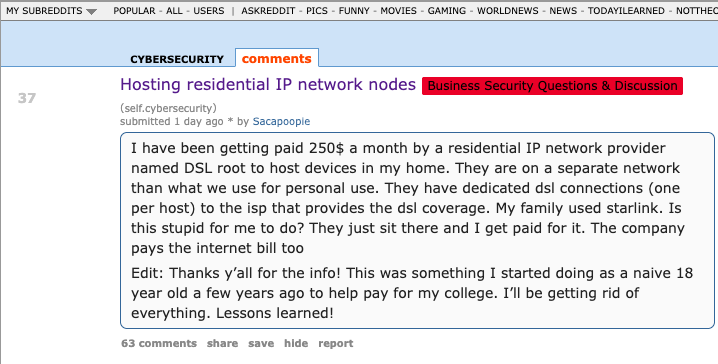
The cybersecurity sector on Reddit reacted with skepticism this month when an individual claiming to be a member of the Air National Guard with top-secret security clearance began raising concerns about an agreement they had with a company named DSLRoot, which was compensating them $250 monthly to connect two laptops to the Redditor’s high-speed internet connection in the United States. This article explores the background and origins of DSLRoot, recognized as one of the earliest “residential proxy” networks originating from Russia and Eastern Europe.
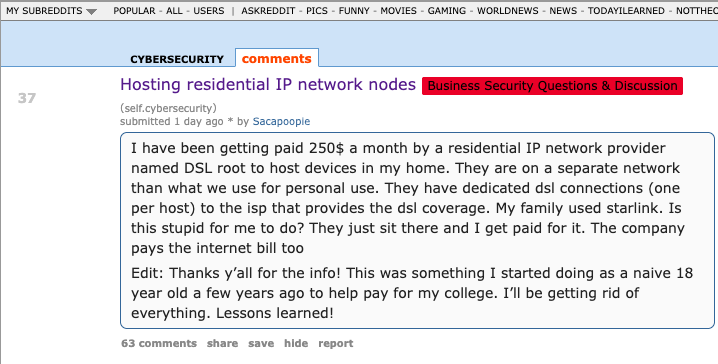
The inquiry concerning DSLRoot was raised by a Reddit user named “Sacapoopie,” who opted not to answer any questions. This user has since removed the initial inquiry from their post, although several of their responses to other Reddit cybersecurity enthusiasts remain in the discussion. The original post was cataloged here by archive.is, starting with the question:
“I have been receiving $250 monthly from a residential IP network provider called DSL root to host devices in my home,” Sacapoopie stated. “They operate on a separate network from what we use for personal purposes. They have dedicated DSL connections (one for each host) to the ISP offering DSL coverage. My family uses Starlink. Is this unwise for me to engage in? They merely sit there, and I earn money for it. The company also covers the internet bill.”
Many Reddit users presumed that Sacapoopie’s post was meant as a joke, asserting that no one with a background in cybersecurity and top-secret (TS/SCI) clearance would consent to allowing a questionable residential proxy company to establish hardware in their network. Other participants highlighted a variety of posts from Sacapoopie in the Cybersecurity subreddit over the preceding two years regarding their cybersecurity work for the Air National Guard.
When pressed for further information by fellow Redditors, Sacapoopie characterized the equipment provided by DSLRoot as “simply two laptops wired into a modem, which then connects to a DSL port in the wall.”
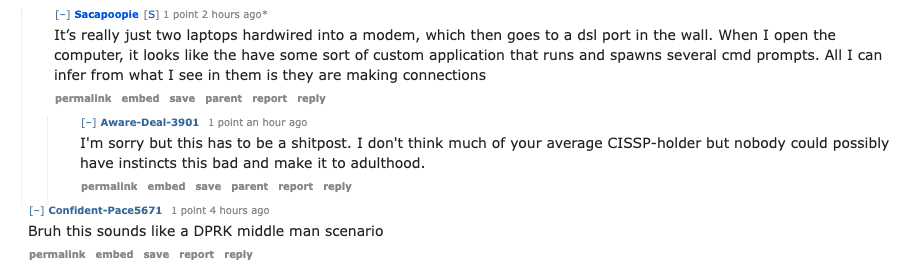
“When I power on the computers, it appears they have some sort of custom application that operates and opens several command prompts,” the Redditor clarified. “From my observations, it seems they are establishing connections.”
When inquired about how they became familiar with DSLRoot, Sacapoopie informed another user that they discovered the company after noticing an ad on a social media platform.
“This was likely 5-6 years ago,” Sacapoopie noted. “Ever since then, I have just been communicating with a technician from that company and assisting with connectivity issues as they come up.”
In response, DSLRoot stated that its reputation has been unjustly tarnished due to that Reddit discussion. The unsigned email claimed that DSLRoot is completely transparent about its purposes and operations, stressing that it functions with the full consent of its “regional agents,” the firm’s designation for U.S. residents like Sacapoopie.
“While we support honest journalism, we oppose all forms of ‘low-quality/misleading Yellow Journalism’ created for sensationalism,” DSLRoot articulated in its response. “It’s clear to us that whoever is behind this, either lacks a thorough understanding of the topic or is deliberately misleading those who are not well-informed to gain attention,” DSLRoot responded to inquiries about the company’s objectives.
“We supervise our clients and prohibit any illegal activities associated with our residential proxies,” DSLRoot added. “We truly weren’t aware that the individual who made the Reddit post was military. Whether it’s an African-American grandmother attempting to pay her rent or a white student striving to finish college, as long as they can provide an internet line or host devices for us — we’re fine.”
WHAT IS DSLROOT?
DSLRoot is offered as a residential proxy service on the forum BlackHatWorld under the names DSLRoot and GlobalSolutions. The organization is headquartered in the Bahamas and was established in 2012. The service is promoted to individuals outside the United States who desire the appearance of being located there. DSLRoot compensates residents in the U.S. to operate the company’s hardware and software, including 5G mobile devices, and in return, the service leases those IP addresses as dedicated proxies to clients worldwide — priced at $190 per month for unrestricted access to all locations.
The DSLRoot website.
The GlobalSolutions profile on BlackHatWorld includes a Telegram account and a WhatsApp number based in Mexico. DSLRoot’s profile on the marketing platform digitalpoint.com from 2010 indicates that their prior username on the forum was “Incorptoday.” GlobalSolutions user accounts on bitcointalk[.]org and roclub[.]com feature the email clickdesk@instantvirtualcreditcards[.]com.
Passive DNS records from DomainTools.com reveal that instantvirtualcreditcards[.]com shared a host back then — 208.85.1.164 — with a limited number of domains, including dslroot[.]com, regacard[.]com, 4groot[.]com, residential-ip[.]com, 4gemperor[.]com, ip-teleport[.]com, and proxyrental[.]net.
Cyber intelligence firm Intel 471 identifies GlobalSolutions registered on BlackHatWorld in 2016 using the email address [email protected]. This user shared their birthday as March 7, 1984.
Several negative remarks about DSLRoot on the forums indicated that the service was managed by a BlackHatWorld user known as “USProxyKing.” Indeed, Intel 471 shows this user prompted fellow forum members in 2013 to reach out to him via the Skype username “dslroot.”
USProxyKing on BlackHatWorld, promoting installations of his adware through torrents and file-sharing sites.
USProxyKing held a reputation for cluttering the forums with advertisements for his residential proxy service and operated a “pay-per-install” scheme where he compensated affiliates a slight fee each time one of their sites led to the installation of his unspecified “adware” programs — presumably a program designed to convert host PCs into proxies. On the other side of this enterprise, USProxyKing marketed that pay-per-install access to others interested in distributing dubious software — for $1 per installation.
Private messages cataloged by Intel 471 indicate that USProxyKing also secured funding from nearly 20 different BlackHatWorld members who were promised ownership shares in a new venture geared towards offering robocalling services capable of placing
“`html
2,000 calls every minute.
Constella Intelligence, a service that monitors data compromised in breaches, discovers that the identical IP address used by GlobalSolutions to register at BlackHatWorld was also utilized to establish accounts on several platforms, including a GlobalSolutions user profile at WebHostingTalk, which provided the email address [email protected]. Linked to [email protected] are the domains dslbay[.]com, dslhub[.]net, localsim[.]com, rdslpro[.]com, virtualcards[.]biz/cc, and virtualvisa[.]cc.
Remember that DSLRoot’s account on digitalpoint.com was formerly identified as Incorptoday. DomainTools reports that [email protected] is linked to nearly two dozen domains dating back to 2008, including incorptoday[.]com, a site that offers to incorporate companies in multiple states, such as Delaware, Florida, and Nevada, for fees between $450 and $550.
As evident in this archived version of the site from 2013, IncorpToday also provided a premium service for $750 that granted the customer’s new business access to a retail checking account, with no inquiries made.
Global Solutions offers access to the U.S. banking system by providing customers with prepaid cards that can be enhanced with various virtual payment methods that were trendy in Russian-speaking regions at the time, including WebMoney. The cards have a limit of $500 balances, but non-Westerners can utilize them to anonymously purchase goods and services from numerous Western firms. Cardnow[.]ru, another domain linked to [email protected], exemplifies this in operation.
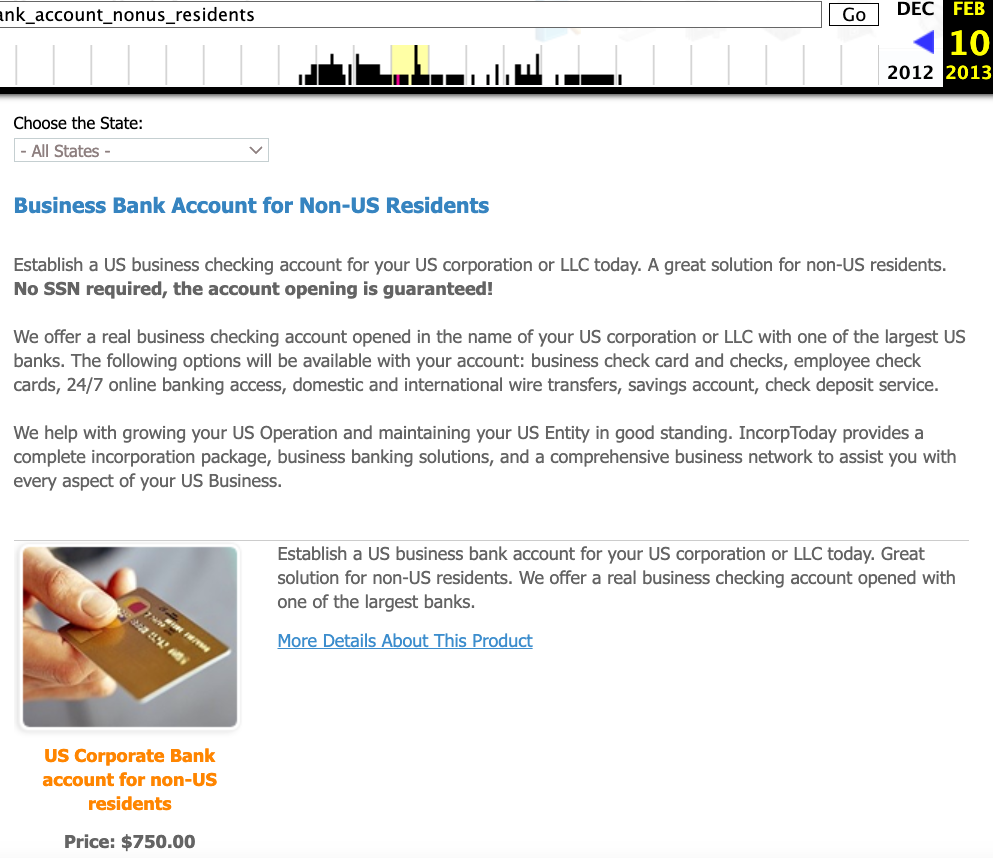
An instance of Incorptoday’s website from 2013 provides non-U.S. residents with a service to establish a business in Florida, Delaware, or Nevada, along with a no-questions-asked checking account, for $750.
WHO IS ANDREI HOLAS?
The eldest domain (2008) linked to [email protected] is andrei[.]me; another is andreigolos[.]com. DomainTools indicates that these and additional domains registered to that email address include the registrant name Andrei Holas, hailing from Huntsville, Alabama.
Public documentation suggests Andrei Holas has resided with his brother — Aliaksandr Holas — at two distinct locations in Alabama. Those records declare that Andrei Holas’ birthday falls in March 1984, while his brother is somewhat younger. The younger sibling did not respond to a request for feedback.
Andrei Holas maintained a profile on the Russian social media platform Vkontakte using the email address [email protected], an address that appears in various records compromised and leaked from Russian government entities over recent years.
These records imply that Andrei Holas and his brother originated from Belarus and have kept an address in Moscow for a considerable duration (that address is roughly three blocks from the main headquarters of the Russian FSB, the successor intelligence agency to the KGB). Leaked Russian banking records confirm that Andrei Holas’ birthday is March 7, 1984 — the same birthdate cited by GlobalSolutions on BlackHatWorld.
A 2010 post by [email protected] on the Russian-language forum Ulitka narrates that the poster faced issues obtaining his B1/B2 visa to visit his brother in the United States, despite having previously been approved for two guest visas and a student visa. It remains uncertain if one, both, or neither of the Holas siblings still resides in the United States. Andrei mentioned in 2010 that his brother was an American citizen.
LEGAL BOTNETS
It’s easy to criticize military personnel who should undoubtedly know better than to install Internet hardware from unfamiliar sources, but in reality, there’s an infinite number of U.S. residents who will resell their Internet access if it means they can earn a bit of cash from it. Presently, numerous residential proxy providers are willing to pay.
Traditionally, residential proxy networks have been formed using malicious software that quietly converts infected devices into traffic relays, which are then sold in obscure online marketplaces. Frequently, this malware is bundled with popular pirated software and video files uploaded to file-sharing networks, covertly turning the host device into a traffic relay. In fact, USPRoxyKing boasted that he consistently achieved thousands of installations weekly via this method alone.
Nowadays, several residential proxy networks incentivize users to monetize their unused bandwidth (requesting them to breach their ISP’s terms of service in the process); others, like DSLRoot, function as a communal VPN, and by utilizing the service, users gate access to the connections of other proxies (users) by default, while also agreeing to share their connection with others.
Indeed, Intel 471’s records reveal that the GlobalSolutions and DSLRoot accounts regularly received private messages from forum members who were college students or young adults attempting to make ends meet. Those messages illustrate that many of DSLRoot’s “regional agents” frequently sought commissions to refer acquaintances interested in reselling their home Internet connections (DSLRoot would cover the monthly expense of the agent’s home Internet connection).
However, in an era when North Korean hackers are continuously masquerading as Western IT professionals by compensating individuals to host laptop farms in the United States, allowing strangers to operate laptops, mobile devices, or any other hardware on your network seems exceedingly risky, regardless of one’s circumstances. As several Reddit users highlighted in Sacapoopie’s thread, an Arizona woman was sentenced in July 2025 to 102 months in prison for hosting a laptop farm that assisted North Korean hackers in securing positions at over 300 U.S. companies, including Fortune 500 firms.
Lloyd Davies is the founder of Infrawatch, a London-based security enterprise that monitors residential proxy networks. Davies stated he reverse-engineered the software powering DSLRoot’s proxy service, discovering that it communicates back to the previously mentioned domain proxyrental[.]net, which offers a service that promises to “get your ads live in multiple cities without getting banned, flagged, or ghosted” (presumably with reference to CraigsList ads).
Davies asserted that he discovered the DSLRoot installer possesses capabilities for remote control of residential networking equipment across various vendor brands.
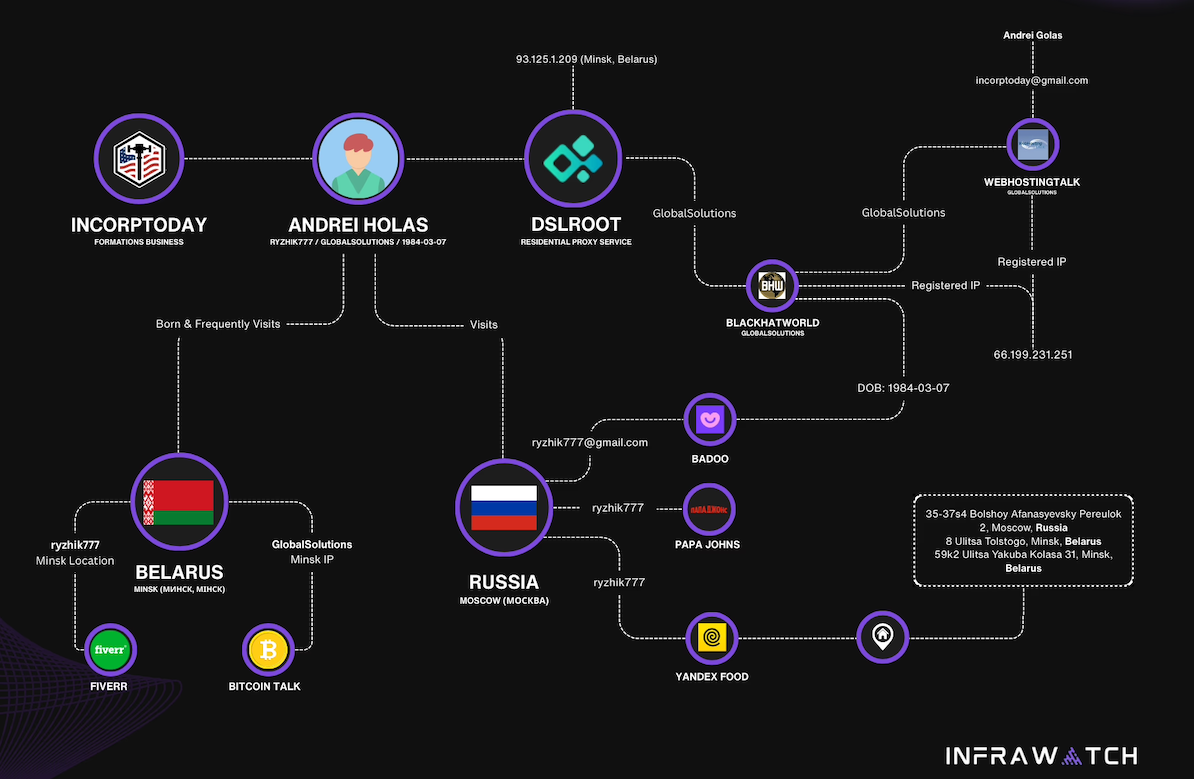
Image: Infrawatch.app.
“The software utilizes vendor-specific exploits and hardcoded administrative credentials, suggesting that DSLRoot pre-configures equipment prior to deployment,” Davies noted in an analysis published today. He indicated that the software conducts WiFi network enumeration to identify local wireless networks, thereby “potentially extending targeting capabilities beyond the primary internet connection.”
It’s uncertain exactly when the USProxyKing was dethroned, but DSLRoot and its proxy offerings are not what they once were. Davies mentioned that the entire DSLRoot network currently comprises fewer than 300 nodes nationwide, primarily from DSL providers like CenturyLink and Frontier.
On August 17, GlobalSolutions announced on BlackHatWorld, stating, “We’re restructuring our business model by downgrading to ‘DSL only’ lines (no mobile or cable).” When inquired via email about these modifications, DSLRoot attributed the decrease in their clientele to the rise of residential proxy services.
“Nowadays, it has become nearly impossible to compete in this niche as everyone is selling residential proxies, and many firms request that you install software on your mobile or desktop, allowing them to resell your residential IPs on a much larger scale,” DSLRoot elaborated. “These so-called ‘legal botnets’ as we perceive them.”
“`