-
Microsoft Reveals Vulnerability in Exchange Server Allowing Stealthy Cloud Access in Hybrid Configurations

Microsoft has issued a notification concerning a significant security vulnerability impacting on-premise iterations of Exchange Server that might permit an attacker to obtain elevated permissions under specific circumstances. The flaw, identified as CVE-2025-53786, has a CVSS rating of 8.0. Dirk-jan Mollema from Outsider Security has been recognized for bringing attention to this issue. “In the…
-
Over 6,500 Axis Servers Put Remoting Protocol at Risk, with 4,000 Located in the U.S. Facing Potential Exploits
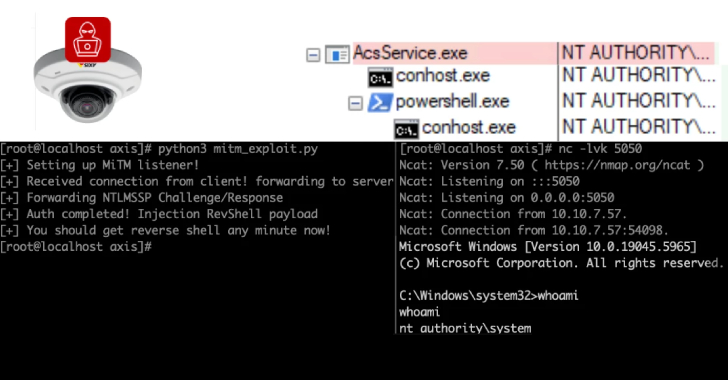
“`html Cybersecurity experts have revealed several security vulnerabilities in video monitoring products from Axis Communications that, if effectively leveraged, could leave them vulnerable to takeover assaults. “The exploitation leads to pre-authentication remote code execution on Axis Device Manager, a server utilized to set up and oversee groups of cameras, along with the Axis Camera Station,…
-
SonicWall Addresses Exploited Vulnerability Linked to Recent VPN Attacks, Clarifies It Is Not a Zero-Day Issue

SonicWall has disclosed that the recent surge in incidents aimed at its Generation 7 and more recent firewalls with SSL VPN activated is associated with an outdated, now-resolved flaw and the reuse of passwords. “We are now highly confident that the recent SSL VPN incidents are not linked to a zero-day vulnerability,” the firm stated.…
-
Empowering Scholars: How Georgia’s Thrive Program Facilitates Smooth College Transitions

Fourteen new students began their academic journey this summer through Thrive at Georgia: Bulldog Bridge, a weeklong residential initiative designed to assist students in feeling ready, connected, and enthusiastic about their inaugural year at the University of Georgia. The initiative, conducted on UGA’s premises from July 25 to Aug. 1, familiarized the students with collegiate…
-
UGA Selects New Alumni President and Board Members

The University of Georgia Alumni Association Board of Directors has chosen its 79th president, Corey Dortch (BSA ’03, MED ’05, PHD ’11), and has welcomed seven new board members. Their tenures commenced on July 1. Dortch has been part of the board since 2016 and takes over from Lee Zell (AB ’96), whose two-year term…
-
China Claims Nvidia Has Embedded Backdoors in Its Chips

The authorities of China have charged Nvidia with embedding a backdoor in their H20 processors: On Thursday, China’s cyber regulatory body announced it conducted a discussion with Nvidia regarding what it termed “serious security concerns” pertaining to the firm’s artificial intelligence processors. It stated that US AI specialists had “indicated that Nvidia’s computing processors include…
-
Unlocking the Ocean’s Potential: Can the Seafloor Enhance CO2 Absorption?

“`html Will Berelson’s research group prepares to deploy the porewater sampler off the coast of Huntington Beach. The sampler is lowered to the ocean floor, where spring-loaded syringes extract water between grains of sand and mud through filters in quartz collection coils. (USC Photo/Stephen Gee) Share Science/Technology Can the seabed assist the ocean in absorbing…
-
Defending Your Python Supply Chain: Essential Strategies and Tools for Prevention
“`html Python is pervasive in contemporary software. From machine learning frameworks to operational microservices, it’s likely that your code—and your enterprise—relies on Python libraries you didn’t develop. However, in 2025, that confidence carries a significant danger. Every few weeks, we encounter new reports about harmful packages submitted to the Python Package Index (PyPI)—many remaining unnoticed…
-
From Trojan Pride to Stem Cell Science: A Journey Through Molecular Biology

Guanyi Huang — currently an associate principal scientist at MerckBodye — attributes his education at USC with positioning him at the leading edge of advancements in biological research.
-
Driving Green: How Eco-Friendly Habits Can Slash Vehicle Emissions

Any driver who has ever endured several cycles for a traffic light to change knows how frustrating signalized crossings can be. However, waiting at crossings isn’t just a nuisance for drivers — idle vehicles could account for as much as 15 percent of the carbon dioxide emissions from U.S. land transport. A comprehensive modeling research…
-
California’s Secret Archive: Unveiling 1.5 Million Pages of Police Records to the Public

Constructed by UC Berkeley and Stanford University, the database will significantly enhance public access to documents that reveal how law enforcement bodies manage claims of misconduct. The article New database unveils 1.5 million pages of previously confidential California police documents was originally published on Berkeley News.
-
Exploring the Digital Landscape: Internet Scanning Insights from ASN 43350
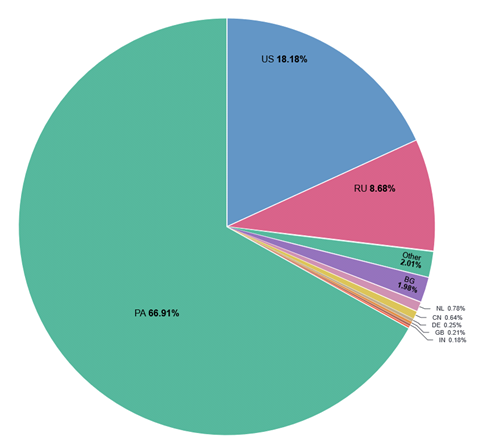
[This is a Guest Journal authored by Duncan Woosley, an ISC trainee participating in the SANS.edu BACS initiative]
-
Harnessing Workforce Potential in the Age of AI | Join Our Webinar on 14-08-2025 at 17:00

Are your clients prepared for today’s AI-driven employment landscape? As a workforce development expert, you hold a vital position in steering job hunters toward rewarding, sustainable professions. However, maneuvering through the technology-centric job environment demands training programs that are compliant, career-oriented, and results-driven. In this 45-minute session designed…Read More.
-
USC Rossier Launches Second Year of Doctor of Education in Mental Health Leadership Program

The groundbreaking initiative addresses an essential void in mental health education, equipping learners for achievement in leadership positions.
-
Exposing ECScape Vulnerability in Amazon ECS: A Gateway for Credential Theft Across Tasks

Cybersecurity analysts have showcased an “end-to-end privilege elevation sequence” within Amazon Elastic Container Service (ECS) that could be leveraged by an attacker to perform lateral movement, retrieve sensitive information, and gain control over the cloud ecosystem. The method of attack has been assigned the codename ECScape by Sweet Security investigator Naor Haziz, who unveiled the…
-
USC Rossier’s Doctor of Education in Mental Health Leadership program enters second year
The innovative program fills a critical gap in mental health education, preparing students for success in leadership roles.
-
Embarking on Your Journey to Oracle Certification: What’s Next?

Embarking on Your Journey to Oracle Certification: What’s Next?
-
Elevate Your Career: The Top 10 Oracle Cloud Certifications You Need for 2025
Elevate Your Career: The Top 10 Oracle Cloud Certifications You Need for 2025
-
Elevate Your Career with Oracle Fusion Cloud Applications Certification: Discover Free and Professional Pathways for Every Aspiration
Elevate Your Career with Oracle Fusion Cloud Applications Certification: Discover Free and Professional Pathways for Every Aspiration
-
Harmonizing Surgical Choices with the Aspirations of Older Adults
Researchers unveil a novel decision-making instrument designed to synchronize surgical procedures with the priorities that are most significant to each older adult.
-
Groundbreaking Study Uncovers Vibrant Microbial Ecosystems Within Trees

The research conducted by YSE researchers paves the way for deeper insights into tree biology, forest ecosystems, and the ways in which trees are reacting to climatic shifts.
-
The Impact of Past Trauma on Our Brain’s Reaction to New Stressors

When faced with slight stressors, neural networks linked to previous trauma demonstrated decreased connectivity, as discovered by Yale researchers find.
-
Living with a ‘Sacramental Lens’: The Journey of YDS Graduate Chad Tanaka Pack

Chad Tanaka Pack ‘10 M.Div. has analyzed figures on Wall Street, held the position of controller at a nonprofit offering legal assistance on LA’s Skid Row, and acted as an ordained minister and associate conference minister in the United Church of Christ.
-
Empowering Rural Education: Yalies Introduce AP STEM Courses in the Mississippi Delta

An academic institution established by Yale graduates provides almost all AP STEM courses in Mississippi’s most disadvantaged areas — at no cost.
-
Unlocking Evolution: Insights from a Jawless Vertebrate Parasite on Thyroid Origins

“`html The thyroid, an essential endocrine gland in vertebrates, plays a crucial role in controlling metabolism and aiding growth. It is the first gland of both the nervous and endocrine systems to mature during an embryo’s development, having first emerged over 500 million years ago from a “primitive“ precursor organ in chordates known as the…
-
MIT-Africa Unveils Exciting Partnership with Angola

The MIT Center for International Studies has revealed the initiation of a new pilot program with Angola, to be carried out via its MIT-Africa Program. This new endeavor signifies an important partnership among MIT-Africa, Sonangol (Angola’s national energy corporation), and the Instituto Superior Politécnico de Tecnologias e Ciências (ISPTEC). The partnership was formalized during a…
-
New Faces Join the School of Architecture and Planning for 2025

“`html Four new educators become part of the School of Architecture and Planning (SA+P) this autumn, providing the MIT community with creativity, expertise, and scholarship across various disciplines. “These individuals significantly enhance the strength and breadth of our faculty,” states Hashim Sarkis, dean of the School of Architecture and Planning. “We look forward to the…
-
Unraveling the Ancient Roots of Addiction: Insights for the Modern Mind

Researchers at Stanford Medicine investigate how our brain, inherently shaped for reward-seeking behavior, can be exploited by addiction, and they examine approaches for prevention and therapy.
-
Could Lithium Hold the Key to Understanding and Treating Alzheimer’s?
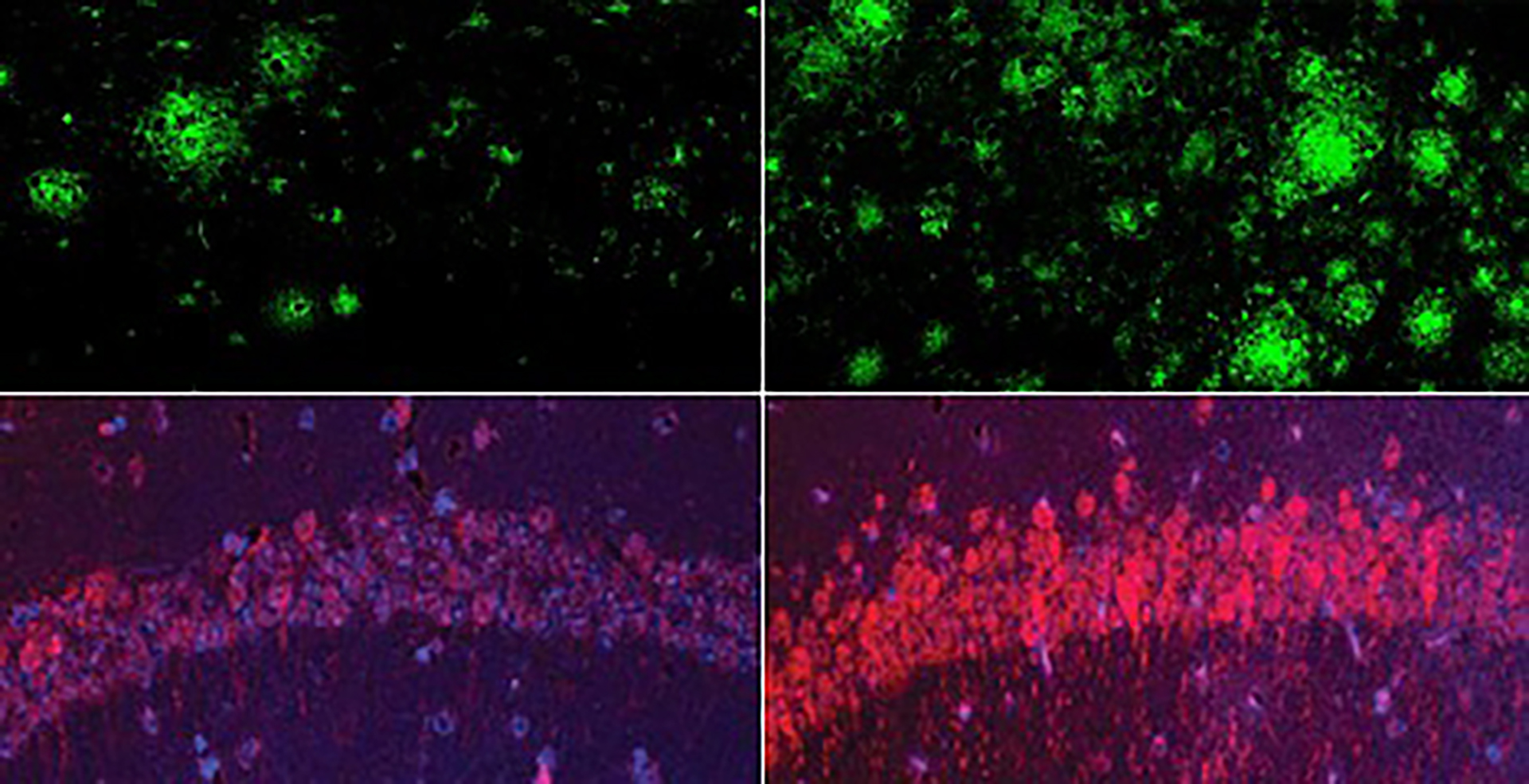
“`html Health Can lithium clarify — and potentially treat — Alzheimer’s? In a mouse model of Alzheimer’s disease, a shortage of lithium (right) greatly increased amyloid beta deposits in the brain when compared to mice with normal lithium levels (left). Bottom row: The same was true for the Alzheimer’s neurofibrillary tangle protein tau. Yankner Lab…
-
Deceptive VPN and Spam Filter Apps Linked to VexTrio Uncovered in Advertising Fraud and Subscription Scams

“`html The nefarious ad technology supplier referred to as VexTrio Viper has been noted for creating a number of harmful applications that have been released on the official app marketplaces of Apple and Google, presented as ostensibly beneficial software. These applications disguise themselves as VPNs, device “surveillance” tools, RAM optimizers, dating platforms, and spam filters,…
-
Reviving a Classic: Florida State PhD Student Breathes New Life into Vintage Novel on Fulbright in France
For numerous authors, finalizing a creative piece necessitates multiple revisions or perhaps an entire rewrite. Samuel Granoff, a doctoral student in the Department of Englishat Florida State University, had put his unfinished World War I novel aside until the Fulbright U.S. Student Program provided him with the opportunity, environment, and motivation to begin anew. Granoff…
-
Exploring the Link Between Cattle Diets and Salmonella Levels: A Texas A&M Study

High-carbohydrate diets may lower harmful bacteria in beef cattle, providing innovative food safety approaches.
-
Honoring the Legacy of Glorya Kaufman: USC Life Trustee and Philanthropic Visionary

“`html Glorya Kaufman arrives at the USC Kaufman School 10th anniversary festivity in May. (USC Photo/Greg Grudt) Disseminate University In remembrance: Glorya Kaufman, USC Life Trustee and benefactor The distinguished arts supporter founded and funded the USC Kaufman School of Dance. August 06, 2025 By USC Staff Glorya Kaufman, a USC Life Trustee and globally…
-
USC Rossier Unveils Innovative Online Master’s in Education Focusing on AI and Future Technologies
The program, crafted at the convergence of educational design, artificial intelligence, and pedagogical advancement, will equip individuals to spearhead innovative instructional design within their workplace environments.
-
Unveiling the Universe’s First Confirmed Black Hole: A Cosmic Giant from the Dawn of Existence

AUSTIN, Texas — A global team of astronomers, spearheaded by The University of Texas at Austin’s Cosmic Frontier Center, has discovered the most remote black hole ever validated. It, along with its host galaxy, CAPERS-LRD-z9, exists 500 million years subsequent to the Big Bang. This positions it 13.3 billion years into the past, at which…
-
Smart Money Moves for First-Year College Students

“`html Enroll in courses. Locate extra long bed linens. Gather microwave popcorn. As incoming students prepare for university, Andrea Stewart-Douglas, the first director of student financial wellness initiatives at Washington University in St. Louis, adds one more task to their checklist: Formulate a budget. “For many students, this marks the first instance of making financial…
-
Philosophy to Future: The Journey from Aristotle to Artificial Intelligence

It is quite uncommon for high schools to provide philosophy courses. And that’s unfortunate, remarked WashU’s Allan Hazlett, a philosophy professor in Arts & Sciences, because adolescents tend to be intrinsic philosophers. “It’s the grown-ups who are rigid and unyielding,” Hazlett noted. “Younger individuals are generally more imaginative, more open to new ideas, and more…
-
Revolutionizing Language Learning: The Role of AI in Education

Yale senior lecturer Michael Farina discusses how AI “TutorBots” can assist students in acquiring languages and promote more dynamic, participatory classrooms.
-
Diving Deep: Student Research Uncovers Connection Between Ocean Swimming and UTIs

Meredith Klashman, a scholar from UC Berkeley, initiated a research project following recent findings indicating that environmental pollution might contribute to UTIs. The article Student-led research finds link between ocean swimming and urinary tract infections was originally published on Berkeley News.
-
Influential Economic Historian Peter Temin Passes Away at 87

Peter Temin PhD ’64, the MIT Elisha Gray II Professor of Economics, emeritus, passed away on Aug. 4. He was 87. Temin was an eminent economic historian whose research encompassed an impressive array of subjects, ranging from the British Industrial Revolution and Roman economic history to the reasons behind the Great Depression and, later in…
-
The Hidden Influence of Your Upbringing on Your Credit Score

“`html Jamie Fogel. Niles Singer/Harvard Staff Photographer Work & Economy What your credit score indicates about your upbringing Research examines national inequalities, finds bill-paying behaviors surface by early adulthood, affecting upward mobility Christy DeSmith Harvard Staff Writer August 6, 2025 6 min read An individual’s credit report narrates a tale of their formative years. Recent…
-
Concerns Grow Among Researchers About the Stability of U.S. Innovation Foundations

“`html Nation & World Foundation for U.S. innovations appears more unstable to researchers August 6, 2025 6 min read Cuts in funding with economic reverberations regarded as a danger to the U.S.’s position as a global leader in scientific advancement With every dollar allocated through its grants, the National Institutes of Health — the premier…
-
FSU and Andrews Foundation Partner to Launch Physician Fellowship Initiative in Northwest Florida

Florida State University is intensifying its commitment to enhanced medical training and healthcare in Northwest Florida through a novel alliance between the FSU College of Medicine and the Andrews Research & Education Foundation. The arrangement, effective from Aug. 1, incorporates the Orthopedic and Sports Medicine Fellowship and the Primary Care Sports Medicine Fellowship under FSU’s…
-
AI Chatbots: Subtle Influencers of Political Perspectives

“`html Researchers from the University of Washington enlisted participants identifying as Democrats and Republicans to make political judgments with assistance from three variations of ChatGPT: a fundamental model, one exhibiting liberal bias, and another displaying conservative bias. Both Democrats and Republicans demonstrated a stronger tendency to align with the biased chatbot they engaged with compared…
-
Decline in Recreational Use of Prescription ADHD Medications Among Teenagers

“`html Research: Patterns in Medical and Nonmedical Use of Prescription Stimulants Among US Adolescents (DOI: 10.1001/jama.2025.11260) Although there are worries regarding the rise in stimulant prescriptions, the nonmedical usage of ADHD medications among adolescents has decreased over the past two decades, a study from the University of Michigan reveals. While the prescription of stimulants for…
-
Empowering Communities: How a U-M Startup Uses Data Science for Positive Change in Flint and Beyond

EXPERT ADVISORY More than ten years later, the tale of one Michigan city’s challenges is widely recognized. In 2014, Flint transitioned its drinking water source from the Detroit system to the Flint River in an effort to reduce costs. The water was inadequately treated, resulting in a health crisis where residents encountered lead contamination and…
-
Navigating Loss: A Mother’s Journey Through Grief and Cicadas

In 2004, Yale investigator Kim Hieftje’s 6-year-old child passed away due to cardiac issues. She is applying that experience along with her knowledge of video games to assist other families.
-
Unleashing Creativity: Wharton Online’s Innovative Course for the AI Era

“`html By Marni Baker Stein, Chief Content Officer, Coursera Ingenuity is a potent ability that converts obstacles and insights into significant chances for innovation and progress. Yet most professionals have not been educated on how to be systematically inventive, even as AI transforms our approaches to addressing issues, generating concepts, and achieving results. Today, I’m…
-
The Strength of Community: How Neighborly Bonds Enhance Disaster Preparedness, According to Texas A&M Research

Studies concerning the 2015 floods demonstrate that robust community connections improve resilience following disasters, providing essential information for health officials and emergency management strategists.
-
Savor the Flavors: Farm Club’s Artisan Brick Oven Pizzas

The student organization informs the community about the Organic Farm.
-
Coosa River Sees a Resurgence of Lake Sturgeon Population

Lake sturgeon were previously plentiful in Georgia’s Coosa River before vanishing entirely. Currently, a program aimed at their resurgence is demonstrating significant advancements, according to a recent study from the University of Georgia. The ancestry of the lake sturgeon can be traced back millions of years, dating back to the age of the dinosaurs. However,…
-
FAMU-FSU College of Engineering Faculty Member Inducted as Fellow of the Royal Aeronautical Society

“`html When Farrukh Alvi entered the realm of engineering, he lacked a comprehensive strategy. His initial focus as an undergraduate was on nuclear engineering, primarily because “it appeared quite fascinating.” However, his courses in mechanical engineering, particularly fluid dynamics, captivated him. He pursued that inquisitiveness, which ultimately directed him to a supersonic wind tunnel during…
-
Groundbreaking Research Links Weight Loss Effects to Binge Eating Behavior at FSU
The article New discoveries by FSU researchers link the biological and behavioral effects of weight reduction to binge eating was first published on News from Florida State University.
-
FSU Graduates Embrace New Beginnings at Summer Commencement

The article Summer Commencement Signals a New Chapter for FSU Graduates was originally published on Florida State University News.
-
University of Arizona Unveils Financial Strategy to Navigate Federal Funding Standstill

“`html University of Arizona discovers financial remedy to federal funding halt nprevenas Wed, 08/06/2025 – 05:51 University of Arizona discovers financial remedy to federal funding halt Tuesday Categories of the Story Current Events Science & Innovation By KOLD Type of News Article News from External Sources “`
-
Sophomore Summer Bash Launches at the Bema

The Dartmouth Dialogues occasion honors the summer semester and fosters comprehension.
-
Arrests Made During the Crackdown on the XSS Crime Forum

“`html On July 22, 2025, the European law enforcement agency Europol announced that a lengthy inquiry spearheaded by the French authorities led to the detainment of a 38-year-old operator of XSS, a cybercrime forum in Russian with over 50,000 members. This operation has sparked a wave of conjecture and anxiety among XSS users regarding the…
-
AI Reduces vCISO Workloads by 68% Amid Rising SMB Demands – New Study Uncovered

As the frequency and complexity of cyber threats and vulnerabilities increase, cybersecurity has become essential for enterprises of every scale. In response to this transition, SMBs are rapidly seeking vCISO services to manage rising threats and regulatory requirements. A recent study by Cynomi revealed that an impressive 79% of MSPs and MSSPs recognize significant demand…
-
Microsoft Unveils Project Ire: Harnessing AI to Automatically Identify Malware

Microsoft on Tuesday unveiled a self-sufficient artificial intelligence (AI) agent capable of examining and categorizing software independently, aiming to enhance malware detection initiatives. The extensive language model (LLM)-driven self-operating malware classification system, which is presently in prototype form, has been designated Project Ire by the technology leader. The system “streamlines what is regarded as the…
-
Trend Micro Confirms Ongoing Exploitation of Critical Vulnerabilities in Apex One On-Premise Solutions

Trend Micro has announced remedies to tackle significant security vulnerabilities in on-premises iterations of the Apex One Management Console, which it claims have been actively targeted in real-world attacks. The flaws (CVE-2025-54948 and CVE-2025-54987), each assessed at 9.4 on the CVSS rating scale, are characterized as command injection issues within the management console and remote…
-
CERT-UA Issues Alert on C# Malware Threats Spread via Court Summons Phishing Tactics

The Ukrainian Computer Emergency Response Team (CERT-UA) has alerted about cyber assaults executed by a malicious entity known as UAC-0099, which is directing its efforts towards governmental bodies, military forces, and firms within the defense-industrial sector of the nation. The assaults, which utilize phishing emails as a primary infiltration method, aim to deploy malware varieties…
-
Sextortion Scams: Are They Still Effective in 2025?
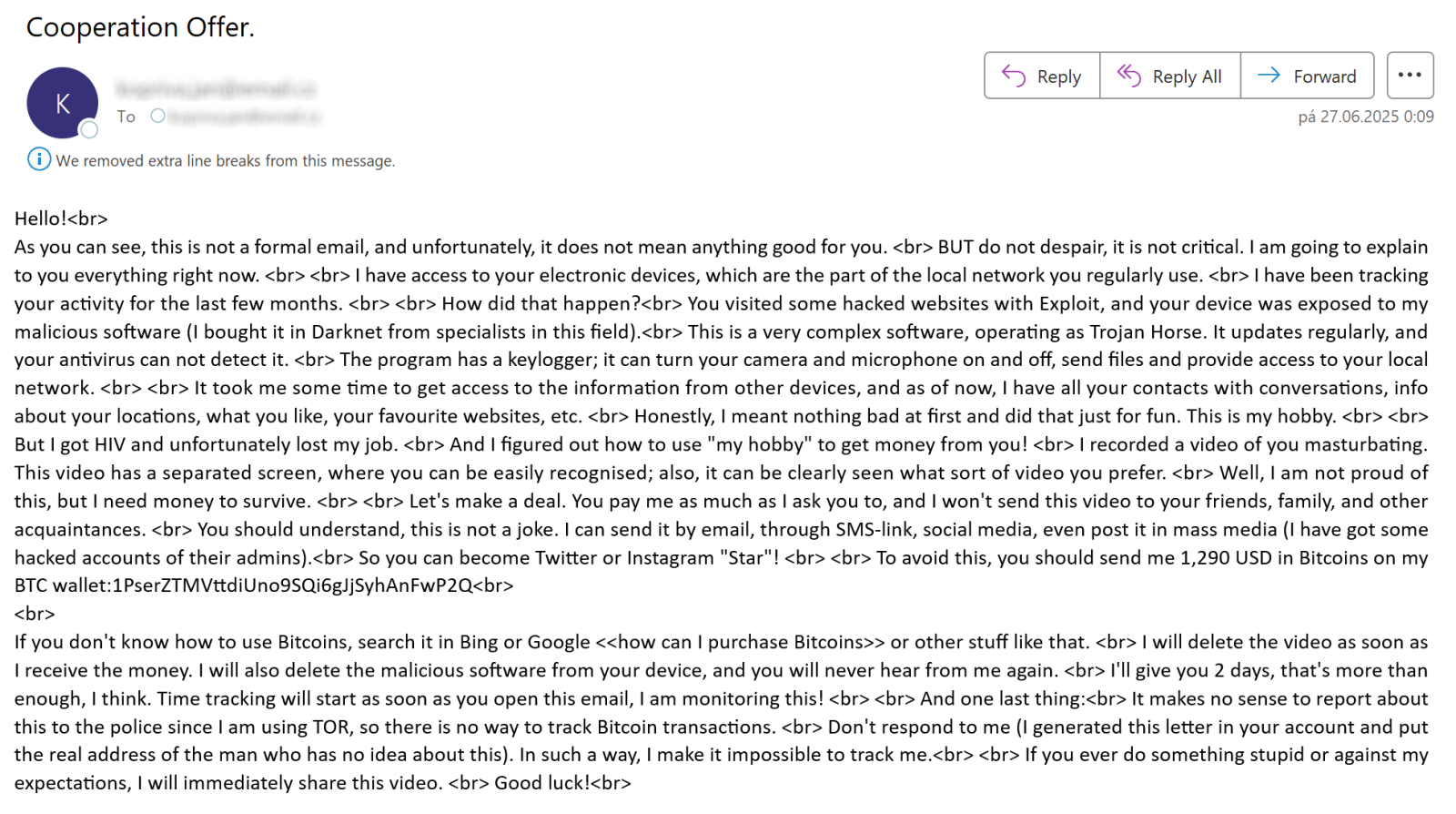
Sextortion emails have been around for a significant period, and currently, many cybersecurity experts view them more as a form of “email background noise” rather than a substantial danger. Considering their prevalence is fairly recognized even by the general populace, this perspective appears to be warranted… But are sextortion communications genuinely insignificant as a threat…
-
Revolutionary Discoveries Unveil New Secrets of the Human Gut Microbiome

Doctoral candidate Nicolaus Jakowec aids in revealing fresh perspectives on the minute organisms that influence human well-being.
-
Revelations in Spinal Cord Research: Unraveling its Influence on Bladder Management

A groundbreaking study provides optimism for upcoming therapies addressing urinary incontinence resulting from neurological issues, aging, and various other factors.
-
Revolutionizing Cybersecurity: The Vision Behind AI-Driven Adversarial Testing by Pentera’s Founder

“`html When Technology Rejuvenates the Landscape In 2015, I established a cybersecurity evaluation software firm, driven by the conviction that automated penetration assessment was not merely feasible, but essential. Back then, this notion frequently encountered doubt; however, currently, boasting over 1200 enterprise clients and countless users, that vision has validated itself. Yet, I am also…
-
CISA Adds New D-Link Router Vulnerabilities to KEV List Following Exploitation Alerts
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday incorporated three legacy security weaknesses affecting D-Link routers into its Known Exploited Vulnerabilities (KEV) catalog, citing proof of ongoing exploitation in the field. The critical vulnerabilities, dating back to 2020 and 2022, are detailed below – CVE-2020-25078 (CVSS score: 7.5) – An unidentified flaw in…
-
Empowering Data Storage for the AI Revolution

“`html Artificial intelligence is transforming the manner in which enterprises store and access their information. This is due to the fact that conventional data storage solutions were constructed to manage simple commands from a limited number of users simultaneously, while current AI systems, equipped with millions of agents, necessitate ongoing access and processing of vast…
-
Navigating Regulatory Compliance in the Semiconductor Industry

“`html Earlier this week, the Trump administration narrowed export regulations on advanced semiconductors prior to US-China trade discussions. The administration is progressively depending on export licenses to enable American semiconductor companies to distribute their products to Chinese clients while securing the most potent of them from our military competitors. These chips power the artificial intelligence…
-
Helping data storage keep up with the AI revolution
Artificial intelligence is changing the way businesses store and access their data. That’s because traditional data storage systems were designed to handle simple commands from a handful of users at once, whereas today, AI systems with millions of agents need to continuously access and process large amounts of data in parallel. Traditional data storage systems…
-
Emerging Insights: Quantum Chaos Arrives Earlier Than Expected

“`html The procedure of scrambling a couple of eggs—breaking them, beating the yolk and whites, pouring the mixture into a skillet, and stirring—may take a few minutes. One can observe the procedure unfolding and gain insights into how the scrambling transpires. Now, a recent theoretical article in Science reveals that, under appropriate circumstances, the subatomic…
-
R. Michael Alvarez of Caltech Honored with Career Achievement Award by the Society for Political Methodology
R. Michael Alvarez, the Flintridge Foundation Professor of Political and Computational Social Science at Caltech, has been honored with the Society for Political Methodology’s Career Achievement Award for his work in modeling electoral dynamics and his contributions to the field. Established in 1983 as a branch of the American Political Science Association, the Society for…
-
Innovative Underwater Sensors Created by UC Berkeley Engineers Enhance Energy Efficiency

This advancement might facilitate advanced computing architectures that combine memory and perception in aquatic environments, similar to the operation of neurons in the human brain. The article UC Berkeley engineers develop energy-efficient sensors that work underwater was originally published on Berkeley News.
-
Stanford Athletics Unveils 2025 Hall of Fame Inductees

On Sept. 26, ten notable graduates will be honored, with public acknowledgment during the football match against San Jose State on Sept. 27.
-
Transforming Disease Management by Unraveling Ribosomal Mysteries

Maria Barna along with her team has created methods to chart ribosomes with an unparalleled degree of precision. This research may transform our comprehension and management of numerous illnesses.
-
First Cohort of CUNY Honors Connect Showcases Innovative Research

This summer, Cornell Tech hosted the inaugural group of the City University of New York (CUNY) Honors Connect initiative, which concluded with a display of student-driven research on July 31.
-
FSU’s University Health Services to Boost Vaping Prevention Initiatives with Fresh Funding

Florida State University has maintained a 100% tobacco/nicotine-free policy since 2014. Thanks to a new two-year grant from the Truth Initiative’s Tobacco/Nicotine-Free College Program, FSU’s Center for Health Advocacy & Wellness (CHAW) can enhance their prevention activities. CHAW, functioning under FSU’s University Health Services, received a $20,000 grant to bolster its vaping prevention efforts. The…
-
Florida State University’s College of Motion Picture Arts Soars in National Rankings
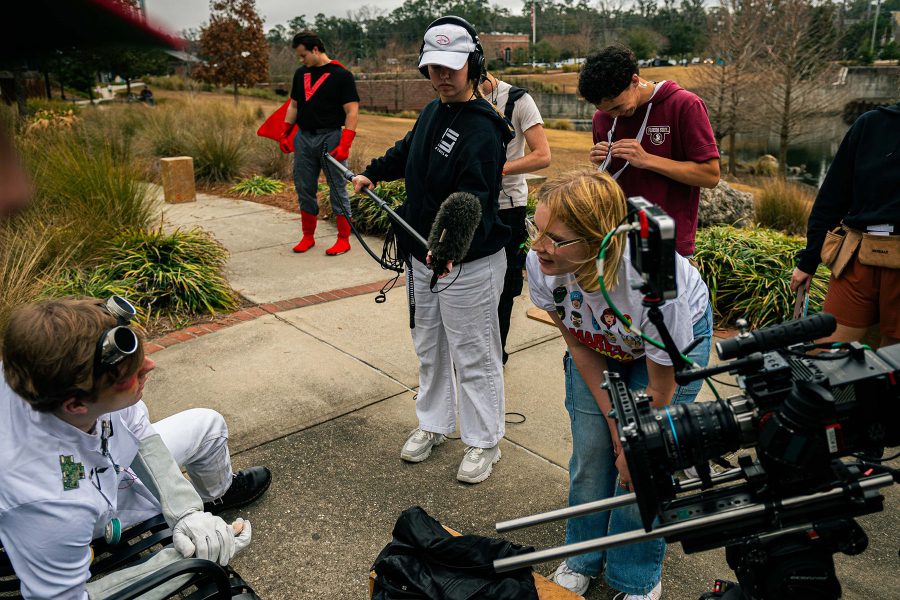
“`html Florida State University’s College of Motion Picture Arts (FSUFilm) maintains its reputation as the fourth-ranked public film school in the country while advancing to No. 14 in The Hollywood Reporter’s 2025 rankings of premier U.S. film schools, up from No. 17. Two significant factors contributed to this advancement: the purchase of a 43,242-square-foot venue…
-
Back-to-School Insights: FSU Experts Ready to Share Their Knowledge

“`html From the beginning of August until shortly after Labor Day, youngsters throughout the United States are heading back to school, aspiring for a rewarding 2025-26 educational year. The K–12 educational framework provides a route for student progression, yet notable obstacles remain. Florida State University has specialists in various educational fields, including student psychological well-being,…
-
Revolutionary Imaging Technology Set to Enhance Hearing Loss Diagnosis and Treatment

USC researchers have modified an economical imaging technique originally created for ophthalmology to observe minute structures within the human inner ear.
-
MIT LGO Alumni: The Driving Force Behind Amazon’s Global Operations

“`html If you’ve placed an urgent order for a package from Amazon — and sighed with relief when it showed up on your doorstep mere hours later — you probably owe thanks to three alumni of the MIT Leaders for Global Operations (LGO) program: John Tagawa SM ’99; Diego Méndez de la Luz MNG ’04,…
-
Empowering Futures: How an Online Job Interview Simulator is Helping Former Inmates Re-enter the Workforce

“`html Research: A practical randomized controlled trial of virtual reality job interview training in prison employment services (DOI: 10.1007/s11292-025-09684-7) In a job-search arena where every advantage matters, many individuals seek methods to differentiate themselves—but what about those reentering society after incarceration? A recent study from the University of Michigan revealed that virtual job interview training…
-
Underestimating Black Carbon Emissions in the Global South
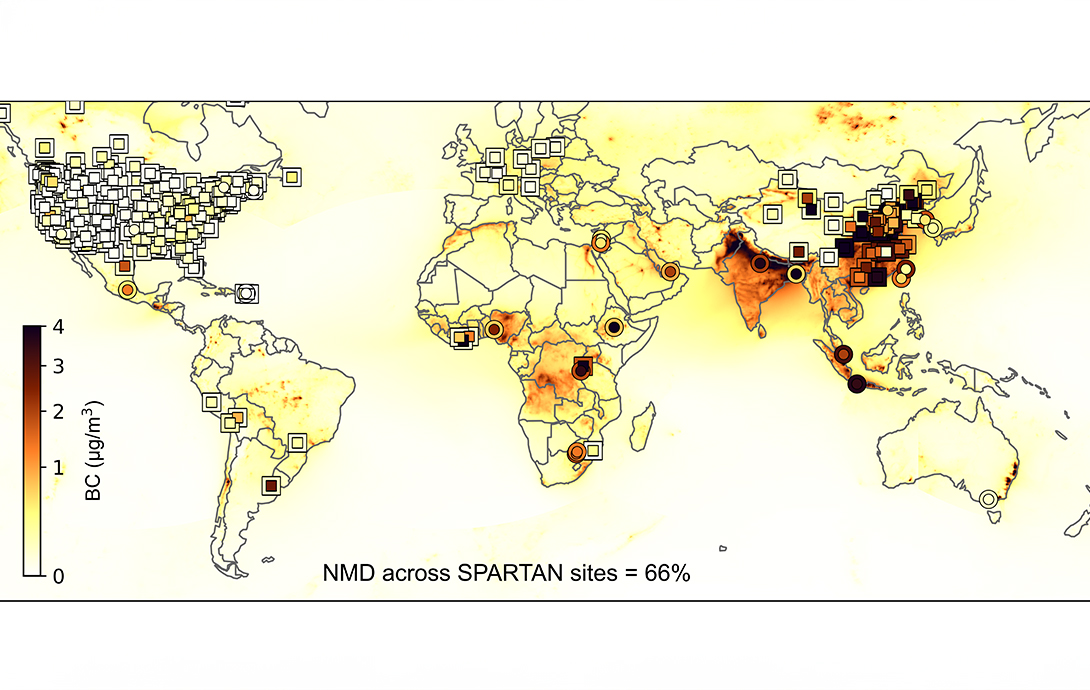
Black carbon, the dark residue resulting from incomplete burning of fossil fuels, has become a significant factor in climate change and adverse effects on human health. Scholars at the McKelvey School of Engineering at Washington University in St. Louis have utilized various models to tackle the complex issue of gauging ambient levels of black carbon…
-
Exploring the Impact of Non-Antibiotic Medications on Our Microbiome
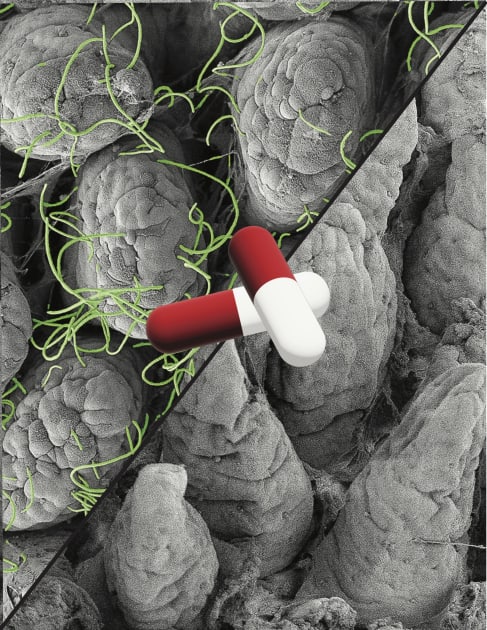
Scientists discover numerous non-antibiotic medications that interfere with the microbiome—occasionally in unexpected manners.
-
A Pioneer in Liturgical Studies Shares Insights on a Journey of Faith and Learning

Teresa Berger, a Professor of Liturgical Studies and the Thomas E. Golden Jr. Professor of Catholic Theology at Yale Divinity School and the Institute of Sacred Music, shares insights about her career and her enthusiasm for her forthcoming book project.