A crafty malware distribution method first detected in targeted attacks last year has now become widespread. In this fraudulent scheme, named “ClickFix,” a visitor to a compromised or deceitful website is prompted to prove they are not a bot by pressing a specific combination of keys, which leads Microsoft Windows to download password-extracting malware.
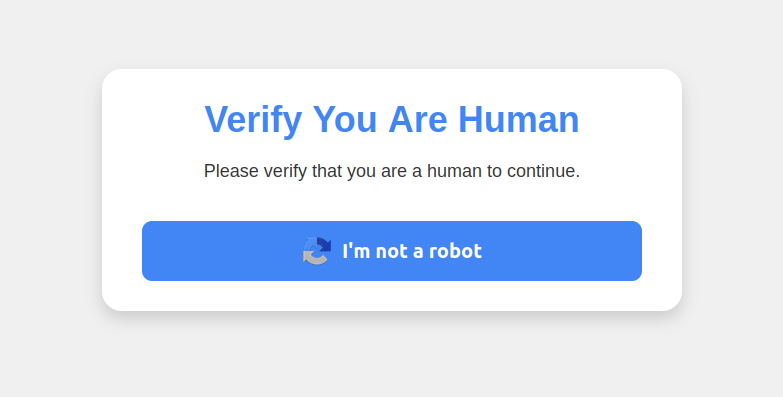
ClickFix assaults imitate the “Verify You are a Human” challenges that countless websites employ to differentiate genuine users from content-scraping bots. This particular con often begins with a website popup that appears somewhat like this:
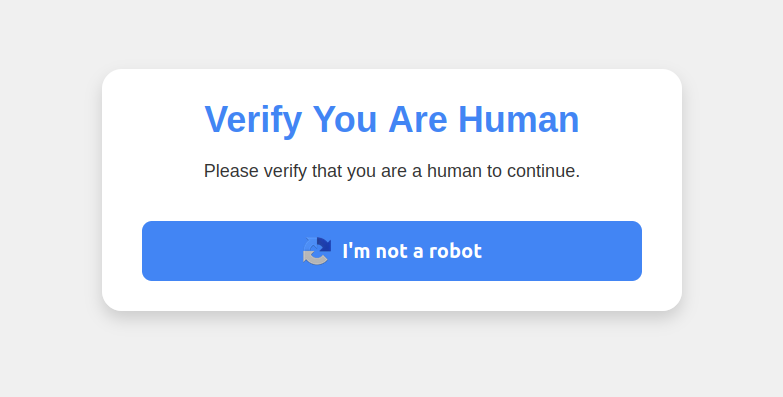
This malware strike pretends to be a CAPTCHA aimed at distinguishing humans from bots.
Selecting the “I’m not a robot” button triggers a pop-up prompting the user to complete three consecutive steps to validate their humanity.
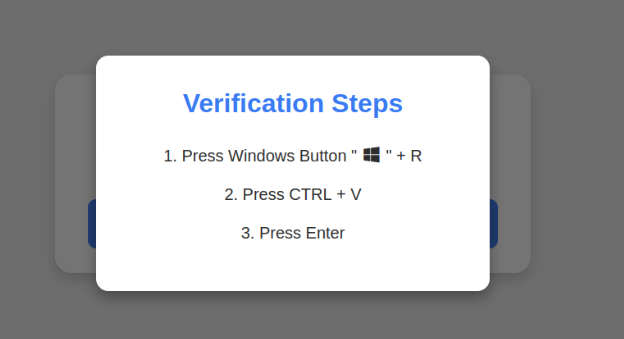
Carrying out this sequence of keypresses prompts Windows to download password-extracting malware.
Step 1 requires the user to press the Windows icon key and the letter “R” simultaneously, which opens a Windows “Run” prompt capable of executing any program installed on the system.
Step 2 instructs the user to simultaneously press the “CTRL” key and the letter “V,” which pastes harmful code from the site’s virtual clipboard.
Step 3 — pressing the “Enter” key — triggers Windows to download and execute malevolent code via “mshta.exe,” a Windows program intended to run Microsoft HTML application files.
“This campaign distributes numerous families of common malware, including XWorm, Lumma stealer, VenomRAT, AsyncRAT, Danabot, and NetSupport RAT,” Microsoft stated in a blog entry on Thursday. “Depending on the particular payload, the code executed through mshta.exe varies. Some instances have downloaded PowerShell, JavaScript, and portable executable (PE) content.”
According to Microsoft, hospitality professionals are being deceived into downloading credential-extracting malware by cybercriminals impersonating Booking.com. The organization reported that assailants have been sending harmful emails masquerading as Booking.com, frequently mentioning negative guest feedback, inquiries from potential guests, or online promotional opportunities — all in an attempt to persuade individuals to engage in one of these ClickFix attacks.
In November 2024, KrebsOnSecurity disclosed that hundreds of hotels utilizing booking.com had fell victim to targeted phishing assaults. Some of those lures succeeded, enabling thieves to gain access to booking.com accounts. Subsequently, they disseminated phishing communications requesting financial details from individuals who had just arranged travel through the company’s application.
Earlier this month, the security firm Arctic Wolf cautioned about ClickFix attacks directed at those working in the healthcare sector. The company noted that these assaults employed harmful code embedded in the popular physical therapy video site HEP2go, redirecting visitors to a ClickFix prompt.
An alert (PDF) issued in October 2024 by the U.S. Department of Health and Human Services cautioned that the ClickFix attack may take various forms, including counterfeit Google Chrome error pages and pop-ups impersonating Facebook.
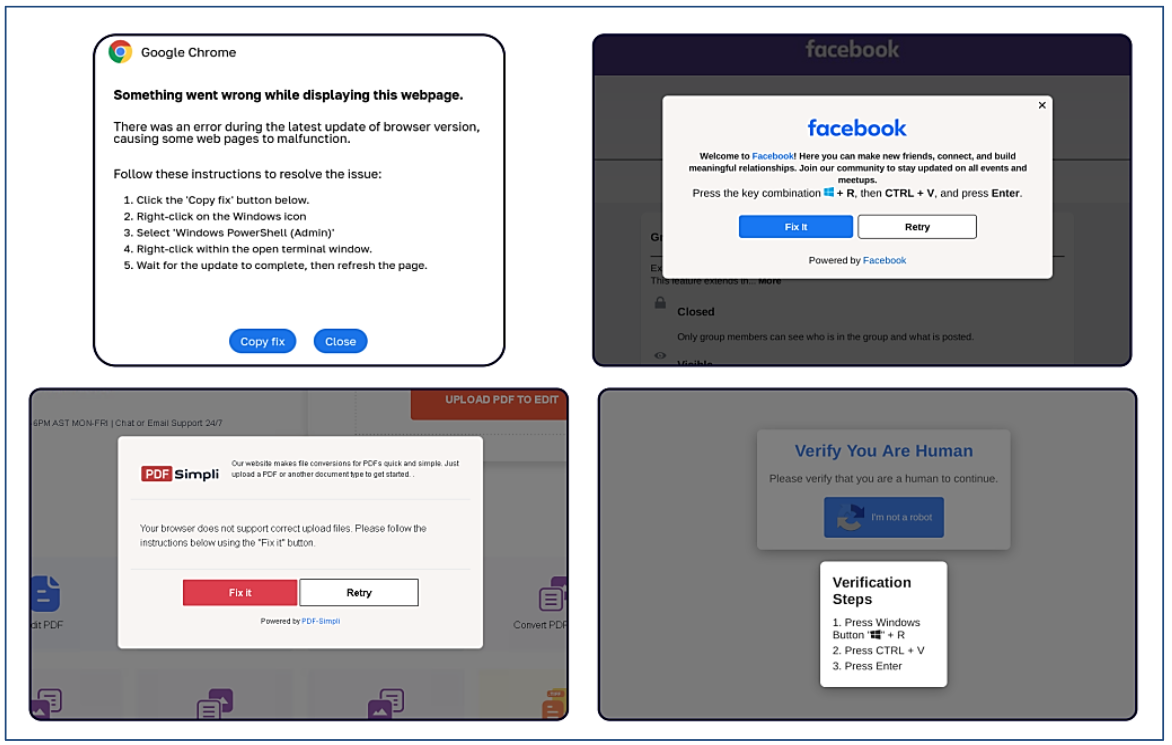
ClickFix strategy employed by malicious websites posing as Google Chrome, Facebook, PDFSimpli, and reCAPTCHA. Source: Sekoia.
The ClickFix attack — and its dependency on mshta.exe — resembles phishing strategies used for years that concealed exploits within Microsoft Office macros. Malicious macros became such a prevalent malware threat that Microsoft had to start blocking them by default in Office documents attempting to download content from the web.
Unfortunately, the email security provider Proofpoint has documented numerous ClickFix attacks via phishing emails containing HTML attachments impersonating Microsoft Office files. When opened, the attachment shows an image of a Microsoft Word document with a pop-up error message directing users to select the “Solution” or “How to Fix” button.

HTML files featuring ClickFix instructions. Examples for attachments labeled “Report_” (on the left) and “scan_doc_” (on the right). Image: Proofpoint.
Entities that wish to mitigate this risk can utilize Microsoft Group Policy restrictions to prevent Windows from executing the “run” command when users press the Windows key and the “R” key simultaneously.