-
Inside the GhostRedirector Attack: 65 Windows Servers Compromised via Rungan Backdoor and Gamshen IIS Module

“`html Cybersecurity investigators have unveiled a previously unrecorded threat group referred to as GhostRedirector, which has succeeded in infiltrating a minimum of 65 Windows servers mainly situated in Brazil, Thailand, and Vietnam. The assaults, according to Slovak cybersecurity firm ESET, resulted in the installation of a covert C++ backdoor named Rungan and a native Internet…
-
A Fish with a Twist: The Intriguing Forehead Teeth of Mating Masters

“`html A research team led by the University of Washington discovered teeth on the tenaculum of adult male spotted ratfish. They unearthed indications of a similar formation in fossils from ancient ratfish relatives, reimagined here by local artist Ray Troll.Ray Troll When discussing teeth, vertebrates exhibit many similarities. Regardless of shape, size, or sharpness, teeth…
-
Unearthing Mysteries: Dark Matter Explorers in the Heart of the French Alps

“`html The DAMIC-M dark matter detector is located beneath the Alps, under 5,000 feet of rock, shielding it from cosmic rays and other types of interference. The Milky Way, along with nearly all other galaxies, is bound together by dark matter, yet researchers have not yet directly witnessed this elusive substance.iStock When researchers examine the…
-
University of Michigan Secures $15 Million NSF Grant to Revolutionize Natural Hazard Research
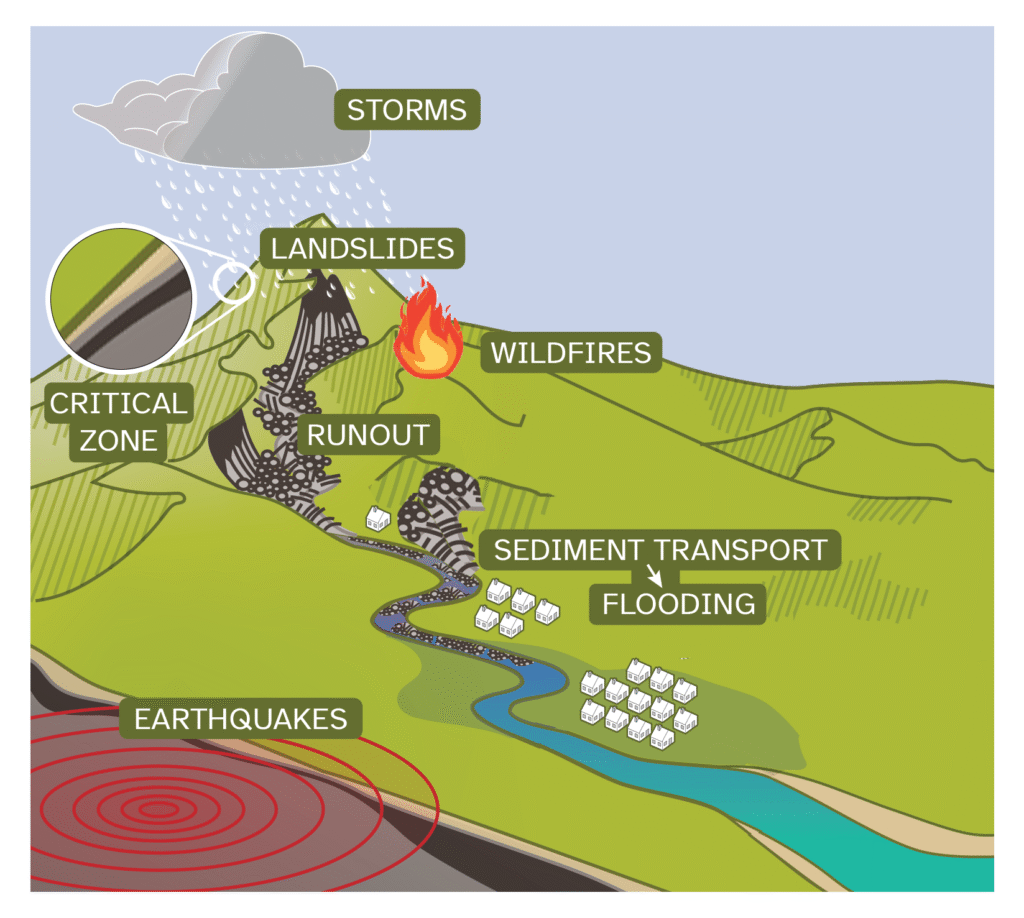
“`html Researchers at the University of Michigan and their partners nationwide are working to deepen comprehension of the interconnected risks that arise from occurrences like earthquakes and wildfires, aiming to bolster resilience against these subsequent threats. Image courtesy: CLaSH The University of Michigan, collaborating with over a dozen educational, governmental, and community entities across the…
-
The Unexpected Dining Habits of Small Black Holes

“`html The state-of-the-art XRISM satellite has disclosed that diminutive black holes do not accumulate matter as anticipated—a discovery that could influence entire galaxies Conceptual depiction of a black hole X-ray binary. The intense gravity of the black hole—displayed as a small black dot at the center of the disk on the right—attracts gas from the…
-
Ignited by Imagination

The Moody Summer Capstone course provides learners a chance to engage in a practical project from the New York advertising firm, Hudson Rouge, and their client, the Lincoln Motor Company. The article Driven by creativity was originally published on UT Austin News – The University of Texas at Austin.
-
Embracing New Beginnings: The Class of 2029 Arrives at Dartmouth

Senior executives welcome first-year students and their families during the yearly event.
-
Navigating Seasons of Purpose: An Alum’s Journey through Faith, Education, and Leadership

In a recent autobiography, Jack Scott ’62 B.D. reflects on a journey characterized not only by extraordinary success but also by a significant transformation — in vocation, in location, and most importantly, in perspective.
-
Exploring the Distinct Biological Factors in Asthma Among Genders

A recent Yale-led investigation clarifies how asthma manifests differently in men and women, both in terms of symptoms and at the genetic expression level.
-
Revolutionizing LIGO: The Power of Artificial Intelligence
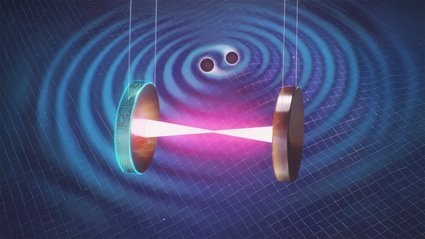
“`html The US National Science Foundation LIGO (Laser Interferometer Gravitational-wave Observatory) has been referred to as the world’s most accurate measuring device due to its capacity to detect movements smaller than 1/10,000 the diameter of a proton. Through these exceedingly accurate measurements, LIGO, featuring two locations—one in Washington and another in Louisiana—can sense ripples in…
-
Is Your Cellphone Use Increasing Your Risk of Hemorrhoids?

“`html Health Does this mobile device habit elevate chances of hemorrhoids? File image by Niles Singer/Harvard Staff Photographer Jacqueline Mitchell BIDMC Communications September 4, 2025 7 min read Gastroenterologist Trisha Pasricha explores how recent discoveries may alter your perspective on restroom habits Hemorrhoids rank among the most common gastrointestinal issues in the United States, leading…
-
Witnessing the Dawn of History

“`html Science & Technology Observing history in the making These visuals are a combination of distinct captures of the “small red dots” obtained by the James Webb Space Telescope through its main near-infrared imager, which offers high-definition imaging and spectroscopy for investigating the early universe. Image: NASA, ESA, CSA, STScI, Dale Kocevski (Colby College) Kermit…
-
Enchanting Remedies for Easing Intense Back Pain

“`html Health With melodies to alleviate a fierce backache Music seems to lower anxiety and discomfort in emergency room patients, research indicates Anna Lamb Harvard Staff Writer September 4, 2025 4 min read Playwright William Congreve noted in the Restoration era that music “has charms to soothe a savage breast.” Interestingly, this also applies to…
-
“Chronic Pain and Sleep Disruption: Insights from Mouse Research”

“`html Moron-Concepcion (left), Musiek and Ibrahim Discomfort and sleep irregularities frequently coexist — over 30% of the U.S. populace endures discomfort, and a substantial number of those suffering also report sleep complications — yet the connection between the two remains significantly underexplored. Recently, investigators at WashU Medicine have created a novel mouse model that replicates…
-
St. Louis Pigeons: An Urban Perspective on a Global Avian Ambassador

“`html Pigeons appear quite comfortable in St. Louis. You can observe groups roosting on rooftops and utility wires, anticipating an opportunity to snatch a stray morsel or smear a windshield. Urban areas have driven numerous animals from their natural environments, yet pigeons flourish in human domains, stated Daisy Lewis, AB ’23, a former undergraduate at…
-
Empowering First-Gen Students: The Fellows Program Offers Skills and Support

“`html Sophomore Kiersten Anderson aims to attain a PhD in developmental psychology. This summer, the Chancellor’s Career Fellows Program supported her internship at the local nonprofit Memory Keepers. (Photo: Zach Trabitz/WashU) WashU sophomore Kiersten Anderson gets ready to dance in front of her laptop, radiating warmth for a Zoom gathering filled with senior patients. Her…
-
Toni Morrison’s Cornell Legacy Commemorated in a Four-Day Celebration

A four-day occasion showcasing movies, discussions, seminars, the reveal of a mural, and additional activities will honor the 70th commemoration of her degree, existence, and contributions. “Toni Morrison: Literature and Public Life” is scheduled for Sept. 18-21.
-
Playful Architecture: Meet José Sánchez, the Faculty Innovating Design Through Engagement

José Sánchez not only creates structures. He devises experiences that educate individuals on constructing an improved world.
-
Harnessing a Varied Approach to Climate Solutions

In a Q&A, Dean Takahashi ’80, ’83 M.P.P.M, the creator and managing director of the Carbon Containment Lab and ex-senior director of the Yale endowment, talks about applying his investment expertise to create approaches for tackling climate change.
-
“Khushi Baby: Celebrating a Decade of Transformation and Looking Towards the Future”

A collective of Yale scholars’ innovative concept of a digital charm for baby vaccination documentation has evolved into the cornerstone of one of India’s most expansive digital health platforms.
-
Navigating the Everyday Politics of Public Sector Workers in Jordan

Elizabeth Parker-Magyar, who became part of the Yale faculty this autumn, examines modern comparative politics of the Middle East, especially those occurring as protests, social movements, revolutions, and civil society associations.
-
“Agroecology Unpacked: A Professor’s 101-Second Insight”

Drawing inspiration from environmental studies and years of agricultural knowledge, agroecology seeks to develop more sustainable methods for food production. The article Watch a professor explain agroecology in 101 seconds was initially published on Berkeley News.
-
J-WAFS Appoints Daniela Giardina as New Executive Director

The Abdul Latif Jameel Water and Food Systems Lab (J-WAFS) has proclaimed that Daniela Giardina has been appointed as the new executive director of J-WAFS. Giardina assumed her responsibilities at the onset of the autumn semester, succeeding founding executive director Renee J. Robins ’83, who is heading into retirement after guiding the program since its…
-
Melodies by the Fire: Sipping Joy on the Move
“`html Campus & Community A joyful location, campfire performance, quality coffee on the move Photo illustration by Liz Zonarich/Harvard Staff September 4, 2025 2 min read Harvard violist shares 3 suggestions to relish life’s simple pleasures An element of the Favorite Things series Suggestions from Harvard faculty Jessica Bodner serves as a Professor of the…
-
The Scent of Discovery: Exploring the Science of Smell

“`html Science & Technology A fragrance assessment for science Graphics by Liz Zonarich/Harvard Team Sy Boles Harvard Staff Journalist September 4, 2025 4 min read Investigator shares vision for devices that could assist patients in regaining crucial ties with their environment One of the more perplexing COVID-related symptoms is the diminished sense of smell, which…
-
The Lasting Impact of Childhood Habits on Adult Life
“`html An individual’s physical capability and cardiovascular wellness in adulthood may be linked to habits formed during childhood, according to a recent study from the University of Georgia. The research indicated that both healthy and unhealthy exercise practices in adolescence, beginning as early as age 11, could lay the groundwork for physical wellbeing later in…
-
The Dynamic Journey of Madeleine Martin: Blending Acting, Animation, and Education

“`html As a young girl, Madeleine Martin created puppet performances behind a quaint wooden stage adorned with crimson drapes. Her siblings provided candid feedback, yet she continued to script and perform. This determination and creativity propelled her journey from living room performances to Broadway, television, animation, and ultimately to Florida State University, where she instructs…
-
Discover 3I/Atlas: A Cosmic Wanderer from Distant Realms

“`html Introducing 3I/Atlas, a celestial body from a different solar system nprevenas Thu, 09/04/2025 – 06:01 Introducing 3I/Atlas, a celestial body from a different solar system Current Day Category of Stories Science & Technology Outer Space By NPR Science Friday Type of News Article Outside News “`
-
Animal Protein: A Key to Enhanced Recovery After Workouts, Research Reveals

New findings from Texas A&M University indicate that pork-based MREs facilitate improved recovery compared to plant-based alternatives following strenuous military training.
-
Broadening Horizons: U-M Leaders Recognized for Enhancing Global Education Opportunities

“`html Cheryl Moyer engages with village elders in Wuru, northern Ghana. Cheryl Moyer collaborates with local nurses at Holy Family Hospital, Ghana. Every year, numerous University of Michigan scholars transform the globe into their learning environment, taking advantage of a diverse range of international educational opportunities. From immersive overseas study and language initiatives to practical…
-
Cybercriminals Take Advantage of X’s Grok AI to Evade Ad Safeguards and Unleash Malware to Millions

“`html Cybersecurity analysts have identified a novel method that cyber offenders have embraced to circumvent social media platform X’s malvertising defenses and disseminate harmful links utilizing its artificial intelligence (AI) assistant Grok. The discoveries were emphasized by Nati Tal, leader of Guardio Labs, in a sequence of updates on X. The method has been designated…
-
France Slaps Google with $379 Million Fine for Missteps in Cookie Consent Regulations

“`html The French data privacy regulator has penalized Google and Chinese online retail behemoth Shein $379 million (€325 million) and $175 million (€150 million), correspondingly, for breaching cookie regulations. Both firms placed advertising cookies on users’ browsers without obtaining their approval, stated the National Commission on Informatics and Liberty (CNIL). Shein has since modified its…
-
CISA Alerts on Actively Exploited Vulnerabilities in TP-Link Routers: CVE-2023-50224 and CVE-2025-9377

“`html The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Wednesday incorporated two security weaknesses affecting TP-Link wireless routers into its Known Exploited Vulnerabilities (KEV) directory, indicating that there is proof of them being utilized in real-world attacks. The vulnerabilities in discussion are outlined below – CVE-2023-50224 (CVSS score: 6.5) – A vulnerability allowing authentication…
-
The Dark Side of Generative AI: A Tool for Cybercriminals

“`html Anthropic reports on a user of Claude: Recently, we thwarted a complex cybercriminal who employed Claude Code to execute extensive theft and extortion of personal information. The perpetrator targeted no fewer than 17 diverse organizations, encompassing healthcare, emergency services, along with governmental and religious entities. Instead of encrypting the pilfered data with conventional ransomware,…
-
Highlights from the Faculty and Staff Assembly: August 2025 Edition

“`html The exceptional faculty at Florida State University play a pivotal role in the university’s objectives. The pursuit of excellence in scholarship, research, and creative endeavors is vital for ensuring high-quality student education and positively impacting the lives of individuals. Throughout the year, accolades and acknowledgments are given to various faculty and staff across the…
-
FSU Named One of America’s Top Employers in 2025 by Forbes

“`html Florida State University has been recognized among America’s Premier-In-State Employers by Forbes. Forbes’ Premier-In-State Employers 2025 list showcases organizations that excel in employee contentment and retention. This esteemed accolade is awarded in partnership with Statista, the leading global statistics platform and industry ranking institution. FSU ranked ahead of various national corporations on this year’s list…
-
Aspirations Soar: Feature Twirler Mikayla Schuller’s Ambitions at FSU

The article Highlight Twirler Mikayla Schuller Holds Ambitious Aspirations at FSU was initially published on Florida State University News.
-
Florida State University iSchool Professor Celebrated with Dual Awards for Advancements in Health Informatics
“`html Professor School of Information at Florida State University, Zhe He, has been awarded two significant accolades for his contributions to health informatics. He has been inducted as a Fellow of the International Academy of Health Sciences Informatics (IAHSI) and has secured a $280,000 grant from the National a2 Pilot Awards Competition, which is sponsored…
-
Exploring the Heart of USC’s Innovative AI Research Hub

To commemorate the debut of the USC School of Advanced Computing, USC Viterbi collaborated with JayByrd Films to produce a drone “fly over” video of the establishment.
-
Garimella’s Inaugural Letter: U of A Shines with Resilience and Promise for Tomorrow
“`html President Garimella’s initial yearly correspondence: U of A is ‘dynamic, robust and prepared for a luminous future’ nprevenas Wed, 09/03/2025 – 08:04 President Garimella’s initial yearly correspondence: U of A is ‘dynamic, robust and prepared for a luminous future’ Visual Today University of Arizona President Suresh Garimella has unveiled his initial yearly letter to…
-
Joint Chiefs Chairman to Address Texas A&M’s Bush School in Washington, D.C.

Gen. John D. Caine will provide perspectives on global issues, inspiring the upcoming cohort of national security pioneers.
-
Harnessing USC-Developed AI: Transforming Army Education

“`html The Army Writing Enhancement (AWE) tool, created at the USC Institute of Creative Technologies, seeks to assist soldiers in enhancing their written communication without supplanting the vital function of human critical thinking. (Photo: iStock) Disseminate Defense How the Army applies USC-developed AI in education Employing a USC Institute for Creative Technologies tool, soldiers harness…
-
A Tribute to Frank Price: Celebrated Hollywood Producer and Esteemed USC Trustee Passes at 95

“`html Frank Price speaks to students (Photo/Courtesy of USC School of Cinematic Arts) Distribute University In remembrance: Frank Price, 95, distinguished Hollywood producer and USC trustee The executive, who managed productions such as Gandhi and Ghostbusters, held the position of founding chairman of the Board of Councilors at the USC School of Cinematic Arts. September…
-
Unlocking the Secrets of Infertility: The Potential of Bioelectronic Materials
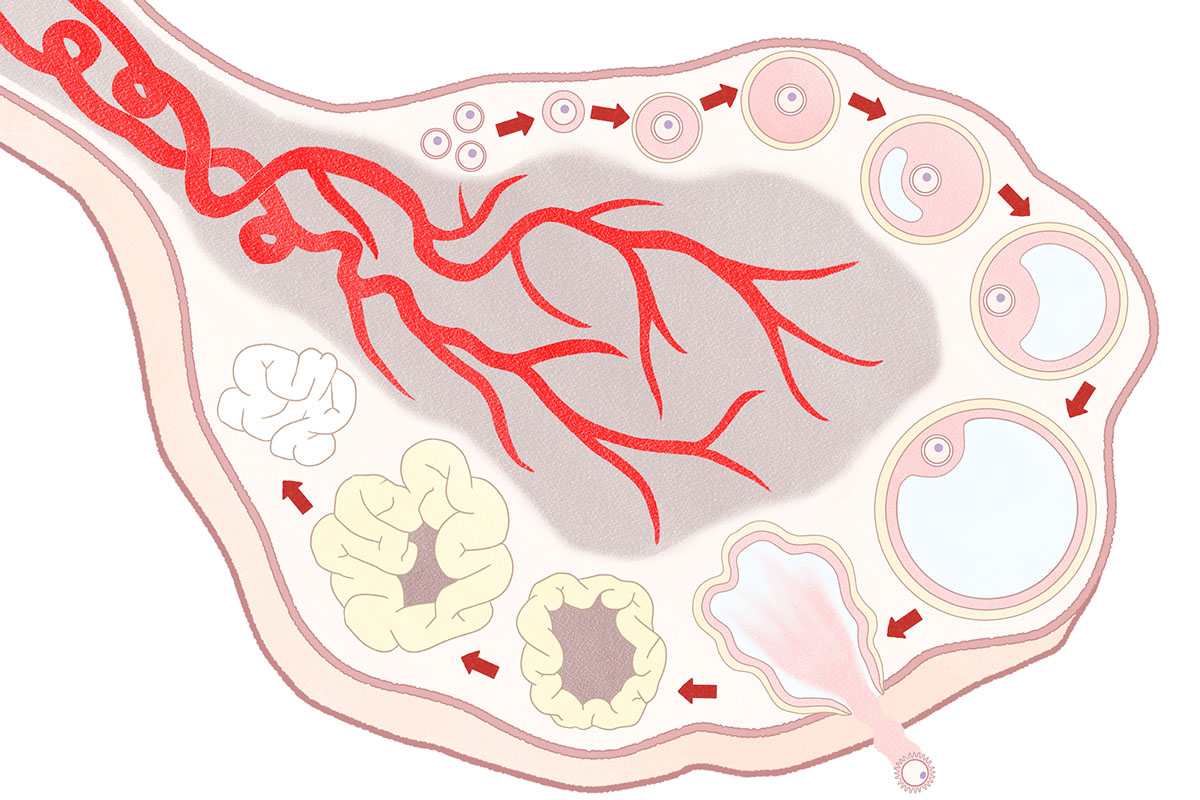
“`html Ovarian follicle maturation (Image: iStock) Throughout a woman’s reproductive lifespan, ovarian follicles harboring an immature ovum are summoned each month for maturation while others remain in reserve for years or even decades. Nevertheless, scientists are uncertain about how this selection occurs. Further insights into the selection mechanism could foster a fresh comprehension of female…
-
Stitziel Receives Prestigious Scholar-Innovator Award

“`html Stitziel Nathan O. Stitziel, MD, PhD, a faculty member in medicine and genetics at Washington University School of Medicine in St. Louis, has been honored with the Harrington Discovery Institute 2025 Scholar-Innovator Award. This accolade aids in expediting innovative treatments for ailments such as cardiovascular diseases, autoimmune conditions, and cancer. He is one of…
-
Doctorow Launches A.D. White Series: A Sci-Fi Adventure in Ithaca, NYC

Best-selling author and tech blogger Cory Doctorow will undertake the A.D. White Professor-at-Large program’s second dual-campus appearance, concluding his week at Cornell Tech in New York City. Four additional professors are scheduled to visit Cornell this autumn.
-
Fostering Public Health Confidence Through Open Communication

Dialogue specialist offers tactics on how to converse — and hear — enabling individuals to feel acknowledged.
-
Promising Molecule Emerges as a Potential Game-Changer for MASH, Endometriosis, and Chronic Illnesses
A research conducted by Yale scientists reveals that the compound Bobcat339 aims at traitor macrophages within the immune system and exhibits beneficial effects in models of hepatic disorders, pulmonary cancer, and endometriosis.
-
Yale Takes Center Stage with Its Sixth Global Virtual Film Festival

Taking place from December 4–6, 2025, the three-day affair will present an exciting array of feature and short films and will be assessed by a distinguished alumni panel featuring TJ Noel-Sullivan, Eunice Kiang, and Daniel Persitz.
-
Embarking on New Adventures: Yale College Welcomes First-Year, Transfer, and Adult Students

Yale College last month embraced 1,640 new freshmen to New Haven as participants of the Class of 2029.
-
Harnessing DNA: A Revolutionary Neural Network that Learns through Examples

“`html Neural networks are computational frameworks crafted to replicate both the organization and operation of the human brain. Caltech scientists have been innovating a neural network constructed from strands of DNA rather than electronic components, executing computations through chemical reactions instead of digital signals. A crucial attribute of any neural network is its capability to…
-
“Accessing Opioid Addiction Treatment: The Ongoing Challenge in Pharmacies”

Merely 4 out of 10 retail pharmacies in the U.S. stock buprenorphine, with availability even more restricted in Black and Latino populations, recent UC Berkeley findings reveal. The article Although prescribing regulations have been eased, opioid addiction treatment remains difficult to locate at pharmacies was initially published on Berkeley News.
-
Revolutionizing Chemistry: A Novel Generative AI Method for Anticipating Chemical Reactions

“`html A multitude of efforts have been undertaken to leverage the capabilities of innovative artificial intelligence and extensive language models (LLMs) to forecast the results of novel chemical reactions. These attempts have encountered limited achievements, partly because they have not been anchored in a comprehension of fundamental physical concepts, such as the principles of mass…
-
Debunking Myths and Revealing Truths About Lyme Disease

A specialist in infectious diseases clarifies the tick-related ailment and why it is frequently misinterpreted by both patients and the healthcare providers guiding them.
-
“Deceptive npm Packages Threaten Ethereum Smart Contracts and Endanger Crypto Developers”

“`html Cybersecurity analysts have identified two additional harmful packages on the npm registry that utilize smart contracts for the Ethereum blockchain to execute nefarious activities on breached systems, indicating the pattern of threat perpetrators perpetually searching for innovative approaches to disseminate malware and evade detection. “The two npm packages exploited smart contracts to hide malicious…
-
Unexploded Ordnance: An Environmental Hazard Amplified by Climate Change

“`html The impact of unexploded ordnance on the environment – and how climate change intensifies the issue nprevenas Wed, 09/03/2025 – 09:32 The impact of unexploded ordnance on the environment – and how climate change intensifies the issue Today Categories of the Story Government, Public Policy & Legislation Current Events By The Conversation Type of…
-
Astronomers Unveil WISPIT 2b: The First Exoplanet in a Multi-Ringed Disk and Larger Than Jupiter

“`html Astronomers identify 1st exoplanet within a multi-ringed disk. WISPIT 2b surpasses Jupiter in size nprevenas Thu, 08/28/2025 – 10:50 Astronomers identify 1st exoplanet within a multi-ringed disk. WISPIT 2b surpasses Jupiter in size Aug. 28, 2025 News Categories Current Events Science & Technology Cosmos By USA Today Type of News Article Outside News “`
-
The Art of Healing: A Creative Perspective on Patient Care

Nursing scholars investigate patient treatment via visual art at the Blanton Museum of Art The article Investigating Patient Treatment Through an Artist’s Perspective was initially featured on UT Austin News – The University of Texas at Austin.
-
Unveiling the Financial Impact of UT Student Volunteers and the Benefits of Joining Campus Organizations
Belonging to Student Groups Offers Significant Advantages, Studies Indicate The article New Research Reveals the Economic Value of UT Student Volunteerism and Impact of Participation in Student Organizations was originally published on UT Austin News – The University of Texas at Austin.
-
Bauer Leaders Academy Launches Grant Applications and Celebratory Breakfast Event

“`html First-year pupils contemplate their mission during a 2024 Bear Beginnings orientation session focused on leadership. (Photo: Danny Reise/WashU) The Bauer Leaders Academy and the Olin Business School’s Bauer Leadership Center are welcoming seed grant applications from instructors across all fields to create a new course or enhance an existing one with content that encourages…
-
September Reflections on the Green
“`html Orientation for the Cohort of 2029 and autumn athletics are set to commence. “`
-
Scott Belsky, Innovator Behind Behance and A24 Labs, Now a Member of Cornell Tech Council

Cornell University graduate Scott Belsky ‘02, associate at entertainment firm A24 and creator of A24 Labs and Behance, has become a member of the Cornell Tech Council.
-
“From Playful to Reserved: The Shift in Brain Activity that Alters Social Behavior as We Grow Up”

Researchers have charted the neural communication that propels social urges essential for the survival of young mammals.
-
Rising Threats: Exploit Attempts Target Dassault DELMIA Apriso – CVE-2025-5086

“`html When I contemplate the safety of production settings, my attention often shifts to IoT gadgets embedded within assembly lines. The numerous tiny sensors and actuators can frequently be quite challenging to safeguard. Conversely, there exists also “large software” utilized for overseeing manufacturing. A notable instance is DELMIA Apriso by Dassault Systèmes. This category of…
-
Rethinking the World: Why Accurate Representations of Africa Matter

Standardized illustrations exaggerate the dimensions of nations situated near the North or South Pole, leading to a diminished portrayal of extensive regions of South America and Africa. The article The Conversation: World Maps Get Africa’s Size Wrong: Cartographers Explain Why Fixing It Matters was originally published on News.
-
UGA and Boehringer’s Collaboration Recognized for Excellence in Sustainability Initiatives

The University of Georgia’s continuing collaboration with Boehringer Ingelheim has not only transformed lives and industries, but now celebrates a Golden Helix Phoenix Award for its Sustainable Development Experience (SDX) initiative. This accolade — endorsed by the Metro Atlanta Chamber and awarded by Georgia Life Sciences — honors a partnership between industry and academia that…
-
Youthful Impulses: The Rising Trend of Insurance Fraud Among Young Adults
“`html If you are below the age of 34, you might be more inclined to engage in insurance fraud, as indicated by recent research from the University of Georgia. The latest study implies that the younger individuals are, the higher the likelihood they may deceive a company or adjuster to obtain preferred funds or results.…
-
FSU’s Faculty Innovator Series Fosters Collaborative Creativity

The article Faculty Innovator Series Fosters a Culture of Cooperation at FSU was initially published on Florida State University News.
-
Peter Collins Triumphantly Re-elected as Chair of FSU Board of Trustees

“`html The Board of Trustees at Florida State University re-elected Trustee Peter Collins as its chair with unanimous support during the assembly on Aug. 29. “I am privileged to take on the role of chair of the FSU Board of Trustees,” Collins remarked. “My affection for the university is profound, and I cherish the opportunity…
-
Shaping Tomorrow: Insights from a Florida State University Expert on the Future of America’s Workforce

“`html The arena of America’s labor force is persistently transforming as challenges like diminishing birth rates, evolving skill priorities, and emerging job opportunities due to AI present a captivating forecast for the future. As stated by the U.S. Chamber of Commerce, employers are creating new positions while embracing advanced technologies but still face difficulties in…
-
FSU Triumphs Over Alabama in Thrilling College Football Season Opener

“`html The Florida State Seminoles triumphed over No. 8 Alabama, 31-17, in front of a packed audience at the recently updated Doak Campbell Stadium. The article Images: FSU triumphs over Alabama in Week 1 of College Football was published first on Florida State University News. “`
-
Unfolding Events: A Glimpse into September 2, 2025
“`html FSU spotlight twirlers, Kylee Saltsman and Mikayla Schuller, are returning to spark another season. As members of the globally acclaimed Marching Chiefs, these two feature twirlers, who have ambitious scholarly and professional aspirations, uphold a legacy that has established FSU as one of the most esteemed programs in collegiate twirling. Learn More … Check…
-
FSU’s Global Summer: A Journey to Remember

“`html Each summer, Florida State University scholars extend their education far beyond the classroom by transcending borders, welcoming new cultures, and engaging in hands-on activities worldwide. From the historic avenues of London to the sun-drenched squares of Valencia and Seville, FSU students utilized their summer to acquire international experiences across Europe, Asia, and further. So,…
-
Ancient Stardust Found in Asteroid Bennu: A Glimpse into the Universe’s Origins

“`html Asteroid Bennu holds stardust that predates the solar system nprevenas Tue, 09/02/2025 – 14:26 Asteroid Bennu holds stardust that predates the solar system Tuesday Article Categories Latest News Science & Tech Outer Space Strategic Goals By Space.com Type of News Article Outsourced News “`
-
Unveiling the Intriguing Composition of Asteroid Bennu: Insights from Recent Research

“`html Recent findings describe substances constituting asteroid Bennu nprevenas Tue, 09/02/2025 – 10:00 Recent findings describe substances constituting asteroid Bennu Tuesday Article Categories Current Affairs Science & Technology Cosmos Key Objectives By KJZZ Type of News Article Outside News “`
-
U of A Students Set to Expand MIA Efforts Following Triumph in Poland

“`html Additional U of A students may participate in MIA search following triumphant mission to Poland nprevenas Tue, 09/02/2025 – 09:30 Additional U of A students may participate in MIA search following triumphant mission to Poland Tuesday Story Categories In the News University News By Arizona Daily Star News Article Type External News “`
-
Arizona University Pioneers Breakthroughs in Clean Fusion Energy

“`html University of Arizona scholars enhance clean fusion energy nprevenas Tue, 09/02/2025 – 09:29 University of Arizona scholars enhance clean fusion energy Tuesday Story Categories Current Affairs Scientific & Technological Strategic Objectives By KVOA Type of News Article Outside News “`