-
Teens Behind August 2024 TfL Cyber Attack Apprehended by U.K. Authorities

“`html Law enforcement agencies in the U.K. have apprehended two adolescent associates of the Scattered Spider hacking collective regarding their purported involvement in an August 2024 cyber assault aimed at Transport for London (TfL), the city’s transit authority. Thalha Jubair (also known as EarthtoStar, Brad, Austin, and @autistic), 19, hailing from East London, and Owen…
-
Mastering Gradient Boosting in Python Using Scikit-Learn: A Comprehensive Guide

“`html It requires more than merely generating forecasts and fitting models for machine learning algorithms to enhance their precision. Most effective models in the industry or competitions have utilized feature transformation and ensemble methods to boost their efficacy. In comparison to feature transformation, these techniques are easier to implement, which …Read More. “`
-
Mastering Socket Programming in Java: A Comprehensive Guide

“`html In this piece, we will explore socket programming in Java. Most computer science graduates possess knowledge of the principles of computer networking and its uses. One of the branches within computer networking is socket programming. Socket programming serves as a method for establishing a connection between two distinct nodes in a network whe…Read More.…
-
Demystifying Operator Overloading in C++: A Comprehensive Guide

In this piece, we will explore an essential characteristic of object-oriented programming principles called operator overloading. The C++ programming language permits the developer to possess multiple execution behaviors for a function or an operator within the same context. In OOPS, overloading indicates having an identical name but with…Read More.
-
Essential SharePoint Interview Questions and Answers for 2025

“`html Nowadays, businesses across all industries are transitioning towards paperless environments. The conventional laborious task of data recording has been surpassed by recent technological innovations. Currently, all details are accessible on the desktop in the format of a pdf document. SharePoint is one such product from Microsoft. It serves as a system for document management…
-
Understanding Angular Directives: A Comprehensive Guide

This article examines a significant Angular concept known as – Directives, their applications, and the process of creating them. What Are Directives in Angular? Angular stands as the fourth (22.29%) most utilized web framework for front-end development leveraging HTML and TypeScript programming languages. Established by Google in 2009, Angular is primarily employed for single-page applications…
-
Mastering Hexaware Interviews: Essential Questions and Answers

“`html In this article, we will explore several of the leading Hexaware Interview Questions and Responses. First, let’s discover a little information about Hexaware Technologies. About Hexaware Hexaware Technologies is among the pioneers in IT Service Management globally, with nearly half of its staff operating in a digital environment. In recent times, there has been…
-
Mastering Java Networking: Your Comprehensive Guide

“`html Network development is the act of creating applications that operate on several devices (computers) that are interconnected through a network. To facilitate low-level communication specifics, Java incorporates classes and interfaces. This article presents a summary of the basics of Java Networking. What is Java Networking? Java networking is t…Read More. “`
-
Essential BGP Interview Questions and Answers You Need to Know

“`html BGP – Border Gateway Protocol serves as the mailing system of the Internet. The mailing system handles a letter when it is dropped in the mailbox and ensures that it is delivered to its designated location in the most effective way. BGP is responsible for evaluating all potential routes to a data set transmitted…
-
Unlocking Your Dream Job: The Power of Off-Campus Placement

“`html In this competitive environment, securing your ideal profession is vital. Essentially, there are two distinct methods through which learners procure their target job. These are either via on-campus placements or off-campus placements. Off-campus placements offer a pathway for recent graduates to attain their ideal positions. In off-campus placement, the student will receive a …Read…
-
Envisioning the Horizon: The Future of Generative AI

“`html When OpenAI unveiled ChatGPT to the globe in 2022, it propelled generative artificial intelligence into the spotlight and initiated a chain reaction that resulted in its swift incorporation into industries, scientific exploration, healthcare, and the daily routines of individuals utilizing the technology. What lies ahead for this robust yet flawed tool? With this query…
-
CISA Alerts on Malware Threats Targeting Ivanti EPMM Vulnerabilities CVE-2025-4427 and CVE-2025-4428

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday unveiled information regarding two groups of malware that were identified within an unnamed entity’s network after security vulnerabilities in Ivanti Endpoint Manager Mobile (EPMM) were exploited. “Every group includes loaders for nefarious listeners that permit cyber threat actors to execute arbitrary code on the breached…
-
Yale Film Archive Secures Grant to Safeguard Innovative Films by Jacqueline Leger

National Film Preservation Foundation funding to assist in safeguarding two early motion pictures by Leger, MFA 1976: “Sunday Morning” and “Jocko’s New Haven.”
-
Engaging Conversations: Barry Wu Explores Essential Questions for the Elderly on Health & Veritas Podcast

Howie and Harlan are accompanied by Barry Wu, a geriatric specialist from the Yale School of Medicine, who offers a structure for family caregivers and doctors to comprehend the requirements of elderly individuals.
-
Guardians of the Liver: How GLP-1 Receptor Agonists Combat Alcohol’s Effects
New discoveries indicate that anti-obesity medications like semaglutide could possess direct safeguarding benefits for the liver as well.
-
Eugene Jarvis: The Berkeley Trailblazer Who Transformed Arcade Gaming

The article How Berkeley Alumni Eugene Jarvis Transformed Arcade Gaming was initially published on Berkeley News.
-
Harnessing Innovation: Five Strategies for California to Address Surging AI Energy Needs

At a recent Stanford discussion, specialists delineated tactical methods to avert a technology retreat while enhancing the electricity network in a sustainable and cost-effective manner.
-
USC’s Solar Revolution: A Milestone in Sustainability for Green Week

“`html Zelinda Welch, USC’s director of energy and sustainability, alongside Campbell Odening, senior project manager for capital construction development, assess the recently placed solar panels atop the Carole Little Building. (USC Photo/Stephen Gee) Disseminate Environment Green Week: USC’s largest solar project approaches finale As USC commences its fifth annual Green Week, the deployment of 1,042…
-
Protect Your Health: Flu Shots Now Offered for Staff

“`html Obtaining the influenza vaccine is a crucial public health initiative to safeguard yourself and the community against the illness. The influenza vaccine may be necessary depending on your workplace or role at WashU. Check flu.washu.edu to determine if you’re mandated to get the vaccine and to access additional details. Scheduled appointments and walk-in clinics…
-
The Emergence of Mid-Decade Redistricting: A New Standard in Political Boundaries

“`html The Missouri Legislature has approved a scheme to redraw the state’s congressional districts, potentially conceding a Democrat-leaning seat to Republicans and granting the GOP a 7-1 district edge. Experts on electoral rights at Washington University in St. Louis assert that partisan mid-decade redistricting, once quite uncommon, might become the standard. Travis Crum, a law…
-
Introducing the New Tenured Professors of the School of Humanities, Arts, and Social Sciences for 2025

“`html In 2025, six educators were awarded tenure in the MIT School of Humanities, Arts, and Social Sciences. Sara Brown serves as an associate professor in the Music and Theater Arts Section. She creates set designs for theater, opera, and dance by viewing the scenographic space as a catalyst for collective creativity. Her endeavors are…
-
“Inflammation Awakens Dormant Cancer Cells, Sparking a Return to Growth”
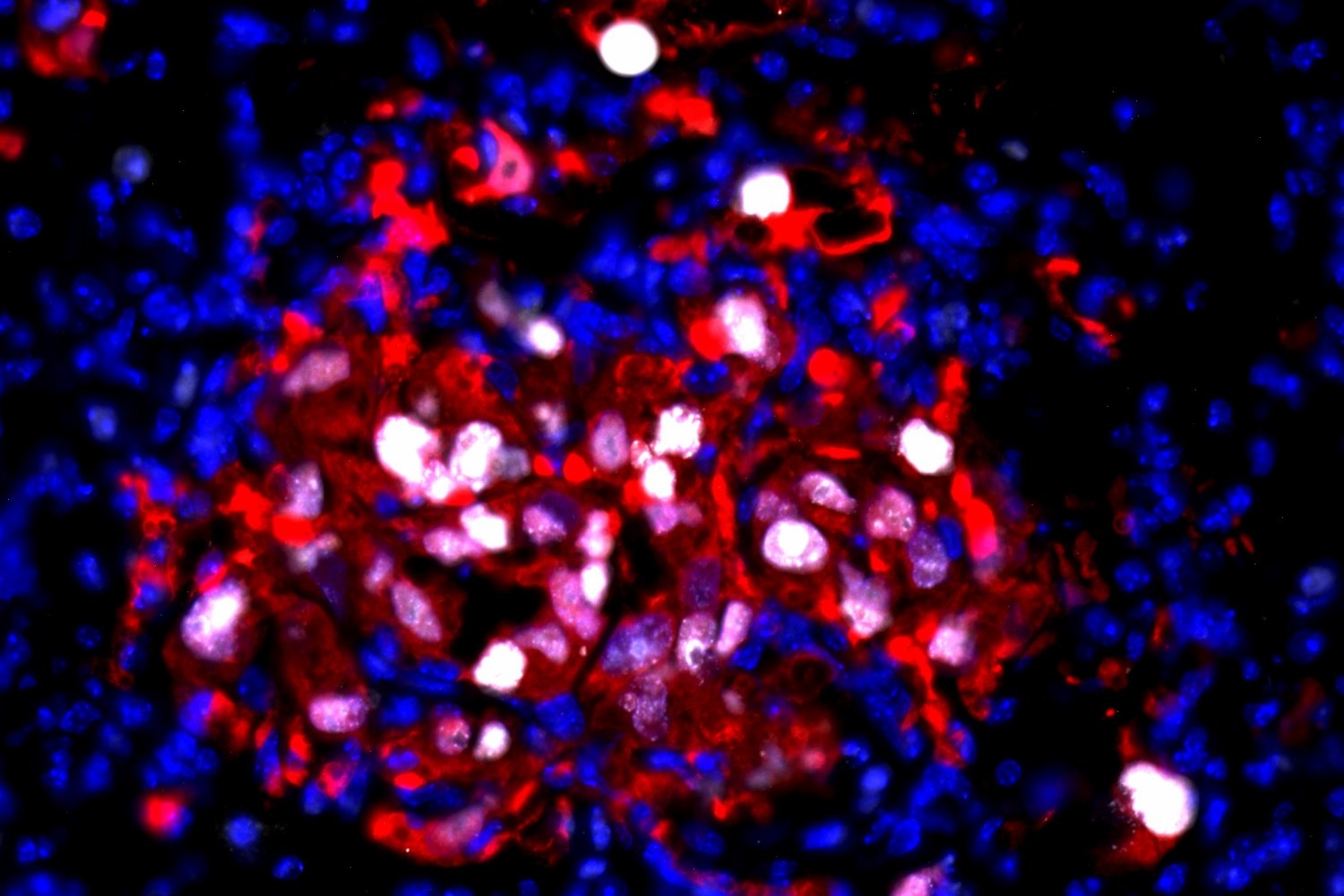
“`html Cancer cells possess a singular, insatiable aim: to proliferate and replicate. While the majority remain clustered within the primary tumor, some rebellious cells detach to journey to far-off organs. In those locations, they can remain inactive — unseen and not multiplying — for extended periods, resembling hidden explosives poised to detonate. This movement of…
-
“How ‘Creeping Fat’ Complicates Crohn’s Disease”

An investigation conducted by Stanford Medicine uncovers that a rare kind of fat that develops close to the intestines in Crohn’s disease may induce debilitating scars.
-
Pioneering a New Frontier: Law Students Unveil the First-Ever Student-Operated Space Law Journal

A novel publication investigates the legal framework of outer space. “On the West Coast, particularly in Silicon Valley, space developments are occurring all around us…Stanford is distinctly situated to incorporate law into that dialogue.”
-
The Myth of Pure Bloodlines: What DNA Science Reveals About Our Ancestry

“`html Images by Niles Singer/Harvard Staff Photographer Science & Technology Contentions of pure lineages? Ancestral territories? DNA research asserts otherwise. Geneticist elucidates how advancements in technology reveal a narrative of mixing, movement, and displacement in human history. Alvin Powell Harvard Staff Writer September 18, 2025 7 min read The history of humanity is filled with…
-
Ancient DNA Research: Unveiling the Secrets of Our Past

“`html Science & Tech His lab’s prehistoric DNA research is altering human history Image courtesy of Stephanie Mitchell/Harvard Staff Photographer Liz Mineo Harvard Staff Writer September 18, 2025 3 min read Yet federal funding reductions have cast doubt on the next phase of David Reich’s work Since 2012, geneticist David Reich and his team of…
-
FSU Achieves Record-Breaking Top 4 Retention and Top 9 Graduation Rates

“`html Florida State University has set new benchmarks in graduation and retention figures, reinforcing its position as a significant national frontrunner in student academic achievement. This year, FSU recorded an unprecedented 78% four-year graduation rate, rising from last year’s 76%, placing it among the Top 9 public schools across the country. The six-year graduation rate…
-
Tucson: A Hidden Gem on the Global Stage
“`html Regional perspective: When Tucson takes center stage nprevenas Thu, 09/18/2025 – 10:42 Regional perspective: When Tucson takes center stage Current Day Article Categories Arts & Humanities Breaking News By Arizona Daily Star Type of News Article Outside News “`
-
MSU’s Top-Ranked Undergraduate Programs Shine Nationally

Michigan State University boasts six bachelor’s programs positioned within the top 25 nationwide, which is an enhancement of two programs compared to last year’s standings.
-
How AI is Transforming Learning for Students, for Better or Worse

“`html University scholars are increasingly utilizing artificial intelligence resources such as ChatGPT for immediate explanations. (Photo/iStock) Distribute Science/Technology The role of AI in transforming student learning — or bypassing it A USC investigation indicates that the majority of scholars utilize resources like ChatGPT to expedite tasks unless educators purposefully direct them towards deeper and more…
-
Revealing the Top Three Deadliest Risk Factors of a Widespread Liver Disease

Patients suffering from a persistent liver condition referred to as MASLD, who exhibit elevated blood pressure, pre-diabetes/diabetes, or reduced HDL cholesterol, are at the highest risk, according to researchers from USC.
-
Harnessing Community Insights to Combat False Information on X: A Study’s Findings

“`html A study conducted by the University of Washington regarding X indicated that entries with Community Notes included were less likely to achieve virality and received reduced engagement. Following the addition of a Community Note, on average, reposts decreased by 46% and likes declined by 44%.iStock In 2022, subsequent to Elon Musk’s acquisition of what…
-
“North Campus Welcomes Its First Two Maize Rays Solar Arrays!”

“`html Two new solar installations at U-M’s North Campus Facilities Services Building include both a rooftop array and a solar carport. The panels are part of the Maize Rays initiative, a multiyear plan to expand on-campus solar capacity, enhance energy resilience, and reduce the university’s carbon footprint. Image credit: Eric Bronson, Michigan Photography Two fresh…
-
Unraveling the Hidden Effects of Childhood Lead Exposure: Insights from a New Study

“`html Exposure to lead during childhood could be considerably more harmful for cognitive growth and academic performance than earlier believed, based on a recent assessment led by data analyst Joe Feldman. Childhood lead exposure typically stems from crumbling lead-containing paint, tainted soil, or aged water pipes — dangers that persist in numerous U.S. neighborhoods. Elevated…
-
Elevating Connections: Top of the Hop Transforms into a Dynamic Social Haven

The well-liked location on campus serves as a venue to review, relax, and socialize with peers.
-
The Intricate Dance of Constitutional Dialogue: Unpacking American Equality

In a recent publication, Yale constitutional expert Akhil Reed Amar explores the era spanning from 1840 to 1920 and four remarkable figures who contributed to America’s comprehension of equality.
-
From Crime Scenes to Campuses: A Veteran Forensic Pathologist Joins Yale

In a Q&A, Susan Ely, who has recently assumed the role of director of the autopsy service at Yale School of Medicine, talks about her journey as a forensic pathologist, the “CSI Effect,” and her perspective on why she identifies as an “ambassador” for the discipline.
-
Exploring the World of Claudia Cea

In a Q&A, Yale engineer Claudia Cea discusses her investigation into how the brain engages with other organs, the reason we experience butterflies in our stomachs when we’re in love, and how a fictitious physician motivated her efforts.
-
Unlocking Resilience: Genetic Insights into the Lives of Kenya’s Nomadic Herders in Desert Environments
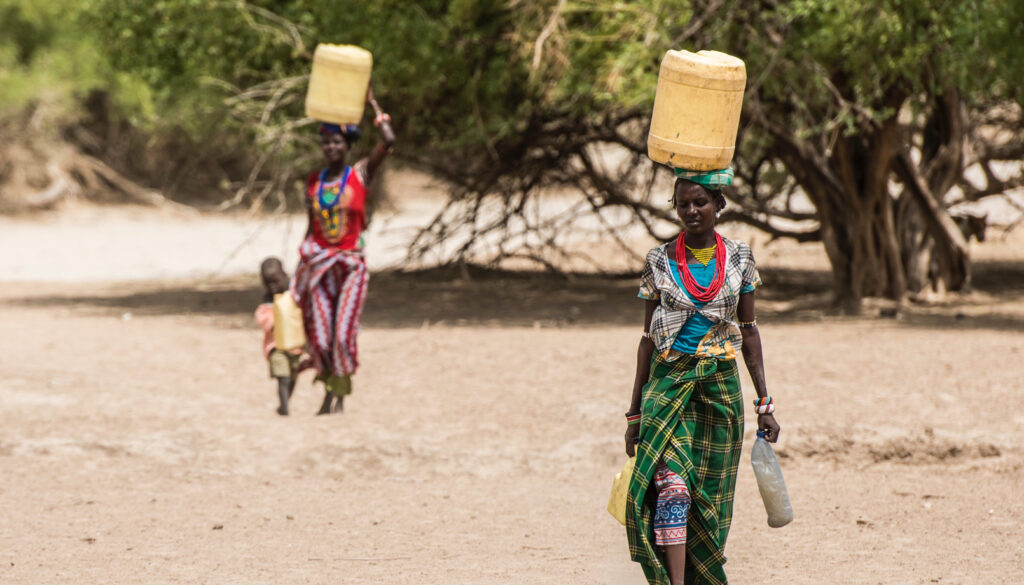
The Turkana community follows a meat-centric diet in one of the most scorching, aridest regions on the planet. Researchers unveiled the genetic diversity that enables this desert acclimatization, and the challenges it presents as the Turkana shift to urban existence. The article Genetic study of nomadic herders in Kenya shows what it takes to adapt…
-
“Unpacking the Flaws of Healthcare: Insights from a Leading Professor”

Health inequalities result in women — especially women of color, immigrants, and other historically oppressed groups — experiencing reduced lifespans compared to their white male peers. The article Health care isn’t effective for everyone. Observe a professor discuss the reasons. was initially featured on Berkeley News.
-
“Biogen’s Bold Move Sparks Excitement in Kendall Square”

“`html Almost 300 individuals convened Tuesday to commemorate the ceremonial commencement for Biogen’s new cutting-edge facility in Kendall Square. This initiative marks the first structure to be erected at MIT’s Kendall Common on the former Volpe federal site and will function as a unified headquarters for the groundbreaking biotechnology firm that has regarded Cambridge as its…
-
Exploring the Essence of ‘We the People’ with Jill Lepore
“`html Nation & World ‘We have the power to rectify. We can transform our conduct.’ Jill Lepore elucidates a document designed for modification in a fresh history of the Constitution Christy DeSmith Harvard Staff Writer September 18, 2025 8 min read A notice from Jill Lepore to her nation: The Constitution was intended for amendments.…
-
Empowering Students: The Triumph of CliftonStrengths at UT and Gallup

“`html Strengths Day showcased executive officials, distinguished alumni, and faculty members from various colleges discussing and honoring the institution’s incorporation of strengths-centered initiatives throughout the campus to assist students in utilizing their inherent abilities for achievement. The article UT, Gallup Celebrate Success of CliftonStrengths in Helping Students Thrive was originally published on News. “`
-
FSU Achieves Record-Breaking Retention and Graduation Rates, Securing a Spot Among the Nation’s Elite

“`html Unprecedented completion rate for transfer student demographic Florida State University has surpassed its previous milestones in graduation and retention metrics, reaffirming its status as a formidable national leader in student scholastic achievement. This year, FSU recorded an unprecedented 78% graduation rate within four years, an increase from last year’s 76%, placing it among the…
-
Revolutionizing Learning: FAMU-FSU Researcher Harnesses AI-Driven Robotic Unicycle to Uncover Motor Skill Acquisition
“`html Scientists are crafting advanced robotic systems that modify themselves to fit unique learning styles, potentially revolutionizing rehabilitation results for individuals with mobility challenges. FAMU-FSU College of Engineering Assistant Professor Taylor Higgins poses with her unicycle. Higgins received a National Science Foundation Mind, Machine, and Motor Nexus (M3X) grant to further understanding of human motor…
-
“Exploring Creativity: FSU’s Art in STEM Exhibition Now Open”

“`html The yearly Art in STEM exhibition at Florida State University, now situated in Dirac Science Library and online, marks its 11th iteration highlighting the exceptional research and artistic abilities of FSU students and postdoctoral scholars in the realms of science, technology, engineering, and mathematics. This year’s installment of the annual exhibition, a joint effort…
-
Florida State University Unveils Exciting New Collaboration Hub in West Palm Beach

“`html IMAGE GALLERY The article Florida State University commemorates the grand inauguration of a fresh collaborative area in West Palm Beach was originally published on Florida State University News. “`
-
FSU Unveils Innovative Collaboration Hub in West Palm Beach

“`html The article Images: FSU commemorates the official launch of a new collaborative area in West Palm Beach was initially published on Florida State University News. “`
-
The Surprising Connection Between Your Gut and Your Mood

“`html Can your gut flora influence your emotions? nprevenas Thu, 09/18/2025 – 09:17 Can your gut flora influence your emotions? Wednesday Article Categories Health & Wellness Current News By Scientific American News Article Class Outside News “`
-
“An Astounding Discovery in an Asteroid Expedition”

“`html An expedition to a remote asteroid has just encountered an unforeseen twist nprevenas Thu, 09/18/2025 – 09:07 An expedition to a remote asteroid has just encountered an unforeseen twist Today Article Categories Current Events Science & Tech Cosmic Exploration By Mashable Type of News Article Outside News “`
-
MSU Immigration Law Clinic Marks 15 Years of Impactful Service

In 15 years of functioning, MSU’s Immigration Law Clinic has advocated for clients worldwide.
-
University of Washington Launches Exciting Renovation of ASUW Shell House

“`html President of the University of Washington Robert J. Jones, writer Daniel James Brown, along with various members of the ASUW Shell House community, convened for a ceremonial groundbreaking at the historic edifice, which is in the final phases of adaptive reuse. Covering roughly 12,000 square feet, the venerable ASUW Shell House rests just steps…
-
Ancient Fossil Unravels Secrets of Fish Evolution from 310 Million Years Ago

Here’s the modified text with synonyms and altered sentence structure while keeping the HTML tags and format intact: “`html Reconstruction of life of Platysomus, displaying an open mouth revealing a toothplate on the bottom of the mouth upheld by gill bones. Image credit: Joschua Knüppe Research: Tongue biting apparatus emphasizes functional novelty in a 310-million-year-old…
-
Record-Breaking Attendance at the KBH Energy Center Symposium with Key Industry Figures

The article KBH Energy Center Symposium Attracts Unprecedented Attendance, Showcases Industry Experts was initially published on UT Austin News – The University of Texas at Austin.
-
UT Achieves Record Enrollment and Student Success Milestones

AUSTIN, Texas — The University of Texas at Austin established seven new records for crucial enrollment metrics in the 2025-2026 academic term, indicative of increasing student interest and performance. The University’s overall enrollment and new freshman class represent the most significant figures in its 142-year existence, while graduation rates, retention rates, conferred degrees, and applications…
-
Innovative Showcase: Sam Fox School Faculty Takes Center Stage at 2025 Exhibit Columbus

“`html “Inside Out,” a display by Sam Fox School of Design & Visual Arts instructors Chandler Ahrens, Constance Vale, and Kelley Van Dyck Murphy, is showcased in the 2025 Exhibit Columbus “Yes And” exhibition in Indiana. An installation perspective of “Inside Out” at “Exhibit Columbus.” (Photo: Hadley Fruits for Landmark Columbus Foundation) The trio, who…
-
Innovative Approach to Boost Brown Fat: A New Frontier in Caloric Burn and Obesity Control in Mice
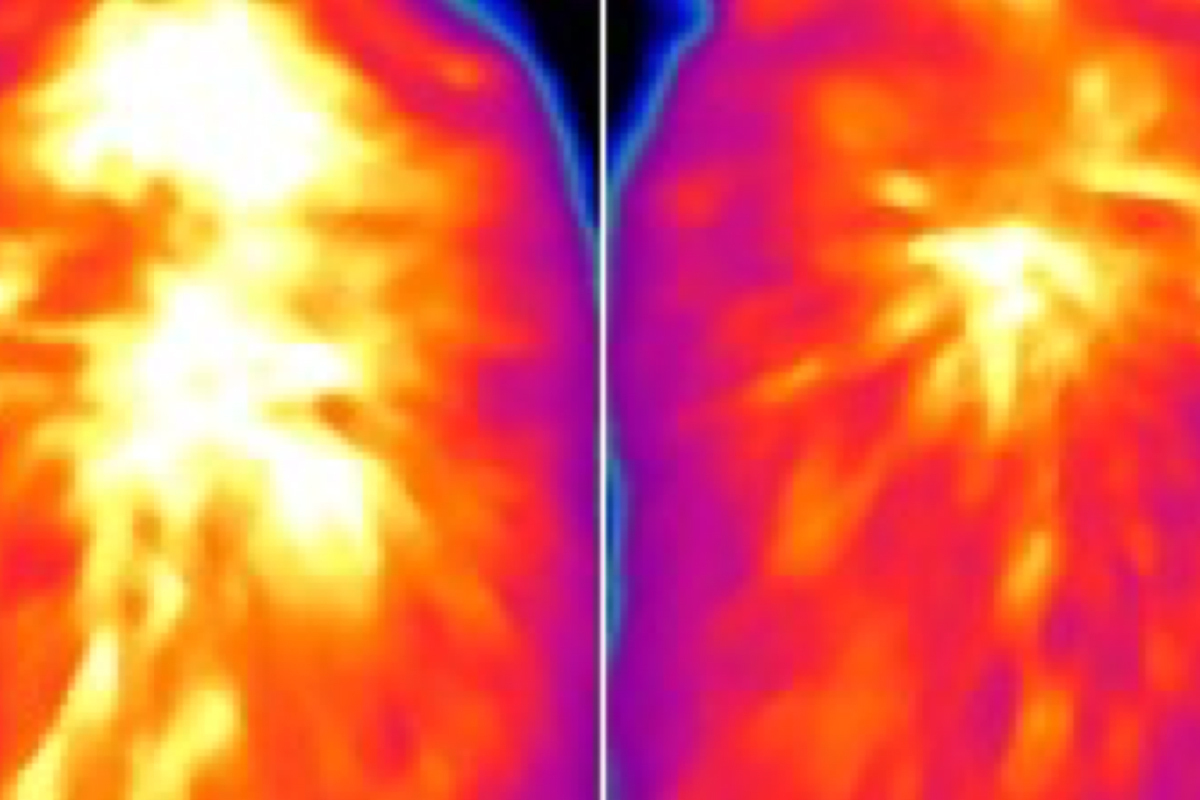
“`html Investigators at Washington University School of Medicine in St. Louis have discovered a groundbreaking method in which brown adipose tissue — a calorie-burning type of fat — can accelerate the body’s metabolic machinery, utilizing cellular energy and generating heat in ways that enhance metabolic wellness. The research, conducted on mice, uncovers new strategies to…
-
Quantum World Congress Celebrates John Preskill’s Pioneering Contributions

“`html The Quantum World Congress (QWC) revealed on September 18 that it was granting John Preskill, the Richard P. Feynman Professor of Theoretical Physics, its Academic Pioneer in Quantum Award for 2025. Preskill obtained a BA from Princeton and a PhD from Harvard in physics, joining the Caltech faculty in 1983. He commenced his career…
-
Thaker Appointed as Head of Gynecologic Oncology Division

“`html Thaker Premal H. Thaker, MD, the David & Lynn Mutch Distinguished Professor of Obstetrics and Gynecology, has been appointed director of the Division of Gynecologic Oncology within the Department of Obstetrics & Gynecology at Washington University School of Medicine in St. Louis. Her new responsibilities commenced on June 1. In her role as director,…
-
Dartmouth Introduces Exciting New Korean Language Course

The inclusion enhances a strong Korean studies program and academic funding.
-
SonicWall Advises Customers to Reset Passwords Following Security Breach in Cloud Backup System

“`html SonicWall is encouraging clients to change their credentials following the exposure of their firewall configuration backup files during a security incident affecting MySonicWall accounts. The organization announced that it has recently identified dubious activity aimed at the cloud backup service for firewalls, noting that unidentified malicious actors gained access to backup firewall configuration files…
-
Milestone Achieved: School of Medicine Receives Preliminary Accreditation from LCME

“`html From Sept. 16–17, the Liaison Committee on Medical Education (LCME) finalized its initial accreditation site assessment for the University of Georgia School of Medicine. This evaluation is a critical and essential procedure for the institution to achieve formal accreditation. A group of evaluators from the LCME dedicated two days on location, undertaking a comprehensive…
-
Unlocking Korean Cultural Richness: Insights from FSU Expert After the Triumph of “KPop Demon Hunters”

“`html By Olivia Sanchez Netflix’s “KPop Demon Hunters” has heightened appreciation of Korean culture by highlighting its folklore, customs, and artistry. Achieving a Netflix-record 266 million views worldwide, “KPop Demon Hunters” narrates the tale of a famous K-pop girl group that possesses the power to combat demons through singing and dancing. Films, series, and music…
-
Pedaling Progress: FAMU-FSU Researchers Innovate Walking Rehabilitation with Unicycles

The article FAMU-FSU Experts Utilize Unicycles to Investigate How Individuals Re-Establish Their Walking Skills was first published on Florida State University News.
-
Bridging the Gap: Leveraging Technology to Combat Bias Against Remote Workers

“`html Research (PDF): Virtually Even: Status Equalizing in Distributed Organizations For many years, remote employees were frequently perceived as less dedicated and less powerful than their in-office counterparts. However, recent findings indicate that the workplace hierarchy is transforming—and that distributed teams may experience greater equality than previously. A research article published in Organization Science by…
-
CountLoader Expands Its Reach: Unveiling a Multi-Version Malware Loader for Russian Ransomware Activities

“`html Cybersecurity analysts have unearthed a novel malware loader referred to as CountLoader, which has been employed by Russian ransomware groups to convey post-exploitation utilities such as Cobalt Strike and AdaptixC2, along with a remote access trojan identified as PureHVNC RAT. “CountLoader is utilized either as a component of an Initial Access Broker’s (IAB) toolkit…
-
Stealthy Threat: SilentSync RAT Emerges from Two Deceptive PyPI Packages Aiming at Python Developers

“`html Cybersecurity analysts have identified two additional harmful packages in the Python Package Index (PyPI) repository, intended to deploy a remote access trojan named SilentSync on Windows platforms. “SilentSync is proficient in remote command execution, file extraction, and screen recording,” Zscaler ThreatLabz’s Manisha Ramcharan Prajapati and Satyam Singh noted. “SilentSync also retrieves “`
-
Leading the Charge: CISOs and the Future of AI Governance

“`html The escalating significance of AI within corporate settings has increased the necessity for Chief Information Security Officers (CISOs) to implement efficient AI governance. Regarding any new technology, overseeing it is challenging – however, proficient governance is considerably more complex. The initial reaction for many organizations is to react with inflexible regulations. Draft a policy…
-
Chronicles of Time: Unraveling Time-of-Check, Time-of-Use Attacks on LLMs

“`html This is an excellent piece of investigation: “Mind the Gap: Time-of-Check to Time-of-Use Vulnerabilities in LLM-Enabled Agents“.: Abstract: Agents powered by Large Language Models (LLM) are swiftly developing across a diverse array of applications, yet their implementation presents vulnerabilities with security ramifications. While earlier research has focused on prompt-based assaults (e.g., prompt injection) and…
-
Mastering SAP SD: 50 Essential Interview Questions and Answers

“`html The rise in the necessity for logistics administration within enterprises has prompted SAP to create various modules that concentrate on sales and distribution. Numerous large corporations are in search of specialists who can assist them in effectively overseeing their supply chain. Revising the following SAP SD interview questions will aid in succeeding at an…
-
Unlocking the Magic of Narrow AI: The Hidden Force Powering Your Beloved Apps

Artificial Intelligence represents one of humanity’s most remarkable and advantageous creations. While it enhances human life, it remains incapable of matching human competition. Narrow AI exemplifies this limitation, as it is designed to execute specific tasks based on pre-acquired knowledge. Through a focused and targeted method, it effectively aids…Read More.
-
Unlocking the Role of a Performance Marketing Manager: Key Skills and Salary Insights

“`html The expansion and need for Performance Marketing Managers in 2024 are escalating, propelled by the growing dependence on data-oriented tactics to optimize ROI. Enterprises across multiple industries are acknowledging the significance of performance marketing in attaining specific, quantifiable outcomes. With progress in ai ml courses, marketers can now utilize advanced…Read More. “`
-
Mastering Java Annotations: A Comprehensive Guide with Real-World Examples

“`html Annotations in Java offer supplementary details to the compiler and JVM. An annotation serves as a label denoting metadata regarding classes, interfaces, variables, methods, or fields. Annotations do not influence the execution of the code they annotate. Several features of annotations include: Start with ‘@’ Do not affect the execution of th…Read More. “`
-
Understanding the Distinctions Between StringBuffer and StringBuilder

“`html Much like the StringBuffer, the StringBuilder retains the entity in a heap and permits alterations. The primary difference between StringBuffer and StringBuilder is that ThreadSafe is absent in StringBuilder. Given that StringBuilder lacks thread-safety, it operates at a faster pace. Strings are also unchangeable as arrays are unalterable (cannot grow). A comprehensive…Learn More. “`
-
Essential LINQ Interview Questions and Answers for 2025

“`html The initial step towards obtaining employment is to prepare for the interview. Conducting some investigation enhances your confidence, serenity, and readiness. Here we showcase several of the most frequently posed LINQ interview questions and responses that will assist you in successfully navigating the technical interview with ease. LINQ signifies Language Integrated Query. LINQ facilitates…
-
Mastering SQL String Functions: A Comprehensive Guide

If you are curious about how to handle string functions in SQL, you have arrived at the perfect spot. String functions are operations within SQL that accept string inputs. The result might be a string or not. SQL provides numerous built-in string functions that you can utilize to process string input values. ASCII(str) Syntax- ASCII…
-
Mastering LinkedIn Interview Questions: Your Ultimate Guide to Success

“`html LinkedIn is recognized as an organization with an exceptional workplace environment and robust employee-centric policies. Its status as one of the finest companies to work for is evident in its outstanding reviews and ratings on Indeed and Glassdoor. If you aspire to secure your ideal position at LinkedIn, you must navigate an interview procedure…
-
Behind the Curtain: Our True Perspectives on the Ultra-Wealthy

Is excessive affluence a moral shortcoming or a symbol of prestige? An international research initiative co-directed by USC Dornsife specialists uncovers what truly influences our perceptions of the exceedingly wealthy.
-
Google Addresses Chrome Zero-Day CVE-2025-10585 as V8 Exploit Poses Risk to Millions

“`html Google on Wednesday unveiled security enhancements for the Chrome web browser to tackle four weaknesses, including one that it indicated has been utilized in real-world attacks. The zero-day flaw being referenced is CVE-2025-10585, characterized as a type confusion problem within the V8 JavaScript and WebAssembly engine. Type confusion flaws can lead to serious repercussions…
-
“Unlocking Cosmic Mysteries: Could a Primordial Black Hole’s Final Burst Illuminate the Source of an Energetic Neutrino?”

The final breath of an ancient black hole might be the origin of the most energetic “phantom particle” discovered thus far, a recent MIT investigation suggests. In a study published today in Physical Review Letters, MIT scientists present a compelling theoretical argument indicating that a newly detected, highly energetic neutrino could have originated from an…
-
“President Levin Inspires New Students to Foster a Culture of Dignity at Convocation”

Stanford’s 135th yearly Convocation event greeted 1,870 new freshmen and 90 transfer students to the university community.
-
Unveiling the Mysteries of Uploads in a Dshield Honeypot: A Guest Perspective
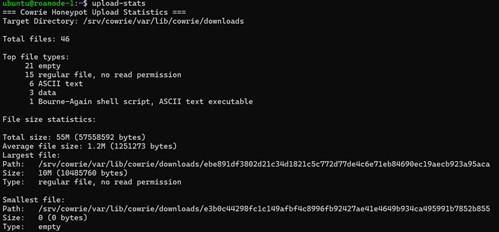
[This is a Visitor Journal by Nathan Smisson, an ISC apprentice as a component of the SANS.edu BACS initiative]
-
Guardians of Our Food Future: Experts Tackle the Biodiversity Emergency

“`html Merely nine plant species currently account for 65% of the global food supply. As genetic variety declines and ecosystems struggle, agrifood systems become progressively vulnerable, endangering food security and human well-being. Specialists caution that this extraordinary deficit in biodiversity — at genetic, species, and ecosystem tiers — carries extensive implications for how the planet…
-
Touchdown Fundamentals: Graduate Students Discover the Passion of American Football

During the New Graduate Student Orientation, past and present Cardinal football athletes educated new students on the intricacies of the U.S. sport.
-
Inaugural Address by President Jonathan Levin at the Opening Convocation

During the Convocation, Levin conveyed to the students, “Higher education is significantly more about posing inquiries than possessing all the solutions.”
-
“Exploring Indigenous Connections to Water: A Captivating Exhibition at FSU MoFA”

“`html A fresh exhibition at the Florida State University Museum of Fine Arts emphasizes the influence of water on cultural landscapes and artistic endeavors, showcasing artists from Florida as well as globally. “Water Ways: Indigenous Ecologies and Florida Heritage” is organized in partnership with the FSU Native American and Indigenous Studies Center (NAIS), the Department…
-
Spartan Scientists Ignite Hope in the Battle Against Brain Cancer

After Emily Burns’ abrupt glioblastoma diagnosis, her son reached out to Michigan State University scientists working on an innovative therapy—now jeopardized by NIH budget reductions.
-
Celebrating Culture: Exciting Hispanic Heritage Month Activities at MSU

Discover the National Hispanic Heritage Month activities occurring throughout Michigan State’s campus from now until October 15!
-
Revitalizing History: UW Unveils Plans for ASUW Shell House Transformation
“`html University of Washington President Robert J. Jones, novelist Daniel James Brown, and various associates from the ASUW Shell House community convened for a groundbreaking event at the historic structure, which is presently in the concluding phases of adaptive repurposing. Covering nearly 12,000 square feet, the historic ASUW Shell House is situated mere feet from…
-
“Embrace the Journey: UW Opened Its Doors to New Students in On-Campus Housing”
“`html This week, the University of Washington campus is once again alive with vibrancy as students start relocating to the residence halls and engage in traditional autumn events for new undergraduates. Most of the UW freshman cohort has enrolled to reside on campus for Fall 2025, with thousands anticipated to move into campus accommodations…