Vendors of SMS phishing kits operating from China are experiencing exceptional success in transforming phished payment card information into mobile wallets associated with Apple and Google. Until recently, the so-called “Smishing Triad” primarily impersonated toll operators and shipping services. However, analysts indicate that these groups have now turned their focus on clientele of global financial institutions, significantly enhancing their cybercrime frameworks and support personnel.

A photo of an iPhone device farm shared on Telegram by a member of the Smishing Triad. Image: Prodaft.
If you possess a mobile device, it’s highly likely that over the past two years you have received at least one text alert regarding an overdue toll charge or a misplaced parcel from the U.S. Postal Service (USPS). Users who click on the provided link are directed to a website that impersonates the USPS or a local toll operator and requests payment card details.
The website will then claim that the visitor’s bank must “authenticate” the transaction by dispatching a one-time code via SMS. In actuality, the bank is sending that code to the mobile number registered for the customer since the criminals have just attempted to register that victim’s card information into a mobile wallet.
If the visitor enters that one-time code, their payment card is subsequently added to a fresh mobile wallet on an Apple or Google device that is under the control of the phishers. The phishing groups generally install numerous stolen digital wallets onto a single Apple or Android device, then sell these phones in bulk to fraudsters who utilize them for illegitimate e-commerce and tap-to-pay activities.
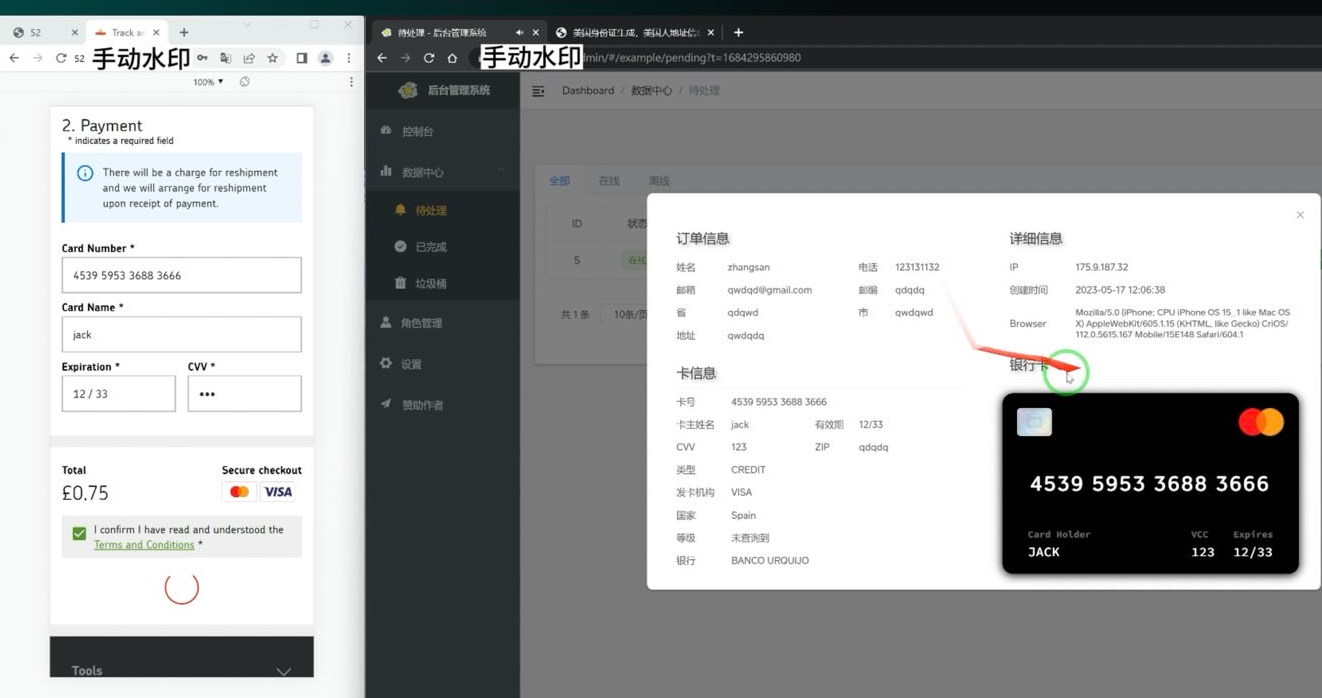
A screenshot depicting the administrative dashboard for a smishing kit. To the left is the (test) data entered at the phishing site. On the right, we observe that the phishing kit has overlaid the supplied card number onto an image of a payment card. When the phishing kit scans that generated card image into Apple or Google Pay, it prompts the victim’s bank to send a one-time code. Image: Ford Merrill.
The term “Smishing Triad” was coined by Resecurity, which was among the first to highlight in August 2023 the rise of three distinct mobile phishing groups based in China that seemed to share some infrastructure and advanced phishing methods. However, referring to them as a triad is somewhat misleading because the phishing messages disseminated by these groups are not SMS or text communications in the typical sense.
Instead, they are transmitted through iMessage to users of Apple devices, and via RCS on devices powered by Google Android. This method allows the messages to evade mobile phone networks entirely, achieving an nearly 100 percent delivery rate (at least until Apple and Google deactivate the fraudulent accounts).
In a report released on March 24, the Swiss cybersecurity firm Prodaft elaborated on the rapid advancements emerging from the Smishing Triad, which it describes as a loosely connected group of Chinese phishing-as-a-service providers featuring names like Darcula, Lighthouse, and the Xinxin Group.
According to Prodaft, there is a noticeable transformation in the underground economy, particularly among Chinese-speaking threat actors, who have traditionally operated in the shadows compared to their Russian-speaking counterparts.
“Chinese-speaking operatives are introducing inventive and cost-efficient systems, allowing them to target larger populations with sophisticated offerings,” Prodaft stated. “Their strategy signals a new chapter in underground operational practices, highlighting scalability and effectiveness in cybercriminal enterprises.”
A recent report from researchers at the security firm SilentPush indicates that members of the Smishing Triad have branched out into selling mobile phishing kits aimed at customers of global financial entities such as CitiGroup, MasterCard, PayPal, Stripe, and Visa, in addition to banks across Canada, Latin America, Australia, and the wider Asia-Pacific region.
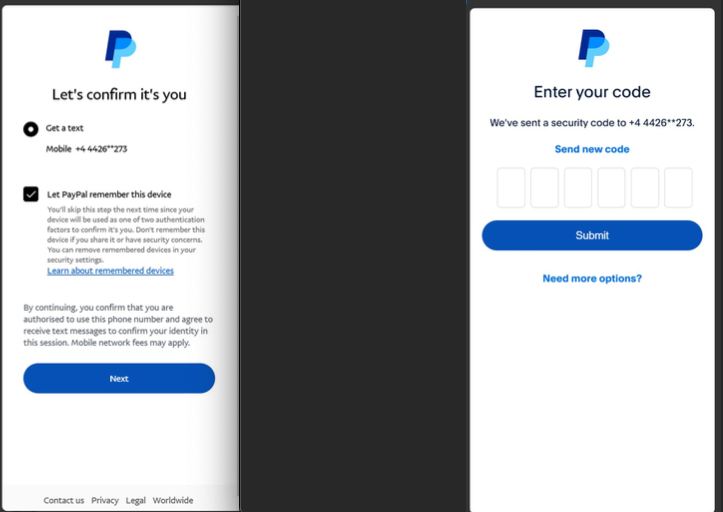
Phishing messages from the Smishing Triad imitating PayPal. Image: SilentPush.
SilentPush discovered that the Smishing Triad is now impersonating well-known brands across various industry sectors in no less than 121 countries, spanning a wide array of fields including postal services, logistics, telecommunications, transportation, finance, retail, and public sectors.
The report outlines that the domains utilized by the Smishing Triad are frequently rotated, with roughly 25,000 phishing domains operational over any eight-day period, most of which are hosted by two Chinese companies: Tencent (AS132203) and Alibaba (AS45102).
“With nearly two-thirds of all nations worldwide targeted by [the] Smishing Triad, it’s reasonable to conclude they are effectively aiming at every country possessing modern infrastructure, with the exception of Iran, North Korea, and Russia,” SilentPush remarked. “Our team has noted some potential targeting towards Russia (for instance, domains that referenced their country codes), but nothing conclusive enough to denote Russia as a consistent target. Interestingly, despite being Chinese criminals, we have observed targeting attempts directed at Macau and Hong Kong, both special administrative regions of China.”
SilentPush’s Zach Edwards reported that his team uncovered a vulnerability that leaked data from one of the Smishing Triad’s phishing sites, which disclosed the daily traffic for each site across thousands of active phishing domains. Based on this information, SilentPush estimates that these phishing sites garnered over a million visits within a 20-day period.
The report mentions that the Smishing Triad claims to have “300+ front desk personnel globally” involved in one of their more sought-after phishing kits — Lighthouse — with these staff primarily tasked with assisting various facets of the group’s fraud and cash-out schemes.
The members of the Smishing Triad operate their own Chinese-language sales platforms on Telegram, which frequently present videos
and images of their personnel diligently engaged in tasks. Some of these visuals showcase extensive arrays of mobile devices utilized to dispatch phishing messages, with human operators positioned directly in front of them, prepared to receive any urgent one-time codes.
As highlighted in February’s article How Phished Data Turns Into Apple and Google Wallets, one of these cash-out operations involves an Android application known as Z-NFC, which can transmit a legitimate NFC transaction from one of these compromised digital wallets to any location globally. For a monthly fee of $500, the user can wave their device at any payment terminal that supports Apple or Google pay, and the app will transmit an NFC transaction over the Internet from a stolen wallet on a phone located in China.
Recently, Chinese individuals were apprehended while attempting to utilize these NFC applications to purchase premium electronics in Singapore. Furthermore, in the United States, law enforcement in California and Tennessee detained Chinese nationals accused of using NFC applications to illicitly acquire gift cards from various retailers.
The Prodaft analysts indicated they successfully discovered an undocumented backend management dashboard for Lucid, a smishing-as-a-service operation linked to the XinXin Group. This dashboard featured victim statistics indicating that the smishing initiatives maintain an average success rate of about five percent, with certain domains garnering over 500 visits weekly.
“In one documented case, a single phishing site captured 30 credit card details from 550 victim engagements over a span of 7 days,” wrote Prodaft.
Prodaft’s analysis elaborates on the Smishing Triad’s success in disseminating their spam messages. For instance, one phishing provider seems to dispatch messages using numerous Android device emulators running simultaneously on a single computer.
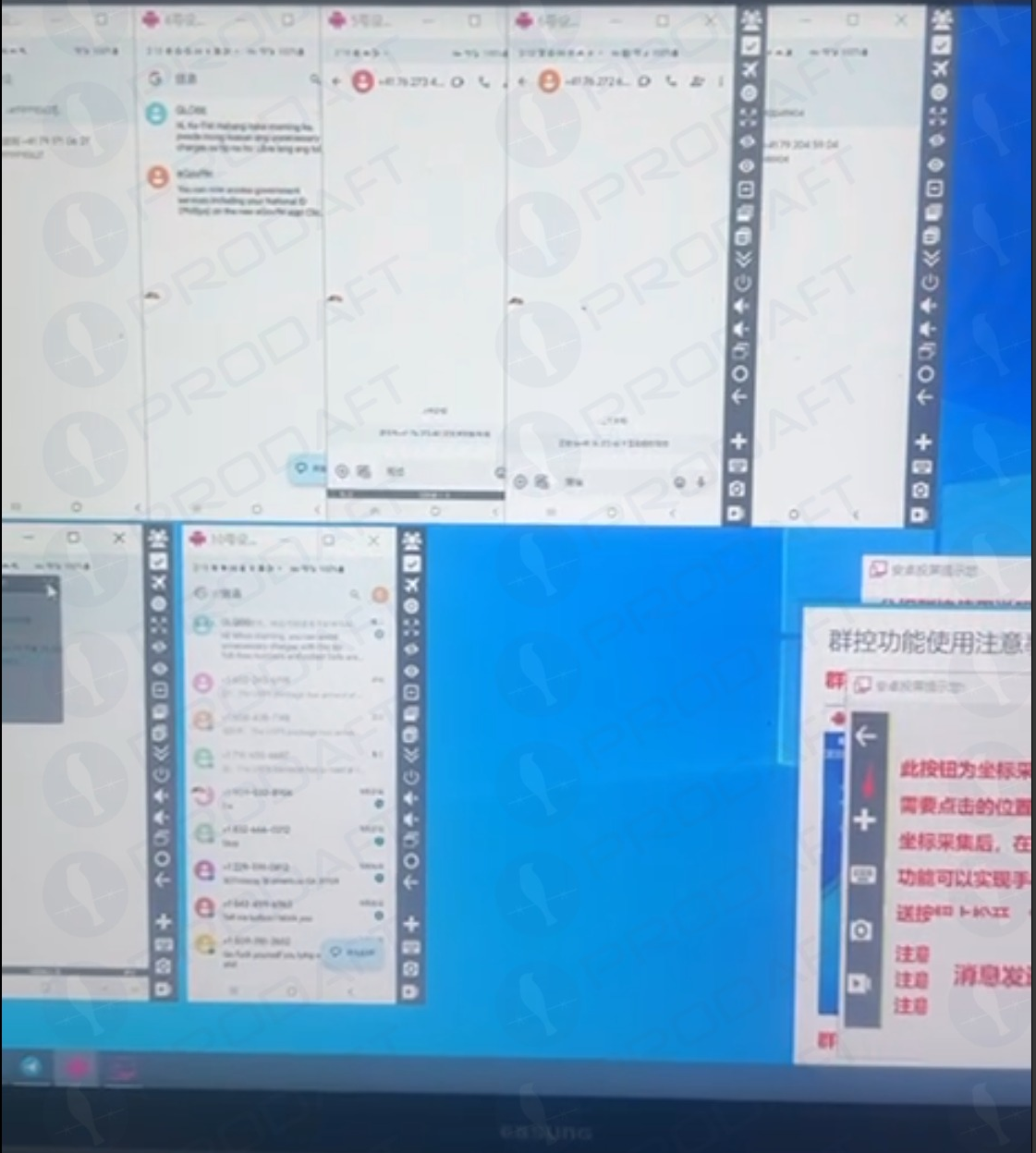
Phishers operating various virtualized Android devices to orchestrate and circulate RCS-based scam campaigns. Image: Prodaft.
According to Prodaft, the threat actors initially gather phone numbers through various channels, including data breaches, open-source intelligence, or by buying lists from underground markets. They then exploit technical vulnerabilities in sender ID verification within messaging platforms.
“For iMessage, this entails creating temporary Apple IDs with impersonated display names, while RCS exploitation takes advantage of carrier implementation discrepancies in sender verification,” Prodaft noted. “Message distribution occurs via automated platforms utilizing VoIP numbers or compromised credentials, often executed in precisely timed multi-wave campaigns to enhance efficacy.”
Additionally, the phishing links embedded in these communications utilize time-sensitive single-use URLs that expire or redirect based on device fingerprinting to bypass security analyses, they discovered.
“The economics heavily favor the attackers, as neither RCS nor iMessage messages incur per-message charges like traditional SMS, allowing for high-volume campaigns at minimal operational costs,” Prodaft further asserted. “The overlap in templates, target demographics, and strategies across these platforms highlights a consolidated threat landscape, with Chinese-speaking individuals spearheading innovation in the underground economy. Their capacity to expand operations globally and evasion methods present substantial challenges to cybersecurity measures.”
Ford Merrill is engaged in security research at SecAlliance, a CSIS Security Group enterprise. Merrill indicated he has observed at least one video showcasing a Windows binary that encapsulates a Chrome executable and can be employed to load target phone numbers and send messages via RCS, iMessage, Amazon, Instagram, Facebook, and WhatsApp.
“The indications we’ve noted suggest that a single device can dispatch approximately 100 messages per second,” Merrill remarked. “We also believe they have the capacity to obtain country-specific SIM cards in large quantities, allowing them to register diverse online accounts that require validation with specific country codes, even rendering those SIM cards accessible to the physical devices over an extended period so that services reliant on validating the authenticity of the phone number or the SIM card presence in a mobile network are thwarted.”
Experts assert that this rapidly emerging trend of card fraud continues because far too many financial institutions still resort to sending one-time codes via SMS for validating card enrollment in mobile wallets from Apple or Google. KrebsOnSecurity has spoken with several security executives at non-U.S. financial institutions who requested anonymity, as they were not authorized to communicate with the media. These banks have since eliminated SMS-based one-time codes and are now necessitating customers to log into the bank’s mobile application before they can link their card to a digital wallet.

