“`html
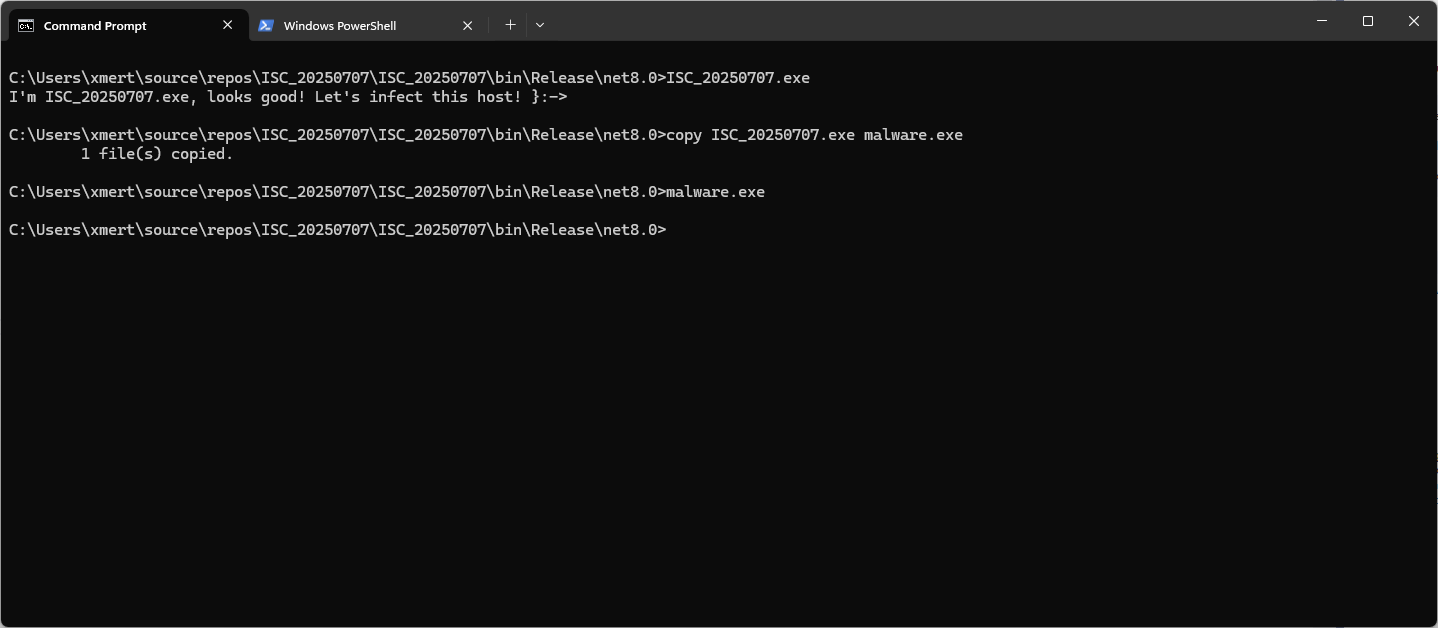
Contemporary malware incorporates numerous anti-debugging and anti-analysis characteristics. Nowadays, when malware circulates in the wild, there exists a likelihood that it will be automatically routed into an analysis pipeline and a sandbox environment. To examine a sample within a sandbox, it must be “transferred” into the sandbox and executed. This process can occur either manually or via automation. When individuals initiate the inspection of a questionable file, they commonly label it as “sample.exe”, “malware.exe” or “suspicious.exe”. This practice is not always prudent, as it may be detected by the malware, alerting it to the fact that “I am being examined”.
“`