“`html

Image: Shutterstock, ArtHead.
In a bid to assimilate and render their nefarious activities harder to obstruct, hosting companies serving cybercriminals in China and Russia are increasingly routing their operations through prominent U.S. cloud services. A study released this week on one such organization — a vast web associated with Chinese organized crime factions and aptly named “Funnull” — sheds light on a recurring whac-a-mole challenge facing cloud providers.
In October 2024, the cybersecurity firm Silent Push published a comprehensive report detailing how Amazon AWS and Microsoft Azure were rendering services to Funnull, a two-year-old Chinese content delivery network hosting an array of fraudulent trading applications, pig butchering scams, gambling sites, and phishing retail pages.
Funnull garnered attention last summer following its acquisition of the domain name polyfill[.]io, which was formerly the home of a widely-used open-source code library enabling older browsers to execute advanced functions lacking native support. At the time of its acquisition, several legitimate domains were still connected to the Polyfill domain, and Funnull subsequently executed a supply-chain assault that redirected visitors to nefarious sites.
Silent Push’s October 2024 analysis uncovered a plethora of domains hosted via Funnull promoting gambling websites adorned with the emblem of the Suncity Group, a Chinese organization mentioned in a UN report from 2024 (PDF) concerning the laundering of millions of dollars for the North Korean Lazarus Group.
In 2023, the CEO of Suncity was sentenced to a prison term of 18 years for charges including fraud, illicit gambling, and “triad offenses,” that is, collaborating with Chinese transnational organized crime syndicates. Suncity is believed to have established an underground banking operation that laundered billions for criminals.
It seems that the gambling websites linked through Funnull are exploiting prominent casino brands as part of their money laundering tactics. In reporting on Silent Push’s October findings, TechCrunch acquired a statement from Bwin, one of the casinos being heavily advertised through Funnull, asserting that those websites were not affiliated with them.
Gambling is prohibited in China apart from Macau, a special administrative region of the state. Researchers at Silent Push suggest that Funnull might be assisting online gamblers in China in evading the Communist Party’s “Great Firewall,” which restricts access to gambling platforms.
Silent Push’s Zach Edwards indicated that upon re-examining Funnull’s infrastructure this month, they discovered numerous Amazon and Microsoft cloud IP addresses still transmitting Funnull traffic through an intricate chain of automatically generated domain names prior to directing malicious or phishing websites.
Edwards remarked that Funnull represents a quintessential instance of an escalating trend which Silent Push refers to as “infrastructure laundering,” where criminals offering cybercrime services channel some or all of their malicious traffic via U.S. cloud providers.
“It’s imperative for global hosting companies situated in the West to recognize that very low quality and dubious web hosts from China are intentionally leasing IP space from various entities and subsequently mapping those IPs to their criminal client websites,” Edwards expressed to KrebsOnSecurity. “We need these major hosting providers to establish internal protocols such that if they are leasing IP space to one entity that further rents it to host multiple criminal websites, all of those IPs should be reclaimed, and the CDN acquiring them should be barred from future IP rentals or purchases.”
A Suncity gambling platform promoted via Funnull. The sites include a prompt for a Tether/USDT deposit initiative.
When contacted for comment, Amazon directed this reporter to a statement included in a report published today. Amazon stated that AWS was already cognizant of the Funnull addresses identified by Silent Push, and that it had suspended all recognized accounts associated with the activities.
Amazon asserted that contrary to implications presented in the Silent Push report, it has every incentive to rigorously monitor its network against such activities, emphasizing that the accounts linked to Funnull relied on “deceptive methods to temporarily acquire infrastructure, for which it does not compensate. Consequently, AWS incurs losses as a result of these abusive practices.”
“Whenever AWS’s automated or manual systems identify potential misuse, or when we receive reports of potential abuse, we act swiftly to investigate and take measures to halt any prohibited actions,” Amazon’s statement continues. “In the event anyone suspects that AWS resources are being exploited for abusive conduct, we urge them to report it to AWS Trust & Safety utilizing the report abuse form. In this particular instance, the authors of the report never alerted AWS of their research findings through our easily accessible security and abuse reporting channels. Instead, AWS was first informed of their research by a journalist to whom the researchers had provided a draft.”
Microsoft similarly emphasized its commitment to addressing such abuses and encouraged others to report any suspicious activities detected on its network.
“We are dedicated to safeguarding our customers against this type of activity and actively enforce acceptable use policies when violations are discovered,” Microsoft stated in a written response. “We encourage reporting any suspicious occurrences to Microsoft so
“`we can explore and implement suitable measures.”
Richard Hummel serves as the lead for threat intelligence at NETSCOUT. Hummel mentioned that previously, “noisy” and often disruptive harmful traffic — including automated application layer assaults and “brute force” attempts to decipher passwords or expose vulnerabilities in websites — primarily originated from botnets, or extensive networks of compromised devices.
However, he remarked that a significant portion of the infrastructure used to channel this kind of traffic is now routed through major cloud providers, complicating efforts for organizations to block it at the network level.
“From the defenders’ perspective, wholesale blocking of cloud providers is unfeasible, as a single IP can accommodate thousands or tens of thousands of domains,” Hummel noted.
In May 2024, KrebsOnSecurity released an in-depth analysis on Stark Industries Solutions, an ISP that emerged at the onset of Russia’s invasion of Ukraine, serving as a global proxy network that obscures the actual origin of cyberattacks and disinformation efforts against Russia’s adversaries. Experts indicated that a large part of the malicious traffic traversing Stark’s network (e.g., vulnerability assessments and password cracking attempts) was being redirected through U.S.-based cloud providers.
Stark’s network has been favored by the Russian hacktivist group referred to as NoName057(16), which regularly conducts large-scale distributed denial-of-service (DDoS) attacks on various targets perceived as antagonistic to Moscow. Hummel stated that NoName’s track record indicates their skill in rotating through new cloud provider accounts, transforming anti-abuse endeavors into a game of whac-a-mole.
“It almost doesn’t matter if the cloud provider is proactive and takes it down, as the perpetrators will simply activate a new one,” he explained. “Even if it’s only usable for an hour, they’ve already inflicted damage. It’s a genuinely challenging issue.”
Edwards mentioned that Amazon refrained from clarifying whether the terminated Funnull users were operating through compromised accounts, stolen payment card information, or other means.
“I’m astonished they chose to emphasize ‘We’ve identified this 1,200+ times and have taken these down!’ and yet failed to connect that each of those IPs was linked to [the same] Chinese CDN,” he remarked. “We are just grateful Amazon acknowledged that account mules are being utilized for this and it’s not merely a front-door operation. We haven’t received similar confirmation from Microsoft, but it’s highly probable that the same scenario is unfolding.”
Funnull was not always a secure hosting network for fraudulent sites. Prior to 2022, this network was recognized as Anjie CDN, located in the Philippines. One of Anjie’s assets was a site named funnull[.]app. Accessing that domain reveals a pop-up message from the original owner of Anjie CDN, stating that their operations had been seized by an entity known as Fangneng CDN and ACB Group, the parent organization of Funnull.
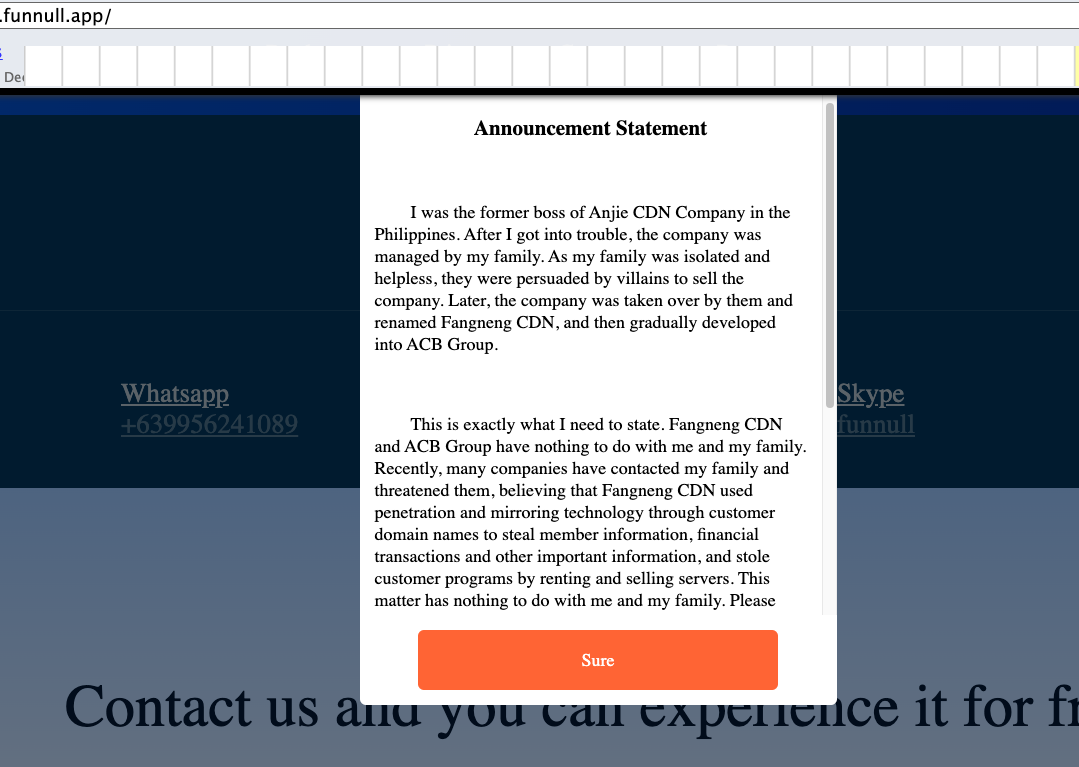
A machine-translated communication from the former proprietor of Anjie CDN, a Chinese content delivery network that is currently Funnull.
“After I encountered legal issues, my family managed the company,” the note clarifies. “Due to their isolation and vulnerability, they were persuaded by malicious individuals to sell the business. Recently, numerous companies have reached out to my family with threats, under the impression that Fangneng CDN utilized penetration and mirroring technology through customer domain names to pilfer member data and financial transactions, as well as appropriating customer programs by renting and reselling servers. This situation is unrelated to me and my family. Please reach out to Fangneng CDN for resolution.”
In January 2024, the U.S. Department of Commerce introduced a proposed regulation mandating cloud providers to establish a “Customer Identification Program” involving procedures to gather data sufficient to determine whether every possible customer is a foreign or U.S. entity.
As stated by the law firm Crowell & Moring LLP, the Commerce regulation would also necessitate “infrastructure as a service” (IaaS) providers to disclose any knowledge of transactions involving foreign entities that might enable the foreign corporation to train an expansive AI model with potential capabilities that could be exploited in malicious cyber-enabled operations.
“The proposed rulemaking has attracted global interest, due to its unprecedented cross-border data collection requirements within the cloud computing realm,” Crowell wrote. “If the U.S. enacts these requirements independently, there are fears that U.S. IaaS providers may face competitive disadvantages, as U.S. allies have yet to announce comparable foreign customer identification mandates.”
It remains uncertain whether the new White House administration will advance the requirements. The Commerce initiative was mandated as part of an executive order issued by President Trump a day before his departure from office in January 2021.

