“`html
Cybercriminal factions disseminating advanced phishing kits that transform pilfered card information into mobile wallets have recently redirected their attention to customer bases of brokerage services, according to fresh investigations. Unfazed by security measures on these trading platforms that prevent users from transferring funds directly from their accounts, the phishers have adjusted their strategies to utilize multiple compromised brokerage accounts simultaneously to influence the prices of international stocks.
Image: Shutterstock, WhataWin.
This so-called ‘ramp and dump‘ tactic derives its name from classic “pump and dump” frauds, in which con artists acquire a substantial quantity of shares in a low-value stock, subsequently promoting the firm through an intense social media campaign to generate interest among other investors. The fraudsters liquidate their shares after the price of the penny stock rises to a certain point, typically resulting in a drastic decline in the worth of the shares for genuine investors.
With ramp and dump, the scammers are not dependent on generating buzz for the stock on social media. Instead, they position themselves within the stock they aim to amplify, using compromised accounts to purchase large amounts and then sell the shares once the stock price hits a predetermined level. In February 2025, the FBI announced it was requesting information from victims of this fraud.
“In this variation, the manipulation of prices primarily stems from controlled trading actions executed by the malicious parties behind the scheme,” reads an advisory from the Financial Industry Regulatory Authority (FINRA), a private, non-profit entity that oversees member brokerage firms. “Ultimately, the result for unsuspecting investors is consistently the same—a devastating collapse in share price that leaves investors with unrecoverable losses.”
Ford Merrill is a cybersecurity researcher at SecAlliance, a CSIS Security Group affiliate. Merrill noted he has traced recent ramp-and-dump practices to a vibrant Chinese-language community that is quite openly marketing sophisticated mobile phishing kits on Telegram.
“They frequently coordinate with other individuals and will wait until a specific time to acquire a certain Chinese IPO [initial public offering] stock or penny stock,” stated Merrill, who has been detailing the rapid evolution and proliferation of the China-based phishing community over the last three years.
“They will utilize all these victim brokerage accounts, and if necessary, they will liquidate the account’s existing positions, while pre-positioning themselves in that asset in an account they control, then sell everything when the price escalates,” he explained. “The victim will be left with devalued shares of that equity in their account, and the brokerage might not be pleased either.”
Merrill noted that the initial stages of these phishing groups—between 2022 and 2024—were characterized by phishing kits that utilized text messages to impersonate the U.S. Postal Service or various local toll road operators, warning of overdue shipping or toll fees that required payment. Recipients who clicked the link and submitted their payment details on a counterfeit USPS or toll operator site were prompted to confirm the transaction by providing a one-time code sent via text.
In reality, the victim’s bank is dispatching that code to the registered mobile number for their customer because the fraudsters have just attempted to enroll that victim’s card details into a mobile wallet. If the individual enters that one-time code, their payment card is then incorporated into a new mobile wallet on an Apple or Google device that is physically managed by the phishers.
The phishing groups typically load multiple stolen cards onto digital wallets on a single Apple or Android device, subsequently selling those phones in bulk to scammers who exploit them for fraudulent e-commerce and tap-to-pay transactions.
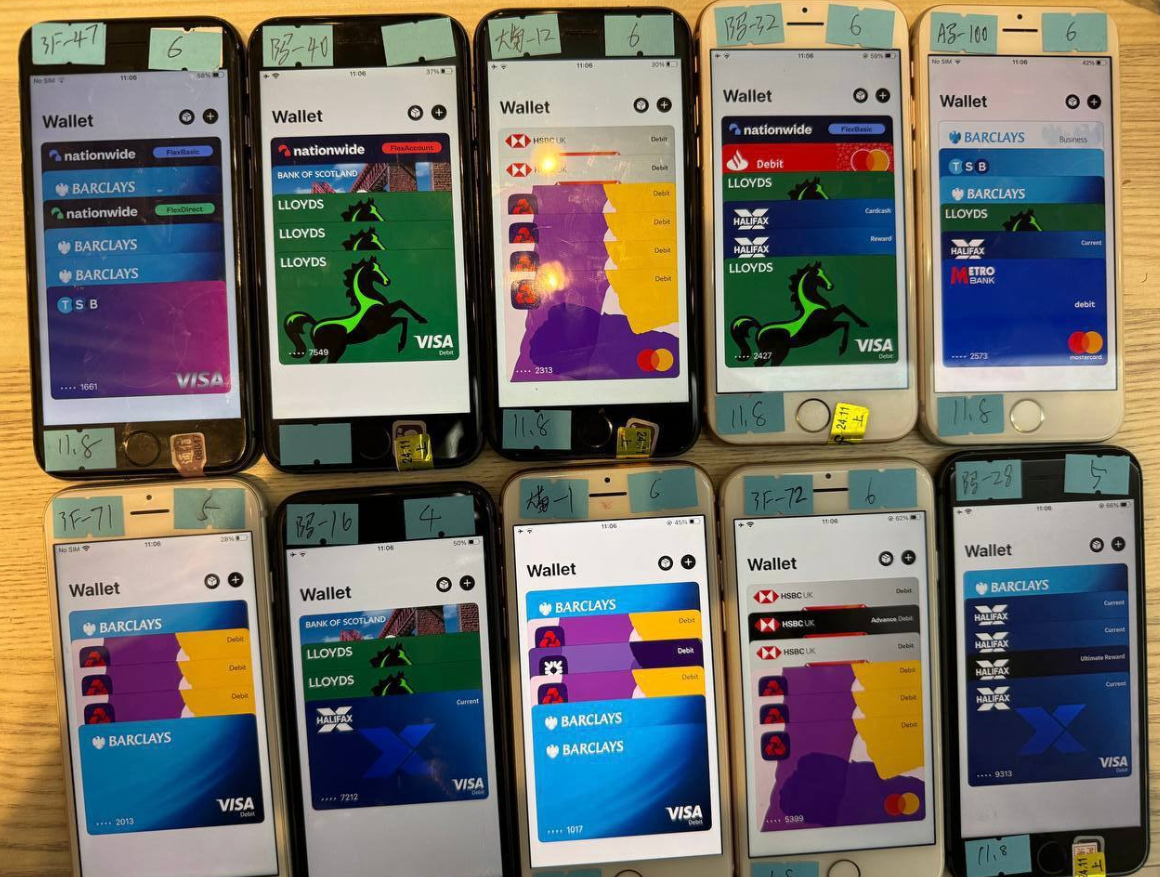
An image from Telegram channel for a well-known Chinese mobile phishing kit vendor displays 10 mobile devices for sale, each equipped with 4-6 digital wallets from various financial institutions.
This China-based phishing collective unveiled a significant vulnerability prevalent among many U.S.-based financial institutions that already implement multi-factor authentication: The dependence on a singular, phishable one-time token for setting up mobile wallets. Fortunately, Merrill remarked that many financial institutions that were caught unprepared by this scheme two years ago have since enhanced authentication requirements for onboarding new mobile wallets (such as necessitating card enrollment via the bank’s mobile app).
However, just as constricting one section of a balloon merely shifts the air contained within to another area, fraudsters do not disappear when their current operations become less lucrative: They simply redirect their focus to a less-protected domain. Recently, that attention has firmly rested on clients of major brokerage platforms, according to Merrill.
THE OUTSIDER
Merrill highlighted several Telegram channels managed by some of the more skilled phishing kit vendors, which are replete with videos illustrating how every feature in their kits can be customized to target specific victims. The video excerpt below is sourced from the Telegram channel of “Outsider,” a popular Mandarin-speaking phishing kit seller whose latest product offers numerous ready-made templates for using text messages to phish brokerage account credentials and one-time codes.
According to Merrill, Outsider is an individual who previously operated under the alias “Chenlun.” KrebsOnSecurity featured Chenlun’s phishing enterprise in an October 2023 article discussing a China-based group that targeted mobile customers of over a dozen postal services worldwide. In that instance, the phishing sites employed a Telegram bot that transmitted stolen credentials to the “@chenlun” Telegram account.
Chenlun’s phishing lures are disseminated through Apple’s iMessage and Google’s RCS service and impersonate one of the major brokerage platforms, warning recipients that their account has been suspended due to suspicious activity and urging them to log in and confirm certain information. The messages contain a link to
“““html
A deceptive webpage that gathers the user’s login credentials and password, and subsequently prompts the individual to input a one-time code that will be sent via SMS.
The latest phishing kit videos on Outsider’s Telegram channel exclusively show templates for Schwab customers, yet Merrill indicated that the kit can be effortlessly modified to target various other brokerage platforms. One reason why scammers focus on brokerage firms, he asserted, relates to the way they manage multi-factor authentication.
Schwab clients are provided with two choices for secondary authentication when they create an account. Users who opt for the setting that only requests a code on untrusted devices can choose to receive it via SMS, an automated incoming call, or an outgoing call to Schwab. By selecting the “always at login” option, clients may receive the code through the Schwab app, a text message, or a Symantec VIP mobile app.
In response to inquiries, Schwab stated that it routinely updates clients about rising fraud trends, including this particular type, which the firm addressed in communications sent to clients earlier this calendar year.
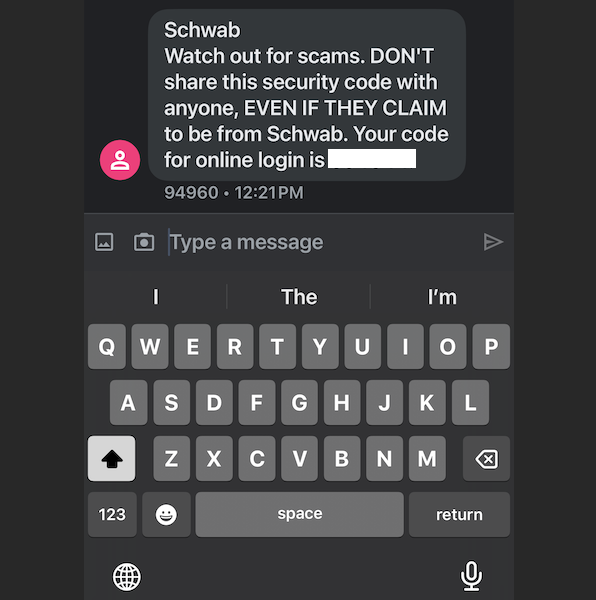
The 2FA text message from Schwab cautions recipients against disclosing their one-time code.
“That communication centered on trading-related fraud, emphasizing both account breaches and schemes conducted via social media or messaging platforms that mislead individuals into performing trades themselves,” Schwab mentioned in a written statement. “We are monitoring and tracking this trend across various channels, along with others that attempt to exploit SMS-based verification utilizing stolen credentials. We continuously observe for questionable patterns and take measures to thwart them. This activity forms part of a wider, industry-wide threat, and we adopt a multi-faceted strategy to address and alleviate it.”
Other prominent brokerage platforms provide similar avenues for multi-factor authentication. Fidelity demands a username and password upon initial login and offers the capability to receive a one-time token via SMS, an automated phone call, or by approving a push notification dispatched through the Fidelity mobile app. Nevertheless, all three of these methods for transmitting one-time tokens are susceptible to phishing; even with the brokerage firm’s app, the fraudsters could urge the user to approve a login request they initiated in the app using the phished credentials.
Vanguard provides customers with various multi-factor authentication options, including the choice to require a physical security key along with one’s credentials at each login. A security key employs a secure form of multi-factor authentication known as Universal 2nd Factor (U2F), allowing the user to finalize the login process simply by connecting an enrolled USB or Bluetooth device and pressing a button. The key operates without the need for any specific software drivers, and a significant benefit is that your second factor cannot be phished.
THE IDEAL CRIME?
Merrill mentioned that in many respects, the ramp-and-dump scheme is the ideal crime because it leaves minimal connections between the victim brokerage accounts and the fraudsters.
“It’s truly ingenious because it separates so many elements,” he commented. “They can purchase shares [in the stock to be inflated] in their personal account on the Chinese exchanges, and the price coincidentally rises. The Chinese or Hong Kong brokerages won’t notice anything unusual.”
Merrill indicated that it’s unclear precisely how those executing these ramp-and-dump schemes coordinate their operations, including whether the accounts are phished well in advance or right before being utilized to elevate the stock price of Chinese firms. The latter scenario would align perfectly with the existing human infrastructure these criminal organizations already have established.
For instance, KrebsOnSecurity recently reported on findings from Merrill and other researchers demonstrating that the phishers behind these sophisticated mobile phishing kits employed individuals to spend hours at a time in front of extensive arrays of mobile phones used to disseminate the text message lures. These technicians were essential for responding in real-time to victims providing the one-time code sent from their financial institution.

The ashtray reads: You’ve been phishing all night.
“You can gain access to a victim’s brokerage with a one-time passcode, but then you should ideally use it immediately if you cannot set new security measures to access that account later,” Merrill noted.
The swift pace of advancements created by these China-based phishing vendors is partly due to their utilization of artificial intelligence and large language models to aid in the development of the mobile phishing kits, he added.
“These individuals are creatively coding together and employing LLMs to translate materials or assist in designing the user interface,” Merrill explained. “It’s only a matter of time before they begin to incorporate the LLMs into their development process to enhance the speed. The technologies they are constructing certainly have contributed to lowering the entry barriers for everyone.”
“`