-
Top AI Certifications to Boost Your Tech Expertise by 2025!

As artificial intelligence transforms sectors, remaining informed about the latest AI capabilities is essential. The year 2025 presents numerous AI certification options aimed at advancing your career to new levels. The appropriate certification can greatly enhance your employability and expertise in this ever-evolving domain, whether you are just beginning or …Read More.
-
From USC Summer Programs to Entrepreneur: Transforming Snacks into Impactful Ventures

A pre-university entrepreneurship program at USC motivated Augustine Awadalla to complete high school ahead of schedule and follow his passion for business.
-
Kents Invest $10 Million to Propel Leadership and Innovation at Olin

Olin Business School at Washington University in St. Louis has been awarded a significant $10 million dual-purpose donation from long-time university supporters Jerry Kent, BSBA ’78, MBA ’79, along with his spouse, Judy Kent. This funding will establish an endowed deanship and advance the school’s Business of Health initiative, marking the largest donation to Olin…
-
Transformative Graduate Research: Creating Change in Urban Centers and Academic Halls

While striving to enhance economic growth in Detroit during the late 2010s, Nick Allen encountered a significant challenge. The municipality was aiming to encourage more investments following a long history of industrial migration to suburban areas and other states. Relying increasingly on property taxes for funding, the city was negotiating personalized tax arrangements with potential…
-
Federal Authorities Indict 22-Year-Old for Orchestrating RapperBot DDoS Network Linked to 370,000 Attacks

A 22-year-old individual from the U.S. state of Oregon has been accused of purportedly creating and managing a distributed denial-of-service (DDoS)-for-hire botnet known as RapperBot. Ethan Foltz from Eugene, Oregon, has been recognized as the operator of the service, according to the U.S. Department of Justice (DoJ). This botnet has been employed to execute significant…
-
A Heartfelt Tribute: Hundreds Honor FSU President Emeritus John Thrasher’s Legacy

“`html John Thrasher entered Florida State University in 1961 as a first-generation higher education student and subsequently made a significant impact as its 15th president. In the intervening years, he became a distinguished veteran, a legislative figure, and a public servant. However, for those who filled Ruby Diamond Concert Hall on Tuesday to commemorate his…
-
The post appeared first on Florida State University News.
-
Unlocking the Timing: Discovering Treatment Opportunities in Genetic Brain Disorders

Yale scientists have developed an innovative technique to forecast crucial intervals of gene expression in the maturing brain — a breakthrough that could pave the way for more precisely targeted genetic interventions.
-
Illuminating Hidden Opportunities: The Brinson Exploration Hub Initiatives

Three groundbreaking new initiatives to investigate Earth and the universe have been chosen to advance through the Brinson Exploration Hub at Caltech. Each project features a co-lead from Caltech’s campus alongside a counterpart from the Jet Propulsion Laboratory (JPL) and aims to chart the enigmatic strands of matter between galaxies utilizing ultraviolet radiation, employ seismic…
-
Tributes Pour In for Professor John Joannopoulos, Innovative Mind Behind Photonics and Soldier Nanotechnologies, Who Passed Away at 78

“`html John “JJ” Joannopoulos, the Francis Wright Davis Professor of Physics at MIT and leader of the MIT Institute for Soldier Nanotechnologies (ISN), passed away on August 17. He was 78. Joannopoulos was a remarkably productive investigator in the realm of theoretical condensed-matter physics, and an early innovator in the examination and utilization of photonic…
-
Revolutionary Technology Transforms Human Waste into Eco-Friendly Fertilizer

Researchers at Stanford have created a prototype that utilizes urine to produce essential fertilizer, providing answers for sanitation and energy in areas with limited resources.
-
Sugar-Infused Ultrasound: A Breakthrough in Targeted Drug Delivery
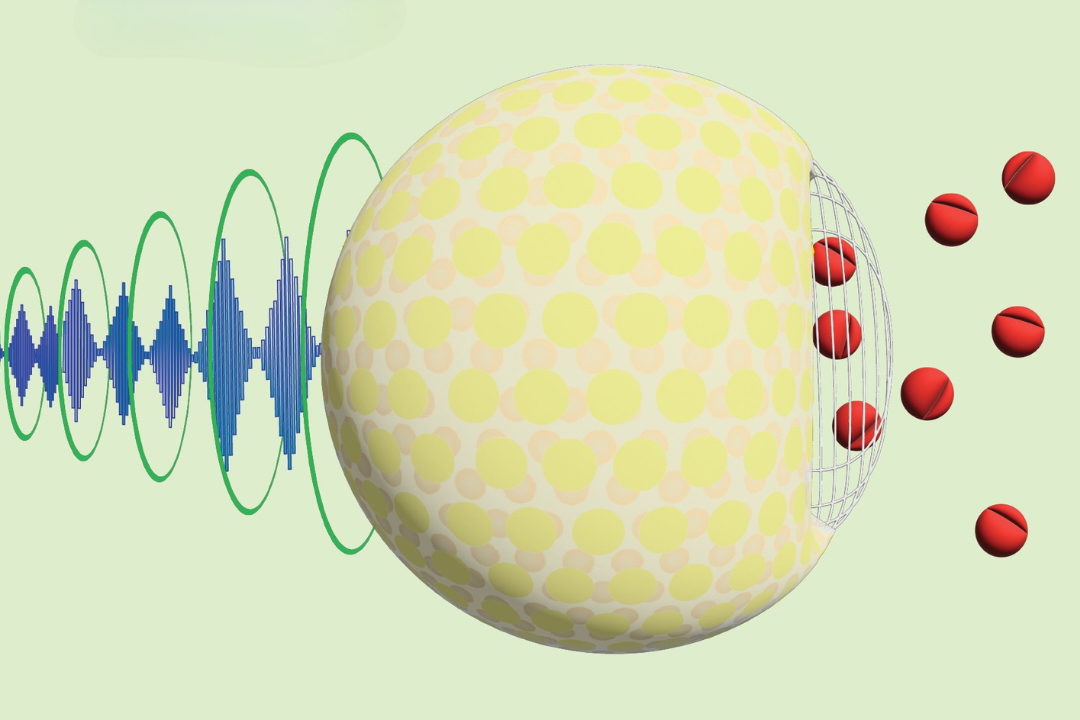
Researchers at Stanford have created a non-intrusive system that employs ultrasound-activated nanoparticles – combined with glucose – to administer medications with exceptional precision, reducing side effects.
-
Empowering Connections: AI Social Coaching for Individuals with Autism
A dedicated chatbot referred to as Noora is assisting people with autism spectrum disorder in honing their social abilities.
-
Oregon Resident Arrested for Involvement in ‘Rapper Bot’ DDoS Operation
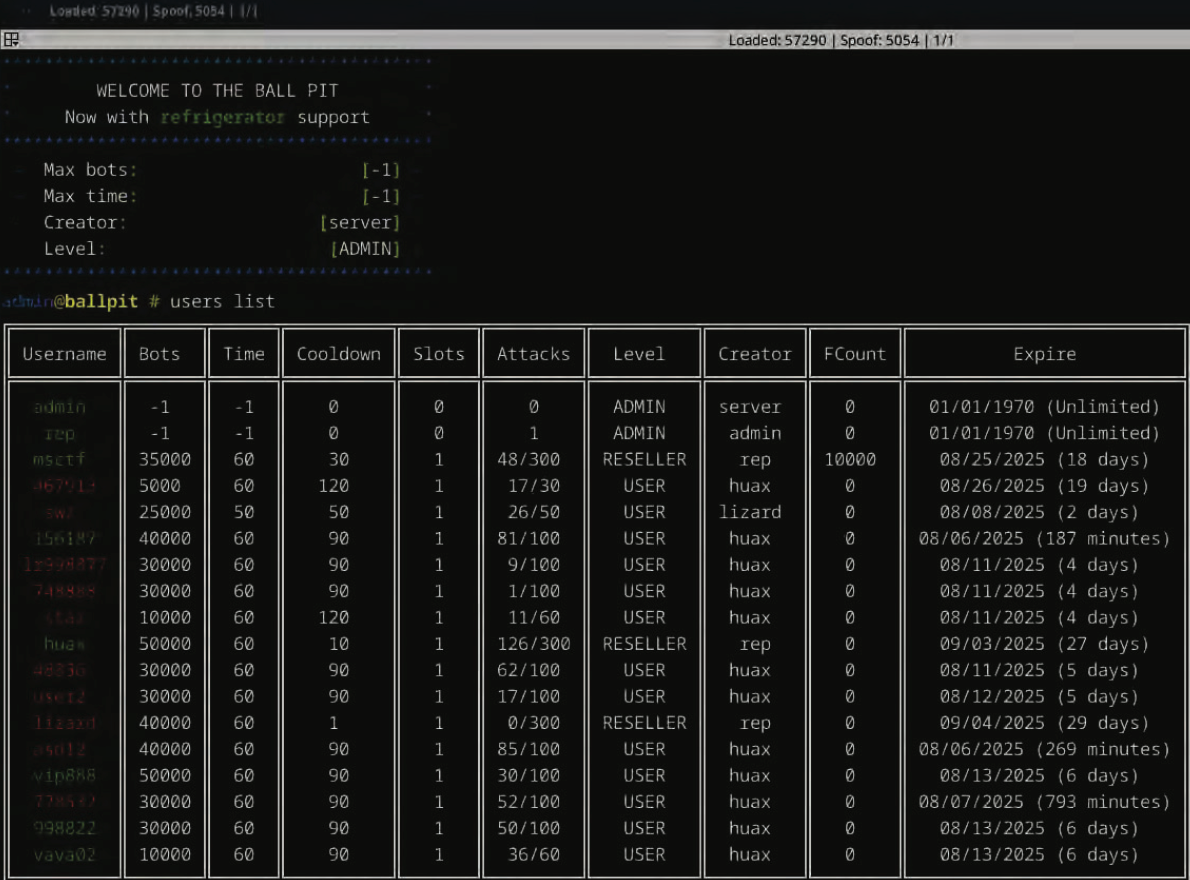
A 22-year-old man from Oregon has been apprehended on charges of managing “Rapper Bot,” a significant botnet employed to facilitate a service for executing distributed denial-of-service (DDoS) assaults on various targets — including a DDoS incident in March 2025 that disrupted Twitter/X. The Justice Department claims that the accused and an unspecified accomplice leased the…
-
Surge in Elasticsearch Reconnaissance Scans: August 19 Update
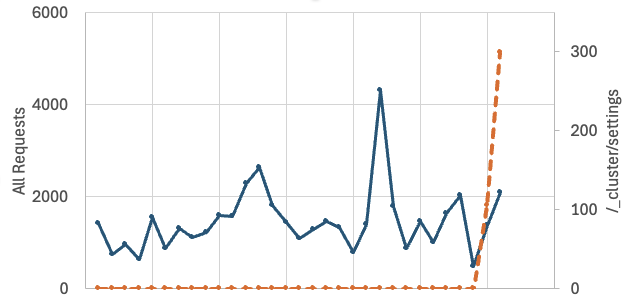
I observed a rise in attempts to detect Elasticsearch instances. Elasticsearch is not a recent focus. Its capacity to effortlessly store and handle JSON data, along with an uncomplicated HTTP API, renders it a handy instrument for storing data that can be directly reached from the browser using JavaScript. Particularly, Elasticsearch has gained traction for…
-
Celebrating the Legacy of William H. Webster: A Centenarian of Influence

“`html William Webster is depicted at his centennial birthday celebration last year. (Photo: Lauren Matthews/FBI) William H. Webster, an honorary emeritus trustee at Washington University in St. Louis, passed away on Friday, Aug. 8, 2025, in Warrenton, Virginia. He was 101 years old. Native to St. Louis, Webster was brought up in Webster Groves. He…
-
Texas A&M to Host Quantum Summit on September 19-20

The inaugural gathering will unite eight research institutions alongside industry executives and governmental policymakers to position Texas as a leader in quantum technologies.
-
Malicious Exploitation of Apache ActiveMQ Vulnerability Leads to DripDropper Malware Infection on Cloud-based Linux Platforms

“`html Malicious individuals are taking advantage of a security vulnerability that is almost two years old in Apache ActiveMQ to obtain lasting entry into cloud Linux platforms and install malware known as DripDropper. However, in a surprising turn of events, the unidentified perpetrators have been noted to be fixing the compromised vulnerability after gaining initial…
-
Lessons for AI Developers from Climate Activists: A Collaborative Future

“`html The objectives of individuals developing AI technologies for environmental purposes and those engaged in climate advocacy don’t necessarily coincide. In order to compare these two groups, researchers at UW conducted interviews with nine individuals focused on AI for sustainability and ten climate advocates.iStock Generative artificial intelligence technologies consume significant energy, however, numerous AI creators…
-
Understanding Our Robotic Companions

A group of joyful automatons, depicted by Sean David Williams, has assisted Yale Insights in elucidating the growth of artificial intelligence.
-
Reflections on Summer DOE Internships: A Yale Undergraduate Experience

Three undergraduates associated with Wright Lab — Diya Naik ’27, Vasilisa Malenkiy ’27, and Ingrid Slattery ’27 — have been chosen by the U.S. Department of Energy, Office of Science, for the Summer 2025 Science Undergraduate Laboratory Internships.
-
Echoes of Inquiry: Unleashing the Impact of Research

In this video series, encounter several individuals — researchers, personnel, andpatients — whose experiences and contributions showcase the significance and influence of Yale’s research throughout America.
-
Challenges in the Battle Against Pediatric HIV

“`html Nation & World Obstacle in the battle against pediatric HIV Funding reduction disrupts endeavor to free Botswana patients from antiretroviral treatment Liz Mineo Harvard Staff Writer August 19, 2025 5 min read Roger Shapiro. Niles Singer/Harvard Staff Photographer For over 20 years, Harvard infectious disease expert Roger Shapiro has battled HIV on the ground…
-
Texas A&M Leading the Charge in AI Innovation

From commerce to medical services to outer space, Texas A&M University is propelling the future of artificial intelligence through groundbreaking investigations.
-
Fresh Bucks Initiative Boosts Vegetable and Fruit Consumption, Enhances Food Security, According to UW Study

“`html The City of Seattle’s Fresh Bucks initiative collaborates with local entities to assist residents in acquiring fresh food.Pixabay Recent findings from the University of Washington indicate that the City of Seattle’s Fresh Bucks initiative can enhance fruit and vegetable consumption and food stability among low-income groups by supplying monetary assistance for procuring nutritious food.…
-
Bouncing Boldly: Essential Safety Tips for Trampoline Use

While a source of delight and physical activity for numerous kids, this apparatus can also act as a catalyst for considerable health hazards. A pediatric orthopedic specialist from Yale discusses optimal strategies for avoiding injury.
-
Caring for Our Community: A Drive for Personal Care Items for Families in Need
A fundraising campaign for Someone Cares Closet, a project by the Yale Child Study Center gathering hygiene products for families in need, will be held at Claire’s Corner Copia in New Haven from September 4–17.
-
“Embracing Growth: Yale Opens Its Doors to New Students”

In two ceremonies held at Cross Campus on Monday, President Maurie McInnis and other Yale officials greeted the university’s latest undergraduate and graduate students.
-
The Dark Allure of the Pacific Northwest: A Hotbed for Notorious Serial Killers
“`html Nation & World Why is the Pacific Northwest associated with numerous serial killers? In ‘Murderland,’ the alum delves into the lead-crime theory through the prism of her childhood memories in the region. Jacob Sweet Harvard Staff Writer August 19, 2025 5 min read In Caroline Fraser’s 2025 publication “Murderland,” the atmosphere is perpetually dense…
-
Stealthy GodRAT Malware Specifically Aims at Trading Companies with Innovative Steganography Techniques and Gh0st RAT Elements

Financial entities such as trading and brokerage companies are the focus of a fresh initiative that introduces a previously unrecorded remote access trojan named GodRAT. The harmful actions consist of the “spreading of harmful .SCR (screen saver) files masquerading as financial papers through Skype messenger,” stated Kaspersky analyst Saurabh Sharma in a technical report released…
-
Finding the Ideal Fit: Chelsea Doman’s Journey to her Dream MBA at Gies College of Business

As a solo mother of four, Chelsea Doman recognized that returning to education would require more than just determination; it necessitated a program tailored to her hectic schedule. She had developed a career encompassing pipeline operations, ten years of data interpretation, initiating a nonprofit focused on educational advocacy, and corporate analytics within the automotive sector.…
-
Remembering the Legacies of Wallis Annenberg and Glorya Kaufman

In remembrance: Honoring the contributions of benefactors and USC Life Trustees Wallis Annenberg, on the left, and Glorya Kaufman.
-
WashU Mobile App to Be Discontinued

Starting Thursday, Aug. 21, the WashU Mobile application will be discontinued as part of a planned shift to a collection of targeted mobile applications intended to offer direct access to the services most utilized by students, faculty, and staff. In the future, the WashU Mobile application will no longer receive maintenance or updates. For additional…
-
Connect with Passion: Meet the Six Montgomery Fellows for 2025-26

Pioneering artists and creative academics will become part of the Dartmouth community.
-
Birdwatching Milestone: Lab of Ornithology Celebrates 2 Billion Sightings and 3 Million Audio Recordings

The Cornell Lab of Ornithology and its eBird initiative, a citizen science platform where individuals globally can report bird observations and sounds for researchers to utilize in studies, recently achieved a couple of significant milestones.
-
Dutch Champion for the North Sea Honored with Stanford’s 2025 Bright Award
Emilie Reuchlin was honored with the accolade for her groundbreaking work in rehabilitating the North Sea’s Dogger Bank and enhancing legal safeguards for its delicate ecosystems.
-
Critical SAP Vulnerabilities Leave Unpatched Systems Vulnerable to Remote Code Execution Attacks

“`html A novel exploit merging two significant, now-resolved security vulnerabilities in SAP NetWeaver has surfaced in the wild, endangering organizations with potential system breaches and data exfiltration. The exploit at hand links CVE-2025-31324 and CVE-2025-42999 to circumvent authentication and enable remote code execution, according to SAP security firm Onapsis. CVE-2025-31324 (CVSS rating: 10.0) – Missing…
-
U.K. Government Abandons Plans for Apple Encryption Backdoor Following U.S. Civil Liberties Concerns

The U.K. administration has seemingly relinquished its intentions to compel Apple to diminish encryption safeguards and incorporate a backdoor that would grant access to the secured information of U.S. citizens. U.S. Director of National Intelligence (DNI) Tulsi Gabbard, in a declaration shared on X, mentioned that the U.S. government had been collaborating with its allies…
-
The Essential Role of Security Culture in Reducing Cyber Risk

“`html Following twenty years of constructing progressively refined security frameworks, enterprises are confronting a stark reality: instruments and technologies alone cannot sufficiently alleviate cyber threats. As technology ecosystems have become more advanced and proficient, adversaries have redirected their attention. They are no longer concentrating solely on infrastructure weaknesses. Rather, they are progressively “`
-
Bridging the Cybersecurity Talent Gap: The Power of Corporate Training

The worldwide cybersecurity skills deficit is at a pivotal point, making organizations more exposed to advanced threats. Attractive salaries and vigorous recruitment are insufficient; businesses require a sustainable strategy to cultivate in-house security proficiency. Corporate cybersecurity education is emerging as the most effective remedy, enabling…Read More.
-
Understanding Push and Pull Marketing: Key Differences and Strategies

Have you ever attempted to pull a door when the notice clearly states “push”? It doesn’t budge, you can’t proceed, and you wind up looking foolish. The same principle applies to marketing. If you push when you should be pulling or the other way around, you won’t accomplish anything. But how can you determine when…
-
Emerging Affiliate Marketing Trends to Watch in 2025

Keeping abreast of the rapidly evolving landscape of affiliate marketing necessitates staying alert to the most recent affiliate trends. As we eagerly anticipate what 2025 has in store, this is an ideal moment to revitalize your tactics, strategize effectively, and reexamine the influence of cutting-edge marketing methodologies. In this piece, we will …Read More.
-
Understanding the Upsides and Downsides of Comparative Advertising

Comparative advertising is a daring method of contrasting rival brands, and it can undoubtedly serve as a powerful means to attract attention. But is it the appropriate focus? Are comparisons too significant a risk for brands aspiring to win favor among consumers? Let’s examine the advantages and disadvantages of comparative advertising to gather some insights…Read…
-
Ubersuggest vs SEMrush: Which SEO Tool Reigns Supreme?

SEO can be challenging due to the necessity of implementing various strategies. From keyword research to analyzing competitors, resolving issues, producing content, performing site audits, and beyond. Utilizing an effective tool to handle these tasks simplifies the process significantly. The two well-known tools, Ubersuggest and SEMrush, provide comprehensive features to enhance your SEO efficiency and…
-
Essential Digital Marketing Statistics to Understand!

Digital marketing has risen as the most influential mode of promotion in the post-pandemic landscape. With the internet becoming the primary environment for companies to operate and for consumers to shop, conventional marketing has taken a backseat. Consequently, brands are depending on their digital approaches like never before. As per the most recent CMO Survey…Discover…
-
Mastering Instagram Threads: Your Comprehensive Guide to Features and Usage

Instagram Threads was introduced in July 2023. This novel social networking application serves as a rival to Twitter. It quickly turned into a sensation, accumulating millions of downloads just hours after its release. Currently, it is regarded as one of the principal social media applications globally and has already established itself as a significant platform…
-
Kickstart Your Cloud Computing and DevOps Career in Just Six Months! Join Our Upcoming Webinar on August 28, 2025, at 3:30 PM.
The necessity for Cloud Computing and DevOps expertise is greater than it has ever been. Compensation is increasing, organizations are transitioning more swiftly than ever, and the technology stack keeps advancing. The challenge? An overwhelming number of tools, numerous routes, and a lack of a definitive starting point. I’m Andy Luis, an IT expert with…
-
Exploring Georgia: UGA’s New Faculty Tour Expands Statewide Influence

The article UGA’s New Faculty Tour enhances statewide influence was initially published on UGA Today.
-
UGA Launches Dynamic Hub for Innovation and Collaborative Creativity

“`html The University of Georgia is redefining educational environments by integrating resources that enable students to explore their concepts and actualize them using advanced technologies. Within the new Creative Engagement Wing at the Miller Learning Center, students have the opportunity to record podcasts, create embroidered tapestries, 3D print prototypes for medical devices, or practice presentations…
-
Empowering Futures: USC Bovard Scholars Experience Hands-On Healthcare Training at USC Verdugo Hills Hospital

The medical facility’s Healthcare Day of Discovery provided attendees tailored career exploration experiences.
-
Groundbreaking Model Forecasts Molecular Dissolution Across Various Solvents
“`html Utilizing machine learning, MIT chemical engineers have developed a computational framework that can forecast how efficiently a specific molecule will dissolve in an organic solvent — an essential step in the creation of almost any pharmaceutical. This sort of prediction may significantly facilitate the formulation of innovative methods for producing medications and other beneficial…
-
U.K. Government Abandons Apple Encryption Backdoor Initiative Following U.S. Civil Rights Criticism
The U.K. administration has seemingly relinquished its intentions to compel Apple to diminish encryption safeguards and incorporate a backdoor that would permit access to the secured information of U.S. citizens. U.S. Director of National Intelligence (DNI) Tulsi Gabbard, in a declaration shared on X, stated that the U.S. government had collaborated with its allies in…
-
Unveiling a Critical Zero-Day Vulnerability in WinRAR

A zero-day flaw in WinRAR is being utilized by at least two Russian criminal organizations: The flaw appeared to possess extraordinary Windows capabilities. It exploited alternate data streams, a Windows functionality that allows for various representations of the same file path. The exploit took advantage of this aspect to activate an unknown path traversal vulnerability…
-
PyPI Takes Action: 1,800 Expired Domains Banned to Safeguard Against Account Takeovers and Supply Chain Threats

The custodians of the Python Package Index (PyPI) repository have declared that the package manager now verifies expired domains to avert supply chain assaults. “These modifications enhance PyPI’s overall account security framework, making it more challenging for malicious actors to misuse expired domain names to obtain unauthorized access to accounts,” stated Mike Fiedler, PyPI safety…
-
New Beginnings: Rawlinson Stadium Opens Its Doors with a Spectacular Victory for the Trojans

“`html USC Interim President Beong-Soo Kim inaugurates Rawlinson Stadium. (USC Photo/Steve Cohn) Share Athletics Rawlinson Stadium launches with ribbon-cutting and a Trojan triumph The venue on the University Park Campus is now the new base for the USC women’s soccer and lacrosse squads. August 18, 2025 By David Medzerian Beong-Soo Kim addresses attendees at the…
-
Safeguarding the Future: Enhancing Safety and Efficacy in Gene Therapy through Risk Management

Yale scientists have developed a novel RNA editing tool that can reduce some of the hazards associated with gene therapy.
-
Revitalizing Great Lakes Ecosystems and Economies: A Community-Driven Approach

“`html Alliance of Great Lakes nonprofits, led by U-M graduate Laura Rubin, aids communities in preserving and restoring the environment while cultivating a new generation of sustainable enterprises A cyclist rides along the Wilder River Walk at Muskegon Lake Nature Preserve. The area had previously been a literal dump before its restoration. Image credit: Greta…
-
Celebrating Excellence: FSU’s College of Social Sciences & Public Policy Recognizes Its 2025 Distinguished Alumni

“`html Florida State University’s College of Social Sciences and Public Policy (COSSPP) will acknowledge four alumni for their career accomplishments, contributions to the community, and assistance to the college and university. The college will honor the 2025 Distinguished Alumni — Jennifer Green, Jeff Kottkamp, Bobby Pittman Jr., and Carissa Schively Slotterback — at the College’s…
-
The Major Headlines: August 18, 2025

“`html In the historic Heritage Museum at Dodd Hall, enveloped by family, associates, and university officials, veteran Florida State University police officer Jason Trumbower was officially appointed on Tuesday as the institution’s new chief of police. Learn more … Access the newsletter. The article The Big Story: August 18, 2025 was originally published on Florida…
-
Transforming Spaces: Daejin Kim on the Impact of Interior Design in Senior Health Care

By Olivia Sanchez As the demographic shifts occur, the environments we inhabit significantly influence our aging process. Florida State University’s Daejin Kim, associate professor within the Department of Interior Architecture and Design, is a well-regarded authority in health care architecture and environmental psychology. His investigations concentrate on how interior spaces can facilitate aging in place,…
-
Are You Being Heard by Your Health Care Provider?

Investigators pinpoint six fundamental listening techniques that can result in the highest quality of care attainable.
-
Redefining the Stage: The Untold Story of Marginalized Artists Who Shaped Broadway Musicals

“`html A recent publication by David Armstrong offers a historical and cultural insight into how the Broadway musical was largely crafted by individuals marginalized from mainstream culture. A recent release from David Armstrong, an adjunct instructor of drama at the University of Washington, has emerged from his well-received course titled, “The Broadway Musical.” This course…
-
Unlocking New Perspectives: The Impact of the Color ‘Olo’ on Vision Science
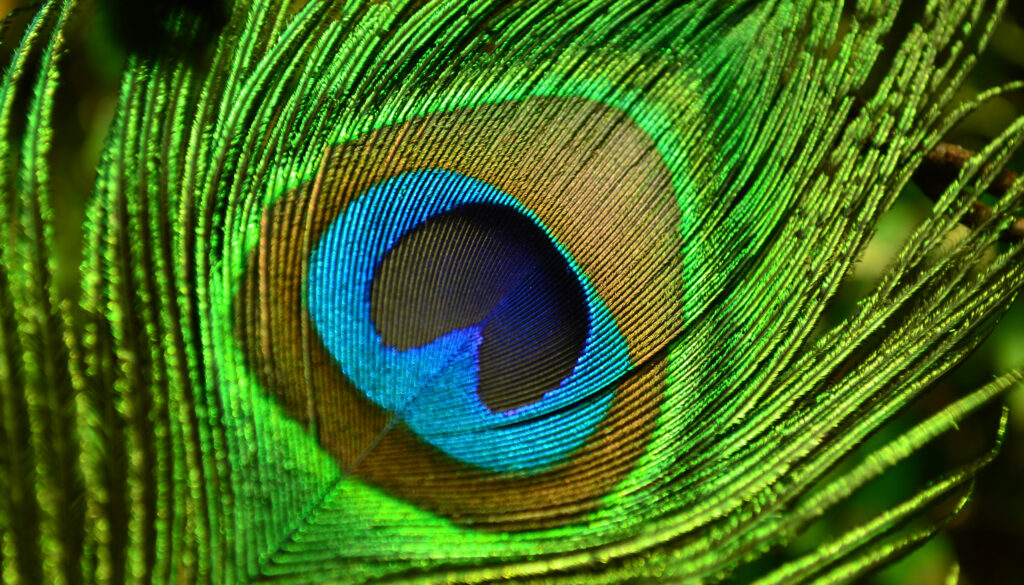
Researchers at UC Berkeley deceived the eye into perceiving “the most vibrant green” they had ever encountered. They claim it could revolutionize our comprehension and treatment of ocular disorders while broadening our perception of the environment around us. The article How seeing the new color ‘olo’ opens the realm of vision science was originally published…
-
Deciphering the Language of Proteins: Insights from Groundbreaking Research
In recent years, models capable of forecasting the structure or function of proteins have been extensively utilized for a multitude of biological applications, such as pinpointing drug targets and crafting novel therapeutic antibodies. These models, grounded in large language models (LLMs), are adept at making highly precise predictions regarding a protein’s appropriateness for a specific…
-
Saintilnord and Reynolds Recognized as Outstanding Early-Career Research Fellows

“`html WashU Medicine’s postdoctoral scholars Wesley Saintilnord (left), from the Department of Genetics, and Matthew Reynolds, from the Department of Biochemistry and Molecular Biophysics, have been recognized as Jane Coffin Childs Fellows. This esteemed accolade supports early-career researchers engaged in biomedical investigations that may illuminate the origins and treatment of human ailments. (Photo credited to…
-
Harnessing Genomic Weaknesses: How Breast Cancer Treatments Target Tumor Deficiencies
Investigating families with several members affected by breast cancer has led to the identification of mutations in BRCA genes. Medical professionals have determined that these mutations heighten the likelihood of developing various tumor types, including breast, ovarian, pancreatic, and prostate cancers. While these BRCA mutations escalate cancer risk by hindering DNA repair, they can also…
-
Kaneko Appointed as New Director of Cardiothoracic Surgery

“`html Tsuyoshi Kaneko, MD, a leader in clinical practice and research in minimally invasive valve operations and transcatheter methods, has been designated as the head of the Division of Cardiothoracic Surgery. Tsuyoshi Kaneko, MD, the John M. Shoenberg Chair of Cardiovascular Disease in the Department of Surgery at Washington University School of Medicine in St. Louis, has…
-
WashU Celebrates the Arrival of the Class of 2029

WashU freshman Ian Pentland received a celebrity’s reception as he entered Umrath House on August 15. “They were clapping and cheering,” remarked Pentland, originally from Kennebunk, Maine. “Everyone was saying, ‘Let’s go.’ I didn’t anticipate that, but it was truly delightful.” Pentland was among the 1,970 newcomers who settled into the South 40 during the…
-
Rising Living Expenses: A Key Issue for New York’s Workforce

The ILR School published its yearly New York at Work Report on Aug. 18, presenting insights regarding caregivers, household workers, individuals within the justice system, and those with intellectual and developmental challenges.
-
The Intersection of Art and Law: Cultivating Exceptional Legal Minds

The course “Arts and the Lawyer” not only necessitates that students reflect on and compose about the arts, but it also offers chances to engage in them.
-
Poorvu Center Unveils Revamped Website
Yale’s Poorvu Center for Teaching and Learning introduced an interactive new website this summer, specifically designed to address the requirements of the campus community.
-
Revolutionizing Cancer Research with 3D Genomic Mapping

Investigators have long been aware that cancer modifies its genome during its evolution. However, what has been less understood is how, when, and why genomic configurations shift as cancer advances. A recent Yale study unveils essential insights and possible biomarkers related to stage-specific cancer development.
-
Noodlophile Malware Campaign Broadens Its Global Scope Through Copyright Phishing Tactics
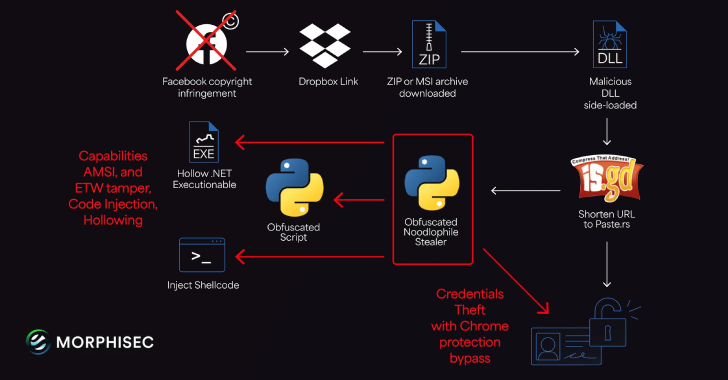
The threat individuals responsible for the Noodlophile malware are utilizing targeted phishing emails and enhanced distribution methods to introduce the information theft tool in assaults directed at businesses situated in the United States, Europe, the Baltic nations, and the Asia-Pacific (APAC) area. “The Noodlophile initiative, ongoing for more than a year, currently employs sophisticated spear-phishing…
-
When a Heart Attack is Only the Beginning of the Journey

“`html Healthcare For some individuals, the heart attack marks merely the onset Getty Images Sy Boles Harvard Staff Writer August 18, 2025 6 min read Harvard clinic employs mindfulness strategies to address medically induced PTSD Heart attacks are transformative experiences, though one specific type can be especially distressing. Spontaneous coronary artery dissection predominantly impacts women…
-
Windows Vulnerability Used as Gateway for PipeMagic RansomExx Malware Attack

Cybersecurity analysts have uncovered the tactics used by threat actors to leverage a recently fixed security vulnerability in Microsoft Windows to install the PipeMagic malware during RansomExx ransomware operations. These operations utilize the exploitation of CVE-2025-29824, a privilege elevation flaw affecting the Windows Common Log File System (CLFS) that was resolved by Microsoft in April…
-
3D Printing: A Game Changer with Unique Fingerprint Technology to Outsmart Adversaries

“`html An illustration of a fractured ghost gun. (Image: Raviv lab) 3D printing offers a straightforward method to produce personalized tools, spare components, and various useful items, yet it is also being utilized to manufacture untraceable weapons, often referred to as “ghost guns.” Netanel Raviv, an assistant professor of computer science and engineering at the…
-
Breakthrough Imaging Method Uncovers Secret Electrical Activity in the Brain
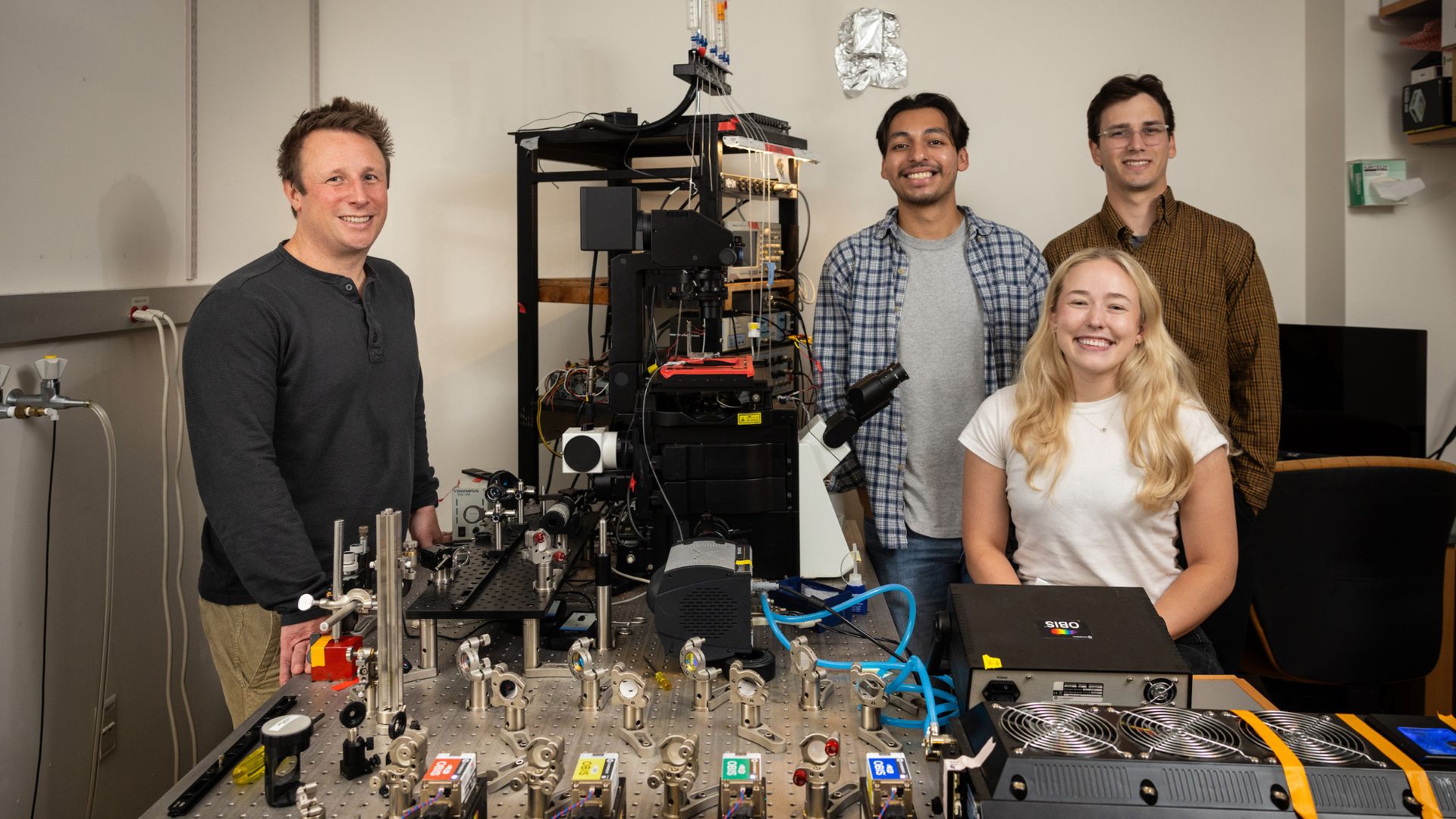
A grant from the Keck Foundation is assisting biological sciences professor Michael Hoppa in creating this innovative technology.
-
Pioneering a Future: Nanoscale Facility Aims to Cultivate Next-Gen Microchip Experts

The Cornell NanoScale Science and Technology Facility has introduced a complimentary VR youth outreach program, aimed at equipping the upcoming generation of learners in advanced microchip manufacturing.
-
“Exploring Passion: Farred’s Journey Through Lifelong Sports Fandom”

Grant Farred, a scholar at the Africana Studies and Research Center, recounts his affection for both a remote and a nearby sports franchise in “A Sports Odyssey: My Ithaca Journal,” released on July 25 by Temple University Press.
-
Spring’s Arrival in NYC Parks: How Urban Heat is Slowing the Season Down

Over twenty years of satellite images and sophisticated remote sensing evaluation reveal that rising winter temperatures and enhanced urban heat are delaying the onset of the growing season for trees.
-
Guarding Against MFA-Bombing Attacks: What You Need to Know

I recently arose (as is customary each day, ideally) and noticed a handful of Microsoft MFA alerts had notified me overnight. Since I had just come to my senses, I simply removed them, and then two minutes later it dawned on me – this indicates that one of my passwords had been breached, and I…
-
Driven by Passion and Purpose: Welcoming the Class of 2029

Cornell greets 3,861 inaugural students and 640 transfer individuals who commence their arrival on campus on Aug. 18, coming from all 50 states, along with Washington, D.C., Puerto Rico, the Mariana Islands, and 97 nations.
-
Fresh Dialogues, New Beginnings

On the day of relocation, Yale College freshmen gathered as unknowns and departed as companions — and even had a moment with President Maurie McInnis, who reminisced about her own beginnings as a Yale student.
-
⚡ This Week in Review: NFC Scams, Curly Comrades, N-able Vulnerabilities, Docker Security Risks & More

Power doesn’t simply vanish in one massive incident. It diminishes through the minor details—a patch that’s overlooked, a configuration that’s incorrect, a system that lacks oversight. Security generally doesn’t collapse all at once; it deteriorates gradually, then abruptly. Remaining secure isn’t about having all the answers—it’s about responding swiftly and decisively before issues accumulate. Transparency…
-
Sunshine Genetics Act: Advancing FSU’s Leadership in Pediatric Rare Disease Research
The article FSU Impact: Sunshine Genetics Act Aids University in Remaining Leading Edge of Pediatric Rare Illness Research was initially published on Florida State University News.
-
New Threats Uncovered: Malicious Packages Targeting Supply Chain Vulnerabilities in PyPI and npm

Cybersecurity analysts have identified a harmful package in the Python Package Index (PyPI) repository that incorporates harmful actions via a dependency, enabling it to maintain persistence and execute code. The package, referred to as termncolor, implements its sinister functionality through a dependency called colorinal via a multi-phase malware operation, Zscaler.
-
Enhancing Regulatory Compliance with Wazuh

Organizations managing different types of sensitive information or personally identifiable details (PII) must adhere to regulatory compliance guidelines and frameworks. These compliance guidelines are also relevant to entities functioning in regulated industries such as healthcare, finance, government contracting, or education. A few of these guidelines and frameworks consist of, but are not limited to:
-
Listening in on Phone Conversations via Vibrational Cues

Scientists have succeeded in intercepting cell phone vocal discussions by employing radar to sense vibrations. It serves more as a demonstration than anything substantial. The radar device is merely ten feet distant, the configuration is refined, and precision is lacking. Nonetheless, it’s a beginning.