“`html
KrebsOnSecurity encountered a nearly record-setting distributed denial-of-service (DDoS) assault last week, registering over 6.3 terabits of data per second (with a terabit equating to one trillion bits). This swift attack appears to have functioned as a test for an expansive new Internet of Things (IoT) botnet, capable of initiating debilitating digital strikes that few online locations can endure. Continue reading for further insights regarding the botnet, the attack, and the presumed architect of this international threat.
As a point of comparison, the 6.3 Tbps assault from last week was tenfold the magnitude of the attack on this site in 2016 by the Mirai IoT botnet, which kept KrebsOnSecurity offline for close to four days. The 2016 strike was so significant that Akamai – which was providing pro bono DDoS protection to KrebsOnSecurity at that time — requested I terminate their service due to the issue it was causing for their paying clientele.
Following the Mirai strike, KrebsOnSecurity.com has benefited from the safeguarding of Project Shield, a complimentary DDoS defense initiative offered by Google subsidiary Jigsaw for websites engrossed in news, human rights, and electoral subjects. Google Security Engineer Damian Menscher informed KrebsOnSecurity that the May 12 strike represented the most extensive that Google has managed. In terms of sheer scale, it is outpaced only by a very parallel strike that Cloudflare addressed and discussed in April.
Upon reviewing information with Cloudflare, Menscher mentioned that the botnet responsible for both attacks exhibits the characteristics of Aisuru, a digital siege apparatus that emerged less than a year ago. Menscher noted that the attack on KrebsOnSecurity was brief, lasting under a minute, and bombarded massive UDP data packets at random ports at a frequency of approximately 585 million packets per second.
“This was the kind of attack usually devised to inundate network connections,” Menscher stated, alluding to the throughput connections between various Internet service providers (ISPs). “For most organizations, this level of attack would be catastrophic.”
The Aisuru botnet consists of a worldwide assortment of compromised IoT devices, including routers, digital video recorders, and additional systems hijacked via default passwords or software weaknesses. As noted by researchers at QiAnXin XLab, this botnet was initially recognized during an August 2024 attack on a major gaming platform.
Aisuru reportedly became inactive following that initial detection, only to resurface in November with even greater capabilities and software exploits. In a January 2025 report, XLab revealed that the revamped Aisuru (also known as “Airashi”) incorporated a previously unidentified zero-day vulnerability affecting Cambium Networks cnPilot routers.
NOT FORKING AROUND
The individuals behind the Aisuru botnet have been offering access to their DDoS apparatus in open Telegram chat groups that are under constant surveillance by several security organizations. In August 2024, access to the botnet was offered on a subscription basis, with prices ranging from $150 per day to $600 per week, providing attacks of up to two terabits per second.
“You are prohibited from targeting measurement walls, healthcare institutions, educational facilities, or government sites,” stated a notice posted on Telegram by the Aisuru botnet owners in August 2024.
Those interested were instructed to reach out to the Telegram username “@yfork” to secure a subscription. The account @yfork had previously used the alias “Forky,” an identity linked to posts in public DDoS-centric Telegram groups since 2021.
As per the FBI, Forky’s DDoS-for-hire domains have been confiscated in several law enforcement actions over the years. Last year, Forky indicated on Telegram that he was selling the domain stresser[.]best, which had its servers seized by the FBI in 2022 as part of an ongoing global law enforcement initiative seeking to reduce both the availability and demand for DDoS-for-hire services.
“The operator of this service, who goes by ‘Forky,’ runs a Telegram channel to showcase features and engage with current and potential DDoS clientele,” states an FBI seizure warrant (PDF) issued for stresser[.]best. The FBI warrant mentioned that on the day the seizures were publicized, Forky shared a link to a post on this blog detailing the domain seizure action, adding the remark, “We are procuring our new domains right now.”
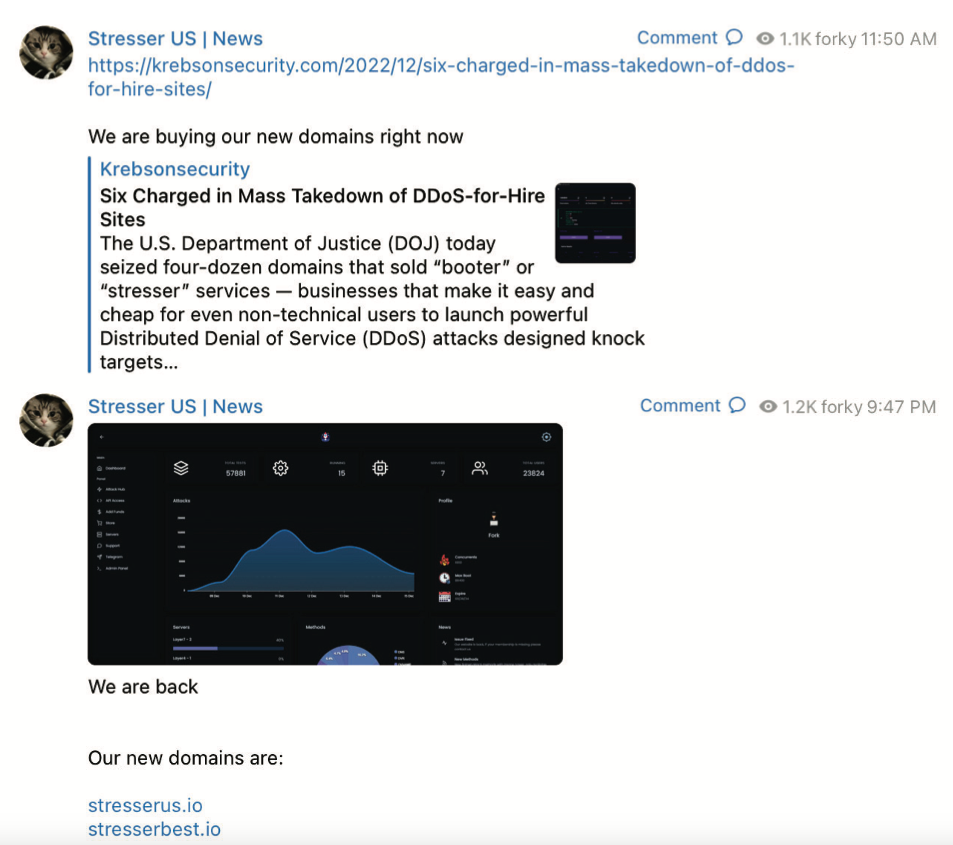
A snapshot from the FBI’s seizure warrant for Forky’s DDoS-for-hire domains reveals Forky announcing the revival of their service at new domains.
Roughly ten hours later, Forky posted again, including a screenshot of the stresser[.]best user interface, directing clients to use their preserved passwords for the old site on the new one.
An analysis of Forky’s contributions to public Telegram groups — as archived by cyber intelligence firms Unit 221B and Flashpoint — indicates that a 21-year-old individual claims to reside in Brazil [full disclosure: Flashpoint is presently an advertiser on this blog].
Since late 2022, Forky’s posts have consistently promoted a DDoS mitigation business and ISP he operates known as botshield[.]io. The Botshield website is linked to a registered business entity in the United Kingdom titled Botshield LTD, which lists a 21-year-old woman from Sao Paulo, Brazil as its director. Internet routing records show that Botshield (AS213613) currently manages several hundred Internet addresses allocated to the company earlier.
“““html
this year.
Domaintools.com states that botshield[.]io was registered in July 2022 to a Kaike Southier Leite located in Sao Paulo. A LinkedIn profile associated with this name indicates that this person is a network expert from Brazil engaged in “the design and execution of resilient network infrastructures, concentrating on security, DDoS countermeasures, colocation, and cloud server offerings.”
INTRODUCING FORKY

Image: Jaclyn Vernace / Shutterstock.com.
In his communications to public Telegram channels, Forky has scarcely made an effort to mask his location or identity. In numerous chat exchanges cataloged by Unit 221B, Forky was observed discussing daily life in Brazil, frequently commenting on the notably low or high prices for various commodities, ranging from computer and networking equipment to drugs and food.
Contacted via Telegram, Forky asserted he had “not participated in this type of illegal activities for years,” and mentioned that the project had been taken over by different unnamed developers. Initially, Forky told KrebsOnSecurity that he had exited the botnet landscape for years but later admitted this was inaccurate when confronted with public posts on Telegram from late last year that clearly contradicted his claim.
Forky refuted any involvement in the assault on KrebsOnSecurity but conceded that he contributed to developing and promoting the Aisuru botnet. He claims that he now merely holds a position within the Aisuru botnet team, stating that he ceased operating the botnet about two months ago after starting a family. Forky also mentioned that the individual identified as the director of Botshield is related to him.
Forky provided ambiguous and evasive answers to several inquiries regarding the Aisuru botnet and his business activities. However, he was unmistakably clear on one point:
“I hold no fear regarding you, the FBI, or Interpol,” Forky stated, claiming that he is now largely focused on their hosting enterprise — Botshield.
Forky opted not to detail the composition of his ISP’s clientele or to clarify whether Botshield functioned more as a hosting provider or a DDoS mitigation entity. However, Forky has shared on Telegram about Botshield effectively mitigating significant DDoS attacks targeted at other DDoS-for-hire services.
DomainTools discovery reveals that the same Sao Paulo street address recorded for botshield[.]io was utilized to register several other domains, including cant-mitigate[.]us. The email address in the WHOIS records for that domain is [email protected], which DomainTools indicates was employed to register the domain for the now-defunct DDoS-for-hire service stresser[.]us, one of the domains confiscated in the FBI’s 2023 crackdown.
On May 8, 2023, the U.S. Department of Justice announced the confiscation of stresser[.]us, alongside a dozen more domains supplying DDoS services. The DOJ reported that ten of the 13 domains were facsimiles of services that had been seized during a prior raid in December, which focused on 48 leading stresser services (commonly referred to as “booters”).
Forky claimed he could determine who targeted my site using Aisuru. But when pressed a day later, he reported coming up empty.
“I made inquiries, but all the major players aren’t foolish enough to attack you,” Forky elucidated in a Telegram interview. “I had no involvement in it. However, you are more than welcome to write the story and attempt to place the blame on me.”
THE PHANTOM OF MIRAI
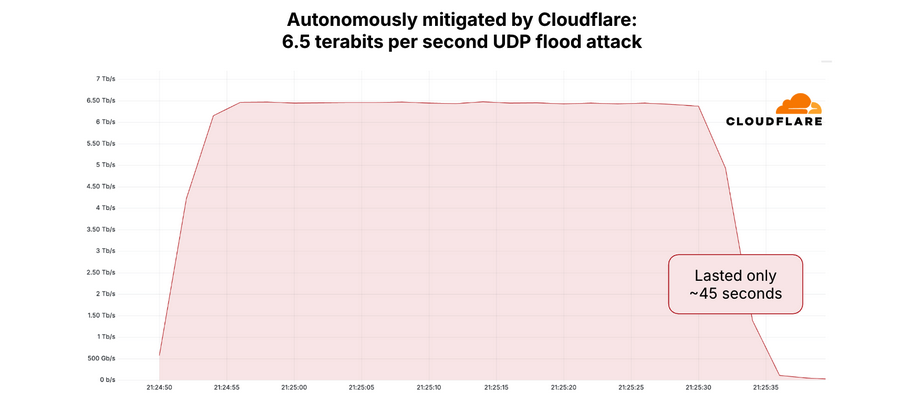
The 6.3 Tbps attack that occurred last week caused no discernible disruption to this site, partly due to its brevity — lasting around 45 seconds. DDoS attacks of such scale and fleeting nature are typically executed when botnet operators intend to test or showcase their power for prospective buyers. In fact, Google’s Menscher noted that both the May 12 assault and the slightly larger 6.5 Tbps attack against Cloudflare last month were probably tests of the same botnet’s capabilities.
In many respects, the threat presented by the Aisuru/Airashi botnet mirrors that of Mirai, a groundbreaking IoT malware strain that surfaced in the summer of 2016 and successfully surpassed nearly all other existing IoT malware strains at that time.
As first disclosed by KrebsOnSecurity in January 2017, the creators of Mirai were two men from the U.S. who co-managed a DDoS mitigation service — even while they were marketing much more profitable DDoS-for-hire services using the most formidable botnet on the planet.
Less than a week after the Mirai botnet was deployed in a prolonged DDoS against KrebsOnSecurity, the Mirai creators released the source code for their botnet to ensure that they would not be the sole possessors of it in case of their arrest by federal investigators.
Ironically, the dissemination of the Mirai source is precisely what ultimately led to the identification and arrest of its creators, who subsequently served probation sentences that mandated them to collaborate with FBI agents on DDoS investigations. However, that leak also rapidly resulted in the emergence of numerous Mirai botnet replicas, many of which were exploited to fuel their own potent DDoS-for-hire operations.
Menscher informed KrebsOnSecurity that, paradoxically, the Internet as a whole would likely benefit if the source code for Aisuru became publicly available. After all, he commented, the individuals behind Aisuru are in relentless competition with other IoT botnet operators who are all striving to seize a limited number of vulnerable IoT devices globally.
Such an occurrence would almost certainly lead to an increase of Aisuru botnet clones, he stated, but at least it would ensure that the overall firepower from each individual botnet would be substantially reduced — or at least within the range of mitigation capabilities of most DDoS protection providers.
In the absence of a source code leak, Menscher expressed hope that someone would publish the full list of software vulnerabilities being exploited by the Aisuru operators to expand their botnet so swiftly.
“A significant part of the reason Mirai was so hazardous was that it effectively eradicated competing botnets,” he mentioned. “This attack somehow succeeded in compromising all these devices that others are unaware of. Ideally, we’d prefer to see that fragmented out, ensuring that no [individual botnet operator] possesses too much power.”
“`