This week, the FBI alongside enforcement agencies in The Netherlands confiscated numerous servers and domains linked to a widely utilized spam and malware distribution service originating from Pakistan. The operators of this service, commonly referred to as “The Manipulators,” have been featured in three articles published here since 2015. According to the FBI, the primary patrons are organized criminal groups that seek to deceive victim companies into making payments to an intermediary.
An example of the current Fudtools websites operated by the leads of The Manipulators.
On January 29, the FBI, in collaboration with the Dutch national police, seized the technical framework for a cybercrime service branded under Heartsender, Fudpage, and Fudtools (and multiple other variations of “fud”). The term “fud” denotes “Fully Un-Detectable,” indicating resources in cybercrime that can bypass detection from security solutions like antivirus software or anti-spam devices.
The authorities in the Netherlands announced that 39 servers and domains located overseas were confiscated, along with the discovery of millions of records from victims around the globe — which included at least 100,000 records related to residents of the Netherlands.
A declaration from the U.S. Department of Justice identifies the cybercriminal group as Saim Raza, from a pseudonym that The Manipulators collectively employed to promote their spam, malware, and phishing operations on social media.
“The websites operated by Saim Raza functioned as marketplaces that showcased and enabled the sale of tools such as phishing kits, scam pages, and email extractors, often utilized to establish and sustain fraudulent activities,” the DOJ clarified.
The primary product offered by The Manipulators is Heartsender, a service for delivering spam whose homepage explicitly marketed phishing kits aimed at users of various online platforms, including Microsoft 365, Yahoo, AOL, Intuit, iCloud, and ID.me, among others.
The government asserts that transnational organized crime organizations utilizing these services primarily executed business email compromise (BEC) schemes, thereby tricking victim companies into directing payments to an outside party.
“These payments would then be redirected to a financial account controlled by the perpetrators, causing substantial financial losses for the victims,” stated the DOJ. “These tools were also employed to gather user credentials from victims and exploit those credentials to further these fraudulent operations. The confiscation of these domains aims to disrupt the ongoing activities of these groups and halt the spread of these tools within the cybercriminal ecosystem.”
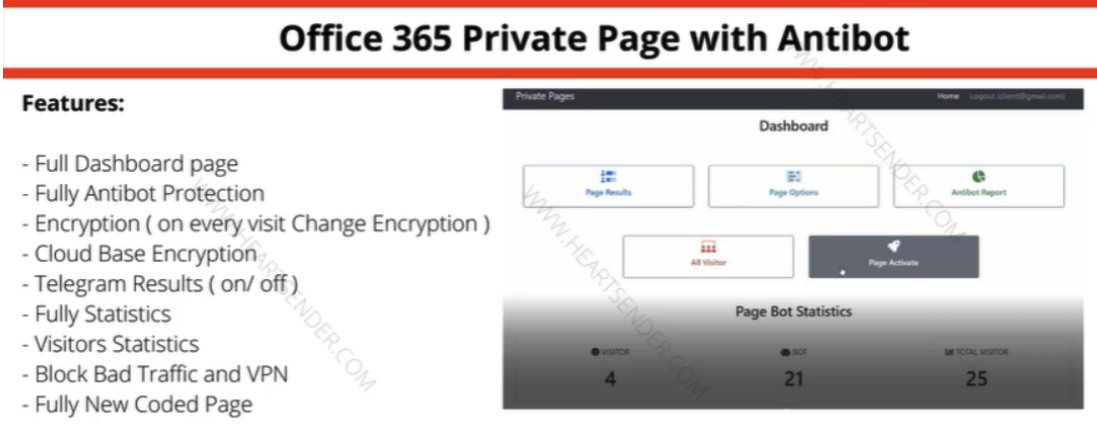
Manipulators’ advertisement for the “Office 365 Private Page with Antibot” phishing kit sold via Heartsender. “Antibot” pertains to functionality aiming to evade automated detection methods, ensuring a phish remains deployed and accessible for an extended period. Image: DomainTools.
KrebsOnSecurity first reported on The Manipulators in May 2015, primarily due to their advertisements saturating several notable cybercrime forums, given their relatively open and audacious demeanor about their operations — even their real identities.
We revisited The Manipulators in 2021, featuring a piece that revealed the main staff members had started a web development firm in Lahore named WeCodeSolutions — presumably to account for their considerable earnings from Heartsender. That article explored how employees at WeCodeSolutions had inadvertently revealed their identities on Facebook by sharing photos from annual company celebrations, showcasing a large cake adorned with the word FudCo in icing.
A subsequent article last year regarding The Manipulators elicited responses from various WeCodeSolutions staff who urged this publication to eliminate stories concerning them. The identity of Saim Raza informed KrebsOnSecurity that they had recently been freed from jail after facing arrest and charges by local law enforcement, although specific details on the charges were not disclosed.
The Manipulators never appeared overly concerned with safeguarding their identities, making it unsurprising they also failed to protect their clients. In a study released last year, DomainTools.com discovered that the web-based version of Heartsender exposed an astonishing amount of user data to unauthenticated individuals, including customer login details and email records belonging to Heartsender staff.

Nearly every year since their inception, The Manipulators have shared an image of a FudCo cake from a company celebration marking its anniversary.
DomainTools also uncovered proof that all computers utilized by The Manipulators were infected with the same password-stealing malware, and countless credentials were pilfered from the collective and sold online.
“Ironically, the Manipulators may pose a greater immediate threat to their own clients than law enforcement,” DomainTools remarked. “The data table ‘User Feedbacks’ (sic) reveals what appear to be customer authentication tokens, user identifiers, and even a support request that reveals root-level SMTP credentials — all accessible to an unauthenticated user on a domain controlled by the Manipulators.”
The police in The Netherlands reported that the investigation into the operators and clients of the service continues.
“The Cybercrime Team is pursuing several purchasers of these tools,” stated the Dutch national police. “It is presumed that these buyers also include individuals from the Netherlands. The investigation into the developers and purchasers of this phishing software remains incomplete despite the confiscation of the servers and domains.”
This week, U.S. authorities also collaborated with law enforcement in Australia, France, Greece, Italy, Romania, and Spain to seize multiple domains associated with several long-standing cybercrime forums and services, including Cracked and Nulled. As per a notice from the European policing agency Europol, the two communities in question garnered over 10 million users in total.
Additional domains confiscated as part of “Operation Talent” encompassed Sellix, an e-commerce platform commonly employed by cybercrime forum members for the transaction of illegal goods and services.