“`html
A cybercriminal collective that employed voice phishing tactics to extract over a billion records from Salesforce clientele earlier this year has established a site threatening to disclose data pilfered from numerous Fortune 500 companies if they decline to settle a ransom. The group also asserted responsibility for a recent breach concerning Discord user information, alongside stealing terabytes of confidential documents from thousands of clients of the enterprise software provider Red Hat.
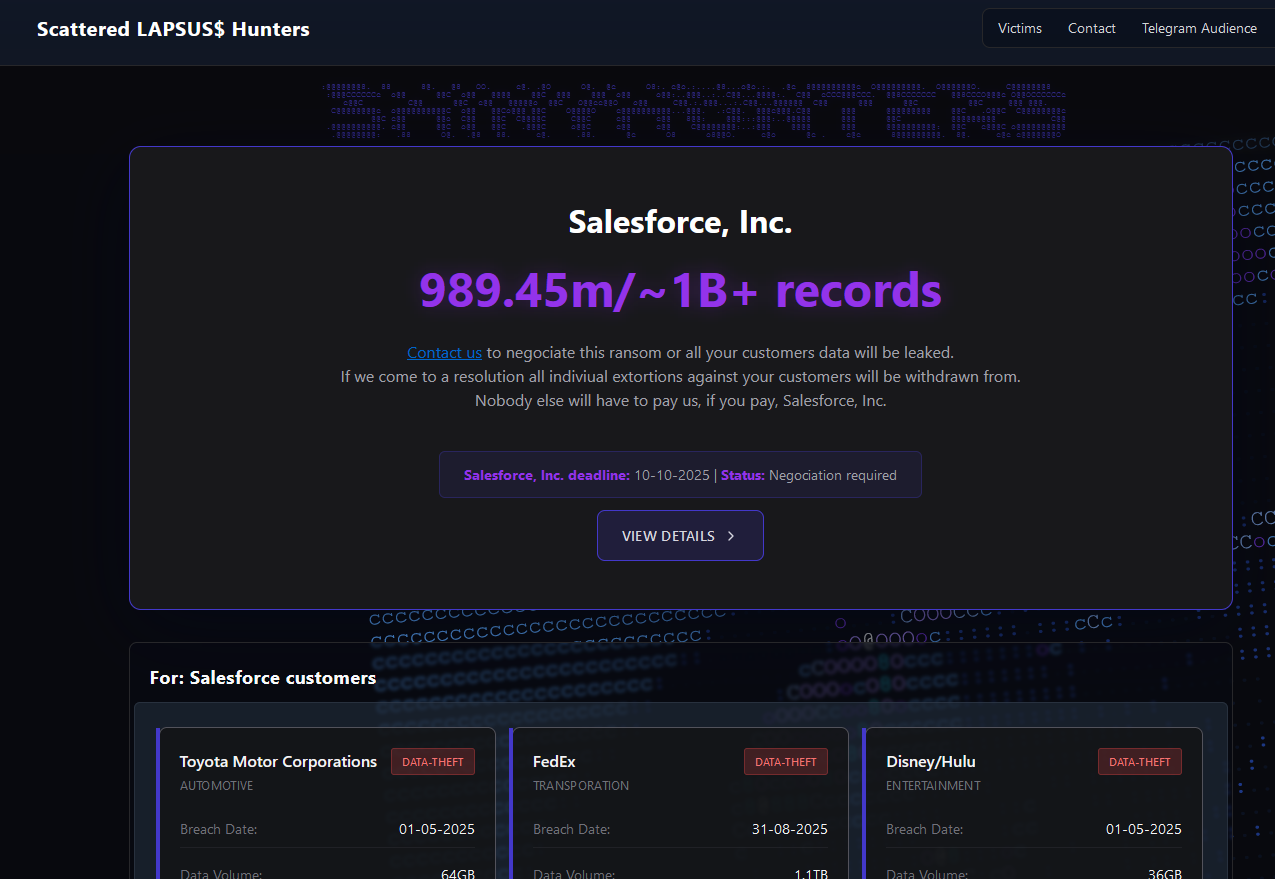
The new extortion platform associated with ShinyHunters (UNC6040), which threatens to reveal stolen information unless Salesforce or individual targeted firms comply with ransom demands.
In May 2025, a prolific and fluid English-speaking cybercrime organization labeled ShinyHunters initiated a social engineering scheme that utilized voice phishing to deceive targets into linking a malicious application to their organization’s Salesforce portal.
The initial concrete information regarding the incident was reported in early June, when the Google Threat Intelligence Group (GTIG) alerted that ShinyHunters — tracked by Google as UNC6040 — was coercing victims over their compromised Salesforce data, and that the group was preparing to launch a data leak site aimed at publicly shaming victimized companies into complying with ransom requests to maintain their records’ confidentiality. A month later, Google admitted that one of its own corporate Salesforce instances was affected by the voice phishing scheme.
Last week, a new victim-shaming blog entitled “Scattered LAPSUS$ Hunters” commenced revealing the identities of firms that had customer Salesforce data appropriated due to the May voice phishing operation.
“Reach out to us to arrange this ransom or all your customers’ information will be disclosed,” the site communicated in a message directed at Salesforce. “If we come to an agreement, all individual extortion attempts against your customers will be rescinded. No one else will need to compensate us if you pay, Salesforce, Inc.”
Below that declaration were over three dozen listings for companies claimed to have had Salesforce data misappropriated, including Toyota, FedEx, Disney/Hulu, and UPS. Each company’s entry detailed the quantity of stolen data available, as well as the date the information was obtained (the alleged breach dates range from May to September 2025).
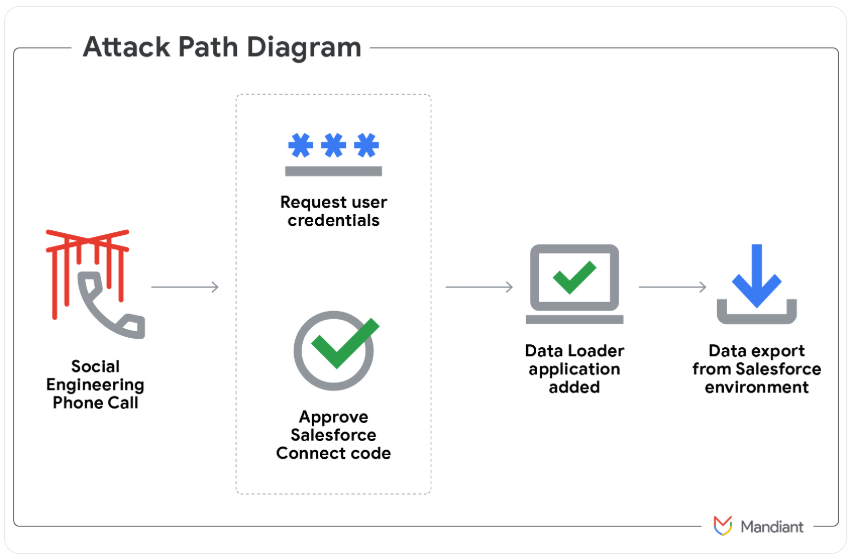
Image: Mandiant.
On October 5, the Scattered LAPSUS$ Hunters victim-shaming and extortion blog proclaimed that the group was accountable for a breach in September involving a GitLab server utilized by Red Hat that housed over 28,000 Git code repositories, inclusive of more than 5,000 Customer Engagement Reports (CERs).
“Many folders contain their clients’ confidential information, such as artifactory access tokens, git tokens, Azure, Docker (Red Hat Docker, Azure containers, Docker Hub), and their clients’ infrastructure details in the CERs like the audits conducted for them, amongst a plethora of other information,” the hackers contended.
Their assertions surfaced several days after an unfamiliar hacker collective identifying itself as the Crimson Collective took responsibility for the Red Hat compromise on Telegram.
Red Hat announced on October 2 that assailants had breached a company GitLab server, and indicated that they were in the process of notifying impacted clients.
“The breached GitLab instance contained consulting engagement data, which may encompass, for instance, Red Hat’s project specifications, sample code snippets, internal discussions regarding consulting services, and limited forms of business contact details,” Red Hat stated.
In a separate incident, Discord has begun informing users affected by another breach attributed to ShinyHunters. Discord reported that an incident on September 20 involving a “third-party customer service provider” affected a “limited number of users” who interacted with Discord’s customer support or Trust & Safety teams. The compromised information included Discord usernames, emails, IP addresses, the last four digits of any stored payment cards, and government ID images submitted during age verification challenges.
The Scattered Lapsus$ Hunters allege they will make public data misappropriated from Salesforce and its clientele if ransom requests are not satisfied by October 10. The group further asserts it will soon begin extorting hundreds of additional organizations that suffered data loss in August following a cybercrime group appropriating extensive amounts of authentication tokens from Salesloft, whose AI chatbot is leveraged by many corporate websites to transform customer interactions into Salesforce leads.
In a message circulated to customers today, Salesforce underscored that the theft of any third-party Salesloft data allegedly acquired by ShinyHunters did not stem from a flaw within the core Salesforce platform. The company also highlighted that it has no intention of complying with any extortion demands.
“Salesforce will not engage, negotiate with, or fulfill any extortion demands,” the message to customers stated. “Our priority is, and continues to be, defending our environment, conducting comprehensive forensic analyses, supporting our customers, and collaborating with law enforcement and regulatory bodies.”
The GTIG monitored the group behind the Salesloft data thefts as UNC6395, and states this group has been seen collecting data for authentication tokens associated with various cloud services like Snowflake and Amazon’s AWS.
Google categorizes Scattered Lapsus$ Hunters under several UNC identities (including UNC6240 for good measure) as it is believed to be a coalition of three hacking factions — Scattered Spider, Lapsus$, and ShinyHunters. The members of these factions originate from many of the same chat channels on the Com, a primarily English-language cybercriminal community operating across various Telegram and Discord servers.
The Scattered Lapsus$ Hunters darknet blog is currently inaccessible. The outage seems to align with the disappearance of the group’s new clearnet blog — breachforums[.]hn — which vanished after relocating its Domain Name Service (DNS) servers from DDoS-Guard to Cloudflare.
However, before it ceased operations, the sites revealed that hackers were taking advantage of a critical zero-day vulnerability in Oracle’s E-Business Suite software. Oracle has since confirmed that a security defect tracked as CVE-2025-61882 enables attackers to execute unauthenticated remote code, and is urging customers.
“““html
to implement an urgent update to rectify the vulnerability.
Mandiant’s Charles Carmichael posted on LinkedIn that CVE-2025-61882 was first exploited in August 2025 by the Clop ransomware group to extract data from Oracle E-Business Suite servers. Bleeping Computer reports that the revelation of the Oracle zero-day initially emerged on the Scattered Lapsus$ Hunters blog, which shared a pair of scripts that were deployed to exploit susceptible Oracle E-Business Suite instances.
On Monday evening, KrebsOnSecurity received a malware-infested message from a reader that threatened bodily harm unless their unspecified requests were fulfilled. The correspondence, titled “Shiny hunters,” featured the hashtag $LAPSU$$SCATEREDHUNTER, and urged me to visit a page on limewire[.]com to check their demands.
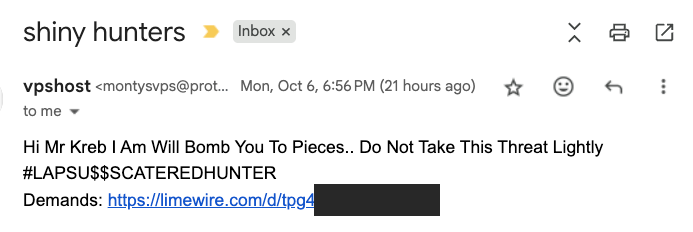
A screenshot of the phishing message directing to a harmful trojan masquerading as a Windows screenshot file.
KrebsOnSecurity refrained from accessing this link, opting instead to forward it to Mandiant, which confirmed that similar threatening messages were dispatched to employees at Mandiant and other security organizations around the same timeframe.
The link within the message retrieves a harmful trojan camouflaged as a Windows screenshot file (Virustotal’s evaluation of this malware is here). Merely viewing the compromised screenshot image on a Windows PC is sufficient to trigger the bundled trojan in the background.
Mandiant’s Austin Larsen indicated that the trojan is a commercially available backdoor named ASYNCRAT, a .NET-based backdoor that communicates via a bespoke binary protocol over TCP, with the capability to execute shell commands and download plugins to augment its functionalities.
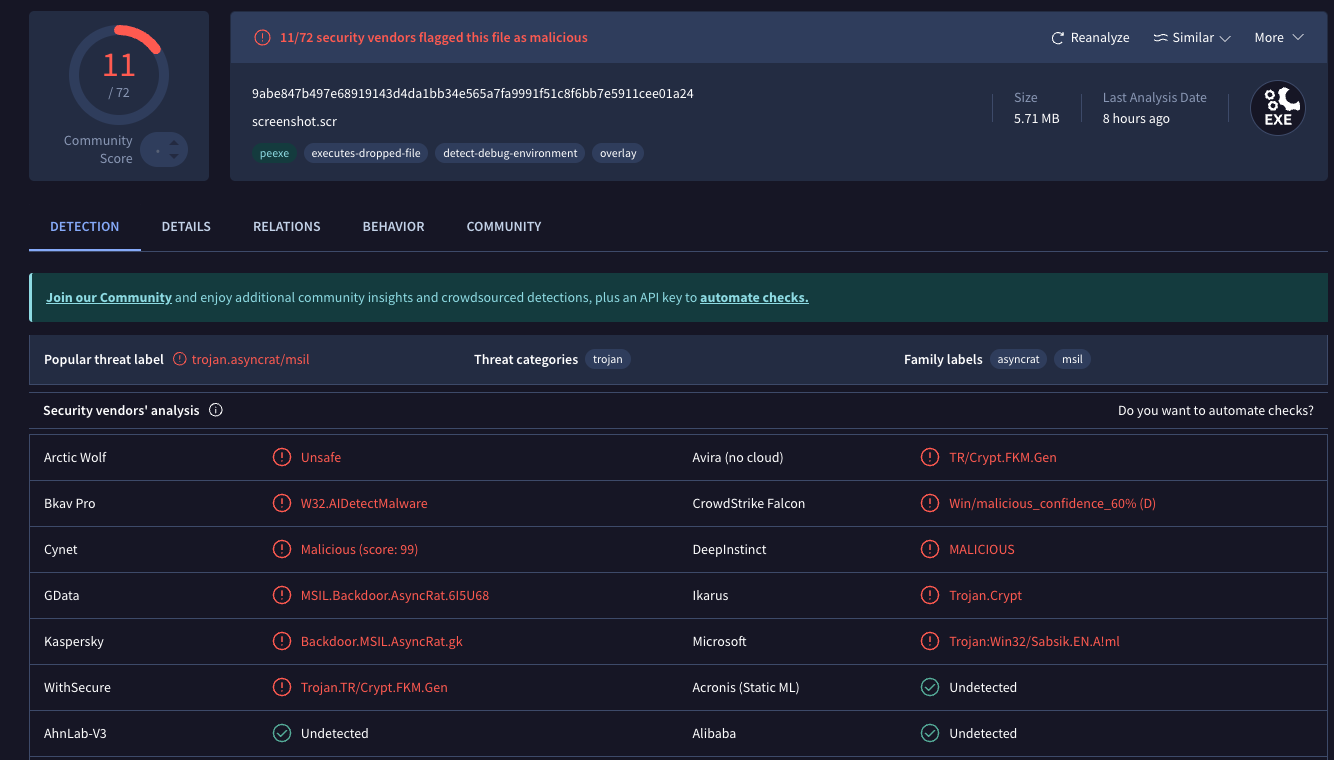
A scan of the malicious screenshot file at Virustotal.com indicates it is identified as harmful by nearly a dozen security and antivirus applications.
“Downloaded plugins can be executed directly in memory or saved in the registry,” Larsen explained in an analysis circulated via email. “Features added through plugins include screenshot capture, file transfer, keylogging, video capture, and cryptocurrency mining. ASYNCRAT also accommodates a plugin that targets login credentials stored by Firefox and Chromium-based web browsers.”
Malware-infested targeted emails are not uncommon for certain individuals associated with the Scattered Lapsus$ Hunters, who have previously intimidated and threatened security researchers and even law enforcement officials investigating and warning about the extent of their actions.
With numerous substantial data breaches and ransom assaults now emerging from cybercrime groups operating on the Com, law enforcement agencies on both sides of the Atlantic are under mounting pressure to capture the criminal hackers involved. In late September, prosecutors in the U.K. accused two alleged Scattered Spider members aged 18 and 19 of extorting at least $115 million in ransom payouts from businesses victimized by data theft.
U.S. prosecutors added their own charges against the 19-year-old in that duo — U.K. resident Thalha Jubair — who is accused of involvement in data ransom attacks against Marks & Spencer and Harrods, the British footwear retailer Co-op Group, as well as the 2023 breaches at MGM Resorts and Caesars Entertainment. Jubair was also purportedly a central figure in LAPSUS$, a cybercrime collective that infiltrated numerous technology companies starting in late 2021.
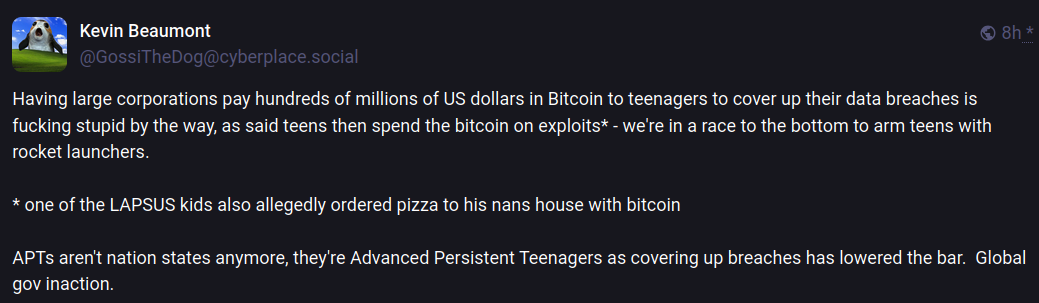
A Mastodon post by Kevin Beaumont, bemoaning the tendency of major corporations to pay millions to extortionist teen hackers, mockingly refers to Thalha Jubair as part of an APT threat known as “Advanced Persistent Teenagers.”
In August, convicted Scattered Spider affiliate and 20-year-old Florida resident Noah Michael Urban was sentenced to 10 years in federal prison and mandated to pay roughly $13 million in restitution to victims.
In April 2025, a 23-year-old Scottish individual believed to be an early member of Scattered Spider was extradited from Spain to the U.S., where he faces charges of wire fraud, conspiracy, and identity theft. U.S. prosecutors assert that Tyler Robert Buchanan and co-conspirators hacked into numerous companies within the United States and internationally, alleging that he specifically controlled over $26 million pilfered from victims.
“`