Carding — the clandestine trade of stealing, trading, and using pilfered payment card information — has historically been dominated by hackers from Russia. Fortunately, the widespread adoption of more secure chip-enabled payment cards in the United States has diminished the carding market. Yet, a surge of creativity from cybercriminal networks in China is revitalizing the carding scene by converting phished card credentials into mobile wallets that can be utilized both online and in brick-and-mortar establishments.
An image sourced from one Chinese phishing group’s Telegram channel showcases various toll road phishing kits that are available.
If you possess a mobile device, it’s highly probable that during the previous two years, you’ve received at least one deceptive message masquerading as the U.S. Postal Service claiming to collect an outstanding delivery fee, or an SMS imitating a local toll road agency warning about an overdue toll charge.
These communications are disseminated via advanced phishing kits marketed by various cybercriminals operating from mainland China. Unlike traditional SMS phishing or “smishing” tactics, these messages bypass mobile networks entirely. Instead, the communications are dispatched via Apple iMessage and through RCS, a functionally similar technology utilized on Google devices.
Victims who submit their payment card details on these fraudulent sites will receive a notification suggesting that their financial institution is sending a one-time passcode to verify a minor transaction. In actuality, that code will be sent by the victim’s bank to confirm that the individual indeed intends to connect their card details to a mobile wallet.
If the victim subsequently provides this one-time code, the fraudsters will associate the card information with a newly created mobile wallet from Apple or Google, installing the wallet on a mobile device that the scammers control.
REINVENTION OF CARDING
Ford Merrill is a security researcher at SecAlliance, a subsidiary of the CSIS Security Group. Merrill has been investigating the transformation of various smishing gangs based in China and discovered that most of them provide useful and instructional video guides within their sales operations on Telegram. These videos demonstrate how the criminals are loading multiple stolen digital wallets onto a single device and subsequently selling these phones in bulk for hundreds of dollars each.
“Who claims carding is obsolete?,” remarked Merrill, who discussed his insights at the M3AAWG security conference in Lisbon earlier today. “This represents the ultimate mag stripe cloning tool. This threat actor asserts you need to purchase a minimum of 10 devices, which they will air transport to you.”
One promotional video depicts piles of milk crates brimming with phones for sale. A closer examination indicates that each device bears a handwritten label, typically denoting the date when its mobile wallets were created, the quantity of wallets present on the device, and the seller’s initials.
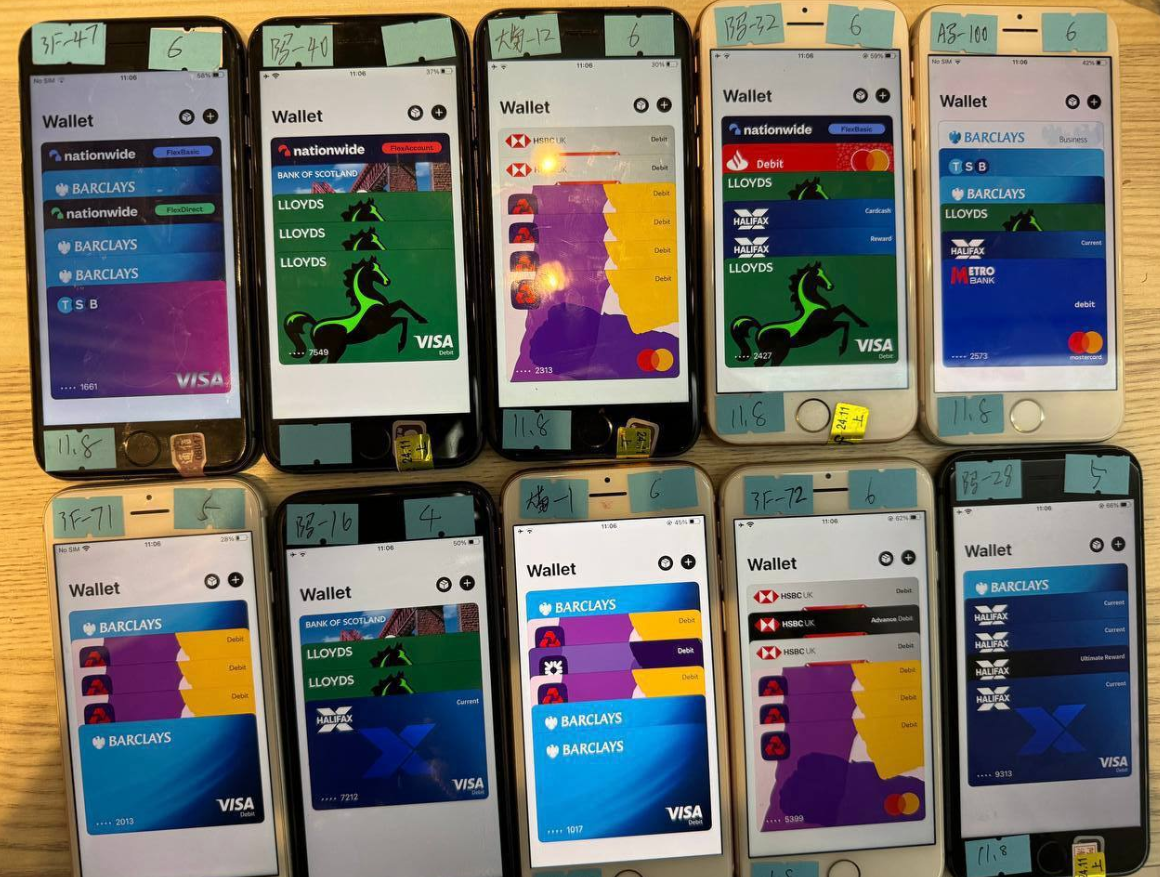
An image sourced from the Telegram channel of a popular Chinese smishing kit provider displays ten mobile phones for sale, each containing 4-6 digital wallets from various UK financial establishments.
Merrill noted that a prevalent method for these criminal groups in China to cash in on stolen mobile wallets is by establishing fraudulent e-commerce enterprises on Stripe or Zelle and processing transactions through these entities — frequently for amounts ranging from $100 to $500.
Merrill explained that when these phishing organizations initially commenced operations in earnest two years ago, they would wait for 60 to 90 days before selling the phones or employing them for fraudulent activities. However, today that waiting period has diminished to just seven to ten days, he mentioned.
“In the beginning, the operators were quite patient,” he stated. “Nowadays, they typically wait only about 10 days before aggressively exploiting the wallets.”
GHOST TAP
Criminals can also liquidate mobile wallets by acquiring legitimate point-of-sale terminals and executing tap-to-pay transactions on multiple devices. Additionally, they provide an innovative mobile fraud solution: Merrill disclosed that at least one of the Chinese phishing groups offers an Android application named “ZNFC” that can transmit a valid NFC transaction to any location worldwide. The user merely needs to wave their phone at a local payment terminal that accepts Apple or Google Pay, and the app will send an NFC transaction over the Internet from a phone situated in China.
“The software can operate from anywhere globally,” Merrill remarked. “These individuals offer the software for $500 each month, and it can facilitate both NFC-enabled tap-to-pay operations and any type of digital wallet. They even provide round-the-clock support.”
The emergence of what is termed “ghost tap” mobile software was first highlighted in November 2024 by cybersecurity experts at ThreatFabric. Andy Chandler, the company’s chief commercial officer, revealed that their analysts have since identified several criminal factions from diverse regions worldwide capitalizing on this scheme.
Chandler noted that this includes organized crime groups in Europe who are utilizing similar mobile wallet and NFC attacks to extract cash from ATMs equipped for smartphone use.
“Nobody is discussing it, but we’re witnessing ten various methodologies employing the same modus operandi, and none of them are executing it identically,” Chandler stated. “This is significantly larger than what the banks are ready to admit.”
A November 2024 article in the Singaporean daily The Straits Times reported that authorities arrested three foreign nationals who were recruited in their home countries via social messaging platforms and provided with ghost tap applications to purchase high-value items from merchants, including mobile devices, jewelry, and gold bars.
“Since November 4, at least 10 individuals who fell victim to e-commerce frauds reported unauthorized transactions exceeding $100,000 on their credit cards for purchases such as electronic gadgets, including iPhones and chargers, as well as jewelry in Singapore,” The Straits Times noted, adding that in another case involving a comparable modus operandi, police apprehended a Malaysian couple on November 8.

Three suspects accused of employing ghost tap software at an electronics shop in Singapore. Image: The Straits Times.
ELABORATE PHISHING STRATEGIES
As per Merrill, the phishing websites mimicking USPS and several toll road companies are driven by various advancements aimed at optimizing the extraction of victim data.
For instance, a potential smishing target might input their personal and financial details but may suspect it’s a fraud before actually transmitting the information. In this scenario, any text input in the data fields of the phishing page will be recorded instantaneously, irrespective of whether the visitor clicks the “submit” button.
Merrill noted that individuals who share payment card details with these phishing sites are often informed that their card cannot be processed and are persuaded to use another card. He explained that this tactic sometimes enables phishers to pilfer more than one mobile wallet from a single victim.
Numerous phishing websites disclose victim information by retaining the stolen data directly on the phishing domain. However, Merrill mentioned that these Chinese phishing kits transfer all victim data to a back-end database managed by the vendors of the phishing kits. Consequently, even when the smishing sites are dismantled for fraudulent activities, the stolen data remains secure.
Another significant advancement includes the utilization of mass-generated Apple and Google user accounts through which these phishers distribute their spam communications. One of the Chinese phishing factions shared images on their Telegram sales channels demonstrating how these automated Apple and Google accounts are loaded onto the respective devices and neatly arranged in an expansive, multi-tiered rack positioned in front of the phishing service operator.

The ashtray proclaims: You’ve been phishing all night.
In essence, the smishing sites are operated by actual human beings as long as new messages are dispatched. Merrill stated that the culprits seem to send merely a few dozen messages simultaneously, likely because executing the scam necessitates manual effort from the human operators in China. After all, most one-time codes utilized for mobile wallet setup typically expire within a few minutes.
Importantly, none of the phishing sites imitating toll operators or postal services will function in a standard Web browser; they will only display if they sense that a visitor is using a mobile device.
“One reason they prefer you to be on a mobile device is they need you to be on the same device that will receive the one-time code,” Merrill stated. “They also aim to reduce the likelihood of you leaving. Furthermore, to capture that mobile tokenization and obtain your one-time code, they require a live operator.”
Merrill discovered that the Chinese phishing kits incorporate another advancement that facilitates the transformation of stolen card particulars into a mobile wallet: They programmatically take the card data provided by the phishing victim and generate a digital representation of a legitimate payment card that corresponds to that victim’s financial institution. This means that enrolling a stolen card into Apple Pay, for instance, becomes as effortless as scanning the forged card image using an iPhone.
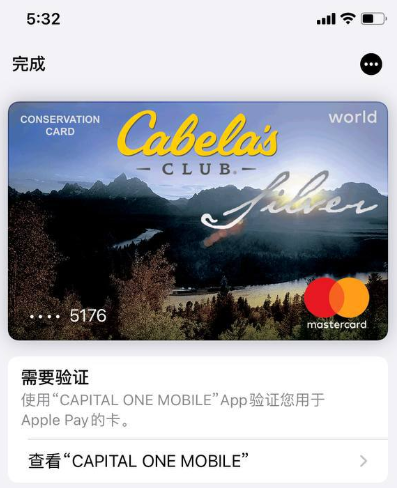
An image from a Chinese SMS phishing group’s Telegram channel illustrating how the service converts purloined card data into an image of the stolen card.
“The phone doesn’t possess the intelligence to discern whether it’s a genuine card or merely an image,” Merrill remarked. “Thus, it scans the card into Apple Pay, which indicates that we need to verify that you’re the legitimate owner of the card by sending a one-time code.”
EARNINGS
How lucrative are these mobile phishing kits? The best estimate to date comes from insights collected by other cybersecurity experts who’ve been monitoring these sophisticated Chinese phishing vendors.
In August 2023, the cybersecurity firm Resecurity uncovered a vulnerability in a well-known Chinese phish kit vendor’s platform that revealed the personal and financial information of phishing victims. Resecurity designated the group as the Smishing Triad, and discovered that the gang had amassed 108,044 payment cards across 31 phishing domains (3,485 cards per domain).
In August 2024, cybersecurity researcher Grant Smith delivered a presentation at the DEFCON security conference concerning the tracking of the Smishing Triad after scammers impersonating the U.S. Postal Service defrauded his wife. By identifying a different vulnerability within the gang’s phishing kit, Smith noted he could see that individuals entered 438,669 unique credit card numbers on 1,133 phishing domains (387 cards per domain).
Based on his investigation, Merrill stated it’s sensible to anticipate losses ranging from $100 to $500 for each card converted into a mobile wallet. Merrill reported observing nearly 33,000 unique domains associated with these Chinese smishing factions over the one-year span between Resecurity’s research publication and Smith’s DEFCON presentation.
Utilizing a median figure of 1,935 cards per domain and a conservative loss of $250 per card, that results in approximately $15 billion in fraudulent transactions within a year.
Merrill was hesitant to disclose whether he had pinpointed further security weaknesses in any of the phishing kits offered by the Chinese groups, remarking that the phishers promptly patched the vulnerabilities that were publicly disclosed by Resecurity and Smith.
COUNTERMEASURES
The uptake of contactless payments soared in the United States following the emergence of the Coronavirus pandemic, and numerous financial institutions in the United States were keen to simplify the process for customers to connect payment cards to mobile wallets. Consequently, the authentication requirement for doing so defaulted to sending the customer a one-time code via SMS.
Experts assert that the ongoing dependence on one-time codes for onboarding mobile wallets has cultivated this fresh wave of carding. KrebsOnSecurity spoke with a security officer from a large European financial institution who requested anonymity because they were not authorized to address the media.
The expert indicated that the delay between the phishing of victim card data and its subsequent utilization for fraud has left many financial institutions grappling to connect the dots regarding their losses.
“That’s part of why the industry as a whole has been blindsided,” the expert remarked. “Many are questioning how this is feasible now that we’ve tokenized a plaintext process. We’ve never encountered such a volume of messaging and responses as we observe with these phishers.”
To enhance the security of digital wallet setups, some banks in Europe and Asia mandate that customers log into the bank’s mobile application prior to being able to associate a digital wallet with their device.
Tackling the ghost tap hazard may necessitate updates to contactless payment terminals, to better recognize NFC transactions relayed from other devices. However, professionals indicate that it’s unrealistic to expect retailers to be eager to replace existing payment terminals before their anticipated lifespans reach their end.
Moreover, Apple and Google hold a greater responsibility, given that their accounts are being mass-generated and utilized to disseminate these smishing communications. Both companies could effortlessly identify which of their devices suddenly have 7-10 distinct mobile wallets added by 7-10 different users from around the globe. They could also advise that financial institutions adopt more secure authentication techniques for mobile wallet provisioning.
No responses were received from Apple or Google regarding requests for feedback on this article.