One of the most infamous providers of abuse-permissive “bulletproof” web hosting for cybercriminals has begun routing its operations through systems operated by the Russian antivirus and security company Kaspersky Lab, as reported by KrebsOnSecurity.
Experts in cybersecurity assert that the Russia-based service provider Prospero OOO (the triple O stands for the Russian equivalent of “LLC”) has long served as a persistent source of harmful software, botnet managers, and a myriad of phishing websites. Previously, in the past year, the French security firm Intrinsec detailed the ties between Prospero and bulletproof services promoted on Russian cybercrime forums under the banners Securehost and BEARHOST.

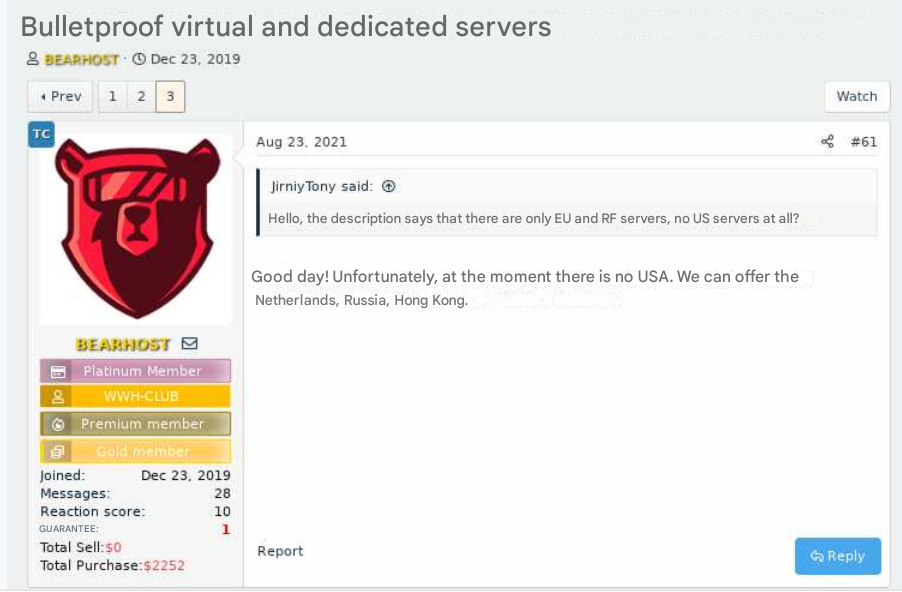
The bulletproof hosting provider BEARHOST. This screenshot has been machine-translated from Russian. Image: Ke-la.com.
Bulletproof hosts receive their name due to their tendency to build a reputation for disregarding legal requests and abuse complaints. BEARHOST has actively nurtured this reputation since at least 2019.
“Should you require a server for a botnet, for malware, brute force attacks, scanning, phishing, counterfeits, or any other purposes, feel free to get in touch with us,” BEARHOST’s advertisement on a forum recommends. “We completely disregard all abuse complaints without exception, including those from SPAMHAUS and similar organizations.”
Intrinsec identified that Prospero has sought relationships with some of Russia’s most notorious cybercrime factions, managing control servers for various ransomware groups over the last two years. Intrinsec’s analysis revealed that Prospero frequently facilitates malware operations like SocGholish and GootLoader, which are primarily disseminated through deceptive browser updates on compromised websites and often pave the way for more severe cyber intrusions — including ransomware incidents.
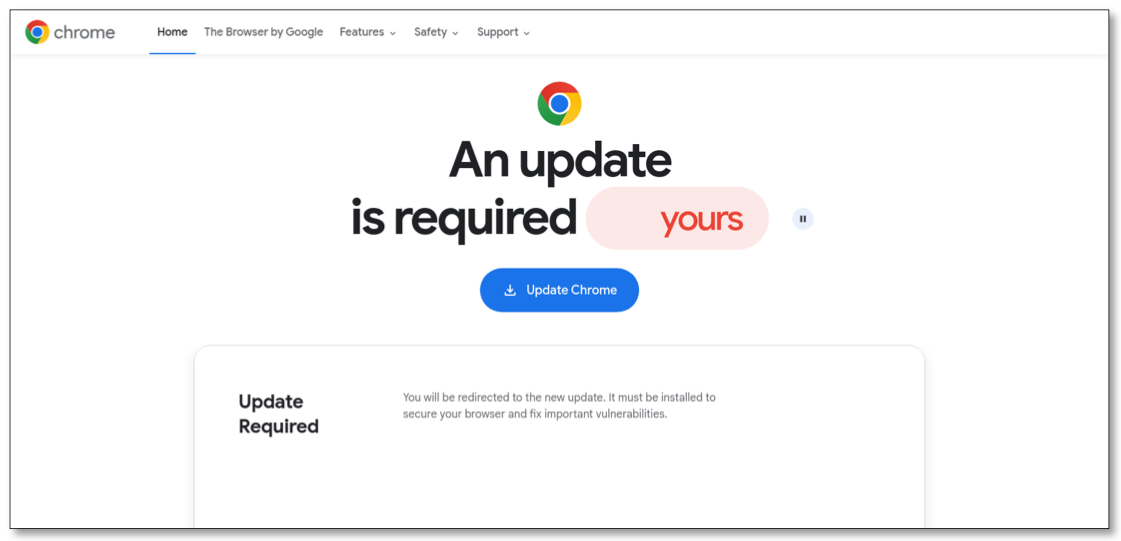
A fraudulent browser update page distributing mobile malware. Image: Intrinsec.
BEARHOST takes pride in its capability to evade blocking by Spamhaus, an organization that numerous Internet service providers globally depend on to identify and eliminate sources of malware and spam. Earlier this week, Spamhaus indicated that it observed that Prospero was unexpectedly connecting to the Internet by routing through networks managed by Kaspersky Lab in Moscow.
Kaspersky did not respond despite multiple requests for comments.
Kaspersky commenced selling antivirus and security software in the United States in 2005, and the company’s malware researchers have received recognition from the security community for many significant findings over the years. However, in September 2017, the Department of Homeland Security (DHS) prohibited U.S. federal agencies from utilizing Kaspersky software, mandating its removal within 90 days.
Cybersecurity journalist Kim Zetter highlights that DHS failed to provide specific reasons for its ban in 2017, yet media reports referencing anonymous government officials cited two incidents. Zetter documented:
One report suggested that an NSA contractor developing offensive hacking tools for the agency had Kaspersky software installed on his personal computer, where he was creating the tools, and that the software flagged the source code as malicious, subsequently extracting it, as antivirus software is designed to do. A second report indicated that Israeli operatives caught Russian government hackers using Kaspersky software to probe customer systems for files containing U.S. secrets.
Kaspersky refuted the claim that anyone utilized its software to seek secret information on customer systems and asserted that the tools on the NSA employee’s machine were flagged in the same manner all antivirus software identifies files it considers suspicious and subsequently quarantines or extracts them for further examination. When Kaspersky recognized that the code detected on the NSA worker’s machine was not harmful software but developmental source code created by the U.S. government for its hacking efforts, CEO Eugene Kaspersky stated he instructed employees to eliminate the code.
Last year, the U.S. Commerce Department prohibited the sale of Kaspersky software in the U.S., effective July 20, 2024. U.S. authorities claimed the prohibition was necessary due to Russian law requiring domestic enterprises to cooperate in all official inquiries, implying that the Russian government could compel Kaspersky to covertly gather intelligence on its behalf.
Phishing statistics compiled last year by the Interisle Consulting Group evaluated hosting networks by their size and concentration of spambot hosts and discovered that Prospero had a significantly higher spam score than any other provider.
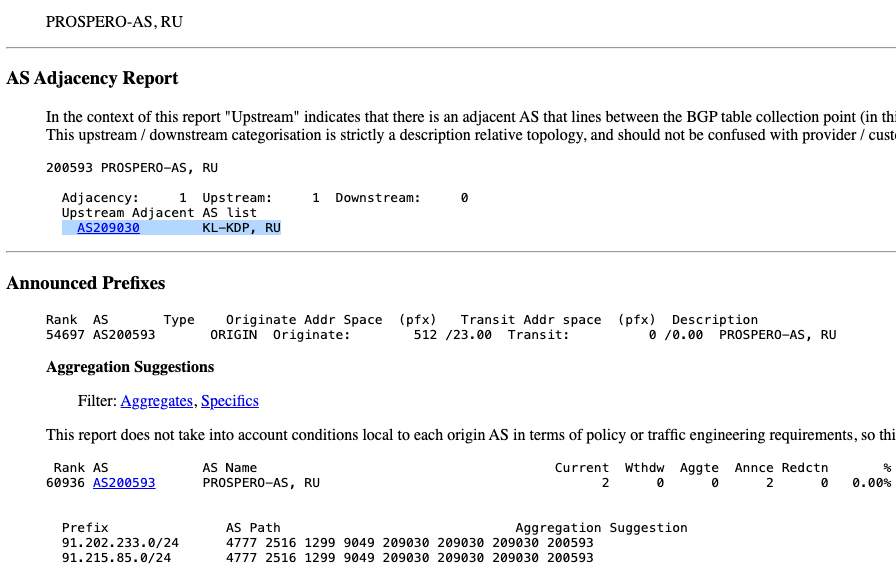
AS209030, owned by Kaspersky Lab, is offering connectivity to the bulletproof host Prospero (AS200593). Image: cidr-report.org.
The reasons behind Kaspersky’s provision of transit to Prospero remain ambiguous. Doug Madory, director of Internet analysis at Kentik, noted that routing records indicate the relationship between Prospero and Kaspersky began at the start of December 2024.
Madory mentioned that Kaspersky’s network seems to be hosting several financial institutions, including Russia’s largest — Alfa-Bank. Kaspersky offers services to assist in protecting clients from distributed denial-of-service (DDoS) attacks and Madory speculated that Prospero might merely be acquiring this protection from Kaspersky.
However, if that is the case, it does not improve the scenario, according to Zach Edwards, a senior threat researcher at the security company Silent Push.
“In certain respects, offering DDoS protection to a well-known bulletproof hosting provider may be even more concerning than merely permitting them to link to the broader Internet using your infrastructure,” Edwards stated.