“`html
At least 18 well-known JavaScript code libraries that are cumulatively downloaded over two billion times each week were briefly undermined with harmful software today, following a developer’s fall into a phishing trap related to the maintenance of the projects. The breach seems to have been promptly managed and was narrowly aimed at pilfering cryptocurrency. However, specialists caution that a comparable assault with a slightly more sinister payload could swiftly result in a disruptive malware epidemic that is significantly more challenging to detect and contain.
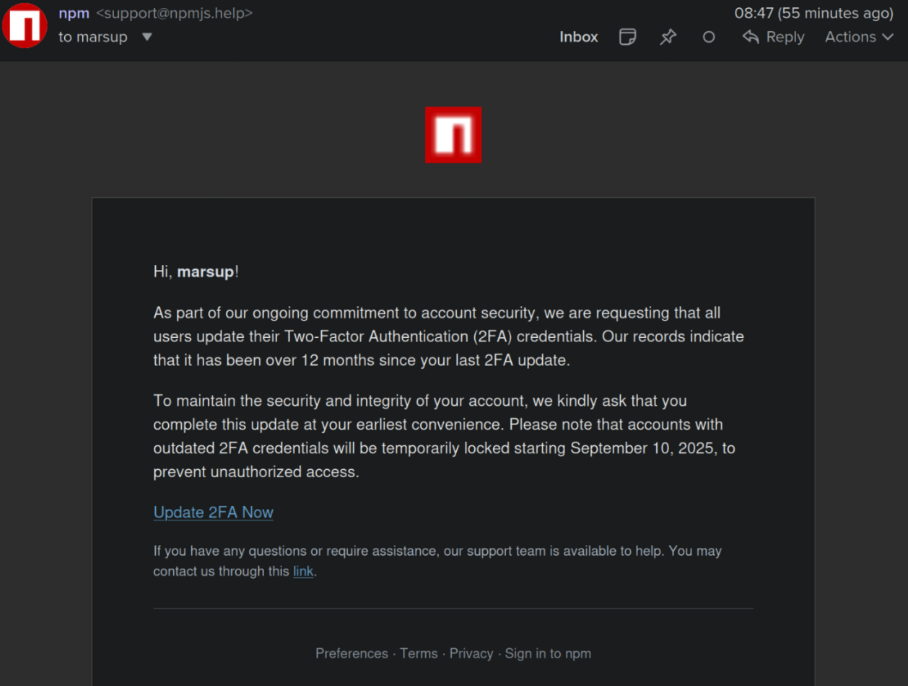
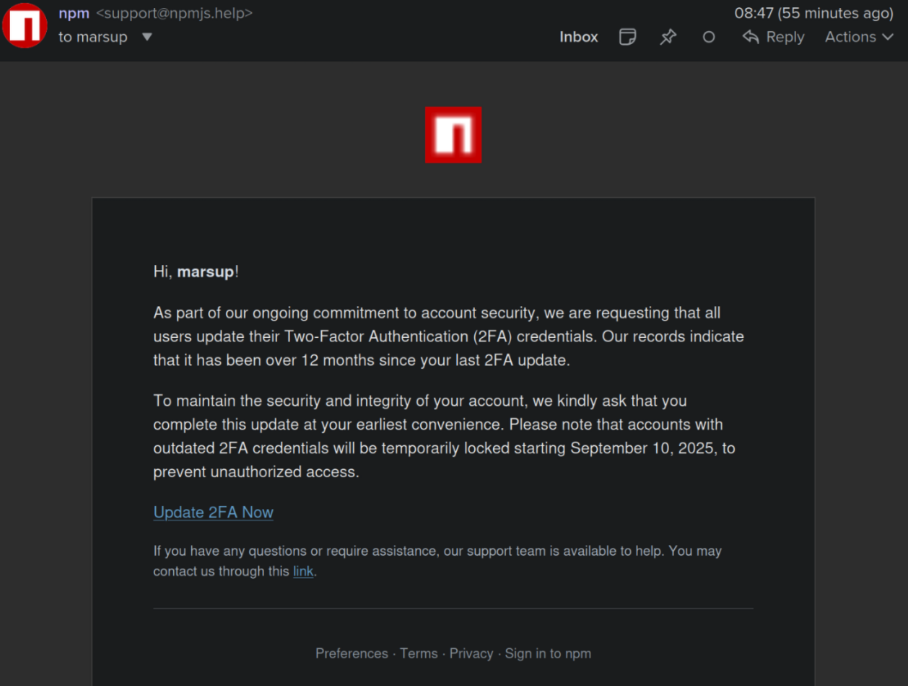
This phishing email deceived a developer into logging into a fraudulent NPM website and providing a one-time token for two-factor authentication. The phishers subsequently exploited that developer’s NPM account to inject harmful code into at least 18 widely-used JavaScript code libraries.
Akido is a cybersecurity firm based in Belgium that scrutinizes new code updates for significant open-source code repositories, scanning any changes for suspicious and harmful code. In a blog entry released today, Akido stated that its systems detected malicious code had infiltrated at least 18 widely-used code libraries accessible on NPM (short for) “Node Package Manager,” which serves as a central hub for JavaScript development and the latest updates for widely-utilized JavaScript components.
JavaScript is a formidable web-based scripting language employed by innumerable websites to create a more interactive experience with users, such as inputting data into a form. However, there’s no requirement for every website developer to construct a program from scratch for data entry when they can simply reuse pre-existing packages of code found on NPM specifically crafted for that function.
Regrettably, if cybercriminals succeed in phishing NPM credentials from developers, they can embed harmful code that enables attackers to fundamentally manipulate what users observe in their web browser when accessing a site utilizing one of the compromised code libraries.
According to Akido, the assailants injected a code segment that covertly captures cryptocurrency transactions in the browser, “influences wallet interactions, and alters payment destinations so that funds and approvals are redirected to attacker-controlled accounts without any evident indications to the user.”
“This malware functions as a browser-based interceptor that seizes both network traffic and application APIs,” Akido researcher Charlie Eriksen noted. “What makes it hazardous is that it operates on multiple levels: Modifying content displayed on websites, interfering with API calls, and manipulating what users’ applications believe they are authorizing. Even if the interface appears correct, the underlying transaction can be diverted in the background.”
Akido mentioned that it utilized the social network Bsky to inform the affected developer, Josh Junon, who swiftly responded that he was aware of having just been phished. The phishing email that Junon fell victim to was part of a broader campaign that impersonated NPM, instructing recipients to update their two-factor authentication (2FA) credentials. The phishing site replicated NPM’s login interface, capturing Junon’s credentials and 2FA token. Once logged in, the phishers altered the email address linked to Junon’s NPM account, temporarily preventing him from accessing it.
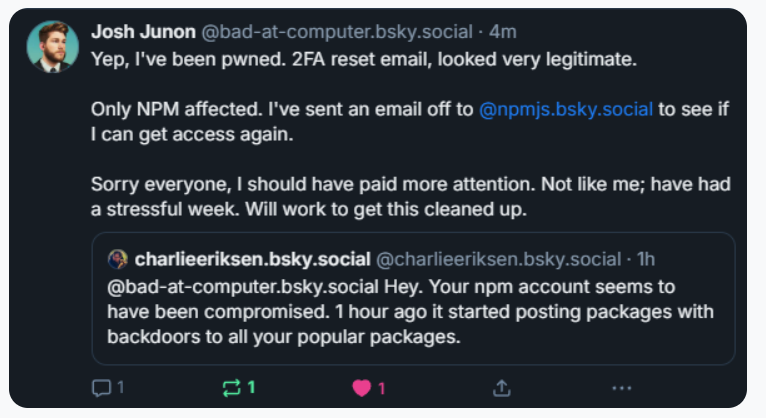
Aikido notified the maintainer on Bluesky, who responded at 15:15 UTC that he was aware of being compromised, and commencing efforts to rectify the compromised packages.
Junon also expressed a formal apology on HackerNews, addressing the community’s programmer-heavy readership, “Hi, yes I got compromised.”
“It seems and feels a bit like a targeted assault,” Junon remarked. “Apologies to everyone, quite embarrassing.”
Philippe Caturegli, “chief hacking officer” at the cybersecurity consultancy Seralys, noted that the attackers appeared to have registered their fraudulent website — npmjs[.]help — merely two days prior to dispatching the phishing email. The spoofed site utilized services from dnsexit[.]com, a “dynamic DNS” company that also offers “100% free” domain names that can be instantly directed to any IP address controlled by the user.
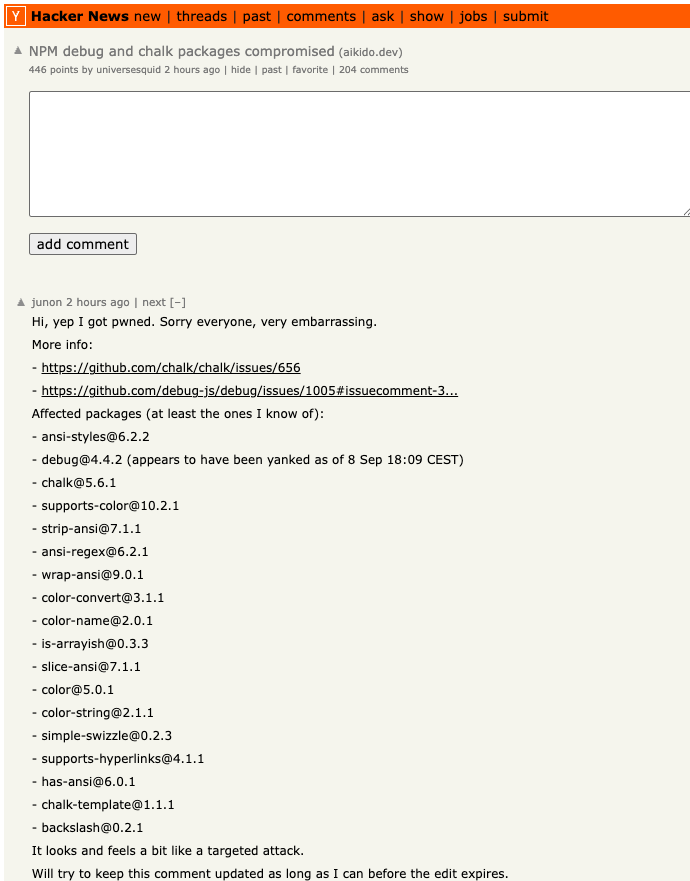
Junon’s apology on Hackernews today enumerated the affected packages.
Caturegli remarked that it is remarkable the attackers in this instance were not more ambitious or malicious with their code alterations.
“The astonishing part is they compromised billions of websites and applications solely to target a few cryptocurrency assets,” he stated. “This was a supply chain attack, and it could have easily turned into something significantly worse than cryptocurrency harvesting.”
Akido’s Eriksen concurred, stating countless websites narrowly avoided disaster because this incident was resolved within a matter of hours. As an illustration of how these supply-chain attacks can escalate rapidly, Eriksen pointed to another incidence involving an NPM developer in late August that added malware to “nx,” an open-source code development toolkit with as many as six million downloads weekly.
In the nx breach, the attackers incorporated code that searched the user’s device for authentication tokens from developer sites like GitHub and NPM, along with SSH and API keys. However, instead of transmitting those stolen credentials to a central server operated by the attackers, the malicious code established a new public repository in the victim’s GitHub account, and published the stolen data there for public view and download.
Eriksen emphasized that coding platforms like GitHub and NPM ought to be taking further actions to ensure that any new code submissions for widely-used packages necessitate a higher level of validation that confirms the code in question was indeed submitted by the account owner and not merely by their account.
“More popular packages should necessitate verification that it originated from trusted sources and not just randomly from some location on the Internet,” Eriksen remarked. “Where is the package uploaded from, by GitHub in reaction to a fresh pull request into the main branch, or elsewhere? In this case, they did not compromise the target’s GitHub account. They left that untouched. They simply uploaded a modified version that did not originate where it was expected to.”
Eriksen noted that compromises of code repositories can be devastating for developers, many of whom ultimately discard their projects entirely following such an event.
“It’s unfortunate because one trend we’ve observed is that individuals have their projects breached and they decide, ‘You know what, I don’t have the stamina for this, and I’m just going to deprecate the whole package,’”
“““html
Eriksen stated.
Kevin Beaumont, a frequently cited security authority who writes about security occurrences on the blog doublepulsar.com, has been closely monitoring this situation today with regular updates on his Mastodon account. Beaumont remarked that the event serves as a reminder that much of the globe still relies on code that is ultimately managed by a remarkably small group of individuals who are often overwhelmed and under-resourced.
“For approximately the last 15 years, every enterprise has been building applications by integrating 178 interconnected libraries created by 24 individuals in a shed in Skegness,” Beaumont expressed on Mastodon. “For about the last 2 years, organizations have been acquiring AI-powered coding tools, where an executive shouts ‘create an online store’ into a computer, and 389 libraries get added, resulting in an app being produced. The result = if you wish to control the world’s companies, simply phish one individual in Skegness.”
Image: https://infosec.exchange/@[email protected].
Akido has recently introduced a product designed to assist development teams in verifying that every code library utilized is scanned for malware prior to its usage or installation. Nicholas Weaver, a researcher at the International Computer Science Institute, a nonprofit based in Berkeley, California, stated that Akido’s new solution exists due to the reality that many organizations remain just one successful phishing attack away from experiencing a supply-chain catastrophe.
Weaver noted that these kinds of supply-chain breaches will persist as long as those responsible for maintaining widely utilized code continue to depend on vulnerable forms of 2FA.
“NPM should exclusively support phish-resistant authentication,” Weaver argued, alluding to physical security keys that are immune to phishing—indicating that even if attackers succeed in stealing your username and password, they cannot access your account without also having that physical key.
“All essential infrastructure must employ phish-resistant 2FA, and given the dependencies in contemporary software, repositories like NPM are indeed critical infrastructure,” Weaver asserted. “The fact that NPM does not require all contributor accounts to utilize security keys or similar 2FA methods should be seen as negligence.”
“`