An essential asset that cybersecurity specialists globally depend on to discover, reduce, and rectify security flaws in both software and hardware is at risk of failure. The federally supported, non-profit research and development entity MITRE alerted today that its agreement to sustain the Common Vulnerabilities and Exposures (CVE) initiative — typically funded annually by the Department of Homeland Security — concludes on April 16.

A correspondence from MITRE vice president Yosry Barsoum, cautioning that the financial support for the CVE initiative will expire on April 16, 2025.
Countless security vulnerabilities in software are detected and documented annually, with these flaws ultimately receiving their distinct CVE tracking identifier (e.g. CVE-2024-43573, representing a Microsoft Windows issue that was remedied by Redmond last year).
A multitude of entities — referred to as CVE Numbering Authorities (CNAs) — are delegated by MITRE to assign these CVE identifiers to newly identified flaws. Numerous CNAs are nation-specific, government-affiliated, or associated with particular software vendors or vulnerability disclosure platforms (otherwise known as bug bounty programs).
Simply put, MITRE serves as a pivotal, extensively-utilized hub for consolidating and standardizing data regarding software vulnerabilities. This implies that the flow of information it provides is integrated into a variety of cybersecurity tools and services that assist organizations in identifying and rectifying security gaps — ideally before malicious software or adversaries can exploit them.
“What the CVE listings genuinely offer is a standardized method to detail the severity of that defect, along with a centralized repository indicating which versions of which products are flawed and require updates,” stated Matt Tait, chief operating officer of Corellium, a cybersecurity company that produces phone-virtualization software for detecting security flaws.
In a letter dispatched today to the CVE board, MITRE Vice President Yosry Barsoum cautioned that on April 16, 2025, “the existing contracting avenue for MITRE to develop, manage, and enhance CVE as well as several related initiatives will cease.”
“If a service interruption were to occur, we foresee numerous ramifications for CVE, including the degradation of national vulnerability databases and advisories, tool providers, incident response operations, and various critical infrastructures,” Barsoum wrote.
MITRE informed KrebsOnSecurity that the CVE website displaying vulnerabilities will remain operational after funding ceases, but no new CVEs will be added post-April 16.
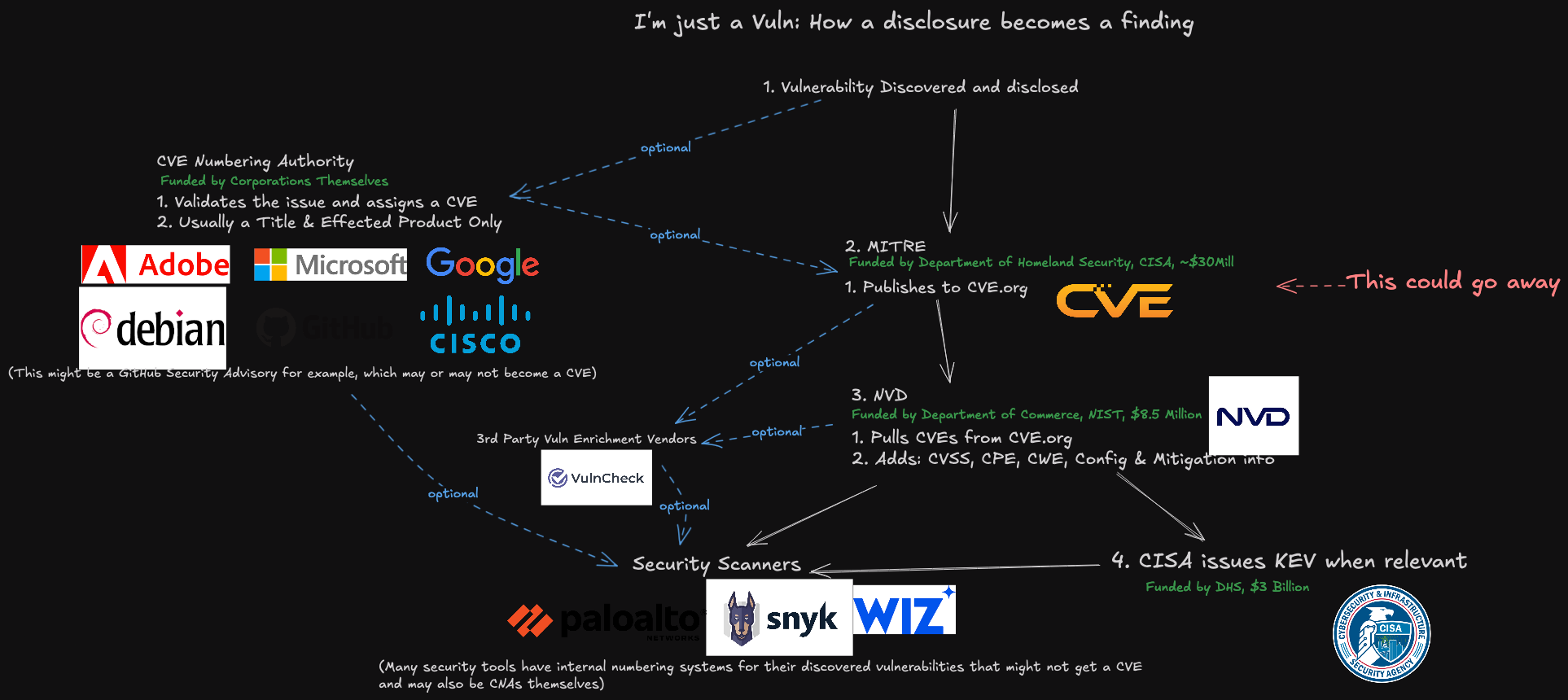
A visualization of the process by which a vulnerability becomes a CVE, and how that information is utilized. Image: James Berthoty, Latio Tech, via LinkedIn.
DHS representatives did not respond immediately to a request for remarks. The program is financed via DHS’s Cybersecurity & Infrastructure Security Agency (CISA), which is presently undergoing significant budget and staffing reductions instigated by the Trump administration.
Former CISA Director Jen Easterly described the CVE initiative as somewhat analogous to the Dewey Decimal System, but tailored for cybersecurity.
“It’s the international catalog that assists everyone—security teams, software vendors, researchers, governments—arrange and discuss vulnerabilities using a unified reference system,” Easterly noted in a post on LinkedIn. “In its absence, entities will be utilizing disparate catalogs or none at all, leading to confusion about whether they are addressing the same issue, wasting valuable time for defenders determining what the problem is, and unfortunately, allowing threat actors to exploit the disorder.”
John Hammond, principal security researcher at the managed security firm Huntress, told Reuters he expressed his frustration audibly upon hearing that CVE’s funding was at risk, stating that losing the CVE program would be akin to losing “the language and terminology we utilize to discuss problems in cybersecurity.”
“I can’t shake the feeling that this will cause significant harm,” remarked Hammond, who shared a YouTube video to express his concerns and inform others.
Many individuals familiar with the situation disclosed to KrebsOnSecurity that this isn’t the first occurrence of the CVE program’s budget being left in uncertain funding status until the final hour. Barsoum’s letter, which seems to have been leaked, struck a hopeful note, asserting that the government is undertaking “considerable efforts to continue MITRE’s role in supporting the initiative.”
Tait mentioned that if the CVE program were to cease, risk managers within organizations would have to continuously check multiple sources for updates on new vulnerabilities that could threaten their IT networks’ security. This could result in more frequent mis-prioritization of software updates, leading to companies deploying vulnerable software longer than they should, he indicated.
“Hopefully they will resolve this, but otherwise, the list will quickly become outdated and cease to be effective,” he stated.

