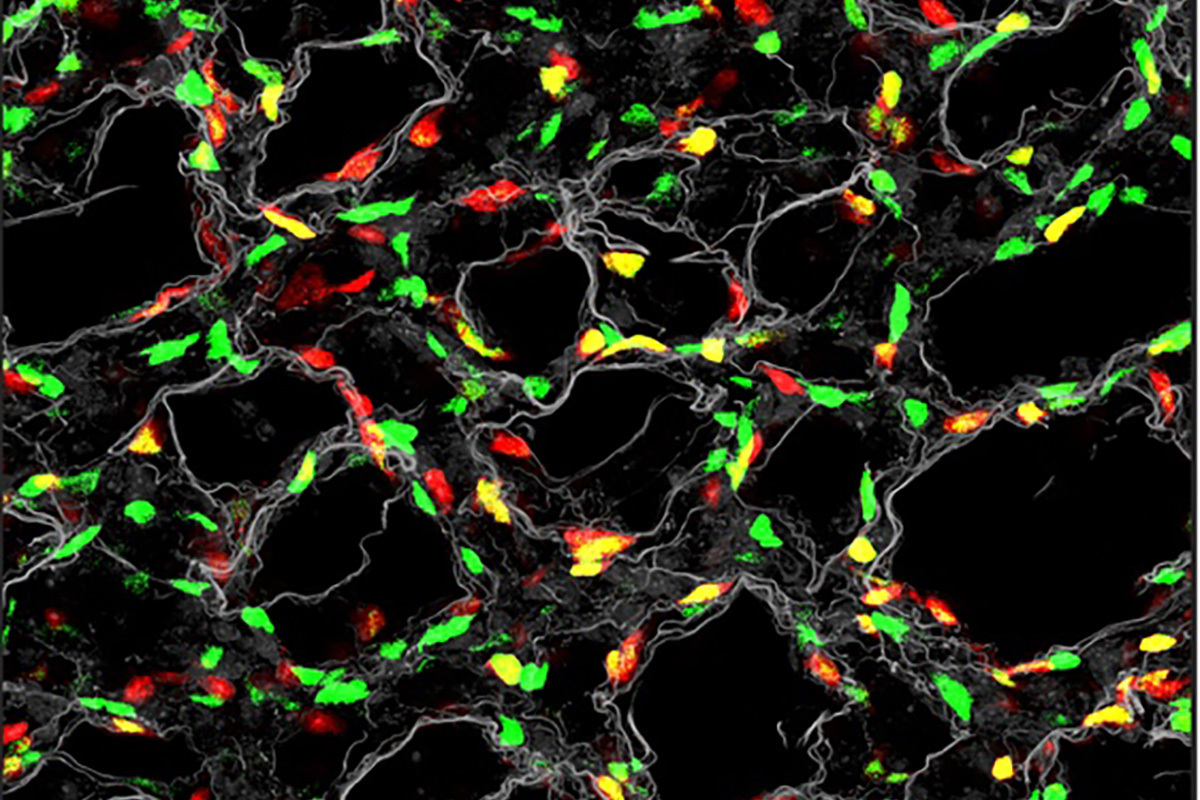
“`html The layout of the peripheral lung during neonatal mouse growth. Elastin fibers, a form of connective tissue, are depicted in white. Myofibroblasts, a cell type crucial for the creation of the lung’s air sacs, known as alveoli, are emphasized in yellow. The Ornitz laboratory has discovered that a molecule termed fibroblast growth factor 18…
-
Celebrating Brown: Honored Among Business Journal’s Influential Women

“`html Brown Rebecca Brown, vice chancellor for strategic initiatives and university governance at Washington University in St. Louis, has been recognized by the St. Louis Business Journal as part of its “Most Influential Business Women” cohort for 2025. Founded in 1999, the “Most Influential Business Women” honors annually acknowledge and commend women in the St.…
-
Research Reveals Historical Erratic Behavior of Winter Jet Stream Prior to Climate Change
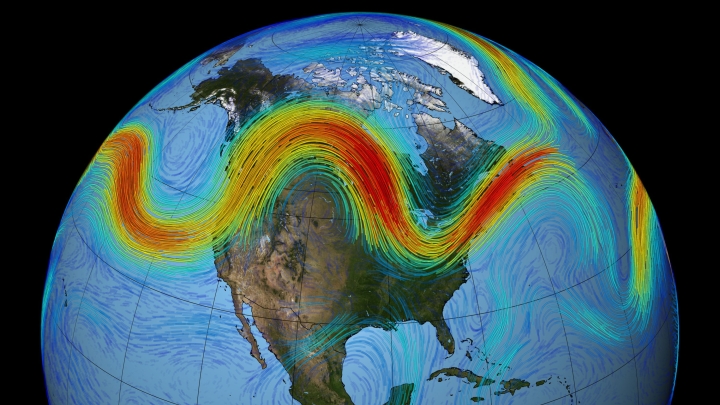
A Dartmouth group discovers unstable phases precede major impacts of climate change.
-
Revolutionary Study Unveils India’s Rich Genetic Tapestry

An examination of over 2,700 full genomes from South Asians reveals a rich array of historical and contemporary diversity along with genetic associations to ailments. The article Researchers finalize the most comprehensive study to date of India’s genetic variability first appeared on Berkeley News.
-
Severe RCE Vulnerabilities in Cisco ISE and ISE-PIC Enable Unrestricted Access for Malicious Actors

“`html Cisco has issued updates to rectify two critical-severity security vulnerabilities in Identity Services Engine (ISE) and ISE Passive Identity Connector (ISE-PIC) that may allow an unauthenticated intruder to carry out arbitrary commands with root user privileges. The vulnerabilities, designated with the CVE identifiers CVE-2025-20281 and CVE-2025-20282, both hold a CVSS rating of 10.0. A…
-
Emergence of New FileFix Method Raises Alarm After 517% Surge in ClickFix Attacks

The ClickFix social manipulation strategy as a primary entry point utilizing counterfeit CAPTCHA validations surged by 517% from the latter part of 2024 to the initial part of this year, based on statistics from ESET. “The catalog of dangers that ClickFix assaults result in is expanding daily, encompassing information stealers, ransomware, remote administration trojans, cryptominers,…
-
Understanding Functional Dependency in Database Management Systems

“`html In a database, merely saving data is insufficient. It must be organized effectively, devoid of duplicate values, and uniformly precise. Functional dependency aids in this by illustrating how one value in a table is reliant on another. It clarifies how one segment of the information correlates with another, which fosters appropriate design and an…
-
The Treasure of Moments

Commemorating $100 million in charitable contributions from the Terry Foundation The article The Gift of Time was originally published on UT Austin News – The University of Texas at Austin.
-
Pioneering Planetary Scientist Frank A. Podosek Passes Away at 83

Frank A. Podosek, a professor emeritus of earth, environmental, and planetary sciences at Washington University in St. Louis, passed away on Sunday, June 8, 2025, in Florida. He was 83 years of age. Podosek was an engaged faculty member from 1973 to 2011, performing isotopic examinations of natural substances to clarify the nature and history…
-
A Comprehensive Guide to Android Versions

“`html Android ranks among the leading mobile operating systems globally. Since its initial commercial launch, it has undergone numerous enhancements, with each update introducing a variety of features, enhanced performance, and heightened security. Every version of Android has delivered design advancements and new functionalities, rendering the system smarter, quicker, and more user-friendly. In this article,…
-
Understanding the Fibonacci Sequence in Java Programming

“`html Have you ever pondered how to compute the Fibonacci numbers using Java? What are the various methods to display the Fibonacci numbers in Java? Is it better to utilize loops, recursion, or dynamic programming, and which technique is the most efficient? Can you gather input from the user to determine how many numbers to…
-
Calculating the Total of Natural Numbers in Python

“`html Calculating the total of natural numbers is among the most frequent activities in programming, particularly when dealing with sequences, enumerating, or fundamental algorithms. Natural numbers are positive integers beginning from 1, and their total is frequently required in data evaluation, automation, and mathematical reasoning. This task can be simply accomplished in Python using loops,…
-
Unlocking the Power of Conditional Formatting in Excel: A Comprehensive Guide for All Skill Levels

“`html Conditional Formatting in Excel transcends mere color application—it involves transforming raw data into visual insights. This comprehensive, step-by-step guide delves into every feature within the Conditional Formatting menu. From basic highlights to sophisticated icon sets and formulas, we’ll navigate through all aspects utilizing a relatable dataset and actual screenshots. It’s perfect for novices and…
-
Understanding the Python str() Function: A Beginner’s Guide

“`html In Python, information appears in various formats, such as integers, arrays, or user-defined objects. Frequently, this information needs to be represented, stored, or transmitted in a comprehensible manner. The str() function facilitates this by transforming nearly any object into a neat and intelligible string. It functions seamlessly with built-in data types and is also…
-
Mastering Dijkstra’s Algorithm: The Path to Efficient Shortest Route Solutions

“`html Dijkstra’s algorithm is a fundamental and effective method for determining the shortest route in a graph with non-negative weighted edges. It is the most commonly utilized method for discovering the optimal answer for shortest pathfinding dilemmas in graph theory. Whether you are designing GPS navigation tools or developing AI pathfinding solutions, Dijkstra’s algorithm can…
-
C vs. C++: Understanding the Key Differences

“`html C and C++ are the most essential programming languages in computer science, as both serve a pivotal function in systems programming and software creation. Although they possess numerous similarities, their unique characteristics result in significant differences that affect their application in specific scenarios. The selection between C and C++ frequently hinges on the particular…
-
Understanding the `strip()` Function in Python: A Comprehensive Guide

“`html In Python, managing and manipulating text is an essential task, particularly when dealing with user input, file content, or web scraping. Strings often harbor unnecessary spaces or characters at the start or finish, which may lead to issues during processing or comparisons. Python provides a very efficient method to address this concern as it…
-
Essential Tools for Effective Data Modeling

“`html In the contemporary data-oriented landscape, establishing a robust framework for data management is vital for making knowledgeable and strategic selections. Data Modeling Tools are instrumental in generating clear visual diagrams that illustrate how data is stored, linked, and applied across diverse systems. These tools assist teams in streamlining reporting, facilitating advanced analytics, guaranteeing data…
-
Understanding Java Generics: A Comprehensive Guide

“`html Generics in Java represent a robust capability introduced in Java 5 that permits developers to create adaptable, type-safe, resilient, and reusable code. By allowing classes, interfaces, and methods to function on specified type parameters, generics eliminate the necessity for explicit type conversion, thereby minimizing the risk of runtime issues like ClassCastException. This article will…