A security architect employed by the National Labor Relations Board (NLRB) has asserted that personnel from Elon Musk‘s Department of Government Efficiency (DOGE) extracted gigabytes of confidential information from agency case files in early March, utilizing temporary accounts designed to minimize traces of their online actions. The NLRB whistleblower reported that these unusual significant data transfers coincided with various unsuccessful login attempts originating from an Internet address in Russia that attempted to access a newly-established DOGE user account using valid credentials.

The cover letter accompanying Berulis’s whistleblower statement, submitted to the leaders of the Senate Select Committee on Intelligence.
The accusations were outlined in a letter dated April 14 addressed to the Senate Select Committee on Intelligence, signed by Daniel J. Berulis, a 38-year-old security architect with the NLRB.
NPR, the first to disclose details regarding Berulis’s whistleblower complaint, notes that the NLRB is a small, autonomous federal organization that investigates and resolves accusations of unfair labor practices, maintaining “vast quantities of potentially sensitive data, spanning confidential information regarding employees aspiring to form unions to proprietary business intelligence.”
The complaint chronicles a month-long span commencing on March 3, during which DOGE officials allegedly insisted on the establishment of all-powerful “tenant admin” accounts in NLRB systems that would be excluded from standard network logging that would typically maintain a comprehensive record of all activities performed by those accounts.
Berulis indicated that the newly created DOGE accounts were granted unrestricted rights to view, copy, and modify information within NLRB databases. Furthermore, these accounts could limit log visibility, delay data retention, redirect logs to other locations, or even erase them completely — privileges that neither Berulis nor his supervisor held.
Berulis recounted that on March 3, a black SUV with a police escort arrived at the NLRB headquarters in Southeast Washington, D.C. The DOGE representatives did not converse with Berulis or any other IT staff at the NLRB, instead choosing to meet with the agency executives.
“Our acting chief information officer instructed us to disregard standard operating procedures for the creation of the DOGE accounts, emphasizing that there would be no logs or records compiled of the accounts established for DOGE employees, who required the utmost access privileges,” Berulis documented about their directives following that meeting.
“We have roles established that auditors have utilized extensively in the past but would not grant the capacity to alter or access subsystems without prior approval,” he elaborated. “The proposal for them to use these accounts was non-negotiable.”
On March 3, Berulis observed that one of the DOGE accounts created an obscure virtual environment referred to as a “container,” which can be employed to develop and execute programs or scripts without disclosing its activities to external observers. He noted that this container captured his interest since he consulted with his colleagues and discovered that none had previously employed containers within the NLRB network.
Moreover, Berulis detected that early the subsequent morning — between roughly 3 a.m. and 4 a.m. EST on Tuesday, March 4 — there was a significant surge in outbound network traffic from the agency. He stated that it took several days of inquiry with his colleagues to ascertain that one of the new accounts had transferred approximately 10 gigabytes of data from the NLRB’s NxGen case management system.
According to Berulis, neither he nor his co-workers possessed the necessary network permissions to examine which files were accessed or moved — or even where they were sent. However, his complaint emphasizes that the NxGen database holds sensitive data concerning unions, ongoing legal matters, and corporate trade secrets.
“I also remain uncertain whether the data amounted to only 10gb in total or if it had been consolidated and compressed prior,” Berulis informed the senators. “This raises the possibility that even greater quantities of data were exfiltrated. Regardless, such an increase is exceedingly unusual as data almost never departs from the NLRB’s databases.”
Berulis mentioned that he and his colleagues became increasingly concerned when they identified nearly two dozen login attempts from a Russian Internet address (83.149.30,186) that utilized valid credentials for a DOGE employee account — one that had been established merely minutes before. Berulis noted that those attempts were thwarted due to existing regulations that block logins from non-U.S. locations.
“The individual attempting to log in appeared to be utilizing one of the newly created accounts associated with other DOGE activities, and it seemed they had the correct username and password, as the authentication mechanism only prevented them through our no-out-of-country login policy being activated,” Berulis explained. “There were over 20 such attempts, and what is particularly alarming is that many of these login attempts transpired within 15 minutes of the DOGE engineers creating the accounts.”
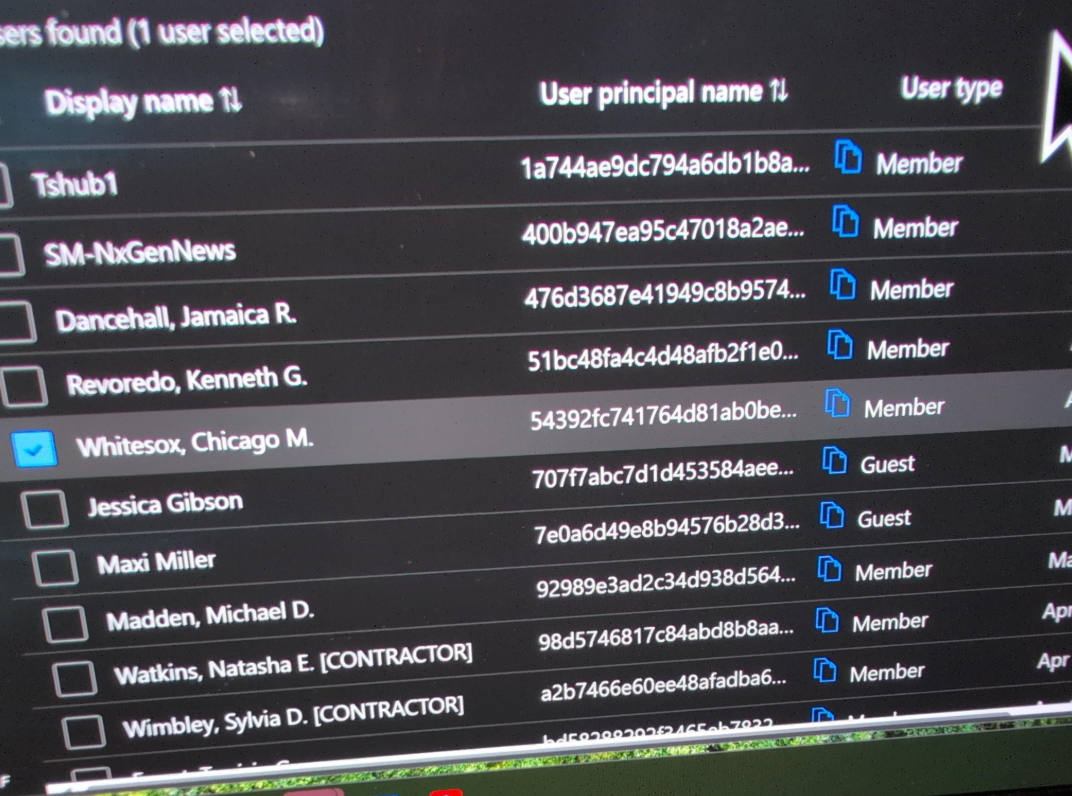
As Berulis observed, the naming format of one Microsoft user account related to the questionable activity indicated it had been set up and later deleted for DOGE utilization in the NLRB’s cloud platforms: “[email protected].” He also uncovered additional new Microsoft cloud administrator accounts with unusual usernames, such as “Whitesox, Chicago M.” and “Dancehall, Jamaica R.”
On March 5, Berulis documented that a significant portion of logs for recently established network resources was absent, and a network monitor in Microsoft Azure had been disabled, meaning it was no longer collecting and recording data as it should.
Berulis reported that someone had downloaded three external code libraries from GitHub, which neither the NLRB nor its contractors had ever employed. A “readme” file within one of the code bundles clarified that it was designed to rotate connections through an extensive pool of cloud Internet addresses serving “as a proxy to create pseudo-infinite IPs for web scraping and brute force attacks.” Brute force attacks consist of automated login attempts that rapidly try numerous combinations of credentials.
The complaint asserts that by March 17 it became evident the NLRB lacked the resources or network access necessary to fully investigate the unusual activities stemming from the DOGE accounts, and that on March 24, the agency’s associate chief information officer had concurred that the issue should be reported to US-CERT. Managed by the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA), US-CERT provides on-site cyber incident response support to federal and state entities.
However, Berulis stated that between April 3 and4, he along with the deputy CIO were advised that “orders had been issued to cease the US-CERT reporting and inquiries, and we were instructed not to proceed or generate an official documentation.” Berulis mentioned that it was at that moment he chose to disclose his findings publicly.
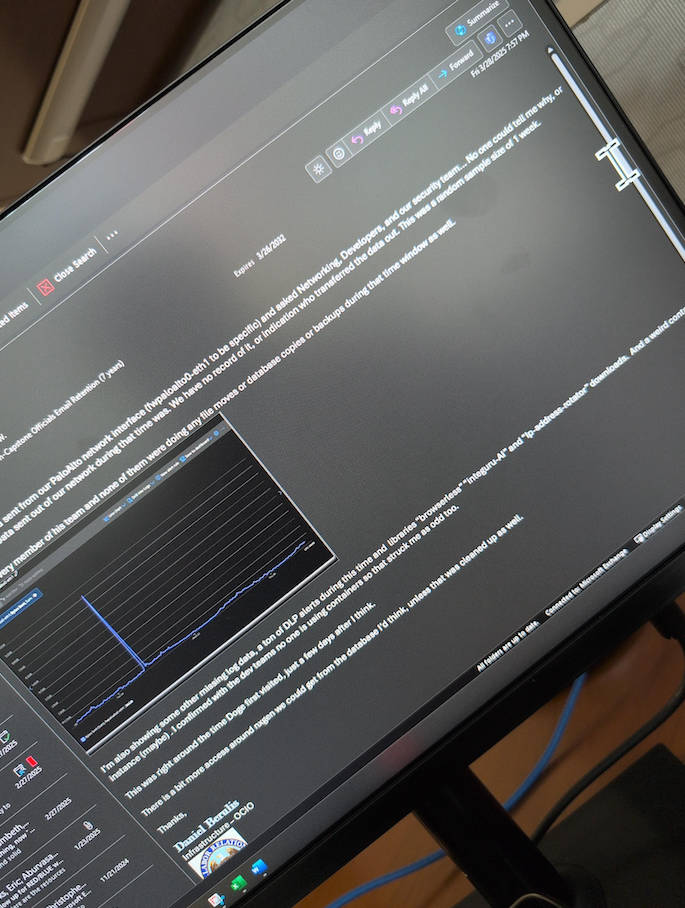
An email from Daniel Berulis to his colleagues dated March 28, referencing the obscure traffic spike observed earlier in the month and the unauthorized modification of security protocols for user accounts.
Tim Bearese, the acting press spokesperson for the NLRB, informed NPR that DOGE neither solicited nor obtained access to its systems, and that “the agency performed an investigation after Berulis brought his concerns to light but ‘ascertained that no breach of agency systems occurred.’” The NLRB did not reply to inquiries from KrebsOnSecurity.
Nonetheless, Berulis has provided several supporting screenshots highlighting agency email exchanges about the unaccounted account activity linked to the DOGE accounts, along with NLRB security alerts from Microsoft regarding network irregularities noted during the described timeframes.
As CNN reported last month, the NLRB has been significantly impaired since President Trump dismissed three board members, resulting in the agency lacking the quorum necessary for it to operate.
“Despite its restrictions, the agency had become a nuisance to some of the wealthiest and most influential individuals in the country — notably Elon Musk, Trump’s major supporter both financially and arguably politically,” CNN stated.
Both Amazon and Musk’s SpaceX have filed lawsuits against the NLRB over allegations the agency made in disputes regarding workers’ rights and union organizing, contending that the very existence of the NLRB is unconstitutional. On March 5, a U.S. appeals court unanimously dismissed Musk’s assertion that the NLRB’s structure in any way contravenes the Constitution.
Berulis revealed screenshots to KrebsOnSecurity demonstrating that on the day NPR published its article regarding his claims (April 14), the deputy CIO at NLRB sent a message stating that administrative privileges had been revoked from all employee accounts. This meant that, abruptly, none of the IT personnel at the agency were able to perform their jobs effectively anymore, Berulis explained.
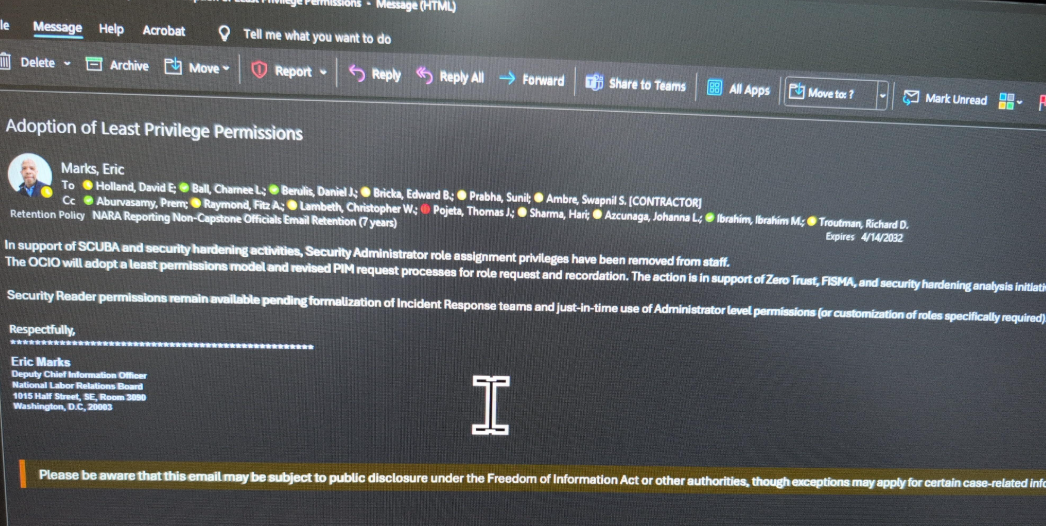
An email from the NLRB’s associate chief information officer Eric Marks, informing employees they will lose their security administrator privileges.
Berulis provided a screenshot of an agency-wide email dated April 16 from NLRB director Lasharn Hamilton stating that DOGE officials had sought a meeting, and reiterating claims that the agency had not had any previous “official” contact with any DOGE personnel. The communication informed NLRB staff that two DOGE representatives would be assigned to the agency part-time for several months.
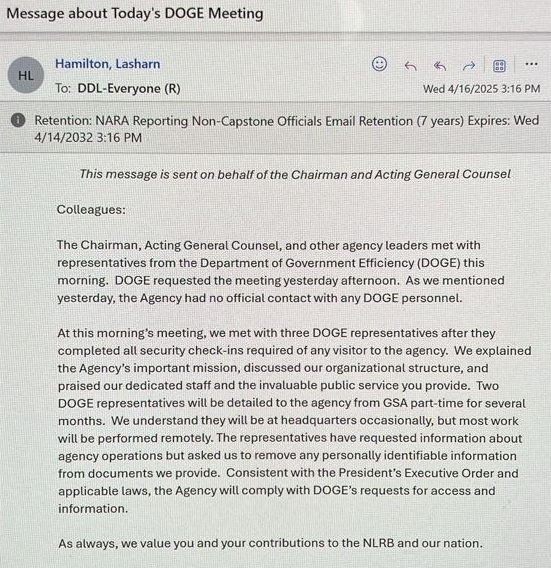
An email from NLRB Director Lasharn Hamilton on April 16, indicating that the agency previously had no interaction with DOGE personnel.
Berulis told KrebsOnSecurity he was in the midst of submitting a support ticket to Microsoft for further details about the DOGE accounts when his network administrator privileges were curtailed. Currently, he hopes that lawmakers will request Microsoft to disclose more information regarding what genuinely transpired with the accounts.
“That would provide us significantly more clarity,” he stated. “Microsoft should have a clearer picture than we do. That’s my aim, at any rate.”
Berulis’s attorney informed lawmakers that on April 7, while his client and legal team were finalizing the whistleblower complaint, someone physically affixed a menacing note to Mr. Berulis’s home entrance, accompanied by photographs — captured via drone — of him strolling in his neighborhood.
“The intimidating note made explicit reference to the very disclosure he was preparing for you, as the appropriate oversight authority,” reads a preamble by Berulis’s attorney Andrew P. Bakaj. “While we do not know explicitly who executed this act, we can only speculate that it involved someone with the capability to access NLRB systems.”
Berulis mentioned that the reactions from friends, colleagues, and even the public have generally been affirmative, and that he does not regret his decision to speak out.
“I didn’t anticipate the note on my door or the backlash from [agency] leaders,” he remarked. “If I had to do it over again, would I make the same choice? Yes, because it wasn’t really even an option the first time.”
At present, Mr. Berulis is on some paid family leave from the NLRB. Which is perhaps for the best, he noted, considering he was deprived of the resources necessary to fulfill his duties at the agency.
“They came in and took complete administrative control and locked everyone out, indicating that limited access will be assigned on a necessity basis moving forward,” Berulis explained regarding the DOGE employees. “We can’t really accomplish anything, so we’re literally being paid to count ceiling tiles.”
Further reading: Berulis’s complaint (PDF).