A 22-year-old man from Oregon has been apprehended on charges of managing “Rapper Bot,” a significant botnet employed to facilitate a service for executing distributed denial-of-service (DDoS) assaults on various targets — including a DDoS incident in March 2025 that disrupted Twitter/X. The Justice Department claims that the accused and an unspecified accomplice leased the botnet to online extortionists, making efforts to evade detection by law enforcement by ensuring their botnet was never aimed at KrebsOnSecurity.
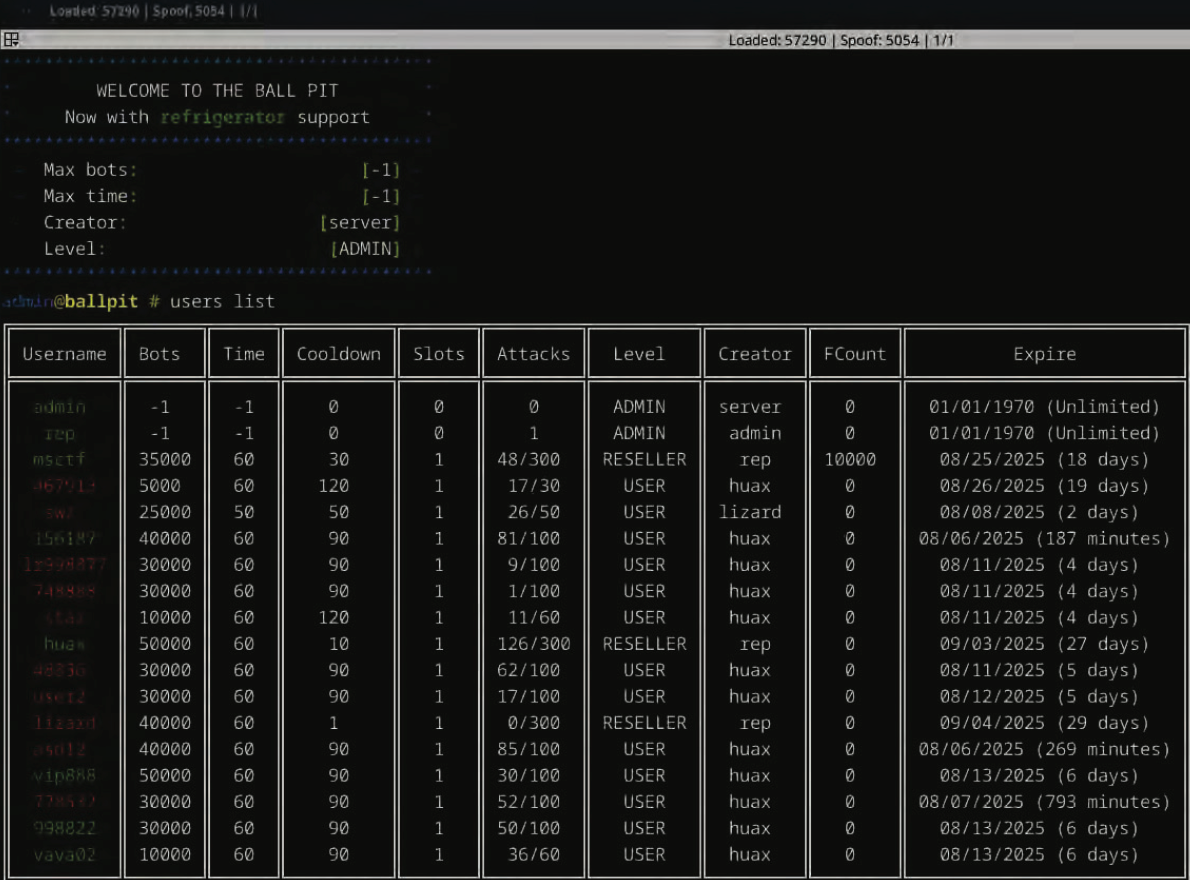
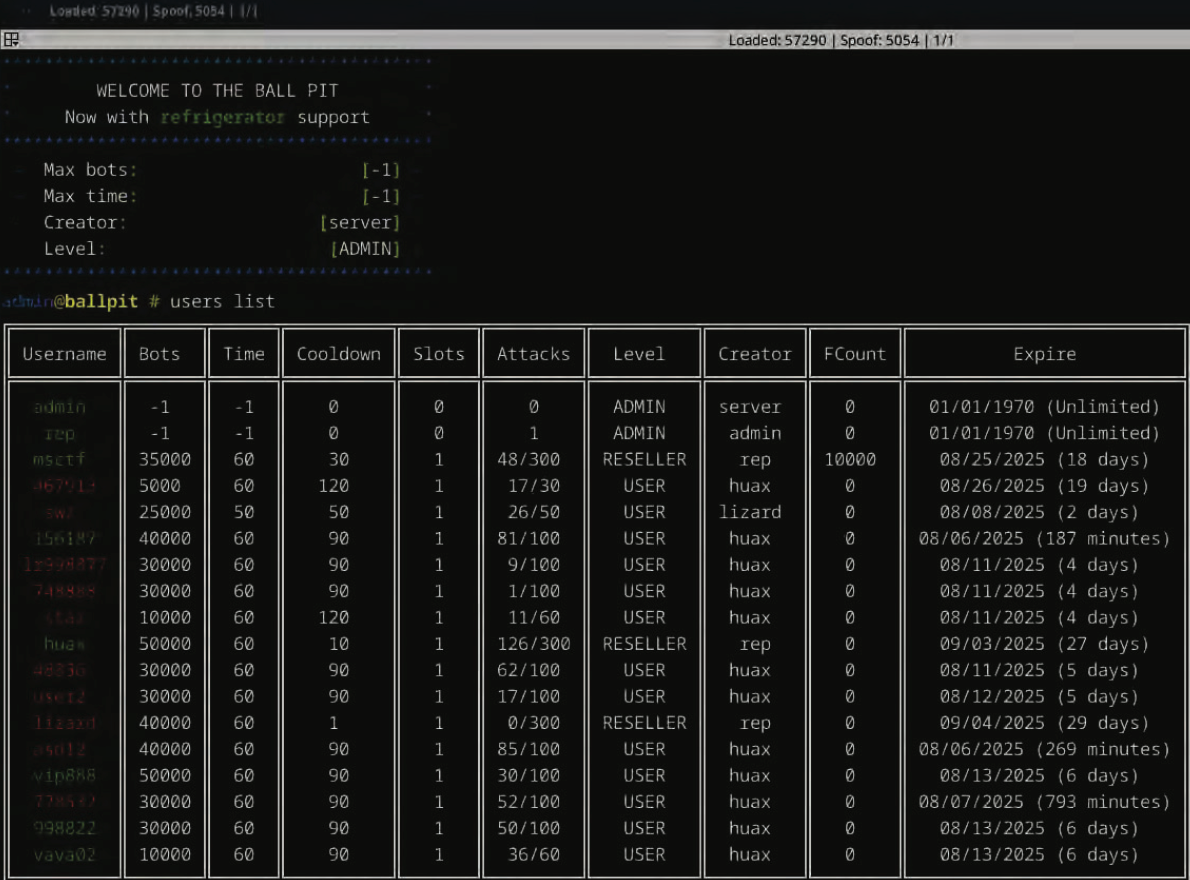
The control interface for the Rapper Bot botnet welcomes users with the note “Welcome to the Ball Pit, Now with refrigerator support,” seemingly alluding to several IoT-enabled refrigerators that were compromised within their DDoS botnet.
On August 6, 2025, federal officials arrested Ethan J. Foltz from Springfield, Ore. on the charge of running Rapper Bot, a decentralized assembly of tens of thousands of compromised Internet of Things (IoT) devices.
The charges against Foltz outline that the assaults typically exceeded two terabits of unwanted data per second (with a terabit equating to one trillion bits), which is sufficiently high to induce significant disruptions for all but the most robustly protected targets. The government indicates that Rapper Bot regularly initiated attacks that were “hundreds of times larger than the anticipated capacity of a typical server situated in a data center,” with some of its most formidable assaults surpassing six terabits per second.
Notably, Rapper Bot was allegedly accountable for the March 10, 2025 incident that caused sporadic outages on Twitter/X. The government asserts that Rapper Bot’s most profitable and frequent clients were involved in extorting online businesses — including various gambling enterprises based in China.
The criminal complaint was composed by Elliott Peterson, an investigator affiliated with the Defense Criminal Investigative Service (DCIS), the criminal investigative sector of the Department of Defense (DoD) Office of Inspector General. The document notes the involvement of DCIS due to several Internet addresses operated by the DoD being targeted by Rapper Bot attacks.
Peterson revealed that he traced Rapper Bot to Foltz after a subpoena to an ISP in Arizona that was hosting one of the botnet’s control servers indicated the account was funded through PayPal. Further legal inquiries into PayPal uncovered Foltz’s Gmail account and previously utilized IP addresses. A subpoena to Google revealed that the defendant routinely searched security blogs for information regarding Rapper Bot and for updates on competing DDoS-for-hire botnets.
As specified in the complaint, following the execution of a search warrant at his residence, the defendant acknowledged constructing and managing Rapper Bot, splitting the earnings 50/50 with a colleague he claimed to recognize solely by the hacker alias “Slaykings.” Foltz also provided investigators with logs from his Telegram discussions, where he and Slaykings deliberated on strategies to remain undetected by law enforcement while their rivals were being apprehended.
In particular, the two hackers communicated about a May 20 assault on KrebsOnSecurity.com that recorded over 6.3 terabits of data per second. This brief assault gained attention as it was the largest DDoS that Google had mitigated at that time (KrebsOnSecurity is protected under Project Shield, a complimentary DDoS defense service offered by Google for websites focused on news, human rights, and electoral content).
The May 2025 DDoS was executed by an IoT botnet dubbed Aisuru, which I uncovered was managed by a 21-year-old individual in Brazil named Kaike Southier Leite. This person was better known online as “Forky,” and Forky expressed that he held no fear regarding me or U.S. federal authorities. Nonetheless, the complaint against Foltz mentions that Forky’s botnet appeared to shrink in size and potency concurrently with the rise in Rapper Bot’s infection counts.
“Both FOLTZ and Slaykings were extremely dismissive of attention-seeking behaviors, the most extreme of which, according to them, was launching DDoS assaults against the site of the renowned cybersecurity journalist Brian Krebs,” Peterson detailed in the criminal complaint.
“You see, they’ll get themselves [expletive],” Slaykings responded to Foltz’s remarks about Forky and Aisuru attracting too much scrutiny.
“Prob cuz [redacted] hit krebs,” Foltz replied.
“Going against Krebs isn’t a wise choice,” Slaykings agreed. “It’s not about being a [expletive] or fearful, you just end up with a lot of troubles for no gain. Immature, but sound. Let them perish.”
“Ye, it’s good tho, they will die,” Foltz responded.
The government asserts that just before Foltz’s arrest, Rapper Bot had commandeered an estimated 65,000 devices worldwide. While this may appear substantial, the complaint observes that the accused were not keen on garnering headlines for constructing the world’s largest or most powerful botnet.
On the contrary: The complaint claims that the defendants were careful to keep their botnet at a “Goldilocks” size — ensuring that “the number of devices enabled significant attacks while still being manageable to oversee and, in the hopes of Foltz and his associates, small enough to avoid detection.”
The complaint indicates that several days later, Foltz and Slaykings resumed discussions regarding their expectations for their rival group, with Slaykings stating, “Krebs is highly vengeful. He won’t cease until they are [expletive] to the core.”
“Surprised they still have any bots left,” Foltz retorted.
“Krebs is not someone you want to antagonize. Not because he’s intimidating or anything, but because he won’t relent UNTIL you are [expletive] [expletive]. He proved it with Mirai and several other incidents.”
[Unknown expletives aside, that may be the highest praise I’ve ever received from a cybercriminal. I might even consider having part of that quote printed on a t-shirt or mug. It’s also relieving that they refrained from directing any of their clients to attack my site — if only out of a paranoid sense of self-preservation.]
Foltz acknowledged erasing the user and attack logs for the botnet approximately weekly, leaving investigators unable to quantify the total number of attacks, clients, and targets of this extensive crime operation. However, the accessible data indicated that from April 2025 to early August, Rapper Bot executed over 370,000 attacks, impacting 18,000 distinct victims across 1,000 networks, with a majority of victims situated in China, Japan, the United States, Ireland, and Hong Kong (in that order).
According to the government, Rapperbot derives a significant portion of its code from fBot, a DDoS malware variant known also as Satori. In 2020, officials in Northern Ireland charged a then 20-year-old individual named Aaron “Vamp” Sterritt with managing fBot alongside a co-conspirator. U.S. prosecutorsare still pursuing Sterritt’s extradition to the United States. fBot is a variant of the Mirai IoT botnet that has devastated the Internet with DDoS attacks since its code was made public in 2016.
The complaint indicates that Foltz and his associate did not permit the majority of clients to initiate attacks that exceeded 60 seconds in length — a tactic aimed at minimizing public scrutiny of the botnet. However, the government alleges that the operators also had exclusive agreements with certain high-paying customers that allowed for significantly larger and prolonged assaults.
The accused and his purported accomplice mocked this blog post regarding the repercussions of one of their botnet assaults.
Individuals who have never experienced a large-scale DDoS attack remain unaware of the expenses and turmoil such assaults can incite. The DCIS’s Peterson noted that he was able to evaluate the botnet’s potential while interviewing Foltz, discovering that “if this had been a server hosting my website, using services like load balancers, and paying for both outbound and inbound data, at estimated industry average costs, the attack (2+ Terabits per second over 30 seconds) could have cost the victim anywhere from $500 to $10,000.”
“DDoS assaults of this magnitude frequently impose severe financial consequences on victims, and an alternative, network engineering solutions that mitigate anticipated attacks such as overprovisioning, or DDoS defense technologies, can themselves be prohibitively costly,” the complaint continues. “This ‘rock and a hard place’ predicament for many victims can leave them acutely vulnerable to extortion demands – ‘pay X dollars and the DDoS assaults will cease’.”
The Telegram chat records reveal that the day prior to Peterson and other federal agents conducting a raid on Foltz’s residence, Foltz supposedly informed his associate that he had discovered 32,000 new devices susceptible to an unrecognized exploit.

Foltz and Slaykings discussing the identification of an IoT vulnerability that grants them access to 32,000 additional devices.
Just prior to the execution of a search warrant at his residence, Foltz allegedly conveyed to his partner that “Once more, we possess the largest botnet in the community.” The next day, Foltz informed his partner that it was going to be a remarkable day — the largest thus far regarding revenue generated by Rapper Bot.
“I sat next to Foltz as the messages flooded in — promises of $800, then $1,000, with profits climbing as the day progressed,” Peterson wrote. “Noticing a shift in Foltz’s demeanor and worried that he was making real-time adjustments to the botnet configuration, Slaykings inquired, ‘What’s up?’ Foltz skillfully typed out some prompt replies. Assured by Foltz’s response, Slaykings replied, ‘Okay, I’m the paranoid one.’”
The case is being prosecuted by the U.S. Attorney’s Office for the District of Alaska (since at least some of the devices identified as infected with Rapper Bot were located there, and Peterson is stationed there). Foltz faces a single count of facilitating computer intrusions. If found guilty, he could serve up to 10 years in prison, although it is unlikely that a federal judge would impose such a lengthy sentence for a first-time conviction.