Officials in at least two U.S. states discreetly reported detentions last week of Chinese individuals alleged to be involved in a unique type of tap-to-pay deception employing mobile devices. Information revealed by officials thus far suggests that the mobile wallets utilized by the con artists were established through online phishing schemes, and that those accused were depending on a bespoke Android application to transmit tap-to-pay transactions from mobile devices situated in China.
Image: WLVT-8.
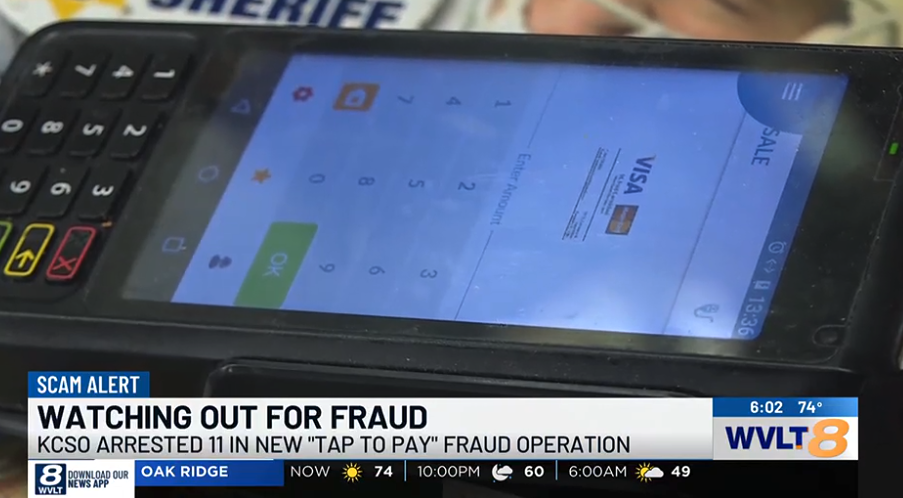
Last week, representatives in Knoxville, Tennessee announced the apprehension of 11 Chinese individuals accused of acquiring gift cards worth tens of thousands of dollars at local stores using mobile wallets generated through online phishing frauds. The Knox County Sheriff’s Office stated that these arrests mark the first instance in the country involving a new variant of tap-to-pay fraud.
In response to inquiries about what makes this scheme particularly noteworthy, Knox County indicated that although it seems the fraudsters are merely purchasing gift cards, they are actually executing multiple transactions to buy various gift cards and are extending their scheme across states.
“These perpetrators have been moving across the country, employing stolen credit card details to acquire gift cards and launder finances,” Knox County Chief Deputy Bernie Lyon commented. “During last Monday’s activity, we recovered gift cards valued over $23,000, all obtained using information from unwitting victims.”
When asked for more details regarding the mobile devices confiscated from the suspects, Lyon remarked, “tap-to-pay fraud involves a group utilizing Android devices to execute Apple Pay transactions with stolen or compromised credit/debit card information,” [emphasis added].
Lyon refrained from providing further details about the operation of the scam, citing an ongoing inquiry.
Ford Merrill engages in security research at SecAlliance, a company under the CSIS Security Group. Merrill pointed out that there are limited legitimate scenarios for Android devices to transmit Apple Pay transactions, unless they are running a special Android application that KrebsOnSecurity reported about last month as part of an in-depth examination of the extensive operations of phishing cartels based in China that are revitalizing the payment card fraud landscape (also known as “carding”).
How are these phishing groups from China acquiring stolen payment card data and subsequently loading it onto Google and Apple devices? It all begins with phishing.
If you possess a mobile phone, it’s highly probable that at some juncture within the last two years you have received at least one phishing communication that impersonates the U.S. Postal Service, allegedly aiming to collect an overdue delivery fee, or an SMS that masquerades as a local toll road operator cautioning about an unpaid toll fee.
Such messages are disseminated through advanced phishing kits sold by various cybercriminals situated in mainland China. Moreover, they are not conventional SMS phishing or “smishing” messages, as they entirely bypass mobile networks. Instead, these communications are transmitted via the Apple iMessage service and through RCS, the functional equivalent technology on Google devices.
Individuals who input their payment card information on these websites will be informed that their financial institution requires verification of a minor transaction by sending a one-time passcode to the user’s mobile device. In truth, that code will be transmitted by the victim’s financial institution in response to a request from the fraudsters to link the phished card information to a mobile wallet.
If the victim subsequently supplies that one-time code, the phishers will connect the card details to a new mobile wallet from Apple or Google, loading the wallet onto a mobile device controlled by the scammers. These devices are then equipped with numerous stolen wallets (typically between 5-10 per device) and sold collectively to fraudsters on Telegram.

An image from the Telegram channel for a well-known Chinese smishing kit vendor showcases 10 mobile phones for sale, each preloaded with 5-7 digital wallets from various financial institutions.
Merrill discovered that at least one of the Chinese phishing groups markets an Android application called “Z-NFC” that can relay valid NFC transactions globally. The user simply needs to wave their device at a local payment terminal that accepts Apple or Google Pay, and the app transmits an NFC transaction over the Internet from a device in China.
“I would be surprised if this isn’t the NFC relay app,” Merrill stated, referring to the suspects apprehended in Tennessee.
Merrill noted that the Z-NFC application can operate from any location in the world, and that one phishing group offers the software for $500 a month.
“It can relay both NFC enabled tap-to-pay and any digital wallet,” Merrill explained. “They even provide 24-hour support.”
On March 16, ABC’s Sacramento affiliate (ABC10) broadcasted a report about two Chinese nationals who were detained after utilizing an app to process stolen credit cards at a local Target store. The news piece cited investigators stating that the individuals were attempting to acquire gift cards via a mobile application that cycled through over 80 stolen payment cards.
ABC10 reported that while the majority of those transactions faced rejection, the suspects still managed to obtain $1,400 worth of gift cards. Following their arrest, both individuals allegedly confessed they were being compensated $250 a day to carry out the fraudulent transactions.
Merrill indicated it is not uncommon for fraud networks to promote this sort of employment on social media platforms, including TikTok.
A CBS News report regarding the arrests in Sacramento mentioned that one of the suspects attempted to use 42 different bank cards, but 32 of those were declined. Nevertheless, the individual was reported to have still managed to spend $855 in transactions.
Similarly, the alleged accomplice attempted 48 transactions on various cards, achieving success 11 times and spending $633, CBS reported.
“It’s intriguing that so many of the cards were rejected,” Merrill observed. “One possible reason for this could be that banks are becoming more proficient at identifying this type of fraud. Another possibility is that the cards had already been utilized and thus flagged for fraud even before these individuals had the opportunity to use them. Therefore, there may be an element of merely sending these individuals to stores to test if it works, and if not, they’re left to fend for themselves.”
Merrill’s research into the Telegram transaction channels for these phishing gangs from China reveals that their phishing sites are actively managed by fraudsters who monitor significant arrays of Apple and Google devices used to disseminate spam and respond to replies in real time.
In essence, the phishing websites are operated by real human agents as long as new messages are being dispatched. Merrill noted that the criminals seem to send only a few dozen messages at a time, likely because completing the con requires manual effort from the human operators in China. After all, most one-time codes utilized for mobile wallet setup generally only remain valid for a few minutes prior to expiring.
For more insights into the operations of these China-based mobile phishing groups, explore How Phished Data Transforms Into Apple and Google Wallets.

The ashtray states: You’ve been phishing all night.