-
Eight Undergraduates Receive Scholarships for Language Studies Abroad

The Gilman and Boren scholarships facilitate international study opportunities.
-
Celebrating Excellence: Eight Cornell Heroes Recognized for Outstanding Service

Cornell is recognizing almost 200 staff members this year as “Cornell Heroes” – a university-wide accolade that acknowledges the remarkable commitment of employees whose efforts might go unnoticed yet are vital to sustaining Cornell’s mission.
-
Michael Manta, an Undergraduate Student, Earns Knight-Hennessy Scholarship

“`html Michael Manta, a fourth-year student pursuing mathematics, has received the esteemed Knight-Hennessy scholarship for graduate education at Stanford University. The Knight-Hennessy Scholars initiative supports individuals who exhibit leadership, independent thought, and a dedication to creating a positive influence on the world, offering up to three years of financial aid for graduate studies in any…
-
Innovative Fuel Cell Technology to Propel the Future of Electric Aviation

“`html Battery technology is approaching its thresholds regarding the amount of energy it can hold relative to its weight. This presents a significant challenge for energy advancements and the exploration of alternative methods to power aircraft, trains, and ships. Currently, researchers at MIT and other institutions have devised a solution that may assist in electrifying…
-
UK employees invited to use new myUK portal as part of preview

-
Upcoming road closure: Huguelet Drive

-
6 students selected as 2025 Sustainability Summer Research Fellows

-
‘Look before you lock’ to prevent hot car deaths

-
From waste to wonder: Narwhal art debuts at Kentucky Children’s Hospital

-
Chilling the Mystery: FSU Scientists Unveil a Stinky Protein through Cryo-EM
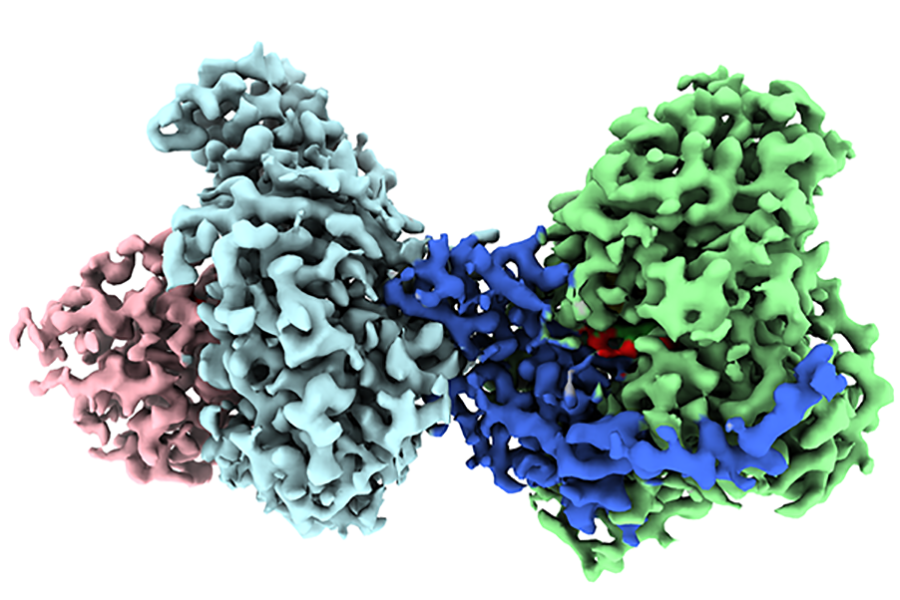
“`html It is often said that an image can convey a thousand expressions. Yet, millions of images are required to grasp the complex chemistry of an enzyme that assists in decomposing sulfur, typically present in fruits, vegetables, alcoholic beverages, and gasoline, into the odorless gas most recognized for its unique scent. Many individuals have experienced…
-
Unlocking the Secrets of Sardinia’s Unique Throat Singing

The vocal ensemble Tenores de Aterue is residing at Dartmouth this spring.
-
MIT Unveils Groundbreaking Initiative for Advanced Manufacturing

“`html MIT has today introduced its Initiative for New Manufacturing (INM), a comprehensive Institute-wide endeavor aimed at revitalizing U.S. industrial production with state-of-the-art technologies, enhancing vital U.S. economic sectors, and stimulating job creation. This initiative will incorporate cutting-edge research, inventive educational programs, and collaborations with businesses across diverse sectors, aiming to revolutionize manufacturing and amplify…
-
Innovating Tomorrow: The Legacy and Vision of MIT in Manufacturing

MIT’s Initiative for New Manufacturing, revealed today by President Sally A. Kornbluth, represents the latest chapter in a longstanding legacy: Since its inception, MIT has consistently endeavored to bolster U.S. manufacturing, generating employment and economic advancement. In fact, a key thread throughout MIT’s history is its dedication to U.S. manufacturing, a pursuit that the Institute…
-
Hidden Cells May Unravel the Secrets Behind the Brain’s Remarkable Storage Ability

The human brain houses approximately 86 billion neurons. These cells transmit electrical impulses that assist the brain in retaining memories and conveying information and commands throughout the brain and the nervous system. The brain also comprises billions of astrocytes — star-shaped cells with numerous long extensions that enable them to engage with millions of neurons.…
-
Mastering the PMP Exam: Your Ultimate Guide to Success

Clearing the PMP Examination in 5 Weeks: An All-Inclusive Guide is an organized blueprint crafted to assist future project managers in succeeding at the Project Management Professional (PMP) examination. This PMP exam preparation PDF dissects the vast curriculum of the PMP exam into a feasible 5-week study schedule, focusing on both the comprehension of material…
-
Scrum Mastery in Just 48 Hours: Your Ultimate Study Guide

Are you prepared to attain your Certified ScrumMaster® (CSM®) designation and elevate your professional journey? Our eBook, CSM Study Guide: Master Scrum in 48 Hours with Proven Exam Strategies, is tailored to assist you in achieving that goal. This strategic guide streamlines your path to comprehending Scrum concepts and succeeding in the CSM exam on…
-
UGA Students Present a Captivating Music-Themed Exhibition

Athens is recognized all over as a musical hub, and the collection at the Georgia Museum of Art located at the University of Georgia is no different. Enrolled in Callan Steinmann’s spring 2025 Topics in Art Museum Education course, students dedicated much of their term to assembling the exhibition titled “Feel the Beat: Rhythm, Music…
-
Unmet Needs: Navigating Alzheimer’s Care in Rural Georgia

Residents of rural Georgia might encounter challenges in obtaining medications that could hinder the advancement of Alzheimer’s disease, as indicated by a recent study conducted by the University of Georgia. This is particularly alarming since rural regions bear a considerably heavier burden of the condition. The investigators examined the presence of facilities that provided the…
-
Unveiling the Secrets of Uranus’ Atmospheric Composition
“`html A recent research indicates the composition of Uranus’ atmosphere nprevenas Tue, 05/27/2025 – 05:54 A recent research indicates the composition of Uranus’ atmosphere Today Article Categories Current Affairs Science & Technology Astronomy By WIRED Type of News Article External News “`
-
Cornell Lacrosse Clinches National Championship, Ending 48-Year Drought

The Big Red triumphed over Maryland 13-10 in the NCAA championship match conducted at Gillette Stadium in Foxborough, Massachusetts.
-
Russian Cybercriminals Compromise Over 20 NGOs with Advanced Evilginx Phishing Tactics Using Counterfeit Microsoft Entra Sites

Microsoft has unveiled details regarding an unreported group of malicious activities stemming from a Russia-linked threat entity known as Void Blizzard (also referred to as Laundry Bear), which the company attributes to “global cloud exploitation.” Operational since at least April 2024, this cybercriminal collective is associated with espionage efforts primarily directed at entities crucial to…
-
Navigating the Non-Human Identity Dilemma: Strategies for Secure Large-Scale AI Deployment
Artificial intelligence is instigating a significant transformation in organizational efficiency, from GitHub Copilot’s coding suggestions to chatbots that explore internal knowledge repositories for immediate responses. Each new agent is required to verify itself with other services, subtly increasing the number of non-human identities (NHIs) within corporate cloud environments. That number is already surpassing manageability for…
-
Navigating Challenges: Staying True to Our Mission During Turbulent Times

“`html Campus & Community Maintaining the mission during a year of challenges Harvard President Alan Garber. Stephanie Mitchell/Harvard Staff Photographer Alvin Powell Harvard Staff Writer May 27, 2025 extended read Garber welcomes Commencement with optimism for students and a strong endorsement of the University’s impact on U.S. development and healthcare As grades were being finalized…
-
Twelve Alumni Step into Leadership Roles on Harvard Boards

“`html Harvard Yard. Photo by Dylan Goodman Campus & Community 12 alumni appointed to Harvard leadership boards New Overseers and HAA directors set to start terms in May, July May 27, 2025 4 min read Six alumni have been recently chosen as members of Harvard University’s Board of Overseers, alongside another six joining the board…
-
Payroll Portal Phishing Scams: How Hackers Exploit Employees’ Searches to Steal Paychecks
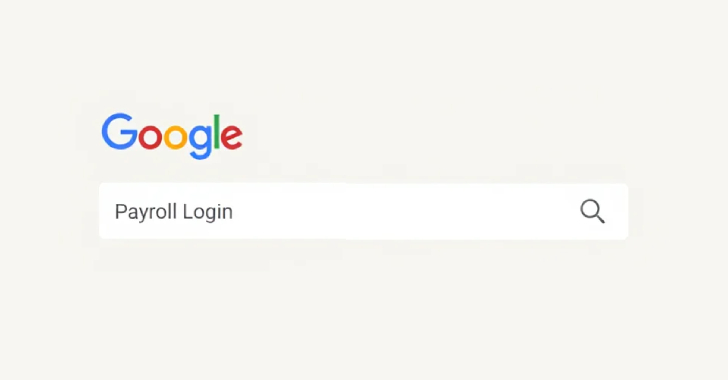
Threat hunters have unveiled a new initiative that employs search engine optimization (SEO) manipulation strategies aimed at employee mobile devices to enable payroll deception. This activity, initially identified by ReliaQuest in May 2025 while focusing on an undisclosed client in the manufacturing industry, is marked by the implementation of counterfeit login pages designed to infiltrate…
-
Navigating the World of VPNs: A Look at Chinese-Owned Options

One of my greatest concerns regarding VPNs is the level of trust users must invest in them, and the lack of transparency many exhibit about their ownership and the types of data they retain. A recent report revealed that numerous commercial VPNs are often (covertly) owned by Chinese firms. It could prove challenging for U.S.…
-
Leading Mobile App Development Firms to Watch in 2025
The digital landscape is expanding swiftly, and the need for mobile applications and software is escalating every day. Even small enterprises are utilizing it as a means to enhance their sales. Let’s explore some of the leading mobile app development firms that have demonstrated their proficiency in this domain. Krify Software Tech Pvt Ltd Krify…
-
Luna Moth’s Covert Phishing Tactics Target Law Firms: FBI Issues Warning

The U.S. Federal Bureau of Investigation (FBI) has issued a caution regarding social engineering assaults executed by a criminal extortion group identified as Luna Moth, which has been aimed at law firms for the last two years. The initiative utilizes “information technology (IT) themed social engineering phone calls and callback phishing emails to acquire remote…
-
Trojan Triumphs: Brian Tinsley’s Legacy as 19-Time Intramural Champion
“`html Brian Tinsley’s flag football squads clinched the title for eight consecutive semesters. (Photo/Courtesy of Brian Tinsley) Share Athletics 19-time intramural champion Brian Tinsley reminisces about Trojan experience on the field and in academia The graduate student has secured 13 titles in intramural flag football and six in soccer. May 27, 2025 By Grayson Schmidt…
-
Canadian Filmmaker from a Small Town Takes a Bold Step into USC’s Producing Program

When Matt Chenuz aimed to establish himself as a thriving film and television producer, he realized that departing Canada was essential. Thus, he enrolled in what he referred to as the “finest producing program globally.”
-
Cyber Assault: Russia-Linked Hackers Strike Tajikistan’s Government with Malicious Documents

The Russia-affiliated threat entity identified as TAG-110 has been seen executing a spear-phishing operation aimed at Tajikistan, utilizing macro-enabled Word documents as their initial delivery method. This sequence of attacks marks a shift from the threat actor’s earlier established use of an HTML Application (.HTA) loader named HATVIBE, as reported by Recorded Future’s Insikt Group…
-
Navigating the Future: Pursuing an MBA in Logistics and Supply Chain Management (2025)
“`html With an MBA in Logistics and Supply Chain Management, you can attain unmatched coordination and synchronization accuracy. If you aspire to elevate your career path or consider a lateral move in your role, this is precisely what you require. In India, you can capitalize on emerging job prospects, international job openings, and lucrative strategic…
-
Understanding the ASP.NET Life Cycle: A Comprehensive Guide

The ASP.NET life cycle is crucial for building scalable and high-performance web applications utilizing the ASP.NET framework. Whether it’s about managing page events, state of controls, or refining application effectiveness, understanding the application and page life cycle in ASP.NET is vital. This article will explore what the ASP.NET life cycle entails, its significance, the stages…
-
Understanding Segmentation in Operating Systems

“`html Effective and proficient memory administration is a crucial component in operating systems as it ensures that numerous programs can operate seamlessly. To manage memory effectively, one robust method is segmentation. Segmentation partitions memory into segments of variable sizes, such as code, data, stack, and heap, depending on their functionality and organization. This approach renders…
-
Unlocking Career Advancement: The Impact of a Supply Chain Management and Analytics Course in 2025

“`html The combination of theory and application offered in a Supply Chain Management with Analytics program could significantly alter your career path. By 2025, data-driven approaches will remain essential for business significance. Refining your SCM and analytical expertise will empower you to assume the position of an industry frontrunner who comprehends supply chain dynamics and…
-
Exploring the Diverse Landscape of Information Systems

Data is crucial for any organization in the modern era, and the way you handle it can determine success or failure. The capability to leverage your information is what distinguishes high-achieving companies from those merely surviving. Whether you are operating a small business or overseeing a vast enterprise, having an appropriate framework to gather, analyze,…
-
Understanding ASP.NET: A Powerful Framework for Web Development

ASP.NET is a robust, open-source, and adaptable web development framework utilized for creating dynamic web applications, APIs, and websites. Whether you are crafting a cloud-based or contemporary web application, ASP.NET ensures optimal performance. This article will explore what ASP.NET entails, its history, progression, reasons for adopting ASP.NET, its architecture, various frameworks of ASP.NET, tools employed…
-
Capturing Browser Screenshots with JavaScript: A Complete Guide

“`html You can acquire a screenshot of the webpage or a designated section by utilizing HTML5 and the Canvas API. Capturing screenshots is relatively straightforward for web applications that necessitate visual documentation, troubleshooting, or sharing information. In this blog, we will explore various techniques to achieve this without requiring any extensions or software. Index: Reasons…
-
What Does a Quality Analyst Do?

“`html In this digital age, product quality can significantly influence user confidence. This underscores the increasing significance of a quality analyst (QA), the individual accountable for ensuring that software and systems function seamlessly prior to being handed over to the client. The QA bears the utmost responsibility for the customer experience and their faith in…
-
Mastering Computer Skills: A Comprehensive Overview and Examples

“`html In the contemporary era, digital literacy is as crucial as conventional reading and writing. Proficiency in computers is tied to fulfilling everyday work obligations such as sending messages, arranging documents, designing forms, settling bills, browsing online, preparing spreadsheets, interpreting data, building websites, and eventually organizing our personal affairs and planning for our future. These…
-
Harnessing the Power of Matrix Visuals in Power BI

“`html Power BI Matrix, alongside the idea of custom measures, represents two key components that assist users in examining and showcasing data. The matrix visual in Power BI enables users to condense data across various dimensions, while DAX permits users to devise bespoke formulas known as measures. In this article, let’s delve into the matrix…
-
ISC Stormcast For Tuesday, May 27th, 2025 https://isc.sans.edu/podcastdetail/9466, (Tue, May 27th)

-
Cornell Lacrosse Claims National Championship Title

The Big Red triumphed over Maryland 13-10 in the NCAA championship match hosted at Gillette Stadium in Foxborough, Massachusetts.
-
Beyond the Spectrum: Exploring the Uncharted Realms of Human Color Perception
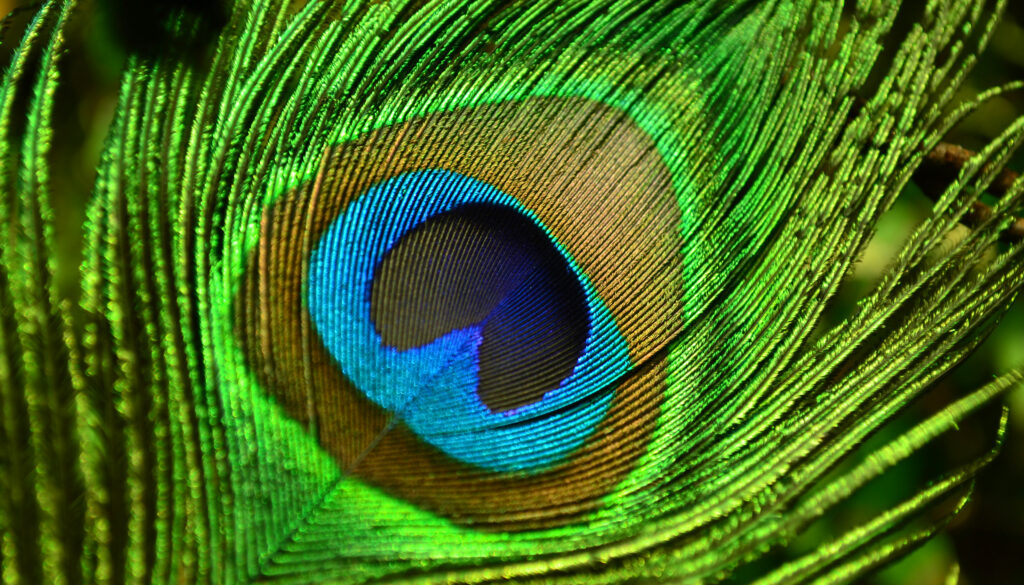
In the previous month, researchers from UC Berkeley deceived the eye into perceiving a novel hue they have designated as “olo.” They argue it could revolutionize our comprehension and treatment of ocular conditions, as well as broaden our perception of the surrounding environment. The article Berkeley Voices: How seeing a new color stretches the limits…
-
Unveiling Secrets: The Art of SVG Steganography

Didier recently released multiple journals pertaining to steganography. I must confess that steganography isn’t particularly my preferred subject. It’s one of those “interesting” infosec gadgets, yet its usefulness is constrained. Data exfiltration typically does not necessitate intricate steganography, as simply adding data to an image will often suffice.
-
Over 70 Malicious npm and VS Code Packages Discovered Compromising Data and Cryptocurrency

As numerous as 60 harmful npm packages have been identified in the package registry featuring harmful capabilities to gather hostnames, IP addresses, DNS servers, and user directories to a Discord-managed endpoint. The packages, released under three distinct accounts, include an installation script that activates during npm install, as noted by Socket security investigator Kirill Boychenko…
-
Abijah Mashava: Journeying from IT Enthusiasm to Pioneering Cloud Computing at Illinois Tech and Beyond

Abijah Mashava’s odyssey originated in Highfield, a modest locale in Harare, Zimbabwe, and has taken him worldwide, into corporate offices, and through diverse positions in software and systems engineering. At present, he stands as a tech entrepreneur and cloud advisor located in Central New York, and he proudly reflects on his accomplishment as a graduate…
-
Unveiling Oracle Guided Learning: Now Integrated with Oracle APEX
Unlock digital integration strategies to assist your users in APEX applications.
-
Navigating Web Privacy Validation: A CISO’s Essential Playbook

“`html Are your website privacy measures safeguarding your users, or merely a compliance formality? This CISO’s manual delivers a pragmatic blueprint for ongoing website privacy assessment that aligns with practical applications. – Download the complete manual here. Web Privacy: Transitioning from Legal Obligation to Business Necessity As regulators intensify enforcement and users become increasingly privacy-conscious,…
-
🔍 Weekly Update: A Deep Dive into APT Activities, Browser Takeovers, AI-Driven Malware, Cloud Vulnerabilities, and Critical CVE Alerts

“`html Cyber dangers no longer appear individually. They are multifaceted, strategized, and frequently remain concealed until it’s too late. For cybersecurity teams, the crucial aspect isn’t merely responding to notifications—it’s identifying preliminary indicators of issues before they escalate into genuine threats. This update aims to provide lucid, precise insights grounded in authentic patterns and changes…
-
Understanding the Role of Typedef in C++: A Deep Dive into Type Aliasing

“`html Is typedef for pointers an effective coding practice or a concealed hazard? While it boosts clarity and simplifies intricate types, it can also lead to ambiguity regarding pointer application, causing potential misunderstanding. Should typedef be utilized for pointers, or is there a superior alternative? Let’s explore some benefits, drawbacks, and recommended practices to uncover…
-
Integrating Python with Power BI: A Comprehensive Guide

Power BI is a platform designed for visualizing and examining data, enhancing the decision-making process. Merging Python with Power BI facilitates the effective construction of a dashboard. Python enables you to restructure, generate, and manage data contingent on specific criteria. Combining Python with Power BI elevates data examination, resulting in improved decision-making. In this article,…
-
Printing an Array in Java: A Quick Guide

“`html When working with Java, we frequently need to showcase the components of an array for debugging or output reasons. By printing the components of an array, we can verify data, confirm the accuracy of calculations, and troubleshoot issues. Java offers various approaches to print an array. In this post, we will explore how to…
-
Sorting an ArrayList of Custom Objects in Java: A Comprehensive Guide

“`html Organizing an ArrayList of User-defined objects by a specific attribute is a frequent task in Java development, particularly when handling extensive datasets. At times, you may wish to arrange an ArrayList according to one or multiple attributes of the objects. Java provides numerous methods to accomplish this, which you will explore in this article.…
-
Testing Private Components in Java: Strategies for Effective Class Evaluation

“`html To evaluate a class that includes private methods, fields, or inner classes, various techniques such as reflection, utility classes, and test doubles can be employed to assess their functionality. In this article, we will explore in-depth how to evaluate a class that features private methods, fields, or inner classes. Table of Contents: What are…
-
Understanding the JavaScript Equivalent of $(document).ready In jQuery, the $(document).ready() function is widely used to execute code as soon as the DOM is fully loaded, ensuring that all elements are accessible for manipulation. However, with the rise of vanilla JavaScript, there are now straightforward methods to achieve the same result without relying on any libraries. To mimic the functionality of $(document).ready() in pure JavaScript, you can use the `DOMContentLoaded` event. Here’s a simple example to demonstrate how you can implement this: “`javascript document.addEventListener(‘DOMContentLoaded’, function () { // Your code here console.log(‘DOM fully loaded and parsed’); }); “` In this snippet, the `addEventListener` method is employed to listen for the `DOMContentLoaded` event, which denotes that the HTML has been completely loaded and parsed. This approach is clean and efficient, making it a preferred choice for modern web development. For those who might be using script tags at the end of the body, it’s important to note that your JavaScript will still execute after the elements are available: “`html Document Ready Equivalent Hello, world! // Code here executes after the body has been fully loaded console.log(‘Body content loaded’); “` In this scenario, placing your JavaScript just before the closing “ tag guarantees that all the DOM elements above are fully loaded when the script runs. By utilizing these techniques, you can harness the full capabilities of JavaScript without the additional weight of libraries, making your web applications more efficient and streamlined.

“`html You can utilize $(document).ready() to ensure the DOM is completely loaded with jQuery. It is essential to confirm that the DOM is prepared before executing your script. In pure JavaScript (native JavaScript without libraries), there are multiple approaches to achieve the same objective. Techniques such as defer Attribute in <script> Tag, window.onload, and setTimeout()…
-
The Future of AI Engineer Salaries in India: Trends and Earnings Insights for 2025

“`html This article provides an insightful overview of AI Engineer salaries in India for 2025, drawing comparisons from multiple online sources. It discusses the variations in salaries for seasoned professionals and forecasts future trends. Additionally, you will gain insights into the crucial technical and interpersonal skills essential for thriving as an AI Engineer in today’s…
-
Mastering Loops in Python: A Deep Dive into For, While, and Nested Structures

“`html Loops hold significant importance in Python. They enable the execution of a code block multiple times without the necessity to rewrite it repeatedly. They prove beneficial for evaluating conditions, handling sequences, and automating tasks that are repetitive. Python provides various loop types, each serving distinct purposes. Moreover, loops can be nested within one another,…
-
Swift Actions and Ready Mindset Rescue USC Swimmer’s Tooth After Scary Incident

Following an accident involving a bus, a university awareness initiative — along with save-a-tooth kits distributed to DPS officers — contributed to preserving Evan Pickles’ grin.
-
Swift Action and Readiness Preserve USC Swimmer’s Grin After Mishap

When an encounter with a bus resulted in Pickles losing his front tooth, a campus awareness initiative — along with save-a-tooth kits given to DPS officers — proved to be crucial.
-
Safeguard Your Guides and Share Them with the World

Blur, Export, and Distribute your OGL Guides with assurance.
-
Preserving Indigenous Languages: The Inspiring Efforts of a Tohono O’odham Linguist in Arizona

“`html This Tohono O’odham language expert is striving to preserve Indigenous languages in Arizona nprevenas Sun, 05/25/2025 – 16:03 This Tohono O’odham language expert is striving to preserve Indigenous languages in Arizona Today Article Categories Current News Social Sciences By The Arizona Republic Type of News Article Outside News “`
-
The Dawn of a New Age in Astronomy: The Giant Magellan Telescope

“`html The Colossal Magellan Telescope inaugurates a fresh chapter in astronomy nprevenas Sun, 05/25/2025 – 15:53 The Colossal Magellan Telescope inaugurates a fresh chapter in astronomy Present Day Article Categories Latest Updates Science & Tech Cosmos By Earth.com Type of News Article International News “`
-
Earning Potential of Graphic Designers in Dubai: Insights and Trends

Dubai houses some of the leading graphic design firms that recruit top-notch designers skilled in providing digitally-oriented services, particularly in logos and branding. They offer attractive salaries, bonuses, and incentives to draw in the finest graphic design experts who possess the ideal blend of passion, creativity, and style. Relevant academic background…Read More.
-
Top 10 Java Books to Master in 2025

Java is a class-based programming language established by James Gosling at Sun Microsystems in 1991. It is utilized to create lightweight and efficient applications for various functions. The TIOBE Index ranks Java among the top three programming languages. Regardless of your stage in the development journey, there are numerous resources available …Read More.
-
Semrush vs. SimilarWeb: Which SEO Tool Reigns Supreme?

What could be more advantageous than gaining insights into your rivals’ keywords and web traffic? Numerous tools provide competitor analysis by gathering and evaluating traffic information. Semrush and SimilarWeb are well-known resources for conducting in-depth assessments. Although Semrush has dominated the market for an extended period, unexpectedly, SimilarWeb has surfaced to present …Read More.
-
Mastering Inbound Marketing: 101 Essential Tools and Resources for Success

An inbound marketer is an individual whose role involves promoting your brand or organization through various mediums such as videos, newsletters, eBooks, blogs, SEO, social media marketing, and more. If the content marketing trends for 2018 are any indication—high-quality content, effectively disseminated, will remain supreme. With three out of four marketers worldwide p…Read More.
-
Harnessing the Power of Azure Cloud Services: A Game Changer for Businesses

Cloud computing provides businesses unmatched capability to swiftly expand on virtual resources, such as storage and processing power, as needed. Initially developed as a software as a service (SaaS) model, cloud computing has evolved significantly over the past two decades. Prominent cloud service providers have introduced new technologies and functionalities to enhance…Read More.
-
Harnessing the Power of Influencer Marketing: A Golden Opportunity for Brands

If you’re pondering whether Influencer Marketing is merely the newest trend in a series of flashy social media marketing concepts, take this into account. According to a current analysis from InsightPool, 70% of adolescent YouTube followers prefer YouTube influencers to celebrities regarding endorsements and insights. In a similar context, Variet…Discover More.
-
Understanding Data Analyst Salaries in Canada: Expectations and Insights

Data analysis has become an essential factor in the growing digital economy. A career in data science is regarded as one of the most sought-after job options, offering the highest salaries in the Canadian employment landscape. Both data scientists and analytics specialists earn a substantial income, even during the early stages of their careers. What…
-
Understanding Graphic Designer Salaries in the United States

Graphic designers craft and produce visual ideas utilizing either a computer or traditional methods, contingent on the nature of the assignment or the organization they are associated with. The goal of producing graphic design is to convey motivating concepts through visual arts, thereby inspiring and attracting a larger clientele. The role of a graphic designer…
-
Navigating IT Salary Trends in the UK: A Comprehensive Overview

In spite of the exceptional difficulties posed by COVID-19, the technology sector in the UK is thriving like never before. Recent statistics reviewed for the UK’s Digital Economy Council indicate that the UK tech industry is presently valued at $1 trillion (£764 billion) – a significant achievement previously reached only by the US and China.…
-
Cybercriminals Deploy Deceptive VPNs and Browser Installers to Spread Winos 4.0 Malware
“`html Cybersecurity experts have revealed a malware initiative that employs counterfeit software installers posing as widely-used applications such as LetsVPN and QQ Browser to deploy the Winos 4.0 framework. This initiative, initially identified by Rapid7 in February 2025, utilizes a multi-tiered, memory-resident loader referred to as Catena. “Catena employs integrated shellcode and configuration modification techniques…
-
The Early Bird Effect: Why Aging Often Means Rising with the Sun

“`html Reasons you rise earlier as you age nprevenas Sat, 05/24/2025 – 20:25 Reasons you rise earlier as you age Today Categories of the Story Health & Wellness Current News By The Huffington Post Type of News Article External News “`
-
“Embracing Community and Values: Kotlikoff’s Message to Graduates”

At a moment when the United States, along with a significant portion of the globe, appears profoundly polarized, President Michael I. Kotlikoff provided graduates at Commencement, conducted on May 24 at Schoellkopf Field, with some historical insight – and a cause for pride: “At Cornell, we’ve strived diligently to uphold a unified community.”
-
Unforgettable Highlights from a Memorable Graduation Week

BEGINNING: Take one last glance at a compilation of video highlights from this year’s premier festivity of the Trojan Family — featuring several new customs.
-
Exploring Diverse Fields through the Prism of Social Work: The Graduate Experience

BEGINNING: USC’s Social Work and Juvenile Justice undergraduate minor merges students’ enthusiasm for social advocacy with an enhanced comprehension of its effects on youth.
-
Unlocking the Power of SQL: Join Our Masterclass on Essential Commands and Syntax | Simplilearn Webinar Kicking Off on May 6, 2025, at 3:30 PM
If information is the new petroleum, SQL is the means by which you extract it! Greetings, I’m Mohammed Sadiq, and I’m excited to assist you in mastering SQL commands and syntax. I’ve dedicated more than twenty years to passionately engaging with data. As a corporate instructor, I have consistently loved showing how to retrieve data,…
-
Unveiling Innovation: Inside the Creation of Platforms Like Uber and Netflix | Simplilearn Webinar Kicks Off on April 6, 2025, at 3:30 PM
Fantastic offerings aren’t mere flukes. They are meticulously designed. Intentionally orchestrated. Skillfully executed. Uber. Netflix. Amazon. Each tale of triumph features a proficient product manager with the talent to strategize effectively. Join me, Suryansh Choudhary, for a comprehensive, engaging session. We won’t merely talk; we’ll analyze everything together in real-time. You’ll witness …Read More.
-
Celebrating Excellence: The 70th Annual Staff Service & Impact Awards at Caltech

“`html On May 22, 2025, Caltech recognized 246 of its personnel at the 70th Staff Service & Impact Awards ceremony conducted in Beckman Auditorium. Julia McCallin, associate vice president for human resources and chief human resources officer, presided as the emcee for the occasion, which celebrated staff for their contributions to Caltech’s research and educational…
-
Creative Currents: June 2025 Highlights

“`html From campus to your home, we invite you to engage with the College of Arts & Sciences community through public events covering the arts, humanities, natural sciences, and social sciences. We look forward to seeing you this June. ArtSci on the Move Searching for additional ways to enhance your experience with Arts & Sciences?…
-
Introducing Angeline Yu, Class of 2025

Yu was raised in the outskirts of Seattle, assisting in her family’s Hawaiian eatery. In June, she will earn her degree in science, technology, and society, with aspirations for medical school.
-
Stanford Scholars Address Critical and Intricate Issues Surrounding Brain Resilience

Four groups have obtained financial support to enhance studies on healthy brain aging and neurodegenerative disorders, featuring an innovative hypothesis on Parkinson’s disease and forecasting aging pathways.
-
Perception of Political Bias Emerges in Leading AI Models
Both Republicans and Democrats believe that LLMs exhibit a liberal bias when addressing political matters.
-
Fresh Insights from USC’s Latest Graduates

BEGINNING: As the thrill of last week’s achievement calms, Trojans convey their concluding reflections and guidance — along with a glimpse of what lies ahead. View the video.
-
Cornell Alumni Set to Forge a Path as Military Leaders

During a ceremony on May 23 in Statler Auditorium, over 25 individuals from Cornell’s Reserve Officers’ Training Corps Tri-Service Brigade were appointed as second lieutenants or ensigns in the Army, Navy, Marines, Air Force, and Space Force.
-
YSPH Dean Ranney Inspires Graduates: Foster Trust and Embrace Optimism

The Yale School of Public Health commemorated its inaugural graduating cohort as an autonomous institution this week with an enthusiastic ceremony in the historic Woolsey Hall.
-
Global Scientists Unite in Nobel Declaration for Immediate Action on Green and Sustainable Chemistry
As a co-head at the Nobel symposium, Yale’s Paul Anastas and other scientific figures are advocating for foundational changes in science, policy, and education to further sustainability objectives that enhance economic growth while protecting health and the environment.
-
Decoding a Single Gene’s Impact on Various Neurodevelopmental Disorders

A recent Yale investigation uncovers how various alterations in a specific gene can lead to cognitive impairment, autism, schizophrenia, and other associated conditions.
-
Elizabeth Askren Takes the Helm as Director of the Yale Symphony Orchestra

Elizabeth Askren — a renowned maestro, educator, and arts proponent — will assume the role of director at the Yale Symphony Orchestra starting in the 2025–2026 season.
-
Incredibly Unique Encounter: The 1978 Incident of a US Naval Ship and an Aggressive Squid

Fascinating narrative: USS Stein was navigating when her anti-submarine sonar equipment unexpectedly ceased functioning. Upon returning to harbor and placing the vessel in a drydock, technicians noticed numerous deep abrasions on the sonar dome’s rubber “NOFOUL” layer. In several spots, the coating was described as being torn, with fissures extending up to four feet in…
-
Celebrating the Moments: Highlights from SOM Commencement 2025
Accompany the latest graduates of Yale SOM as they receive their degrees, engage in campus customs, and rejoice with their family and friends.
-
Reframing the Future: Empowering Low-Income Students in Today’s World

“`html Nation & World Let’s avoid sending underprivileged students back to the ’80s Niles Singer/Harvard Staff Photographer Max Larkin Harvard Staff Writer May 23, 2025 5 min read Financial aid bureaucracy nearly obstructed Susan Dynarski’s undergraduate aspirations. Now, she perceives decades of advancement under jeopardy. Part of the Profiles of Progress series Back in the…
-
FSU Gilman Scholars Ready to Embark on Summer Study Abroad Adventure

“`html Twenty-two students from Florida State University will explore the world this summer via the esteemed Benjamin A. Gilman International Scholarship Program. Endorsed by the U.S. Department of State’s Bureau of Educational and Cultural Affairs, the Gilman Scholarship provides students with the chance to study or intern abroad, equipping them with essential skills vital to…
-
Tolhurst examining economic behavior changes, impacts caused by extreme weather events on agriculture
-
The Eco Champion: Skylar Funk

“`html Skylar Funk was originally Skylar Boorman but legally altered his surname to Funk — in honor of his deceased mother’s maiden name — just prior to registering at USC. “I’d been using it as a stage name since 2011,” he remarks. “Skylar Funk is more appropriate as a music educator.” (Photo: Colleen Allison) Share…
-
Honoring Student Discoveries in Sea Scorpion Research
Catie Fenstermaker ’25 received the Peabody Museum’s Greg Yamanaka Senior Essay Award for her research examining approximately 4,000 ancient sea scorpion fossils gathered from regions in New York and Ontario.
-
Engaging Conversations at Yale: An Afternoon with Maytal Saltiel and Alison

University Chaplain Maytal Saltiel partners with Alison Cole ’99, the executive director of the Yale Alumni Association, to delve into her role on campus and explore how the alumni network can assist.
-
Unlocking the Mystery: The Magnetic Secrets of Lunar Rocks Revealed by MIT Researchers
“`html Where has the moon’s magnetism gone? Researchers have contemplated this inquiry for years, ever since orbiting spacecraft detected indications of a substantial magnetic field in lunar surface minerals. Today, the moon possesses no intrinsic magnetism. Now, scientists at MIT might have unraveled the enigma. They suggest that a blend of an ancient, feeble magnetic…
-
Bridging the Climate Data Divide: Stanford’s Innovative Approach

A recent study advocates for available, dependable climate information to propel efficient greenhouse gas mitigation approaches.