The financial card behemoth MasterCard has just rectified a significant flaw in its domain name server configurations that could have permitted anyone to intercept or redirect online traffic for the organization by registering a dormant domain name. This misconfiguration remained unaddressed for almost five years until a cybersecurity expert invested $300 to secure the domain and thwart any potential takeover by malicious actors.
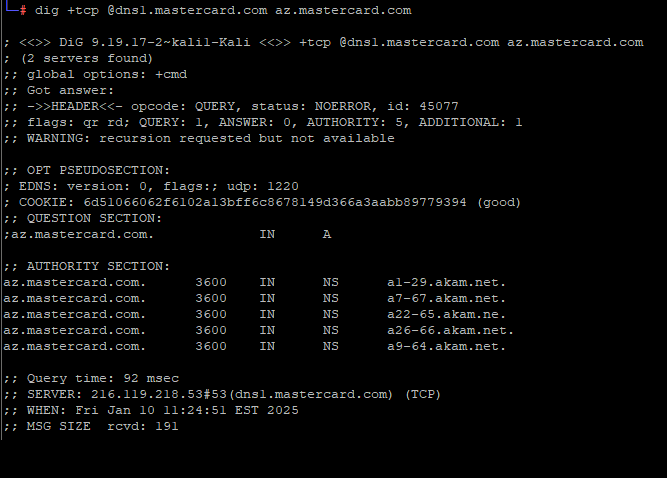
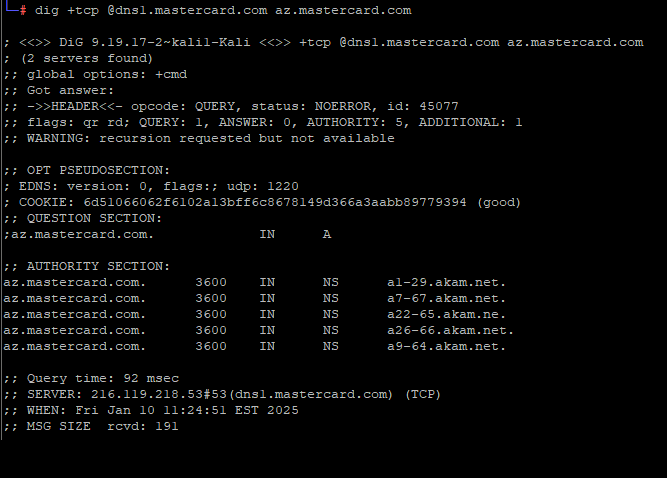
A DNS inquiry for the domain az.mastercard.com on Jan. 14, 2025, reveals the incorrectly typed domain name a22-65.akam.ne.
From June 30, 2020, until January 14, 2025, one of the primary Internet servers that MasterCard utilizes to manage traffic for parts of the mastercard.com network was incorrectly named. MasterCard.com depends on five shared Domain Name System (DNS) servers from the Internet infrastructure provider Akamai [DNS functions as a type of Internet directory, converting website names into numerical Internet addresses which are easier for computers to process].
All of the Akamai DNS server names utilized by MasterCard should conclude with “akam.net”, but one was misconfigured to depend on the domain “akam.ne.”
This minor yet potentially detrimental typographical error was recently identified by Philippe Caturegli, the founder of the cybersecurity consulting firm Seralys. Caturegli speculated that no one had previously registered the domain akam.ne, which falls under the jurisdiction of the top-level domain authority for the West African nation of Niger.
Caturegli mentioned it took $300 and nearly three months of waiting to acquire the domain through the registry in Niger. After activating a DNS server on akam.ne, he observed hundreds of thousands of DNS requests hitting his server daily from various locations worldwide. Evidently, MasterCard wasn’t the exclusive entity that had mistakenly included “akam.ne” in their DNS entry, although they were by far the most substantial.
If he had set up an email server on his newly acquired domain akam.ne, Caturegli would likely have received misrouted emails intended for mastercard.com or other related domains. Should he have exploited his access, he might have been able to obtain website encryption certificates (SSL/TLS certs) authorized to accept and relay web traffic for the impacted sites. He may have even been capable of passively receiving Microsoft Windows authentication credentials from employee systems at the affected companies.
However, the researcher stated he refrained from doing any of that. Instead, he informed MasterCard that the domain belonged to them if they wished to claim it, copying this author in his communications. A few hours later, MasterCard admitted to the error but asserted that there had been no genuine threat to the integrity of its operations.
“We have investigated the situation, and there was no risk to our systems,” a MasterCard spokesperson stated. “This error has now been amended.”
In the meantime, Caturegli received a communication through Bugcrowd, a platform that offers financial incentives and acknowledgment to cybersecurity researchers who uncover vulnerabilities and work discreetly with the affected vendor to rectify them. The message indicated that his public revelation of the MasterCard DNS mistake via a post on LinkedIn (after he secured the akam.ne domain) was not consistent with ethical security practices, and relayed a request from MasterCard to have the post removed.
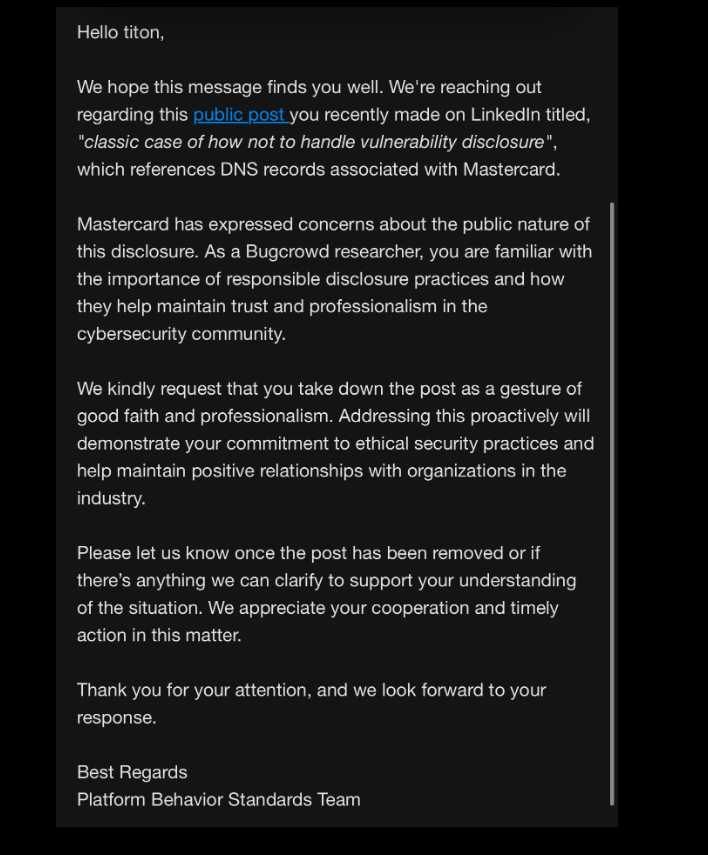
MasterCard’s request to Caturegli, a.k.a. “Titon” on infosec.exchange.
Caturegli stated that while he does have an account on Bugcrowd, he has never reported anything through their program and directly contacted MasterCard regarding this issue.
“I did not disclose this problem via Bugcrowd,” Caturegli responded. “Prior to making any public announcement, I ensured that the affected domain was registered to avert exploitation, thus reducing any risk to MasterCard or its clients. This step, which we executed at our own cost, reflects our dedication to ethical security standards and responsible disclosure.”
Most organizations maintain at least two authoritative domain name servers, but some manage so many DNS inquiries that they require additional DNS server domains to distribute the load. In the case of MasterCard, that number is five, so it follows that if an attacker managed to gain control of just one of those domains, they would only be able to access about one-fifth of the total DNS requests received.
However, Caturegli remarked that many Internet users tend to rely, at least in part, on public traffic forwarders or DNS resolvers such as Cloudflare and Google.
“All it takes is for any of these resolvers to query our name server and cache the outcome,” Caturegli noted. By configuring their DNS server records with a lengthy TTL or “Time To Live”—a setting that can modify the longevity of data packets on a network—an attacker’s corrupted instructions for the targeted domain can be disseminated by major cloud providers.
“With an extended TTL, we could redirect a LOT more than just 1/5 of the traffic,” he emphasized.
The researcher expressed hope that the credit card giant might express gratitude, or at least offer to reimburse the expenses incurred in purchasing the domain.
“We clearly dispute this evaluation,” Caturegli stated in a follow-up update on LinkedIn regarding MasterCard’s public statement. “But we’ll allow you to determine— here are some of the DNS inquiries we recorded before reporting the problem.”
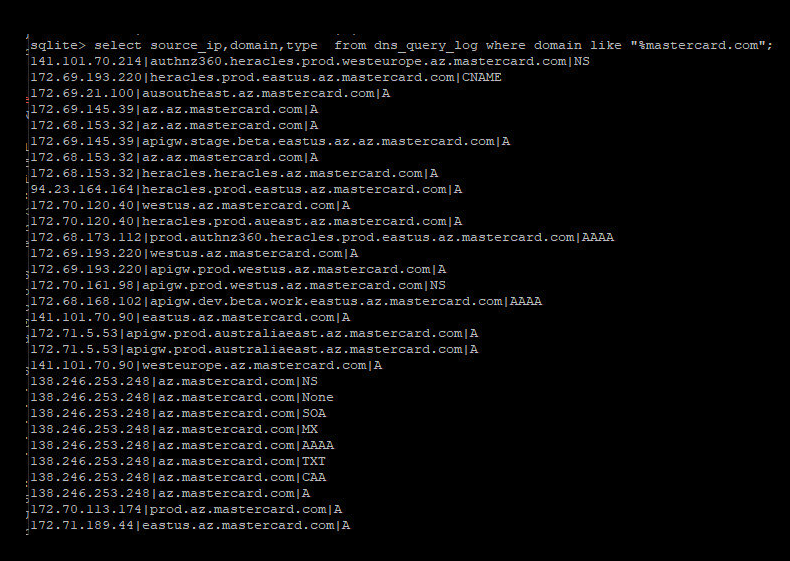
Caturegli shared this screenshot of MasterCard domains that were potentially endangered due to the misconfigured domain.
As depicted in the screenshot above, the misconfigured DNS server that Caturegli uncovered involved the MasterCard subdomain az.mastercard.com. It’s unclear exactly how this subdomain is utilized by MasterCard; however, their naming conventions imply that the domains correspond to production servers within Microsoft’s Azure cloud services. Caturegli mentioned that all domains resolve to Internet addresses associated with Microsoft.
“Don’t emulate Mastercard,” Caturegli concluded in his LinkedIn post. “Don’t underestimate risk, and don’t leave your marketing department in charge of security disclosures.”
Lastly, it’s noteworthy that the domain akam.ne has been registered before— in December 2016 by an individual using the email address [email protected]. The Russian search engine giant Yandex identifies this user account as belonging to an “Ivan I.” from Moscow. Passive DNS records from DomainTools.com indicate that between 2016 and 2018, the domain was associated with an Internet server in Germany, and that the domain was allowed to lapse in 2018.
This is intriguing considering a comment by an ex-Cloudflare employee on Caturegli’s LinkedIn post who referenced a report he co-authored regarding a similar typographical domain error seemingly registered in 2017 for organizations that might have mistyped their AWS DNS server as “awsdns-06.ne” instead of “awsdns-06.net.” DomainTools reports that this misregistered domain was also linked to a Yandex user ([email protected]) and hosted by the same German Internet service provider — Team Internet (AS61969).