“`html
Late in the previous year, cybersecurity analysts uncovered a shocking revelation: Kremlin-supported misinformation operations were evading oversight on social media networks by utilizing the same harmful advertising technology that fuels a vast landscape of online con artists and website infiltrators. A recent report on the aftermath of that inquiry reveals this shadowy ad tech sector is considerably more robust and interconnected than previously understood.
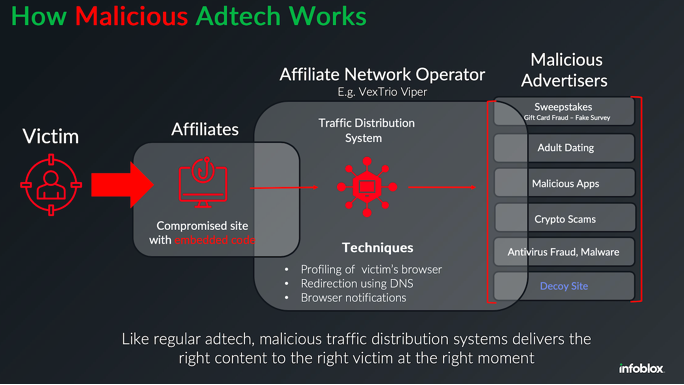
Image: Infoblox.
In November 2024, investigators from the security organization Qurium released an analysis of “Doppelganger,” a misinformation network that disseminates pro-Russian themes and permeates Europe’s media realm by propagating false news through a network of replicated websites.
Doppelganger initiatives utilize specific links that route the user’s browser through an extensive series of domains before the phony news content is displayed. Qurium discovered that Doppelganger depends on an advanced “domain cloaking” service, a technology that permits websites to show varied content to search engines compared to what typical visitors observe. The implementation of cloaking services enables the misinformation sites to remain online for extended periods, ensuring that only the intended audience views the curated content.
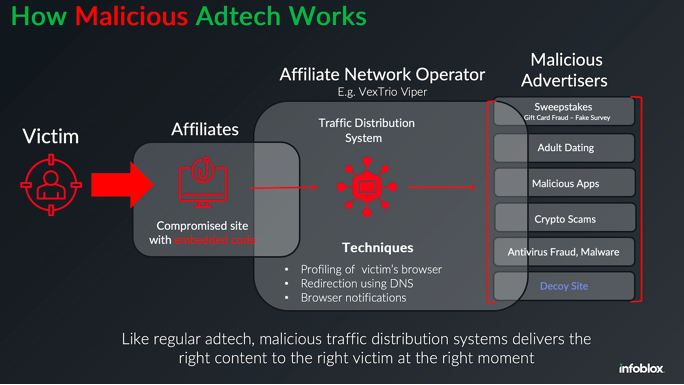
Qurium found that Doppelganger’s cloaking service also endorsed online dating platforms and shared considerable infrastructure with VexTrio, believed to be the oldest malicious traffic distribution system (TDS) currently operational. While TDSs are frequently employed by legitimate advertising networks to manage traffic from diverse sources and to monitor who or what is causing each click, VexTrio’s TDS primarily oversees web traffic from individuals victimized by phishing, malware, and social engineering frauds.
BREAKING BAD
Upon further investigation, Qurium identified that Doppelganger’s cloaking service utilized an Internet provider in Switzerland as the initial entry point in a sequence of domain redirections. They also observed that the same infrastructure supported a couple of co-branded affiliate marketing services that were funneling traffic to dubious adult dating sites: LosPollos[.]com and TacoLoco[.]co.
The LosPollos advertising network integrates numerous elements and allusions from the popular HBO series “Breaking Bad,” reflecting the fictional “Los Pollos Hermanos” restaurant franchise that functioned as a money laundering scheme for a dangerous methamphetamine cartel.
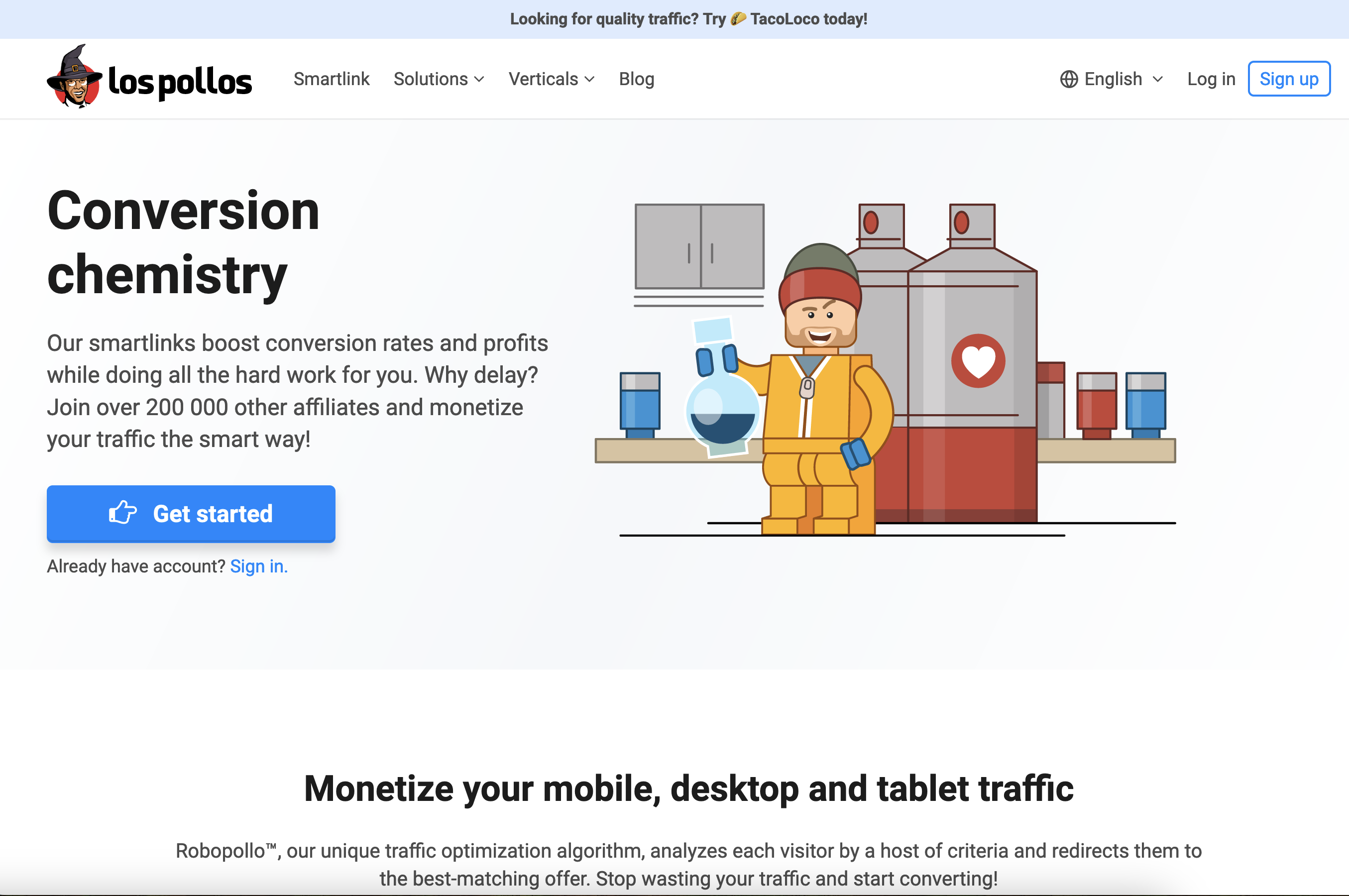
The LosPollos advertising network draws from characters and themes featured in the popular show Breaking Bad. The logo for LosPollos (top left) depicts Gustavo Fring, the fictional proprietor of the restaurant chain in the series.
Affiliates who enlist with LosPollos are provided with JavaScript-intensive “smartlinks” that guide traffic into the VexTrio TDS, which subsequently diverts the traffic among various advertising partners, including dating platforms, sweepstake opportunities, deceptive mobile applications, financial scams, and sites for malware downloads.
LosPollos affiliates commonly embed these smart links into WordPress sites that have been compromised through known vulnerabilities, and those affiliates earn a minor commission each time an Internet user redirected from their hacked sites falls for one of these traps.
The Los Pollos advertising network advertising itself on LinkedIn.
As per Qurium, TacoLoco functions as a traffic monetization network that utilizes misleading strategies to deceive Internet users into permitting “push notifications,” a cross-platform browser standard that facilitates websites in displaying pop-up alerts outside of the browser environment. For instance, on Microsoft Windows systems, these notifications generally appear in the lower right corner of the display — just above the system clock.
In the case of VexTrio and TacoLoco, the requests for notification authorizations are misleading — masquerading as “CAPTCHA” challenges intended to differentiate between automated bot traffic and real users. For numerous years, VexTrio and its affiliates have effectively duped countless individuals into permitting these site notifications, which are then employed to incessantly bombard the user’s device with various false virus warnings and misleading pop-up alerts.
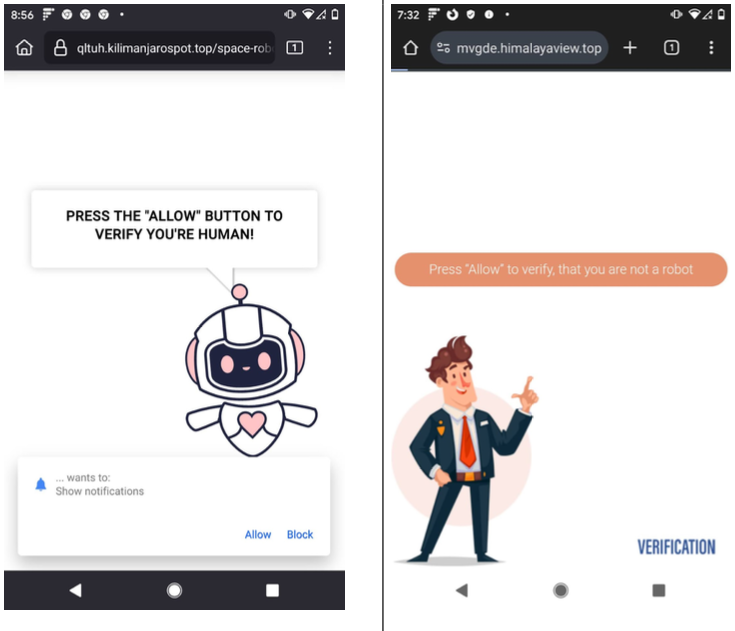
Instances of VexTrio landing pages persuading users to accept push notifications on their device.
According to a December 2024 annual report from GoDaddy, almost 40 percent of compromised websites in 2024 redirected visitors to VexTrio through LosPollos smartlinks.
ADSPRO AND TEKNOLOGY
On November 14, 2024, Qurium released findings to corroborate its conclusions that LosPollos and TacoLoco were services operated by Adspro Group, a business registered in the Czech Republic and Russia, and that Adspro manages its infrastructure at the Swiss hosting providers C41 and Teknology SA.
Qurium highlighted that both the LosPollos and TacoLoco websites claim their content is copyrighted by ByteCore AG and SkyForge Digital AG, two Swiss entities headed by the owner of Teknology SA, Guilio Vitorrio Leonardo Cerutti. Further probing unveiled that LosPollos and TacoLoco were applications developed by a firm named Holacode, which lists Cerutti as its CEO.
The applications promoted by Holacode consist of several VPN services, alongside one called Spamshield, which asserts it blocks unwanted push notifications. However, in January, Infoblox claimed they tested the app on their own mobile devices and found that it conceals the user’s notifications, only to stop hiding them after 24 hours and subsequently demands payment. Spamshield later altered its developer name from Holacode to ApLabz, although Infoblox pointed out that the Terms of Service for multiple rebranded ApLabz apps continued to reference Holacode in their service agreements.
Remarkably, Cerutti threatened to sue me for libel before I had even made a statement.
“““html
his designation or sent him a request for feedback (Cerutti returned the unsolicited legal threat back in January after his enterprise and my name were simply tagged in an Infoblox post on LinkedIn regarding VexTrio).
When prompted for a response about the revelations by Qurium and Infoblox, Cerutti firmly rejected any association with VexTrio. Cerutti maintained that his businesses strictly follow the laws of the nations in which they operate and that they have been entirely open about all of their activities.
“We are a collective functioning within the advertising and marketing sector, with an affiliate network program,” Cerutti replied. “I am not [going] to claim we are flawless, but I emphatically state we have no ties to VexTrio whatsoever.”
“Regrettably, as a significant player in this realm, we also encounter a multitude of publisher fraud, dubious traffic, fraudulent clicks, bots, hacked, listed, and resold publisher accounts, etc., etc.,” Cerutti elaborated. “We incur substantial financial losses from such misconduct and conduct regular internal evaluations and audits in a persistent struggle to eliminate harmful traffic sources. It is also a fiercely competitive arena, where some newcomers often resort to underhanded tactics against more established mainstream participants like us.”
Collaborating with Qurium, specialists at the security firm Infoblox disclosed information regarding VexTrio’s infrastructure to their industry collaborators. Merely four days after Qurium made its findings public, LosPollos declared it was halting its push monetization service. Less than a month after that, Adspro had rebranded to Aimed Global.
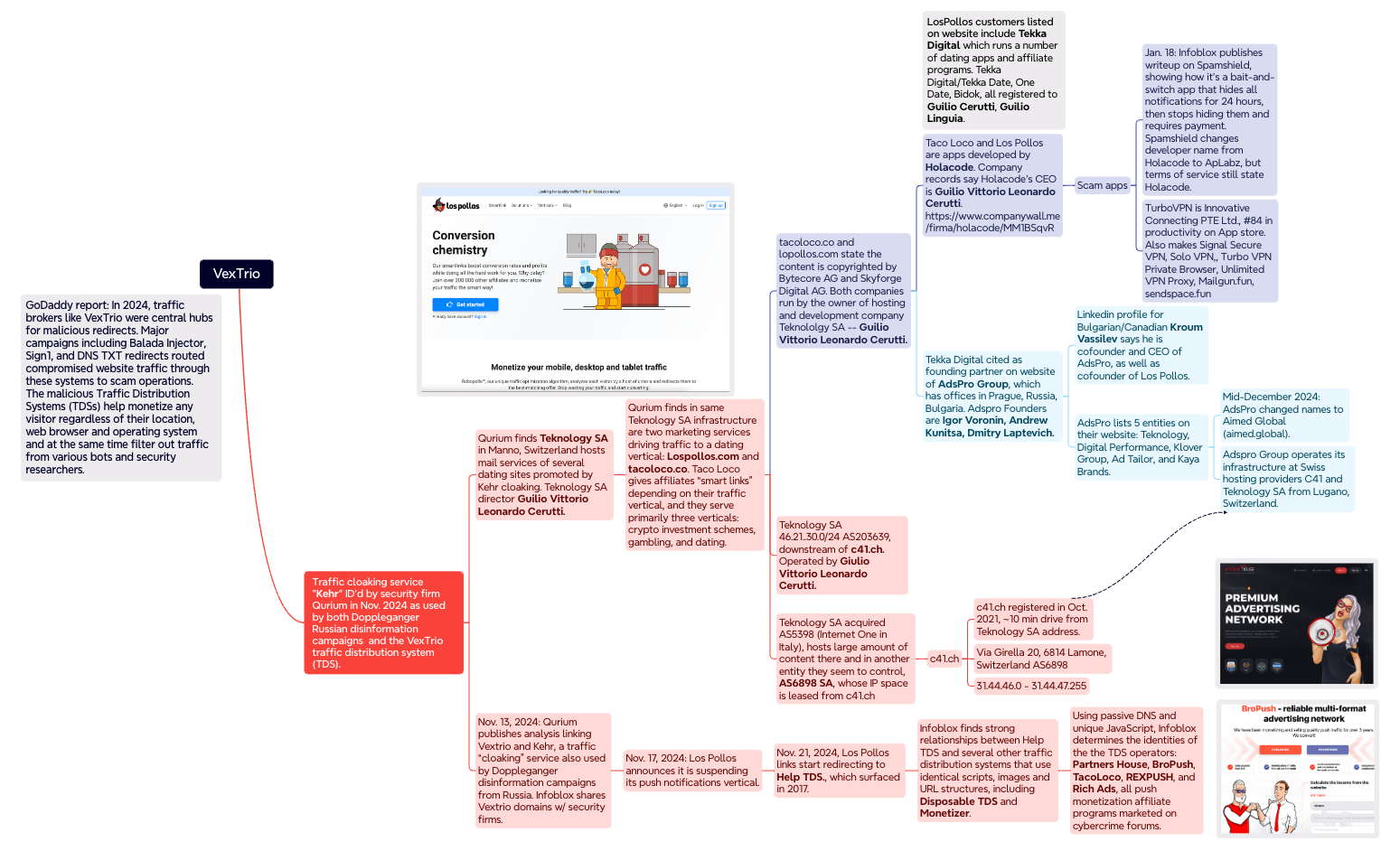
A mind map depicting some key revelations and connections in the Infoblox and Qurium investigations. Click to enlarge.
A REVEALING TURN
In March 2025, analysts at GoDaddy documented how DollyWay — a malware variant that has persistently redirected victims to VexTrio over its eight years of existence — abruptly ceased doing so on November 20, 2024. Almost overnight, DollyWay and several other malware families that had previously utilized VexTrio began channeling their traffic through another TDS known as Help TDS.
Diving deeper into historical DNS records and the unique code scripts employed by the Help TDS, Infoblox established that it has for a long time maintained an exclusive relationship with VexTrio (at least until LosPollos discontinued its push monetization service in November).
In a report released today, Infoblox stated that a thorough investigation of the JavaScript code, website lures, smartlinks, and DNS patterns utilized by VexTrio and Help TDS connected them with at least four additional TDS operators (not including TacoLoco). Those four entities — Partners House, BroPush, RichAds, and RexPush — are all Russia-based push monetization programs that compensate affiliates to drive signups for various schemes, primarily online dating services.
“As Los Pollos’ push monetization concluded, we’ve observed a rise in fake CAPTCHAs that promote user acceptance of push notifications, chiefly from Partners House,” the Infoblox report states. “The relationship among these commercial entities remains enigmatic; while they certainly are long-time partners directing traffic to one another and all possess a Russian connection, there is no obvious common ownership.”
Renee Burton, vice president of threat intelligence at Infoblox, indicated that the security community generally assumes the deceptive tactics employed by VexTrio and other harmful TDSs as a kind of legally ambiguous zone that is mostly linked with less severe security threats, such as adware and scareware.
However, Burton contends that this perspective is shortsighted and aids in sustaining a dark adtech industry that also proliferates a significant amount of outright malware, noting that hundreds of thousands of compromised websites globally redirect victims to the convoluted network of VexTrio and its affiliate TDSs.
“These TDSs represent a malign threat, as they are the ones intertwined with the delivery of items like information stealers and scams that cost consumers billions of dollars annually,” Burton stated. “From a broader strategic standpoint, my conclusion is that Russian organized crime has dominion over malicious adtech, and these are merely a few of the numerous groups involved.”
WHAT CAN YOU DO?
As KrebsOnSecurity cautioned back in 2020, it’s advisable to be very selective in granting notifications while navigating the Web. In numerous instances, these notifications are benign, but as we’ve observed, there are many questionable firms compensating site owners to implement their notification scripts and then reselling that communication pathway to fraudsters and online scams.
If you want to prevent sites from ever displaying notification requests, all major browser developers allow you to accomplish this — whether universally or on a site-by-site basis. While entirely blocking notifications might disrupt the functionality of some websites, implementing this for any devices you manage on behalf of your less tech-savvy friends or family can ultimately save everyone a great deal of trouble down the line.
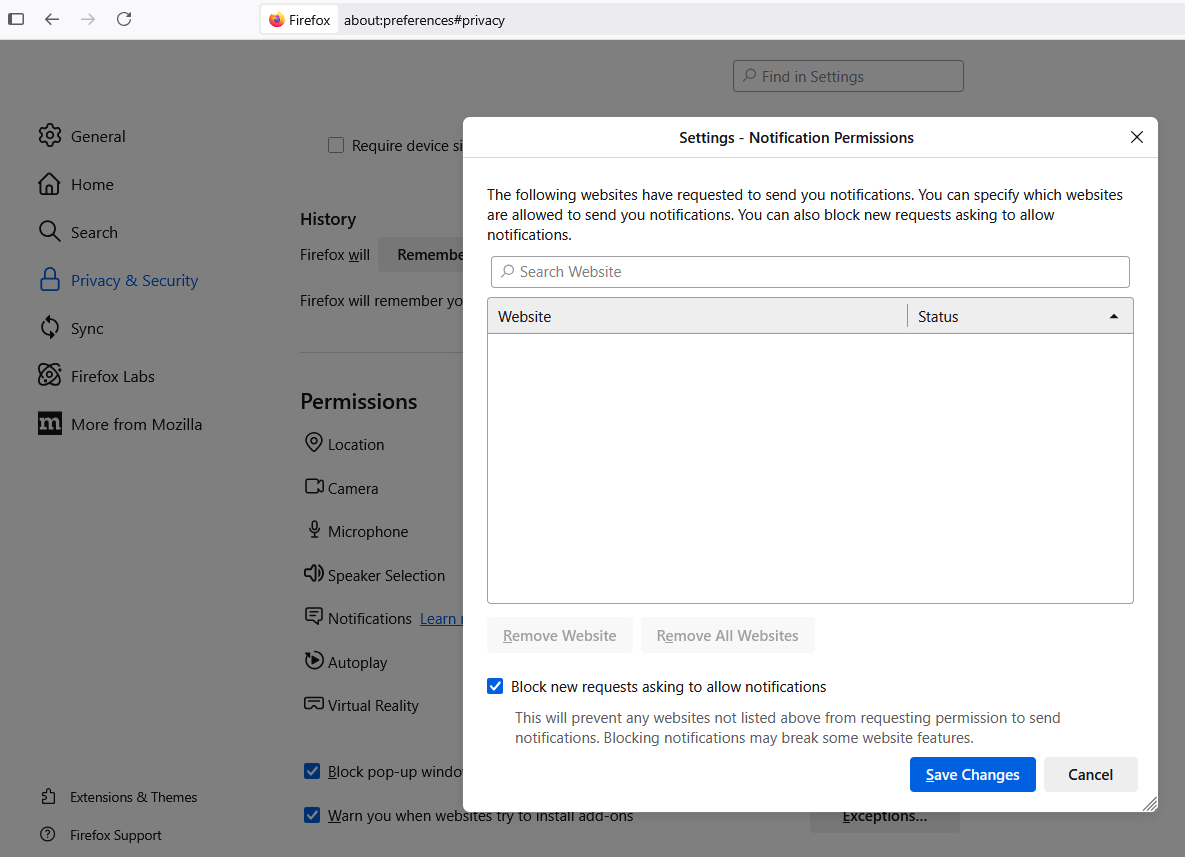
To modify site notification preferences in Mozilla Firefox, go to Settings, Privacy & Security, Permissions, and click the “Settings” tab next to “Notifications.” This page will showcase any notifications already permitted and enable you to edit or remove any entries. Check the box next to “Block new requests asking to allow notifications” to eliminate them entirely.
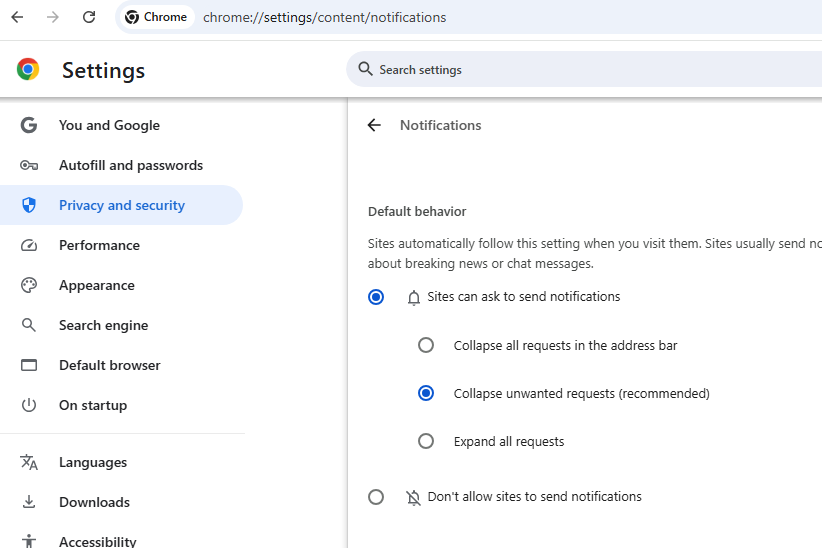
In Google Chrome, click the icon with the three dots located to the right of the address bar, scroll down to Settings, Privacy, and Security, Site Settings, and Notifications. Select the “Don’t allow sites to send notifications” option if you wish to ban notification requests indefinitely.
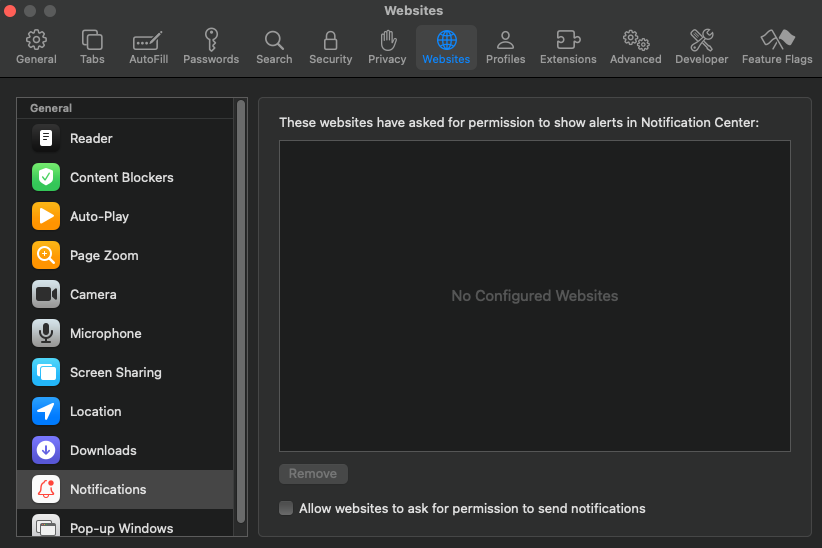
In Apple’s Safari browser, navigate to Settings, Websites, and click on Notifications in the sidebar. Uncheck the option to “allow websites to request permission to send notifications” if you wish to completely disable notification requests.
“`