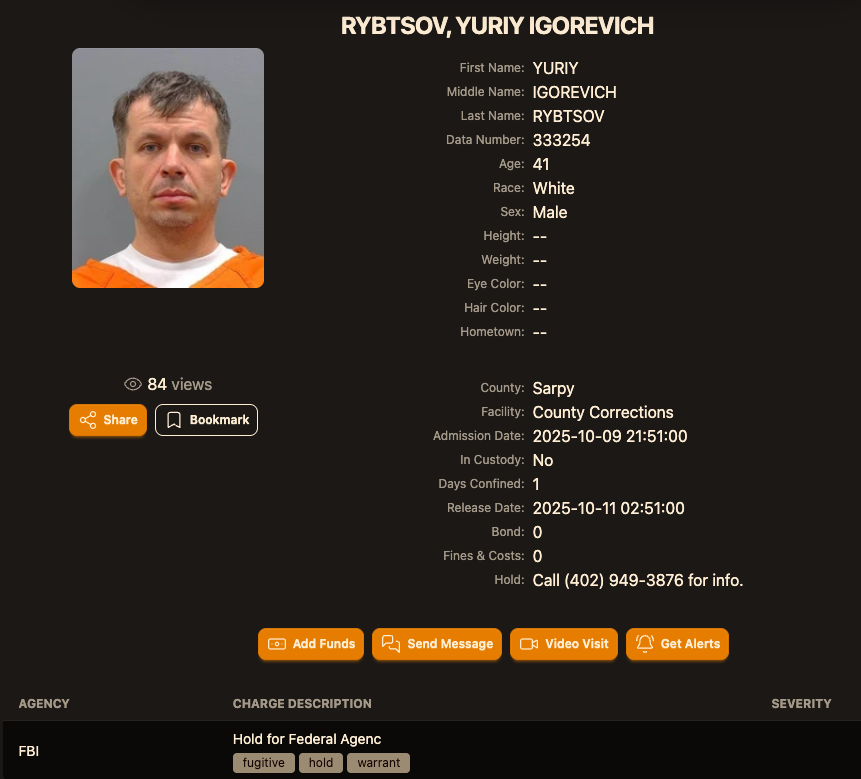
A Ukrainian individual charged in 2012 for colluding with a notorious hacking faction to unlawfully acquire tens of millions of dollars from American enterprises was apprehended in Italy and is presently in custody in the United States, as reported by KrebsOnSecurity.
Insiders knowledgeable about the probe indicate that Yuriy Igorevich Rybtsov, a 41-year-old from the Russia-governed city of Donetsk, Ukraine, was referred to in U.S. federal indictment documents solely by his online alias “MrICQ.” According to a 13-year-old indictment (PDF) submitted by prosecutors in Nebraska, MrICQ served as a developer for a cybercriminal organization known as “Jabber Zeus.”
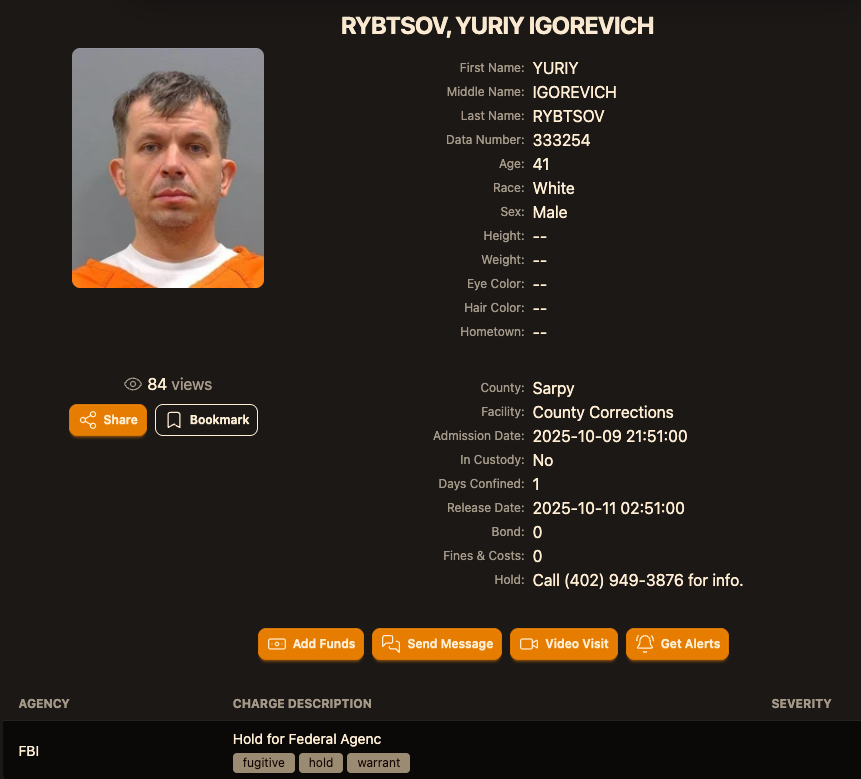
Image: lockedup dot wtf.
The title Jabber Zeus is derived from the malware they implemented — a tailored version of the ZeuS banking trojan — which pilfered banking login information and dispatched an instant message via Jabber to the group each time a new victim inputted a one-time passcode at a financial institution’s site. The syndicate primarily targeted small to medium-sized enterprises and functioned as early innovators of so-called “man-in-the-browser” assaults, malware capable of discreetly intercepting any information victims submit through web-based forms.
Upon gaining access to a victim’s accounts, the Jabber Zeus team would alter the company’s payroll to include numerous “money mules,” individuals recruited through intricate work-from-home schemes to facilitate bank transactions. The mules, in turn, would transmit any misappropriated payroll deposits — subtracting their commissions — via wire transfers to other mules situated in Ukraine and the United Kingdom.
The 2012 indictment aimed at the Jabber Zeus team identified MrICQ as “John Doe #3,” stating this individual managed incoming alerts regarding newly victimized targets. The Department of Justice (DOJ) mentioned that MrICQ also assisted the team in laundering the gains from their crimes through electronic currency exchange platforms.
Two individuals familiar with the Jabber Zeus investigation confirmed that Rybtsov was detained in Italy, although the specific date and conditions of his arrest remain ambiguous. A summary of recent judgments (PDF) released by the Italian Supreme Court specifies that in April 2025, Rybtsov lost a final appeal to evade extradition to the United States.
As per the mugshot site lockedup[.]wtf, Rybtsov arrived in Nebraska on October 9, and was being detained under an arrest order from the U.S. Federal Bureau of Investigation (FBI).
The data breach monitoring service Constella Intelligence uncovered compromised records from the business profiling site bvdinfo[.]com indicating that a 41-year-old Yuriy Igorevich Rybtsov resided in a building at 59 Barnaulska St. in Donetsk. Further exploration of this address in Constella reveals that the same apartment complex was also associated with a business registered to Vyacheslav “Tank” Penchukov, the leader of the Jabber Zeus group in Ukraine.

Vyacheslav “Tank” Penchukov, pictured here performing as “DJ Slava Rich” in Ukraine, in an undated snapshot from social media.
Penchukov was captured in 2022 while en route to meet his spouse in Switzerland. Last year, a federal court in Nebraska sentenced Penchukov to 18 years in prison and mandated him to refund over $73 million.
Lawrence Baldwin is the founder of myNetWatchman, a threat intelligence firm based in Georgia that began monitoring and disrupting the Jabber Zeus syndicate in 2009. myNetWatchman had clandestinely accessed the Jabber chat server utilized by the Ukrainian hackers, enabling Baldwin to eavesdrop on the daily interactions between MrICQ and other Jabber Zeus associates.
Baldwin shared these instant chat records with multiple state and federal law enforcement bodies, and with this journalist. Between 2010 and 2013, I dedicated several hours each day to informing small enterprises nationwide that their payroll accounts were at risk of being depleted by these cybercriminals.
Those alerts, along with Baldwin’s relentless efforts, saved innumerable potential victims from significant financial losses. In numerous instances, however, it was already too late. Nonetheless, the pilfered Jabber Zeus group conversations formed the foundation for numerous articles published here concerning small businesses contesting their banks in court over six- and seven-figure monetary damages.
Baldwin remarked that the Jabber Zeus team was significantly ahead of its competitors in various aspects. For one, their intercepted communications indicated they collaborated to create a highly personalized botnet directly with the creator of the original Zeus Trojan — Evgeniy Mikhailovich Bogachev, a Russian national who has long been featured on the FBI’s “Most Wanted” roster. The authorities have a standing $3 million bounty for information that leads to Bogachev’s capture.

Evgeniy M. Bogachev, in undated images.
The main breakthrough of Jabber Zeus was an alert that MrICQ would receive whenever a new victim submitted a one-time password into a phishing page that imitated their financial institution. The internal codename for this feature was “Leprechaun,” (the video below from myNetWatchman demonstrates it in action). Jabber Zeus would actually revise the HTML code as represented in the victim’s browser, enabling them to intercept any passcodes sent by the victim’s bank for multi-factor authentication.
“These individuals had compromised such an enormous number of victims that they were inundated with a flood of stolen banking details,” Baldwin informed KrebsOnSecurity. “However, the primary aim of Leprechaun was to isolate the most valuable credentials — the commercial bank accounts equipped with two-factor authentication. They understood these were far more appealing targets as they undoubtedly contained considerably more funds to protect.”
“`html
Baldwin stated that the Jabber Zeus trojan also featured a tailored “backconnect” element that enabled the cybercriminals to transmit their theft of commercial banking accounts via the compromised individual’s infected computer.
“The Jabber Zeus team were essentially linking to the victim’s bank account from the victim’s IP address, or through the remote control capability while completely imitating the device,” he remarked. “That trojan was akin to a heated knife slicing through what everyone regarded as state-of-the-art secure online banking at that time.”
Even though the Jabber Zeus team maintained direct communication with the Zeus creator, the discussions intercepted by myNetWatchman reveal that Bogachev often disregarded the group’s requests for assistance. Authorities assert that the genuine leader of the Jabber Zeus team was Maksim Yakubets, a 38-year-old Ukrainian national possessing Russian citizenship who operated under the hacker alias “Aqua.”

Alleged Evil Corp leader Maksim “Aqua” Yakubets. Image: FBI
The intercepted Jabber conversations captured by Baldwin indicate that Aqua engaged almost daily with MrICQ, Tank, and other participants of the hacking group, frequently overseeing the team’s money mule and cashout operations remotely from Russia.
Authorities claim that Yakubets/Aqua eventually rose as the leader of a sophisticated cybercrime syndicate comprising at least 17 hackers who internally designated themselves as “Evil Corp.” Members of Evil Corp devised and utilized the Dridex (also known as Bugat) trojan, which facilitated the extraction of over $100 million from numerous victim organizations across the United States and Europe.
This 2019 article concerning the government’s $5 million reward for leads resulting in Yakubets’s apprehension includes snippets of dialogues among Aqua, Tank, Bogachev, and other members of the Jabber Zeus crew discussing articles I had written about their victims. Both Baldwin and I were extensively interviewed for a new weekly six-part podcast by the BBC that deeply explores the saga of Evil Corp. Episode One concentrates on the development of Zeus, whereas the subsequent episode revolves around an examination of the group by former FBI agent Jim Craig.

Image: https://www.bbc.co.uk/programmes/w3ct89y8
“`