“`html

Image: Shutterstock, ArtHead.
The U.S. administration today enacted economic sanctions against Funnull Technology Inc., a firm based in the Philippines that supplies computer infrastructure for numerous websites involved in virtual currency investment deceptions known as “pig butchering.” In January 2025, KrebsOnSecurity revealed how Funnull was utilized as a content delivery network catering to cybercriminals looking to funnel their traffic through U.S.-based cloud services.
“Americans lose a staggering amount of money each year to these cyber frauds, with revenues from these crimes reaching unprecedented levels in 2024,” states a statement from the U.S. Department of the Treasury, which sanctioned Funnull and its 40-year-old Chinese administrator Liu Lizhi. “Funnull has actively facilitated several of these operations, resulting in over $200 million in reported losses from U.S. victims.”
The Treasury Department indicated that Funnull’s activities are associated with the majority of virtual currency investment scam websites documented to the FBI. The agency asserted that Funnull directly enabled pig butchering and other schemes, leading to over $200 million in financial damages to Americans.
Pig butchering represents a widespread type of fraud where individuals are enticed by charming strangers online to invest in phony cryptocurrency trading platforms. Victims are encouraged to continually invest more money into what seems to be a highly lucrative trading platform, only to discover their funds are missing when they attempt to withdraw.
The con artists frequently demand that investors pay additional “taxes” on their crypto “gains” before they can reclaim their invested money (spoiler alert: they never do), and an alarming number of individuals have lost six figures or more through these pig butchering schemes.
KrebsOnSecurity’s January article on Funnull was founded on research from the security firm Silent Push, which uncovered in October 2024 that a large number of domains hosted via Funnull were advertising gambling websites affiliated with the Suncity Group, a Chinese entity identified in a 2024 UN report (PDF) for laundering millions of dollars for the North Korean state-sponsored hacking organization Lazarus.
Silent Push determined that Funnull was a criminal content delivery network (CDN) generating significant traffic related to scam websites, diverting the traffic through an intricate series of auto-generated domain names and U.S.-based cloud services before redirecting to harmful or phishing sites. The FBI has published a technical document (PDF) detailing the infrastructure used to manage the nefarious Funnull domains from October 2023 to April 2025.
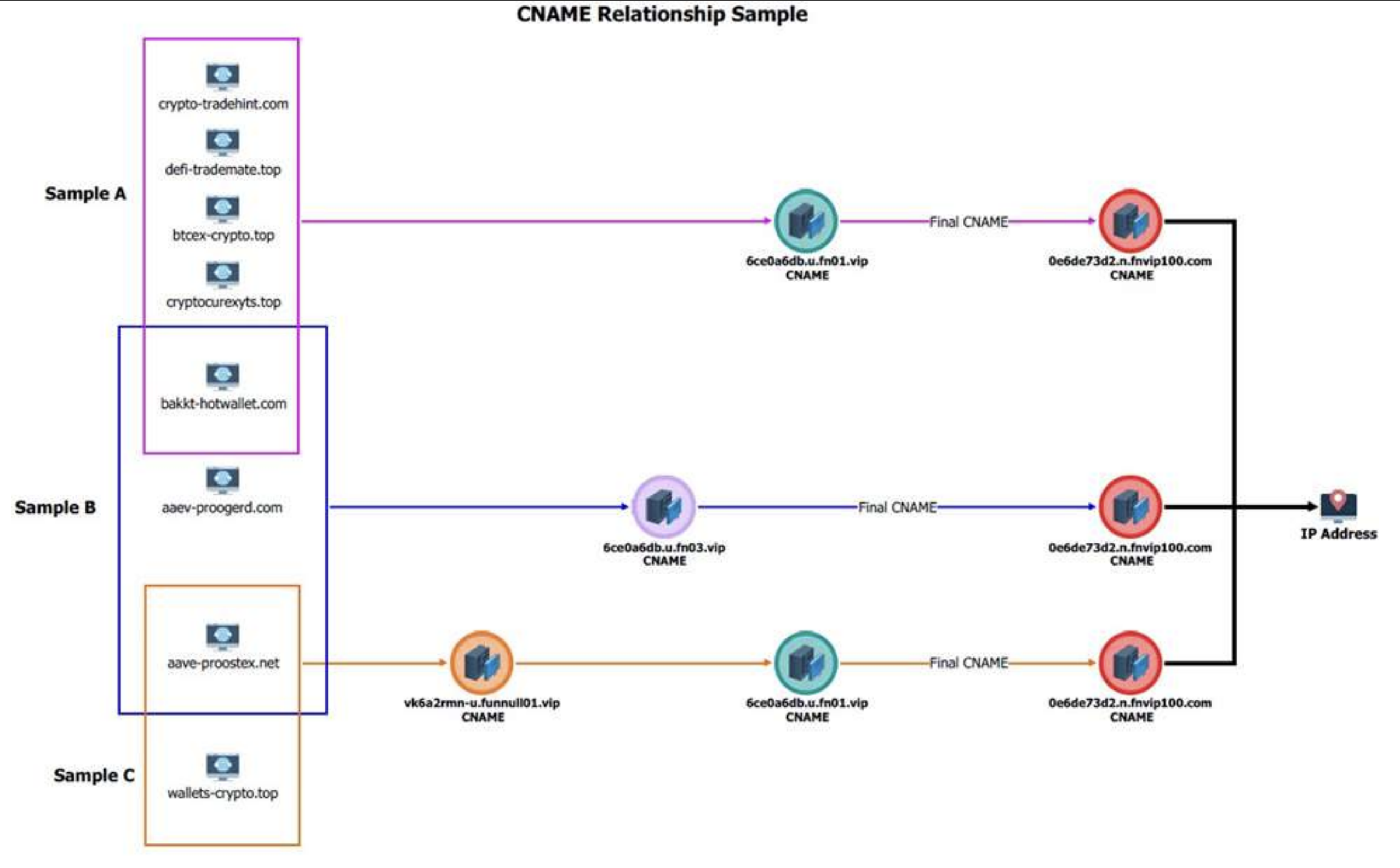
A graphic from the FBI illustrating how Funnull consistently produced a plethora of new domains and linked them to Internet addresses on U.S. cloud services.
Silent Push reassessed Funnull’s infrastructure in January 2025 and found that Funnull was still utilizing many of the same Amazon and Microsoft cloud Internet addresses recognized as harmful in its October report. Both Amazon and Microsoft vowed to eradicate Funnull’s presence from their networks following the report, but according to Silent Push’s Zach Edwards, only one of those companies has acted on that commitment.
Edwards noted that Silent Push no longer observes Microsoft Internet addresses appearing within Funnull’s infrastructure, while Amazon continues to face challenges in eliminating Funnull servers, including one that seems to have first appeared in 2023.
“Amazon is not performing adequately — daily since they made those assertions to you and us in our public blog, they have had IP addresses still associated with Funnull, including several that have persisted for inexplicable durations,” Edwards stated.
Amazon asserted that its Amazon Web Services (AWS) hosting platform actively counters abusive attempts.
“We have thwarted hundreds of attempts this year related to this group, and we are investigating the information you provided earlier today,” reads a statement shared by Amazon. “If anyone suspects that AWS resources are being employed for abusive activities, they can report it to AWS Trust & Safety using the report abuse form here.”
U.S.-based cloud providers remain a tempting home base for cybercriminal entities because many organizations are reluctant to proactively block traffic from U.S.-based cloud networks, as doing so can inadvertently block access to a multitude of legitimate web destinations that exist on the same shared network segment or host.
Moreover, funneling their malicious traffic so that it appears to originate from U.S. cloud Internet providers allows cybercriminals to connect to websites from web addresses that are geographically closer to their targets and victims (to bypass location-based security measures from banks, for instance).
Funnull is not the only cybercriminal infrastructure-as-a-service provider that faced sanctions this month: On May 20, 2025, the European Union imposed restrictions on Stark Industries Solutions, an ISP that emerged at the onset of Russia’s invasion of Ukraine and has been utilized as a global proxy network to conceal the actual source of cyberattacks and disinformation campaigns against adversaries of Russia.
In May 2024, KrebsOnSecurity published an in-depth analysis of Stark Industries Solutions that discovered much of the malicious traffic navigating Stark’s network (e.g. vulnerability scanning and password cracking attempts) was being routed through U.S.-based cloud services. My investigation revealed how extensively Stark had infiltrated U.S. ISPs, and that Ivan Neculiti had for many years marketed “bulletproof” hosting services stating that Russian cybercrime forum customers would not face any repercussions for abuse complaints or police inquiries.
The homepage of Stark Industries Solutions.
This investigation examined the background of Stark’s co-founders, Moldovan brothers Ivan and Yuri Neculiti, who each denied previous involvement in cybercrime or any current engagement in facilitating Russian disinformation campaigns or cyberattacks. Nevertheless, the EU sanctioned both siblings as well.
The EU asserted that Stark and the Neculiti brothers “enabled various Russian state-sponsored and state-affiliated entities to engage in destabilizing activities, including coordinated information manipulation and cyber-attacks against the Union and third countries by providing services designed to obscure these activities from European law enforcement and security agencies.”
“`

