Inhabitants throughout the United States are overwhelmed with text alerts claiming to originate from toll road operators such as E-ZPass, cautioning that recipients may incur fines if an outstanding toll charge goes unsettled. Analysts indicate that the increase in SMS spam aligns with new functionalities added to a widely-used phishing kit marketed in China, facilitating the establishment of convincing traps impersonating toll road operators across several U.S. states.
Last week, the Massachusetts Department of Transportation (MassDOT) alerted residents to remain vigilant against a fresh SMS phishing scheme, or “smishing,” aimed at users of EZDriveMA, MassDOT’s all-digital tolling initiative. Those who succumb to the scam are prompted to submit payment card information and will ultimately be requested to provide a one-time password dispatched via SMS or a mobile verification application.
Reports detailing comparable SMS phishing schemes targeting patrons of other state-operated toll facilities in the U.S. emerged around the same time as the MassDOT warning. Residents in Florida noted receiving SMS phishing messages impersonating Sunpass, Florida’s prepaid tolling system.

This phishing module designed for mimicking MassDOT’s EZDrive toll system was released on Jan. 10, 2025, by an SMS phishing service based in China, known as “Lighthouse.”
In Texas, locals reported receiving text alerts regarding unpaid tolls from the North Texas Toll Authority. Similar accounts were reported by individuals in California, Colorado, Connecticut, Minnesota, and Washington. This certainly isn’t an exhaustive enumeration.
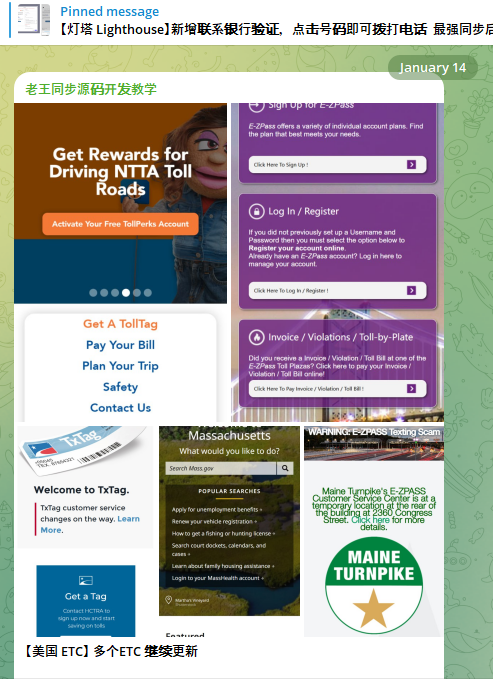
A new module from the Lighthouse SMS phishing kit launched on Jan. 14 specifically targets users of the North Texas Toll Authority (NTTA).
In each instance, the rise of these SMS phishing attacks corresponds with the introduction of new capabilities within phishing kits that closely replicate toll operator websites as viewed on mobile devices. Notably, none of the phishing pages will load unless the site identifies that the visitor is utilizing a mobile device.
Ford Merrill is involved in security research at SecAlliance, a division of CSIS Security Group. According to Merrill, the occurrence of SMS phishing schemes impersonating toll road operators dramatically increased after the New Year, when at least one Chinese cybercriminal organization known for distributing advanced SMS phishing kits began presenting new phishing pages crafted to mimic toll operators in several U.S. states.
Merrill noted that numerous cybercriminals based in China are peddling various SMS-based phishing kits, each with hundreds or thousands of clients. Their primary objective, he stated, is to extract sufficient data from victims so that their payment cards could be incorporated into digital wallets and utilized for purchases at retail locations, online shopping, or laundering funds through shell companies.
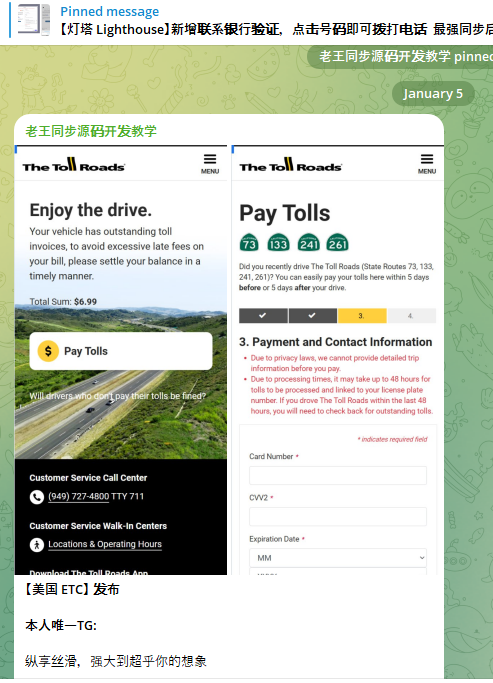
A segment of the Chinese SMS phishing kit Lighthouse created to target patrons of The Toll Roads, which covers several state routes in Orange County, California.
Merrill explained that different vendors of these SMS phishing tools have typically impersonated shipping firms, customs agencies, and even governmental entities with tax refund schemes and visa or immigration renewal scams aimed at individuals who may be living abroad or new to a country.
“What we’re observing with these toll scams is merely an extension of the Chinese smishing groups transitioning from package redelivery frauds to toll road scams,” Merrill commented. “By this point, everyone is fed up with these package smishing schemes, so now it has taken a new twist on a familiar scam.”
In October 2023, KrebsOnSecurity covered a significant rise in SMS phishing scams targeting U.S. Postal Service clients. This report revealed that this surge was associated with advancements introduced by “Chenlun,” a proprietor in mainland China known for a popular phishing kit and service. At the time, Chenlun had recently rolled out new phishing pages intended to impersonate postal services in the United States and at least a dozen other nations.
Though SMS phishing kits are not novel, Merrill stated that Chinese smishing groups have recently implemented innovations in their delivery capabilities, more effectively integrating their spam communications with Apple’s iMessage technology, and with RCS, the analogous “rich text” messaging feature embedded within Android devices.
“While conventional smishing kits relied predominantly on SMS for dissemination, modern actors extensively utilize iMessage and RCS because telecom providers struggle to filter them, and these channels likely yield a higher success rate,” he explained.
It remains uncertain how phishers determine their targets or where their data might be obtained. A warning from MassDOT states that “the targeted phone numbers appear to be selected randomly and are not specifically linked to an account or usage of toll roads.”
Indeed, one individual mentioned on Mastodon yesterday that they received one of these SMS phishing attacks impersonating a local toll operator, despite not owning a vehicle.
Whether targeted or not, these phishing websites pose significant risks as they are continuously operated in real-time by criminals. If you receive one of these messages, it is advisable to disregard it or delete it, but please refrain from visiting the phishing site. The FBI urges anyone to consider filing a complaint with the agency’s Internet Crime Complaint Center (IC3) before discarding the messages, providing the phone number from which the text was sent and the web address included within the text.

