“`html
The recent widespread theft of authentication tokens from Salesloft, whose AI chatbot is utilized by a vast array of corporate America to transform customer engagement into Salesforce leads, has prompted numerous companies to scramble to invalidate the compromised credentials before cybercriminals can take advantage of them. Now Google cautions that the breach extends well beyond access to Salesforce data, emphasizing that the hackers involved also pilfered valid authentication tokens for hundreds of online platforms that clients can link with Salesloft, such as Slack, Google Workspace, Amazon S3, Microsoft Azure, and OpenAI.

Salesloft asserts that its products are relied upon by over 5,000 clients. Some of the more prominent names are displayed on the company’s homepage.
Salesloft announced on August 20 that, “Today, we identified a security concern in the Drift application,” referencing the technology that powers an AI chatbot utilized by many corporate websites. The notification urged clients to re-authenticate the link between the Drift and Salesforce applications to invalidate their current authentication tokens, but did not indicate at that time that those tokens had already been compromised.
On August 26, the Google Threat Intelligence Group (GTIG) alerted that unidentified cybercriminals tracked as UNC6395 utilized the access tokens stolen from Salesloft to extract substantial amounts of data from various corporate Salesforce instances. Google noted that the data breach commenced as early as Aug. 8, 2025, and continued through at least Aug. 18, 2025, and that the incident did not involve any vulnerabilities within the Salesforce platform.
Google indicated that the attackers have been examining the massive data cache for credentials such as AWS keys, VPN details, and access for the cloud storage provider Snowflake.
“If successful, the appropriate credentials could enable them to further compromise victim and client environments, as well as pivot to the victim’s clients or partner systems,” the GTIG report highlighted.
The GTIG updated its guidance on August 28 to acknowledge that the attackers used the stolen tokens to access email from “a very limited number of Google Workstation accounts” that were specifically configured to work with Salesloft. More critically, it cautioned organizations to promptly invalidate all tokens stored in or linked to their Salesloft integrations — irrespective of the third-party service involved.
“Given GTIG’s observations of data exfiltration tied to the campaign, organizations employing Salesloft Drift to integrate with third-party platforms (including but not limited to Salesforce) should regard their data as compromised and are strongly advised to take immediate remedial actions,” Google recommended.
On August 28, Salesforce prohibited Drift from connecting with its platform, along with its productivity services Slack and Pardot.
The Salesloft incident follows a sweeping social engineering campaign that employed voice phishing to deceive targets into linking a malicious app to their organization’s Salesforce portal. That campaign resulted in data breaches and extortion attacks impacting several companies, including Adidas, Allianz Life, and Qantas.
On August 5, Google revealed that one of its corporate Salesforce instances was infiltrated by the attackers, which the GTIG has labeled UNC6040 (“UNC” is Google’s abbreviation for “uncategorized threat group”). Google stated that the extortionists regularly claimed to be the threat group ShinyHunters and that the group seemed poised to escalate its extortion efforts by establishing a data leak site.
ShinyHunters is a nebulous threat group recognized for utilizing social engineering to infiltrate cloud platforms and third-party IT providers, as well as for posting numerous stolen databases to cybercrime forums like the now-defunct Breachforums.
The ShinyHunters name has been in use since 2020, and the group has been credited with or has taken responsibility for numerous data leaks that exposed hundreds of millions of compromised records. The group’s member base is believed to be somewhat fluid, primarily drawing from active members within the Com, a predominantly English-language cybercrime collective spread across an ocean of Telegram and Discord servers.
Recorded Future’s Alan Liska informed Bleeping Computer that the overlap in the “tools, techniques, and procedures” employed by ShinyHunters and the Scattered Spider extortion group likely suggests some collaboration between the two groups.
To further cloud the situation, on August 28, a Telegram channel that now boasts nearly 40,000 subscribers was launched under the deliberately misleading title “Scattered LAPSUS$ Hunters 4.0,” wherein participants have repeatedly asserted their involvement in the Salesloft breach without actually providing any evidence to substantiate their claims.
The Telegram group has sought to draw media attention by threatening security researchers at Google and other firms. It is also leveraging the channel’s sudden popularity to promote a new cybercrime forum called “Breachstars,” which they assert will soon host data stolen from victimized companies that refuse to engage in ransom negotiations.
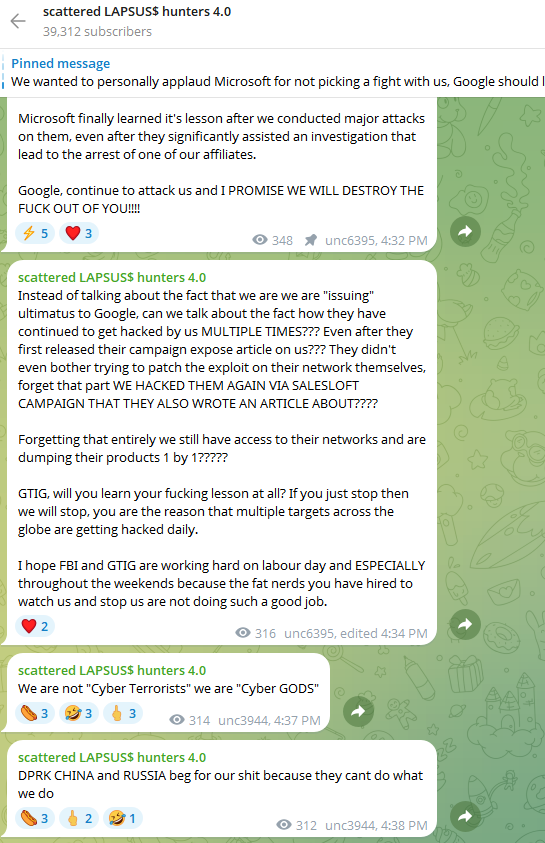
The “Scattered Lapsus$ Hunters 4.0” channel on Telegram now has roughly 40,000 followers.
However, Austin Larsen, a principal threat analyst at Google’s threat intelligence group, stated that there is no convincing evidence to link the Salesloft activities to ShinyHunters or any other known groups at this juncture.
“Their grasp of the incident seems to be derived solely from public reporting,” Larsen remarked to KrebsOnSecurity, referring to the most active participants in the Scattered LAPSUS$ Hunters 4.0 Telegram channel.
Joshua Wright, a senior technical director at Counter Hack, is credited with coining the term “authorization sprawl” to describe a key factor that enables social engineering attacks from groups like Scattered Spider and ShinyHunters to frequently succeed: They exploit legitimate user access tokens to navigate seamlessly between on-premises and cloud systems.
Wright noted that this attack methodology often goes undetected because the attacker adheres to the resources and access already granted to the user.
“Rather than following the conventional path of initial access, privilege escalation, and endpoint bypass, these threat actors leverage centralized identity platforms that provide single sign-on (SSO) and integrated authentication and authorization systems,” Wright wrote in a June 2025 column. “Instead of crafting custom malware, attackers utilize the resources already accessible to them as authorized users.”
It remains unclear exactly how the attackers obtained access to all Salesloft Drift authentication tokens. Salesloft announced on August 27 that it enlisted Mandiant, Google Cloud’s incident response division, to probe the root cause(s).
“We are collaborating with Salesloft Drift to analyze the root cause of what transpired, and thereafter it will be their responsibility to disseminate that information,” Mandiant Consulting CTO Charles Carmakal told Cyberscoop. “There will be much more information forthcoming tomorrow, the day after, and the day following.”
“`

